Contents:
DNS records or resource records (RR) contain various types of data about domain names and IP addresses. They are stocked in DNS databases on authoritative DNS servers.
DNS records offer information about what IP address is associated with what domain, for example. When you type, let’s say, www.example.com on your mobile, the device sends further a DNS query. The DNS resolvers pass on the query until they identify the server that keeps the DNS records for www.example.com.
The records are a collection of text files written in DNS syntax, with a specific TTL. TTL is short for time-to-live and refers to how frequently the DNS server refreshes the record. You can use the NSlookup command to find DNS records for a website.
For users to reach a website by its domain name, a domain must have at least the essential DNS records.
Key takeaways
- not all DNS records are public
- hackers can alter records for malicious activities
- some record types are used by DNSSEC for DNS security: DNSKEY, DS, NSEC, RESIG
- to find the available records of a domain name you can use the nslookup command
Most Common Types of DNS Record
A record
A is for „address”, and this record is the most frequently used DNS record type. A records are usually used for IP address lookups. They translate domain names that humans understand into IP addresses that machines can operate with.
DNS-based Blackhole Lists (DNSBL) rely on A records so that mail servers can spot & block emails from known spammers.
AAAA record
While A records list the IPv4 ones, AAAA records contain the IPv6 addresses. IPv6 replaced the old IPv4 address system because the initial one did not offer enough combination possibilities. IPv6 addresses are 128 bits long and can cover the ever-growing request.
CNAME record
A Canonical Name (CNAME) Record creates an alias from one domain name to another domain name. This type of DNS record does not provide an IP address.
CNAMEs are used for providing a distinct hostname for certain network services, like email, or FTP. They also point that hostname to the root domain. Another usage of CNAME records is pointing from different websites that belong to the same company to a primary site.
Detour Dog Attacks Explained by Ethical Hacker Glenn Wilkinson and Former Cybercrime Detective Adam Pilton
byu/liv_v_ei inHeimdalSecurity
MX record
MX records direct mails to email servers. They show how emails should be directed in compliance with the Simple Mail Transfer Protocol (SMTP). MX records must always point to another domain, not to an IP address, just like the CNAMEs.
TXT record
They enable the admin to enter text into the DNS. TXT records are often used for email security, even if they were not initially designed for this. Currently, admins use DNS TXT records to prevent email spam and check domain ownership.
When spammers try to spoof the domains from which they send the messages, TXT records work as a part of various email authentication methods. They help an email server check if the message comes from a trustworthy source.
If they properly configure TXT records like SPF, DKIM, and DMARC, admins can mitigate domain spoofing and also track this kind of activity.
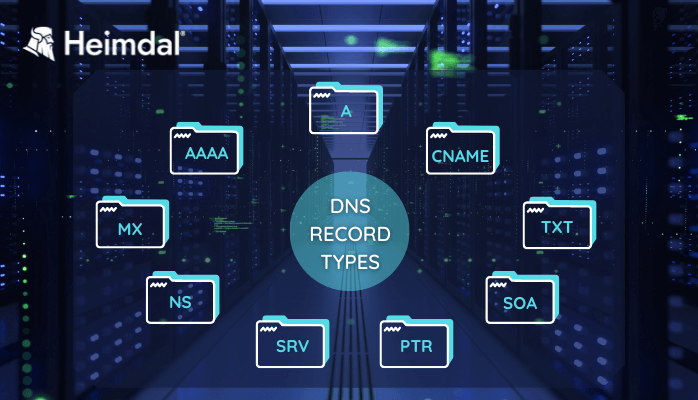
Most common DNS record types
NS record
The nameserver record (NS) points to the authoritative DNS server of a certain domain. It tells you where to find a domain`s IP address.
SOA record
Start of Authority (SOA) records contain administration data about a domain or a zone. Here you can find out what is the email address of the admin, when was the last update, and how often should the server refresh. SOA records are employed in zone transfers, a process that sends DNS record data from a primary nameserver to a secondary one.
SRV record
Service (SRV) records identify a host and port for a certain service, like instant messaging, for example. Emails and instant messages enter a device through the same Internet connection, but they are further directed to different ports. Ports also have assigned numbers, like IP addresses.
PTR record
DNS pointer records reveal what domain name is associated with an IP address. They are used in reverse DNS lookups.
PTR records are also used in spam prevention. Email filters check the domain names of email addresses to see if their associated IPs belong to legitimate email servers.
Record Types Used for DNSSEC
The Domain Name System was not designed to face security challenges. At the time, there was no need for system admins to think about DNS securing. But when threat actors developed a series of DNS attack types, admins created a solution we now call DNSSEC.
DNSSEC is short for Domain Name System Security Extensions. It ensures the security and confidentiality of data by signature checking. You can read more about how DNSSEC works here. Now let’s focus on the DNS record types DNSSEC uses:
DNSKEY
This DNS record type was created to help enforce cryptographic signatures. The DNSKEY record contains a public signing key that resolvers use to check DNSSEC signatures in RRSIG records.
DS
Along with the DNSKEY records, DNSSEC resolvers also use Delegation Signer records (DS) to check the authenticity of DNS records. Admins use Delegation Signer records to secure delegations. DS records have a key tag that helps identify the referenced DNSKEY record.
NSEC
NSEC is short for „Next Secure” and it is part of DNSSEC. Resolvers use this record to check that a record does not exist.
RRSIG
The Resource Record Signature stores the digital signatures needed to authenticate records in compliance with DNSSEC.
Can Hackers Change DNS Records?
Unfortunately, yes, hackers can mess up DNS records. This results in several DNS attack types.
If threat actors compromise a DNS server and manage to change DNS records, they can redirect DNS queries to forged sites. This is one of the common types of DNS hijacking and the technique is called “Rogue DNS Server”.
If they succeed altering DNS records, hackers can redirect traffic to their malicious infrastructure. The activity will mimic normal trusted network communications. Unless you carefully monitor DNS traffic, you might not spot the forgery in time.
Another type of attack is the Man-in-the-Middle (MITM). In this case, threat actors interfere with the communication between a user and a DNS server. They offer IP addresses pointing to malicious sites, instead of the ones the user was actually looking for.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
How Can Heimdal Help Prevent DNS Attacks on Your Company?
Heimdal® is your company’s best ally against cyberthreats, DNS attacks included. Heimdal®’s Threat Prevention – Endpoint solution provides you with DarkLayer Guard, the most advanced endpoint DNS threat hunting tool in the world. Threat actors never lack creativity, so it`s vital for your organization`s cybersecurity to keep up with top tech solutions.
DarkLayer Guard – Endpoint creates a local DNS server that works as a filtering engine before it resolves a DNS query. The DarkLayer Guard DNS server highjacks the DNS IP Address on the active Network Adapter(s) so it can scan for malicious websites, servers, ads, etc. It literally eliminates communication that could be leveraged to install malware or launch a cyberattack.
The filtering process takes place extremely fast, so it doesn’t impact your internet connection speed. If a user stumbles upon a forged site, he will simply not be able to load it. The filter will immediately block all communication with that item.
Wrapping Up
DNS records contain all this vital information, so we could rightfully say they are at the very core of the DNS infrastructure. Being aware of how that works helps you understand better why DNS security is so important. And it can also help you take a more educated choice when deciding what cybersecurity solution to employ.
According to the 2022 Global DNS Threat Report, 88% of organizations suffered a DNS attack during the past year. The researchers estimated an average cost of $942,000 for each one of the attacks, but the numbers could be even bigger.
So, keep safe from this kind of event and make sure you choose the best DNS security solution there is. DarkLayer Guard uses cutting-edge technology, is extremely versatile, and is always one step ahead of threat actors. All this makes the Heimdal® solution the best cybersecurity choice for any large enterprise.
DNS records FAQs
How can I check DNS records for a domain name?
A DNS lookup enables you to see available DNS records of a domain name. To query DNS records you can use an online DNS lookup tool, like nslookup.io, dnschecker.org, etc. The nslookup command line is also built-in operating systems like Windows, MacOS and Linux.
How do I find out what mail server does a certain email address use?
Do a DNS lookup to query the MX records of the email address’ domain.
Are Alias records different from CNAME records?
Both Alias and CNAME records point one domain name to another. The main difference is that you can use Alias records at the root domain, while CNAME records are for subdomains only.
Additionally, Alias records allow load balancing, as they can point to multiple IP addresses or hostnames.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security