Contents:
Twitter is one of the most popular social media networks used nowadays. Most users are attracted to it because of its 140-character limit and the chronologically ordered feed.
It’s used not only by private users, but also by musicians and actors who want to promote their work, or companies and brands who want to grow and nurture their community.
It’s proven to be extremely useful to journalists and press agencies who want to keep up with what’s going on in different corners of the world. It is widely used as a news spreading tool on terrorist attacks, revolts or natural disasters.
In the recent years, we also witnessed many security breaches of popular Twitter accounts. The latest victim is Katy Perry – a few days ago a hacker breached her account and started sending NSFW tweets from her account. With almost 90 million followers, she is also the most followed person in the world.
It would be reckless for someone to consider its Twitter account bulletproof from online dangers – nothing is 100% safe, no matter what anyone will say to you to try to convince you otherwise. However, there are a few things that you can do to increase your security and privacy.
To enhance your Twitter’s account security, here’s what steps you can take:
1. Create and use a strong password
Yes, we know we keep nagging you about this one. In the light of the recent major data breaches, it’s more essential than ever to have healthy passwords habits.
The password needs to be:
– Strong. I know that it might seem like a great day to use something familiar and easy to remember, like a family member name, favorite pet or birthdate. However, with the huge amount of data available online about us, it would also be extremely easy for a cyber crook to guess your password.
– Unique. People, please stop recycling your password. In case one network gets breached and all the emails and passwords end up leaked, the cyber criminals will use that database to test passwords on all other networks.
To make sure that your account is safe, create a strong password that includes upper and lower case characters, numbers and symbols. It should be more than 10 characters long.
Here’s a more detailed guide on how to secure your passwords.
[Tweet “This guide on how to secure my Twitter account is really useful”]
2. Use login verification
After setting a strong and unique password, this is the next best thing to protect your Twitter account.
Login verification is a form of two-factor authentication. It works as a second layer of protection, besides passwords.
When you’ll want to login from a new device (computer, mobile), in order to verify your identity, Twitter will request you to enter another passcode. That code will be unique, time-sensitive and sent as a text message on your mobile phone.
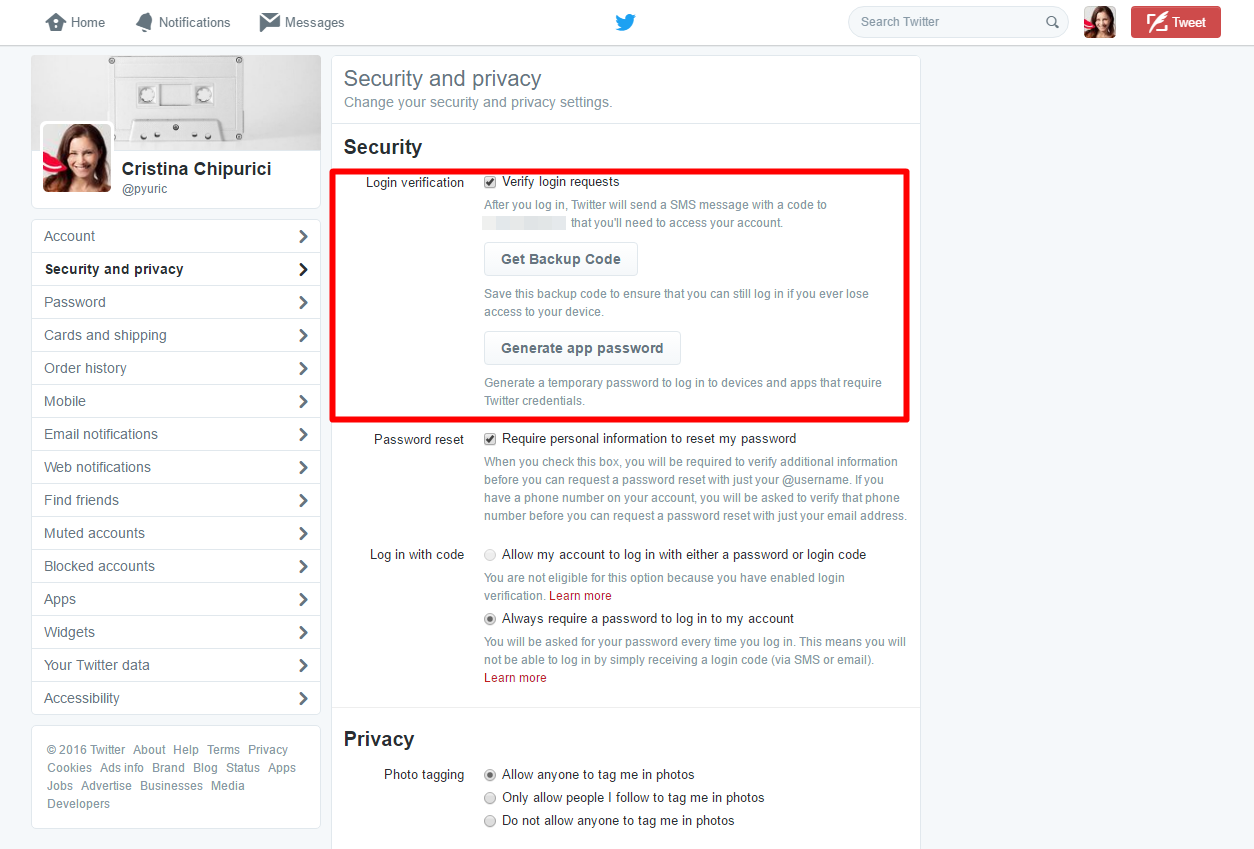
To set up Login verification from your browser, follow these steps:
- Log in to your Twitter account.
- Click on your user photo from the top right corner of the screen.
- Go to Settings from the drop down menu.
- Click on Security and Privacy from the left menu.
- Activate and set up Login verification.
As an alternative in case you ever lose your phone or your mobile network won’t be available, you’ll also receive a backup code that you can use. Save it in a secure place, to ensure that you’ll still be able to log in.
From Login Verification you’re also able to generate an app password. That’s a temporary password that you can use to log in to devices and apps that require Twitter credentials.
3. Don’t post private information and do not disclose your location
By default, Twitter is a public network and anyone will be able to follow you and see what you tweet. Keep in mind that the main keyword here is “public” – every little thing that you tweet will be available online, for anyone who wants to see it.
A few years ago, I ended up setting my account to private because of a competitor. In my naivety (I was also extremely young back then), I was bragging about all the plans that I had and all the meetings I took in order to make my dreams come true. One of my competitors was keeping an eye on everything I was publishing and then copying my exact strategy for their project. They didn’t last long on the market, but it was still unpleasant.
Now try to remember all the tweets that you ever sent out.
Can they somehow be used against you?
Didn’t you divulge any personal, sensitive information, that someone with malicious intentions might take advantage of?

If you want to have some degree of control over who’s following you, you can make your account private by activating the option “Protect my tweets”.
In the previous phrase I used the word “some” because you can never be 100% secure. One of your friends’ accounts can end up hacked – it can be their fault or the networks, it doesn’t even matter.
You can also never be sure that the ones who are following you really are who they say they are or they have good intentions.
That’s why you should always be careful about what you’re posting online. Make sure that you don’t offer any kind of valuable information.
Also keep your tweets’ location disabled – this kind of data can also be used by cyber criminals.
Just imagine the following scenario: you check in from your home, perhaps even post photos of it. During the summer, you leave for that holiday you’ve long been waiting for and you brag about it online. When you arrive back home, you realize that you’ve been the target of burglars, thanks to all the information you posted online. Now who’d want that to happen?
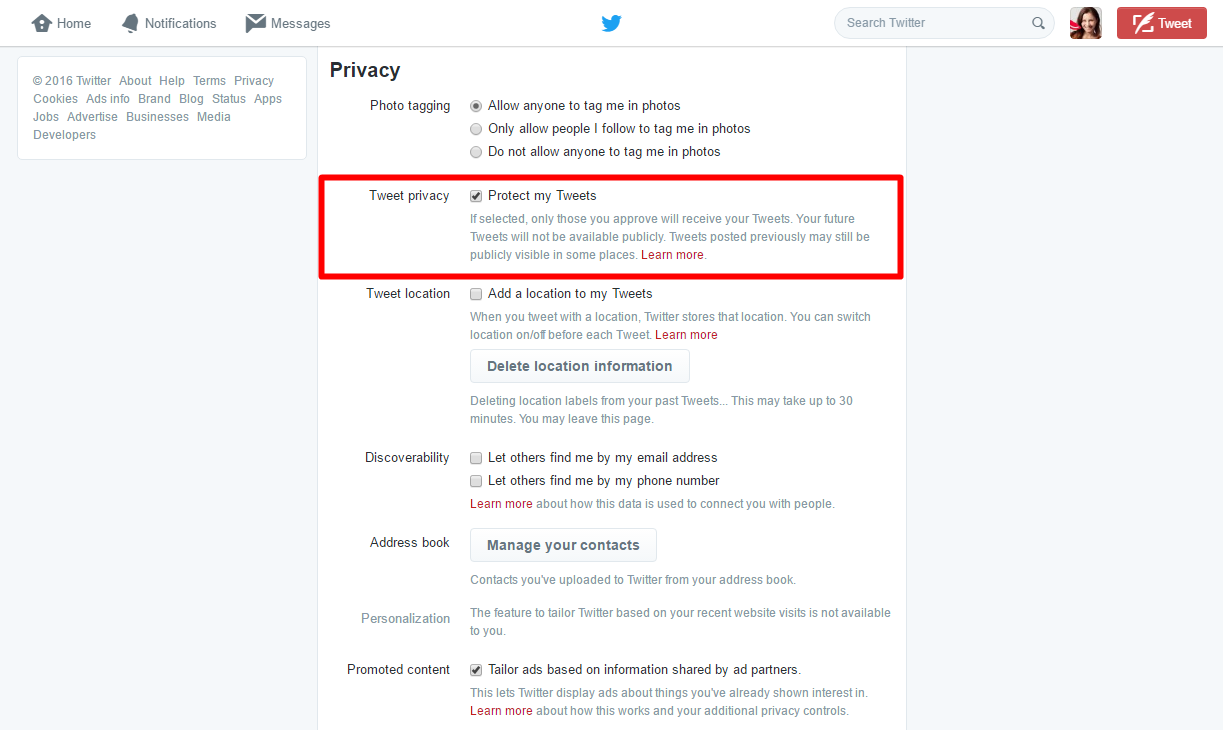
To protect your tweets, follow these steps:
- Log in to your Twitter account.
- Click on your user photo from the top right corner of the screen.
- Go to Settings from the drop down menu.
- Click on Security and Privacy from the left menu.
- Go to Tweet privacy and check “Protect my Tweets” option.
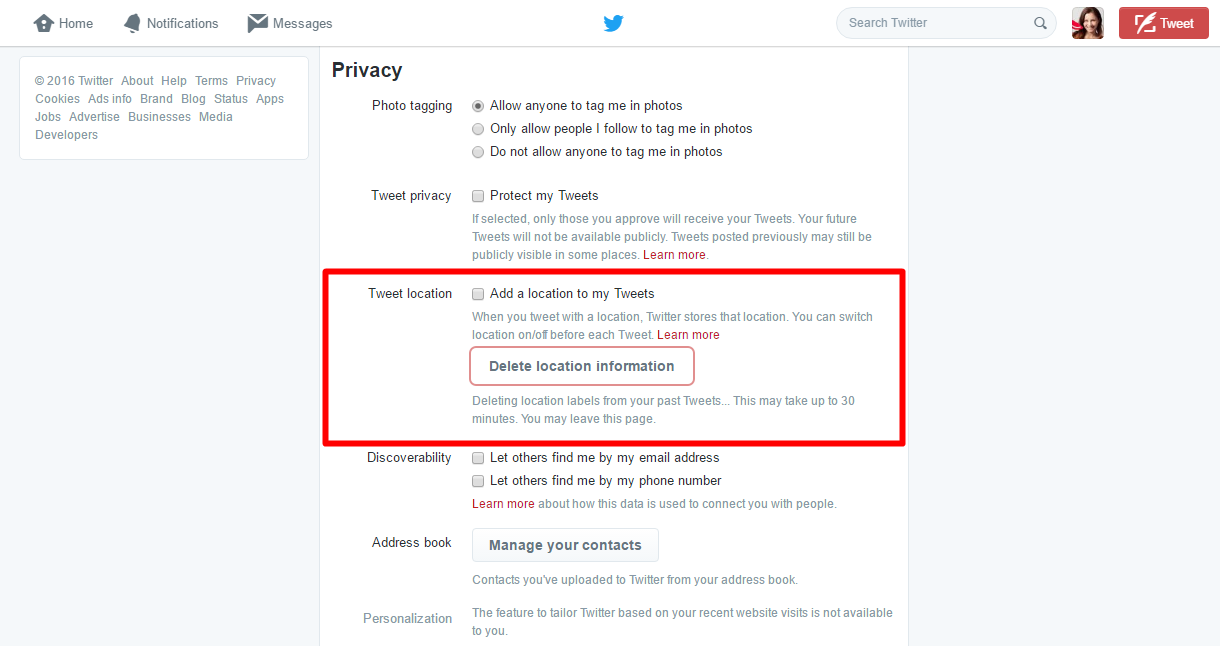
To disable the tweet location, follow these (almost identical) steps:
- Log in to your Twitter account.
- Click on your user photo from the top right corner of the screen.
- Go to Settings from the drop down menu.
- Click on Security and Privacy from the left menu.
- Go to Tweet location and disable the “Add a location to my Tweets” option.
- From here you can also delete the previously stored Tweets location information.
4. Stay safe from phishing attempts
Email phishing attempts are still extremely efficient. Cyber criminals specialized in creating email forms and websites and other elements that look exactly like the ones used by Twitter.
But phishing attacks can also be carried via private messages or replies, from persons who want to obtain your Twitter credentials or any other personal information.
If you want to learn more about how to protect yourself, you can read this guide on detecting and preventing phishing attacks.
Most likely, you also have friends who ended up with hijacked accounts and sent unusual direct messages to all their followers, messages that contained infected links. If you receive any suspicious message, ask them what’s that link about before clicking on it.
5. Use a specialized security solution against spyware threats
Even if you pay attention to phishing attempts and spam campaigns, you still need to keep yourself secured with as many safety nets as possible. Start using a security solution specialized against spyware threats.
Such products that you can use are: Malwarebytes, Spybot Search and Destroy, Lavasoft’s Ad-Aware, etc.
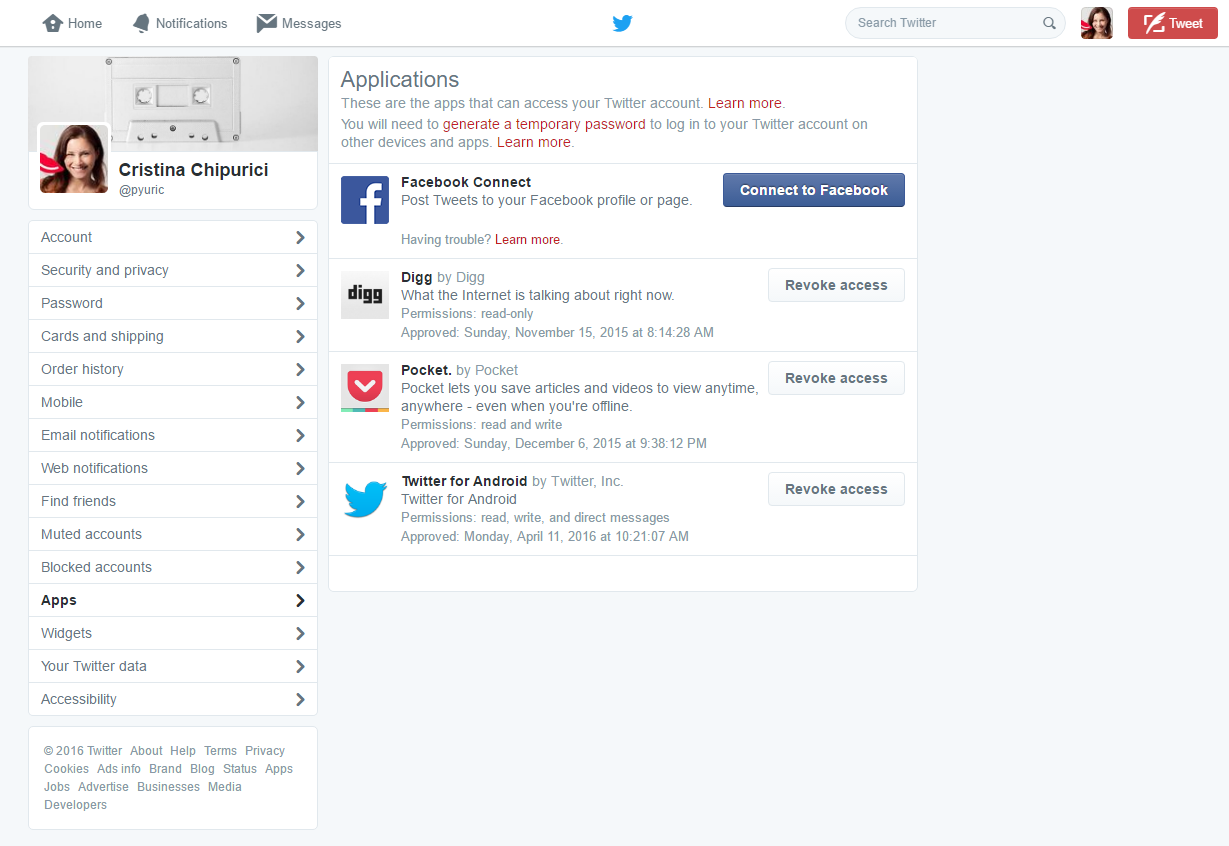
6. Check what apps can access your Twitter account
It’s also essential that you pay attention to third-party apps that connect to your account.
Most likely, in time, you’ve allowed lots of apps to access your Twitter account. Perhaps you used it to connect to other social networks or analytics apps.
What you should realize is that those apps now have access to all your Twitter data. They can take control over your account or take actions that will lead to your account being suspended.
It’s important that you only allow trustworthy apps to connect to your account.
Also stay away from apps that promise to bring you free followers or make easy money. Those are some of the biggest scams used by cyber criminals.
To check permissions apps have to your Twitter account, follow these steps:
- Access your Twitter account.
- Go to the top right corner and click your user image.
- Choose Settings from the drop down list.
- Click Apps in the left menu.
- Take the necessary steps to allow or revoke access.
Here are more details on how to master the app permissions for social networks.
7. Make sure you keep your vulnerable apps up-to-date
Security news on software vulnerabilities have appeared lately all over the important security blogs and related IT channels in the industry.
Security news on software vulnerabilities and attacks because of them keep popping up in the news. However, most users ignore them because they aren’t aware of how close to them those threats really are.
Here’s how it works: cyber crooks take advantage of software vulnerabilities from our systems, our mobile phones apps or our plugins. They use them to gain access to our systems and obtain private information.
That’s why it’s important that you always keep up to date the vulnerable software, like your browsers or plugins, such as Java or Adobe Flash.
Also pay attention to the updates pushed by mobile operating systems.
[Tweet “Found an easy-to-follow guide on securing my Twitter account, make sure you check it out”]
8.Use a Virtual Private Network To Hide Your IP Address
One of the favorite methods used by cyber criminals to steal your credentials to your Twitter account is by using wireless sniffers. With them, they are able to retrieve the data that you send over unsecure, public networks.
To encrypt that traffic and guard your online activity, you can use a VPN – that is a Virtual Private Network.
Using a VPN means that you hide your IP address, encrypt your connection and access various web locations in a private environment. This method keeps your sensitive data protected from identity theft or phishing attempts.

9. Secure your browsing habits
Choose your web browser with care and make sure you’ve taken the necessary steps to enhance your security and privacy.
Browsers are some of the most vulnerable software, making them extremely attractive to cyber criminals.
To secure your online privacy, follow these guidelines:
- Always keep your browser up to date, make sure you use its latest version and install the latest security patches. Here are more than 15 top security experts explaining why patching is key to online security.
- Read (and follow) this Ultimate Guide to Secure your online browsing.
- If you access your social media account from an unsafe location, choose a private (incognito) browsing session in order to remove the browsing history details.
10. Don’t forget to log out from your Twitter account
Last but not least: if you ever connect to your Twitter account from someone else’s device or from a public computer, make sure you don’t forget to log out. As soon as you’re done with your activity, log out and clean all the data of the browser or app.
If we don’t do this, especially if we are in a public location, the next person who opens the browser will be able to access our online profile.
Private browsing sessions are also recommended if you want to prevent authentication credentials (or cookies) from being stored.
Conclusion
When a network becomes very popular, you can bet that scammers will be there, ready to take advantage of any vulnerabilities. They know they have potential new victims and they won’t miss any opportunity to attack.
However, if you’ll set in place all the security layers and keep healthy habits, you’ll be able to minimize the risks of a breach.

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE* This article was initially published by Aurelian Neagu in November 2014 and updated by Cristina Chipurici in June 2016.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security