Today’s organizations rely on a more diverse array of devices than ever before. From laptops to desktops, smartphones to smart devices, IoT and more… the list goes on.
This leaves a huge cybersecurity risk for those organizations that can’t inventory, monitor, and protect the various endpoints they rely on.
That’s where EDR comes in, and of course, EDR implementation matters.
Endpoint detection and response (EDR) products are a bedrock of modern cybersecurity – for precisely this reason.
For many organizations, they’re by far the best way to understand and protect their endpoints.
But to get the most from the tools on offer, it’s important to understand what you’re protecting, the features you’re using to do so, and how to best set up your product for success.
Here’s what you need to know.
Looking to transform your security strategy?
Don't just stop at EDR. Simplify and strengthen your security posture with a unified approach.
4 Essential EDR Features You Need to Know About
No two EDR products are exactly the same – as we’ll go on to explain in more detail below.
But there is a generally accepted feature set that’s common to all conventional tools.
Before you can start choosing your EDR product, it’s helpful to understand the key differences between these products and the way they can be used to keep your IT environment safe.
Here are the most important features you need to be aware of:
1. Threat Detection And Monitoring
This is the fundamental task of an EDR product: To monitor your IT environment and identify real-time cyber threats.
Generally, it’s doing this by compiling and analyzing .log files to understand how users are interacting with your IT environment and the data and endpoints within it.
The goal is to identify strange or anomalous behavior so you can lock down attacks before they can do damage.
The most advanced products on the market also use real-time ‘telemetry’ data.
When a cyberattack is identified in one customer’s IT environment, the intelligence about who that attacker is and how they behaved is used to strengthen the defense for every other user of that software.
2. Endpoint Detection
Most endpoint security solutions will also offer a series of tools to identify all the endpoints in your environment.
This is important because few companies have an accurate list of all the laptops, desktops, mobile devices, IoT devices, and more that they have.
Manually compiling this inventory can be a tedious, long-winded task and there’s no guarantee you’ll include everything.
Yet all endpoints need to be monitored if you’re going to keep them safe.
Running an endpoint detection scan, therefore, is the best place to start.
3. Real-Time Response
If you want to avoid a damaging cyberattack, speed is everything. The moments after suspicious behavior is detected are crucial.
If you can’t lock down the affected accounts as quickly as possible, there’s a good chance the attacker will do permanent damage before you have the chance to stop them.
So what happens if the security team lead is off making a coffee?
In all seriousness, even the most engaged and attentive security team will take a few moments to look at an alert, understand what’s going on, decide on the response, and implement.
But in the first instance, you really just need to lock down any accounts that are showing overly suspicious signals – and automation is overwhelmingly the fastest and most effective way of doing that.
EDR products therefore contain a range of tools to help you define and automate this first-line response.
4. Behavioral Analysis
In the seconds and minutes after an attack, the priority is to stop the attacker’s progress as quickly as possible.
In the hours and days after, however, it’s important to take the time to understand in rich detail how the attacker targeted, infiltrated, and moved through your IT environment.
EDR products also provide a wealth of information about user behavior so you can analyze attacks after they’ve taken place.
This will help you understand how the attacker got in, what damage has been done, and what measures you need to take to mitigate the damage.
How to Choose the Right EDR Product for Your Business
Though the core functionality is similar across most EDRs, there can be significant variation in the quality of these tools and the specific IT environments they’re designed to protect.
This means that the right EDR isn’t going to be the same for every organization.
There are a number of factors that you’ll need to consider when finding the right EDR solution for you.
Here are the most important:
1. How Extensive Is the Support?
If you’re running desktops and laptops on largely Windows-based operating systems, you’re going to be supported by most conventional tools.
But when you start adding Mac or Linux-based endpoints, as well as mobile devices, IoT devices, and more – you’ll have to be more careful about the software you choose.
When assessing an EDR provider, checking the support is a good place to start, because it’s pretty easy to rule contenders in or out based on whether they have the support you need.
Where possible, it’s important to avoid having separate EDR solutions supporting different endpoints – as this creates confusion for the IT team and less effective overall security.

- Andrei Hinodache, Cybersecurity Community Leader
2. What’s the Breadth of Functionality?
Some EDR features are more specialized than others.
Specifically, there can be a lot of variation in how extensive and customizable the automation capabilities are.
For organizations with particularly complex IT environments, it can be helpful to have more granular controls to govern how the platform responds to specific threat signals.
You may want to specify that all logins to privileged accounts should require MFA.
Alternatively, you might want to do the same for all non-privileged logins from new devices and locations.
Some platforms are more effective at giving you this control than others.
The best way to assess the contenders is to look at what other security teams are saying on public reviews, as this will give you a good idea how the product is being used in real life.
3. How Advanced Are the Threat Detection Capabilities?
Some EDR products are better than others at detecting potential security threats and distinguishing them from normal activity.
This is largely due to the telemetry data we discussed earlier.
Cybersecurity providers with a larger customer base generally have more data to analyze about genuine and potential threats – and can use that to make more accurate risk analyses.
Generally, the less effective platforms are going to compensate for this by lowering the threshold at which something is flagged as risky.
If you’re less sure whether something is an attack, the logic dictates that it’s better to be safe than hacked.
But this can create excessive false positives (i.e. normal behavior that’s flagged as risky) for the IT team to wade through, and unnecessary friction in the workflows of everyday users.
This makes it harder for the IT team to identify genuine threats and more likely that the end users will use unsanctioned workarounds to get done what they need to do.
As ever in cybersecurity, every decision you make will have a trade-off elsewhere.
There are no catch-all solutions.
But it’s important to be aware of what these trade-offs are before you decide on the right product for you.
4. Pricing Model
Another crucial distinction; the pricing of your EDR will hugely vary based on the target market it’s aimed towards.
Unsurprisingly, the enterprise-focused products (CyberArk, Beyond Trust etc.) are the most expensive on the market.
But there are plenty of more cost-effective alternatives that still have a wide range of effective security controls.
It’s also important to be aware of the pricing model.
Generally, this is going to involve a monthly subscription based on the number of devices being monitored, employees being supported, or technicians using the EDR platform.
But some providers also offer flat rates based on the size of the organization. And most will also have a series of add-ons and additional products with their own independent pricing structures.
Sounds confusing, right? It gets worse: Many providers also use several of these pricing structures in combination, such as having different per-endpoint rates depending on the size of your organization or features being employed.
That situation only gets more complex as you add additional products.
When choosing your platform, therefore, it’s vital to keep an eye both on the total pricing and how easy it’s going to be to monitor, scale, and predict in the long run.
5. Complexity & Ease of Use

- Morten Kjaersgaard, Heimdal Chairman & Founder
Some cybersecurity tools are easier to use than others.
This probably won’t come as a surprise, but it’s a more important distinction than it may first appear.
The more enterprise-focused tools are generally designed to be managed and monitored by specialist cybersecurity teams.
This makes them much more difficult to use, particularly without training or managed support.
Secure your world with MXDR!
Amplify the power of your security operations with Heimdal's 24x7 fully managed MXDR solution here.
But for most conventional small and medium-sized organizations, in-house security support is likely to be restricted to a handful of generalist IT technicians. In these situations, the full bells-and-whistles approach can do more harm than good.
There’s no point having the most advanced cybersecurity functionality in the world if you can’t get to grips with the most basic tools.
Again the best approach here is to find reviews and testimonials from similar businesses as yours.
One product can be the absolute holy grail of cybersecurity for one customer and an absolute nightmare for another.
The right research can make a huge amount of difference here.
Every EDR provider has their pros and cons.
The market giants tend to have the most advanced features and the best telemetry data – but they’re also the most expensive and difficult to use.
As a rule of thumb, the opposite tends to be true for the lowest-priced products.
Success isn’t about choosing the ‘best’ product here – it’s about getting the right balance of priorities for your specific organization.
How to Implement Your EDR Product
The next step is to roll your EDR product out across the organization.
It’s important to think carefully about how you’re going to do this, since these platforms can take a while to set up and fine-tune.
Here are some tips for how to get it right.
1. Don’t Do Everything at Once
Setting up your new EDR tool isn’t an overnight job; it’s going to take some time to find the right balance of policies.
It’s important, therefore, to reduce the disruption on employees during this stage as much as possible.
The best place to start is to use ‘detect-only’ mode.
This means you can gather the information you need to design effective policies before actually implementing them, including what endpoints are in your environment, as well as the apps, services, and files they’re interacting with.
Once you’ve designed a set of policies, it’s helpful to first roll them out to a small group of pilot users, including technical specialists, business executives, or people with privileged access.
These people will be most affected by the policies and most knowledgeable of the reasons why they’re being implemented – so it’s helpful to start here.
This will let you test the impact these policies have on those using them before rolling them out across the organization – reducing unnecessary disruption to a minimum.
2. Let Users Know What to Expect
Even the most effective software in the world can fail if it’s not used properly.
This is particularly the case for the most complex EDR products – because they generally give IT teams more scope to customize and design their own policies.
It can therefore be worthwhile to ensure technicians are trained to understand the policies on offer and the best way to use them.
The more complex the technology, the more important this is.
But everyday employees also need to understand what’s happening, how it’s going to affect their workflows, and why it’s being implemented.
If the policies you’ve created are likely to cause disruption and frustration, it’s better they hear it from you first.
3. Set Up an Incident Response Process
If you’re using your EDR effectively, you should set up automated policies to lock down high-risk activity as soon as it’s detected.
But beyond that, it’s important to also have a clear idea what the next stages are going to be after both a successful and unsuccessful attack.
Even if the immediate threat has been stopped, your priority is going to be to assess the scope of the damage, identify if there’s another path or account the hacker can take, and work out how likely it is that another attack of the same type can occur.
While the EDR tool can give you the information to make these decisions, it’s going to require a person with a good knowledge of your IT environment to analyze the data and make a qualitative assessment of the risk.
That’s why most organizations over a certain size (particularly those with customer-facing digital services) will have specialists on hand 24/7 to respond to these security incidents.
Read more: How to set up an incident response team by Heimdal’s Machine Learning Research Engineer, Valentin Rusu.
Set Your EDR Implementation Up for Success with Heimdal

- Andrei Hinodache, Cybersecurity Community Leader
If there’s one thing you should take away from this article, it’s this: The success of your EDR strategy is hugely dependent on the product you choose and how well-suited it is to your business.
But there’s also one other key factor that it’s important to consider.
Even the most expansive EDRs are still just that.
Generally, you’ll need to combine them with any combination of email security tools, privileged access management software, SIEMs, and other products to get the full cybersecurity coverage.
But the more licenses and disconnected products you combine, the less effective your overall security posture is going to be.
There’s no point having one tool to protect privileged data and another to protect the endpoints being used to access it.
Instead, it’s important to get as much functionality as possible under one license.
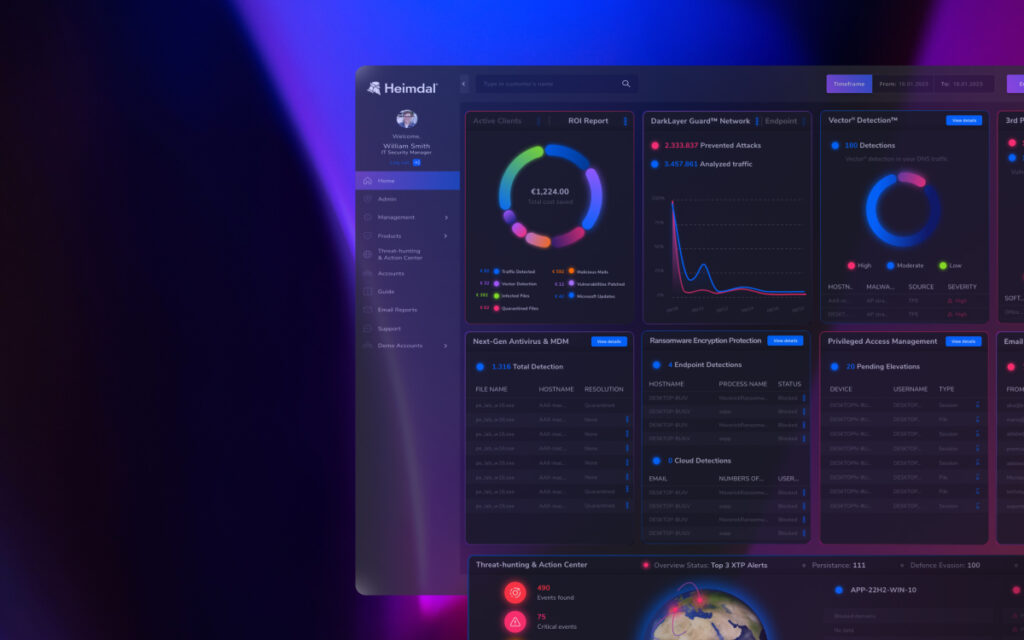
That’s what Heimdal offers. Instead of stringing together multiple complex and siloed products, you get access to a single, comprehensive cybersecurity platform, including:
- Network security;
- Endpoint security;
- Vulnerability management;
- Privileged access management;
- Email & collaboration security;
- Threat hunting;
- Unified endpoint management.
Here’s a detailed product demo for you to see for yourself:










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








