Contents:
A DNS leak is a vulnerability that discloses DNS requests to the Internet Service Provider (ISP) or a third-party server despite using a VPN.
Virtual Private Networks (VPNs) should hide a user’s browser activity and details like IP address and location. When using a VPN, no one, not even your ISP, should be able to see any of your web searches.
Threat actors can use DNS leaks to track your activity, eavesdrop on DNS traffic, and redirect you to a malicious website.
In this article, I’ll explain what causes a DNS leak, how it can affect you, and how to spot it. Further on, I’ll show you how to prevent leaking DNS traffic and avoid having your assets at risk.
Key takeaways
- DNS leaks can lead to social engineering, phishing, malvertising, malware deployment, or ransomware attacks
- run a DNS leak test regularly to assess your network’s privacy level
- make sure your VPN provider uses private DNS servers
- misconfigurations or malware can cause DNS queries to exit the VPN tunnel and cause DNS leaks
How Does a DNS Leak Work?
The Domain Name System (DNS) maps domain names to IP addresses. Here’s what happens when you type example.com into your browser.
First, the browser will contact a DNS server and request the unique IP address of the site. Then, the DNS server provides the IP address. The browser uses it to connect to the web server hosting example.com. Finally, the server sends the website’s data back to the browser and you can view and interact with the site.
If you use default DNS settings, your ISP or anyone with legal or illegal access to the DNS server can see which websites you want to visit. Ideally, using a Virtual Private Network (VPN) helps you keep your DNS requests private.
This means your DNS queries are encrypted, pushed through a VPN tunnel, and sent through the VPN service’s DNS servers. Thus, not even your ISP can track your online activities.
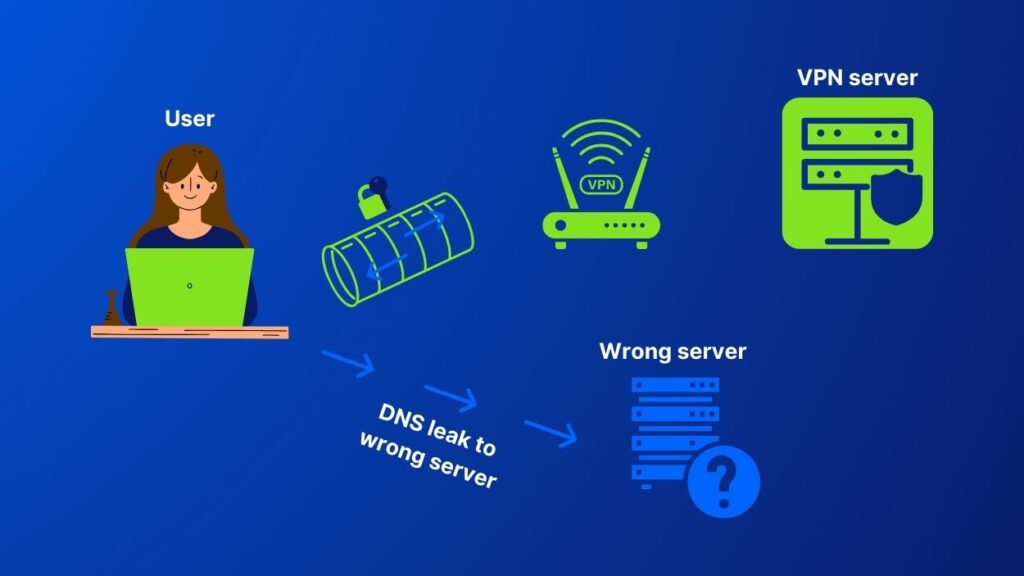
However, using a VPN is not 100% safe. Sometimes, VPN servers leak DNS requests. Instead of encrypting DNS queries and routing them through the VPN server, your device sends them to another DNS server. This process is called a DNS leak and can raise privacy issues.
Various reasons such as incorrect configuration, or your VPN service lacking its own DNS servers can expose your DNS traffic to third parties.
What Causes a DNS Leak?
When you connect to a VPN, all your internet traffic passes through an encrypted tunnel to the VPN server. In case of a DNS leak, your DNS requests evade routing through the VPN tunnel. At this point, the ISP or a malicious third party can see your entire online activity. Why does this happen?
Here are five reasons that cause DNS leaks:
Misconfigured VPN
Misconfigured VPNs are a common cause of DNS leaks. For example, a VPN could fail to reroute your DNS query to their private server. Instead, they would send them to your ISP’s default DNS servers or an unknown one. This issue is common with users who switch frequently between networks.
Choose carefully your VPN service provider. Some simply don’t have DNS servers of their own.
Lack of IPv6 support
The vast majority of VPN services only support IPv4. This means they can’t process requests made from or received by IPv6 devices. Not all VPNs support IPv6, so the user’s DNS query will be sent outside the secure tunnel.
Teredo Feature
To address the IPv6/IPv4 gap, Microsoft has introduced Teredo Technology. But since Teredo is a tunneling protocol, it can also bypass a VPN’s encrypted tunnel and cause a DNS leak.
Transparent DNS Proxies
When ISPs discover that their customers have changed their DNS Server settings to a server other than their own, they can use transparent DNS proxies to force customers back. The transparent server terminates the users’ sessions and redirects them to the ISP’s DNS server. Does this sound illegal or abusive? Not necessarily. Some use transparent proxies for censorship, but there are also other reasons someone would use them:
- content filtering, to keep kids from accessing harmful websites or employees spending too much time on social media during working hours
- prevent DDoS attacks by spotting and blocking suspicious DNS queries. If you’re only active on the US market and all of a sudden, you’re getting a large amount of traffic from Russia, this should trigger an alert.
Windows Smart Multi-Homed Name Resolution (SMHNR)
This smart feature activates on Windows 8 and later. SMHNR tends to send the request to all of the available DNS servers. It uses the first that responds, most likely your ISP’s DNS server. Which means you’ll get a DNS leak.
Why Are DNS Leaks Dangerous?
When your DNS leaks, your computer is essentially broadcasting which websites you’re trying to visit. This means your DNS queries are no longer private. Whoever intercepts them will know exactly what topics and website’s you’re interested in. Also, unauthorized third parties can use them to track your browsing habits.
A leaking DNS might enable a potential attacker to see which websites you are visiting. Further on, they can use that information to redirect you to malicious websites. Also, they can correlate the ‘leaked’ information with other data to perform phishing attacks, deploy malware, or plot ransomware attacks.
They can even use it for social engineering attacks or malvertising. A DNS leak gives hackers enough data for them to learn a lot about your interests, habits and connections.
DNS leaks can also cause computer performance issues. They can make your internet connection slower, as your computer will be constantly sending out DNS requests. Additionally, it can make it difficult to access certain websites, as your computer may be trying to connect to the wrong DNS server.
How to Prevent a DNS Leak?
You can prevent DNS leaks across your infrastructure if you follow a few simple DNS security best practices:
- Use a reputable, trustworthy VPN service that encrypts all traffic and routes it through a private server. Your VPN service provider owning private servers makes it less likely to leak DNS queries. Choose a VPN vendor that offers a DNS leak check. This way you’ll be able to see the status of your IP address, connection and DNS server.
- Configure your VPN to use the private DNS servers that your VPN service provides.
- Disable IPv6 on your computer or router if you don’t necessarily need it. As I explained above, the transition to IPv6 can sometimes cause DNS leaks.
- Use a Firefox or Chrome extension such as DNSCrypt to encrypt and secure your DNS requests
- Use completely anonymous web browsers, like Tor Browser. Not only do they hide the user’s identity, but they also don’t require any DNS configuration on the operating system.
- Run occasional tests with online tools like dnsleaktest.com to check for leaks and make sure your security measures work as intended.
How Can Heimdal® Help?
DNS leak protection is critical, if you want your computer data to remain private.
Even if you are experiencing DNS leaks, using a trustworthy VPN service is still a great option to protect your privacy. However, to keep your infrastructure safe, you need a threat prevention product.
A DNS traffic filtering solution is your best bet for detecting and stopping malicious attacks targeting your DNS traffic.
This is where we come to the rescue – with Heimdal® DNS Security, a product designed to protect both endpoints and networks by detecting and preventing future threats.
Heimdal’s DNS filtering engine uses AI and machine learning to detect unknown malicious domains. It scans and terminates communication with potentially harmful URLs and processes in DNS, HTTP, and HTTPS traffic. This means that even in case of an infection, the threat actor won’t be able to exfiltrate data.
Once it spots a suspicious domain, Heimdal’s DNS security tool will immediately block it. So, communication to and from the Command-and-Control server, will no longer be possible.
Our software:
- stops man-in-the-middle attacks
- discovers zero-day exploits
- fights data leakage
- prevents security breaches or network infections
How? By screening all network packages based on the origin and destination of DNS requests and preventing malicious inbound or outbound communication.
Heimdal® DNS Security also enables you to perform category-based web page blocking, ensuring that your private information is secure regardless of where you or your employees (if you’re an organization) choose to work from. It works in tandem with any existing antivirus product to block malicious domains as well as communications to and from C2 centers and other malicious servers.
Heimdal® DNS Security Solution
Wrapping Up
A DNS leak can be a serious issue, as it can allow third parties to intercept and eavesdrop on your traffic. If you’re concerned that you might have a DNS leak, you can first run a DNS leak test to check. But keep in mind that even with a VPN service on, you are not one hundred percent safe so adding multiple layers of proactive protection to your system would be the best choice to ensure you and your organization’s cyber defense.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security