Contents:
Medusa malware was noticed to target multiple geographic regions. Its goal? Financial fraud and online credentials theft.
More Details on Medusa Malware
A new report from the ThreatFabric researchers came out revealing insights into the latest methods employed by this banking Trojan.
Medusa malware, also known as TangleBot, has been leveraged in North America and Europe campaigns employing distribution services similar to FluBot malware, as researchers confirmed that Medusa is currently using the same service as FluBot in the process of SMS phishing campaign development, being also of the opinion that this method was adopted after seeing the success of the FluBot campaigns.
Medusa has multiple botnets. The samples seen in side-by-side campaigns with Cabassous are identified by the actors themselves with the tags FLUVOICE, FLUFLASH and FLUDHL (possibly as a reference to the corresponding Cabassous/Flubot campaigns). All these botnets use two separate C2 backends to manage bots. The first is the fronting C2, to which bots connect to, while the second is the actual bot operator panel, used by operators to manage their different botnets.
One of the methods leveraged by this malware consists in abusing the Android ‘Accessibility’ scripting engine, fact that lets hacker impersonate users in order to perform multiple actions such as
It’s also worth mentioning that this banking trojan shows a set of interesting features like live audio and video streaming, remote command execution options, and also keylogging features.
The above-mentioned researchers managed to access the backend administration panel of the baking trojan. This helped them notice the ability of its operators to edit any field regardless of banking application. This means that any baking platform is faced with the risk of fake phishing login forms that will ultimately result in credentials theft.
The researchers also shared an image displaying the backend administration panel:
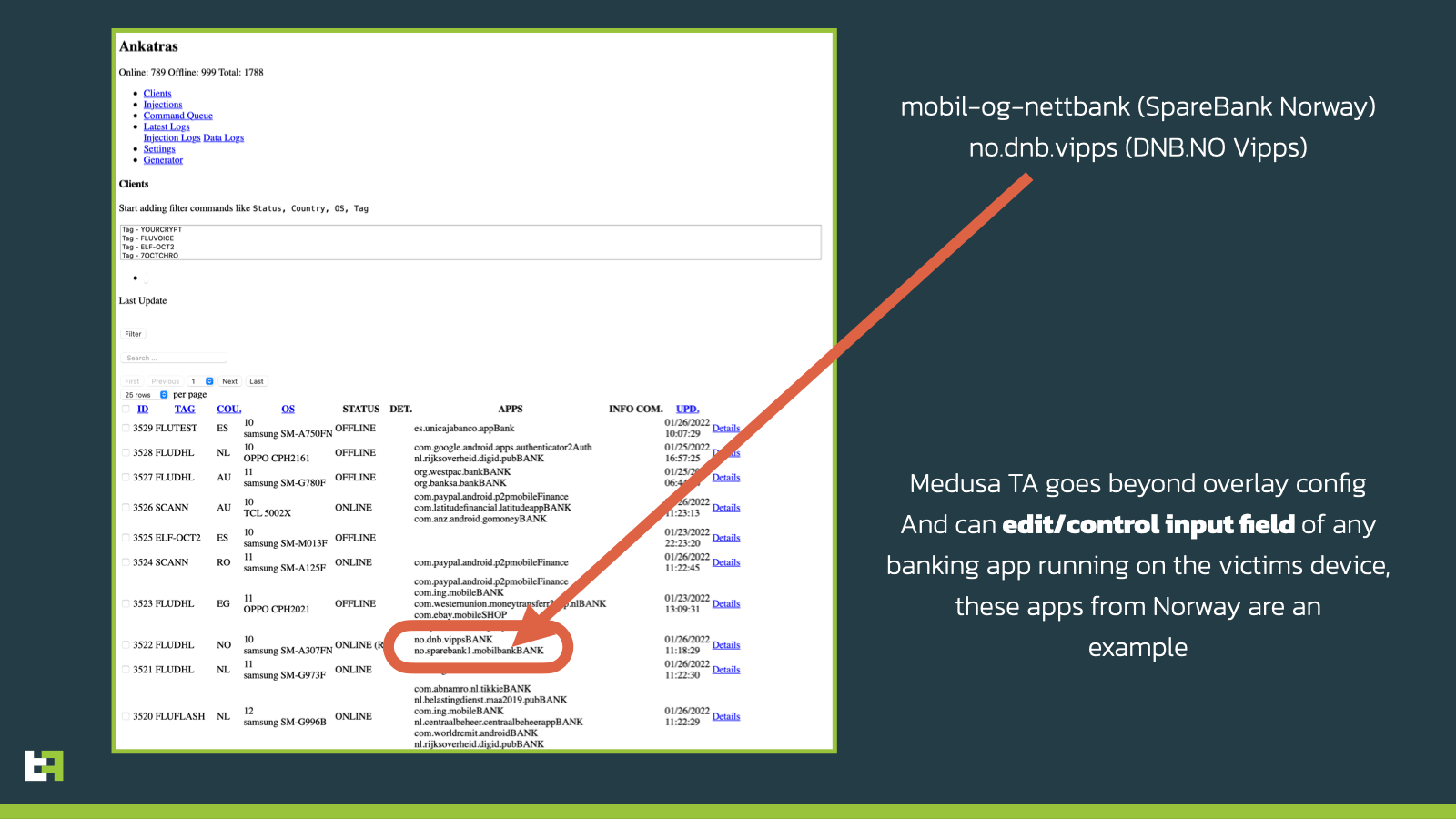
The panel that Medusa leveraged is dubbed Ankatras. Threat actors usually distribute it via Purolator or DHL applications but also posing as Android Update, Flash Player, Amazon Locker, and Video Player. The victims will manually install the APKs because they are sent an SMS message that contains a link that directs them to a website showing the malicious application.
How Can Heimdal™ Help?
Phishing is all around nowadays with more and more advanced techniques being adopted. Make sure that you use an efficient Email Security tool paired with a good Email Fraud Prevention product. The first keeps mail-delivered threats away, while the latter protects against Business Email Compromise and fraud attempts through a combination of threat intelligence and a number of 125 analysis vectors.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










