Contents:
For the past few weeks, your teenage child has been distant and quiet, even more so than usual. You’ve tried to engage in a conversation, but nothing comes out of it. You suspect it’s a passing phase and let it run its course.
But then you get a phone call from your kid’s school principle. Apparently, nude photos of your child leaked and spread like wildfire around campus. Your teenager is now the subject of intense abuse, while the grades are plummeting.
“Is everything ok back home? Did you know about this?”
By now, you are lost for words. You heard of similar examples of cyberbullying before, but never thought it would happen to your own child. Now it’s up for you to pick up the pieces and get things back on track again.
What is cyber bullying?
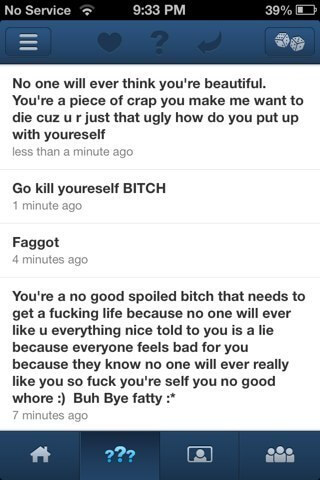
Cyberbullying is a type of harassment carried out through electronic means. The cyberbully seeks to intimidate or emotionally abuse the victim by exploiting a perceived flaw, such as being overweight. In other cases, the bully might attempt to leverage the victims intimate information, such as nude photos or sensitive personal stories.
Most of the times, this happens to children in their teenage years. Teenagers keep their parents in the dark about this, for various reasons, such as shame, fear of being misunderstood or simply because the parent is outright indifferent.
The longterm violence and humiliation can severely damage the victim’s self-esteem, generate stress and anxiety or even induce depression. In some of the worst cases recorded, the constant harassment and stress lead to the victim committing suicide.
How do cyber bullies operate?
In most cases, the cyber bully knows the victim in real life, and collects his/her information that way. For instance, the two might study at the same school, or live very close to one another.
A frequent tactic employed by cyber bullies is to create fake online personas. If the victim is a boy, then the bully creates a girl’s profile to seduce him, and learn more private information. If the information is “controversial” (for teenage standards at least), he then shares it in their social network, such as a school or neighborhood.
When targeting girls, the cyber attacker looks to obtain nude photos. They can then either make them public, or demand “favors” from the victim in order to keep them private.
Cyberbullying facts and statistics
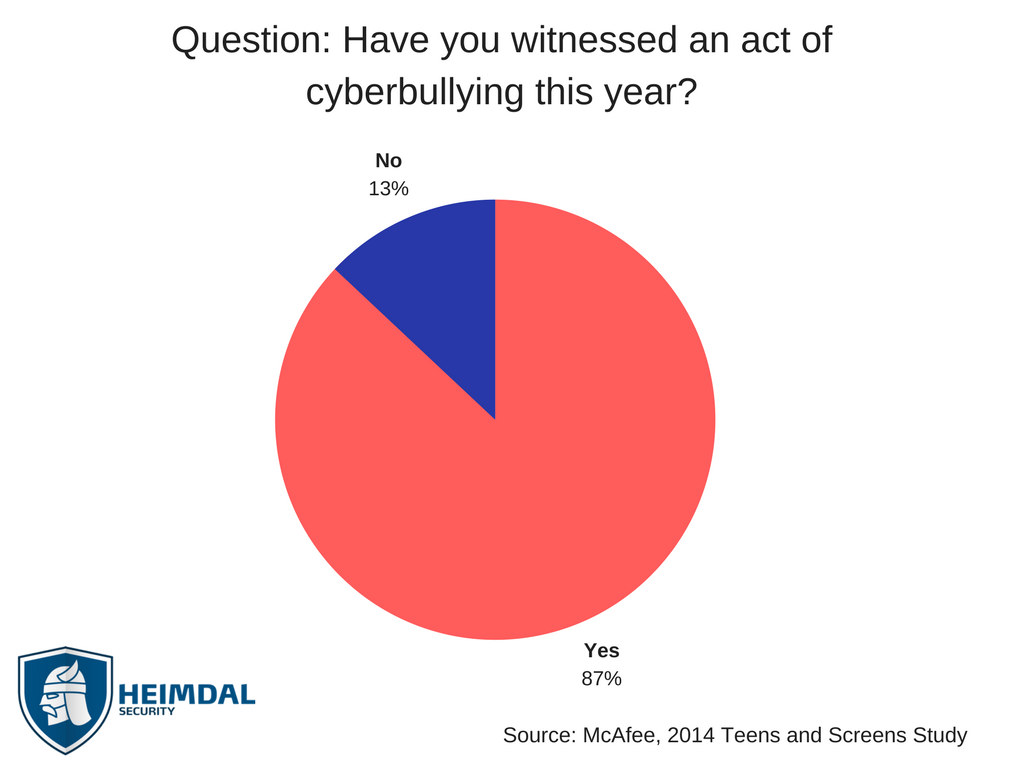
In a 2014 study by McAfee , nearly 87% of youngsters witnessed an act of cyberbullying. In a more narrow study conducted on a single school, nearly 34% of 11 to 15 year olds students said they were victims of this phenomenon.
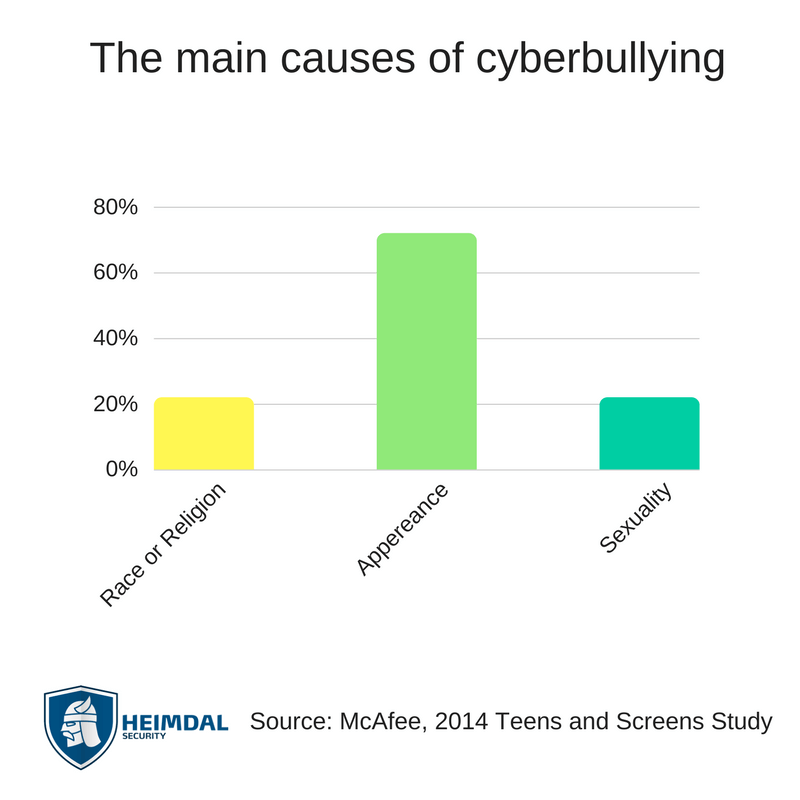
In the McAfee study, victims were also asked what caused the harrasment. Around 72% of responders said it was their appearance, 26% claimed it was their race or religion, while 22% stated it was their sexuality. Another interesting finding was that girls in general are more exposed than boys.
The two types of cyberbullies and what motivates them
Cyberbullies do what they do for a variety of reasons, and understanding their motivation and mode of operation will help you figure out if your child is dealing with a school bully, or a more sinister threat.
1. School bullies
According to this study, nearly 90% teens who were cyberbullied also reported offline harrasment. A school bully might look for new ways to pester his target, so he opts to use the Internet. The cyberbully might create a fake online persona to gain the trust of the victim and learn personal information. which he then reveals to a wider social circle, as a shaming or humiliation tactic.
In other cases, the bully might even create a fake profile of the victim itself, filled with compromising photos or other types of content.
However, the easiest way for a cyberbully to strike his victim is through messaging apps such as Skype or Facebook Messenger. The harassment can target anything, such as physical appearance, general demeanor or perceived intelligence.
2. Cybercriminals looking to make a profit
A more insidious case of online harassment are people looking to make a profit. A cybercriminal will typically lurk on dating sites, web chat apps and other such places, looking for potential victims.
Once he settles on a target, the cybercriminal seeks to obtain leverage. An easily obtainable one are intimate recordings, such as sex acts or other explicit material.
After the cybercriminal gets his hands on these, the blackmail commences. He threatens to reveal the photos/videos to the victims friends, family, school colleagues and more. The only way out is for the victim to pay to keep the secret.
But paying up won’t guarantee the attacker will keep his side of the bargain. After all, adult sites are filled with photos and videos of revenge porn.
One such case was that of Daniel Perry, a 17 year old Scottish teenager. Using the Internet, he got himself involved with someone he thought was a girl of his age. The “girl” eventually convinced him to make an explicit video of himself. She then used the video as blackmail, demanding Daniel pay up in order to avoid the video’s publication. In Daniel’s mind however, the only way out of the situation was to commit suicide.
[Tweet “Some cybercriminals blackmail teenage kids, and extort them for money”]Most frequently used cyberbullying tactics
Cyberbullies have come up with many ways to harass and abuse their victims. The ones we’ve listed are the most prevalent and used ones out there.
1. Chat room bashing
During chat room bashing, a victim gets targeted by the users from an online messaging board. Teenagers sometimes use chat rooms as massive online meeting places, where they discuss the comings and goings of their school lives.
These discussions can turn nasty if the subject of the conversations switches to making fun of the “weird, unpopular kid”.
But it’s not just school chat rooms that are susceptible to this. Other types of forums and chat boards are also likely places where harassment and abuse might take place.
2. By proxy
In this case, the bully manages to convince other Internet users to harass the victim, either through lies or persuasion. Things are made worse if the bully attracts adults to his side.
3. Cyber harassment
Direct messaging apps like Messenger or WhatsApp allow a cyberbully to repeteadly abuse and harass his victim. The bully uses the victims physical appearance, race, sexual orientation and other “flaws” as beating sticks to humiliate and dominate her.
4. Denigration and isolation
Denigration involves the spreading of false rumors and other forms of gossiping about the victim. The point is to make the victim feel undesirable in her social circle, and isolate her from friends.
5. Exposure
In this method, the attacker somehow gets their hands on personal information about the victim, which he then spreads in an effort to shame and humiliate her. Sexual and other such explicit videos are the most damaging types of information a cyberbully can spread. Unfortunately, in some cases these can have negative effects well into adulthood, such as hiring attempts or job stability.
6. Recordings of physical abuse
Being physically abused and bullied is a humiliating experience. Bullies know this of course, it’s one of the reasons why they do it.
Bullies use modern phone cameras to record the abuse and then spread it online so that mass viewership by the victim’s peers will deepen the humiliation.
7. Phishing
This type of phishing is slightly different than the standard fake email or SMS we’re used to seeing.
A cyberbully can create a fake online profile and then use it to befriend or seduce the victim into revealing information about herself, her parents or any other type of useful data the phisher might use.
How to prevent cyberbullying
Going through such a period can be a difficult thing to go through, both for the victim and their parents. But there are ways to prevent this, and keep the damage to a minimum.
1. Talk to your child about this, prepare him
One of the best cyberbullying preventive measures is to talk about it before it happens. Explain to your child how it happens, why someone would want to harass him, and also how to deal with it.
Arming your child with the knowledge on how to deal with the threat will ease the initial panic and confusion. It won’t be something new to him, and he’ll already have a set of tools to cope with the bully.
Here’s a small list of advice you can impart to your child:
- Your child should talk to someone he trusts. Ideally, it should be you, as a parent, but it could also be a teacher, a counselor or a friend.
- Tell the bully to stop. This eliminates any possibility that the abusivev behavior might have been consensual. After this point, the cyberbully is fully responsible for his behavior.
- Copy all of the messages and other evidence of the abuse.
- Report everything.
- Block the cyberbully from any messaging apps he might use. Social networks such as Facebook allow you to report abusive content.
It’s kind of like how we tell our kids not to ride a car alone with a stranger, and why it’s dangerous to do so. If the situation ever comes when a stranger proposes them to get into their car, they will lean on your teachings and say “No way, Jose”.
2. Educate yourself and your child
Even if you suspect your child is already a victim you should still educate and talk to him about it. Chances are they will not admit this is happening to them.
The stress, shame and fear can make children feel alone and misunderstood, so they hide what they are going through. Only 1 in 10 children open up to their parents and allow them to help.
If you feel that’s the case with your child, then try not to pressure him/her, and ease into the subject. Simply attaching a name for what he is going through will allow him to explore solutions on his own. He can then figure out that what he is going through can be contained and dealt with.
3. Use strong passwords to secure your social media account
Facebook and other social networks contain a lot of information about a user such as private photos and conversations.
To secure these accounts, a strong password is a must have. Weak passwords such as “123456” or “password123”, open the door for a cyber bully to access your account.
This advice applies to parents as well, not just for teenagers. Strong passwords are essential in preventing dictionary or brute force attacks.
4. Log out of online accounts
As a rule, it’s always best for your teenager to log out of his social media accounts when he isn’t using them. This way, if his device gets stolen or hacked, they won’t be accessible.
This advice is even more relevant when it comes to logging out of accounts from public devices such library computers. Nobody should take the risk of having someone log in to their account, reading their messages or impersonating them.
5. Encourage your child to double think what he posts online
Social media is a public space, and everything you do and say there will make its way into the wider world. Things a teenager posts on social media might ruin his reputation and paint him as a target for ridicule, even if he is well-intentioned. Other people, and teenagers especially use social media to weigh up their peers and judge them based on what information they share.
6. Never send nude photos
Sending nude photos is almost always a bad idea. Sure, the other person may be trustworthy now, but will they continue to be trustworthy 5 years into the future? What about 10?
Girls in particular are vulnerable to this. In their rebellious teen years, they might send nude photos of themselves to boyfriends, or other boys they want to impress. In many cases, the boys don’t reciprocate this level of trust, and end up leaking them, showing them off to friends or colleagues.
This was the case with Jess, who shared nude photos to her boyfriend, in an effort to keep their long-distance relationship warm. Soon after, their relationship took a turn for the worse and the two broke up.
A month afterward, a friend told Jess her ex-boyfriend had posted the photos on a revenge porn website for all to see. She pleaded with the ex to have the photos removed, but got rebuffed. He claimed she was “filth” and “deserved it”.
Eventually, the photos were taken down after commenters said they would be willing to rape her.
[Tweet “Don’t send nude photos unless you want them to appear on revenge porn sites”]7. Adjust the privacy settings
When set up correctly, privacy settings can greatly limit how much information a social media account reveals about a user.
Social networks such as Instagram or Twitter have fairly limited privacy settings. At best, you can make your profile private and prevent others from seeing your content. Not much, but still useful.
Facebook on the other hand, has much more extensive and powerful privacy settings. Sure, they are labyrinthine and confusing, but they work.
Here’s a set of guides you can use to secure each of the major social networks:
- Facebook privacy and security guide
- Twitter security and privacy tips and tricks
- LinkedIn privacy and security guide
- Instagram privacy and security guide
8. Use parental control software
Limiting your child’s privacy is always a difficult choice to make, and there isn’t a clear answer if this is a good or a bad thing to do.
If you are willing to take this step, then you might consider using parental control software. This will give you an overview of your child’s online activities, such as websites he’s visiting, people he’s talking to and so on.
Here’s a comprehensive list of the best parental control software of 2017.
9. As a parent, try to figure out if your child is cyberbullied
This sounds a lot easier than it is. In most cases, bullied children prefer to keep these problems to themselves and refuse to share them with their parents. There are however some telltale signs that something isn’t quite right:
- School grades drop. The stress, fear, and harassment often distract a teenager from his school duties, and discourage him from his studies.
- Missing school. Sometimes cyberbullying and real life violence go hand in hand. As such, a teenager might skip school to prevent the abuse and humiliation.
- A pronounced, negative mood swing.
- Isolation and loneliness. A bullied teenager may not be able to discern friend from foe, especially if his friendships weren’t strong and supportive to begin with. As a defense mechanism, the teenager might withdraw himself from friendships and other social circles.
10. Take the fight to the cyberbully, record all the conversations
One advantage that the online world gives to victims is the ability to record the act as its happening.
Each and every violent and threatening act or message should be saved and recorded as evidence. In many cases, cyberbullying constitutes a legal crime, and can be punished as such. In order for this to happen, however, the victim needs to prove the harassment took place.
Messages, posts, fake profiles, photos, should all be saved somewhere.
In some cases, the cyberbully will stop the harassment once the victim makes it clear they will fight back against the abuse.
11. Report the aggressor
Often times, victims believe their tormentors cannot be punished. This fosters a feeling of helplessness, that then further empowers the bully.
But some sort of punishment and correction is possible. In order for this to happen however, the teenager has to come out with what he’s going through.
Here are just a few of the possible avenues you, or your child can follow in order to report the behavior:
- The school principle or college dean, if you suspect the bully is a student at the respective schools.
- Contact your SMS provider to find the phone number or IP of a cyberbully who harasses users using the phone or other messaging apps.
- Facebook has its own policy to tackle this threat, so be sure to contact or report such behavior.
- If things devolve and start to include physical threats and violence, then you should consider notifying the police and bringing it to their attention.
Conclusion
Cyberbullying can have a severe impact on a child’s proper development and can lead to harmful long-term consequences, and some of these can be more than psychological.
As a teenager, it’s important to know that you can, and should ask for help in dealing with this problem. Parents too also carry responsibility in helping their child navigate through this challenge.

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE

 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security