Contents:
Cactus Ransomware claims responsibility for the January 17th Schneider Electric data breach. Schneider Electric confirms hackers got access to their Resource Advisor cloud platform.
The French-based energy giant says the attack only hit their Sustainability Business division. The platform holds data belonging to more than 2000 companies worldwide.
For the moment, there’s no impact on the company’s other entities.
From a containment standpoint, as Sustainability Business is an autonomous entity operating its isolated network infrastructure, no other entity within the Schneider Electric group has been affected.
Source – Schneider Electric’s press release
Schneider immediately mobilized their incident response team to contain the attack. This is not the first time they are targeted with ransomware. In June 2023, the Cl0p threat group added them to their dark web leak site as victims of MOVEit attacks.
Schneider Electric data breach impact
Due to network segmentation, the Cactus ransomware attack only impacted Schneider’s Sustainability Business Division.
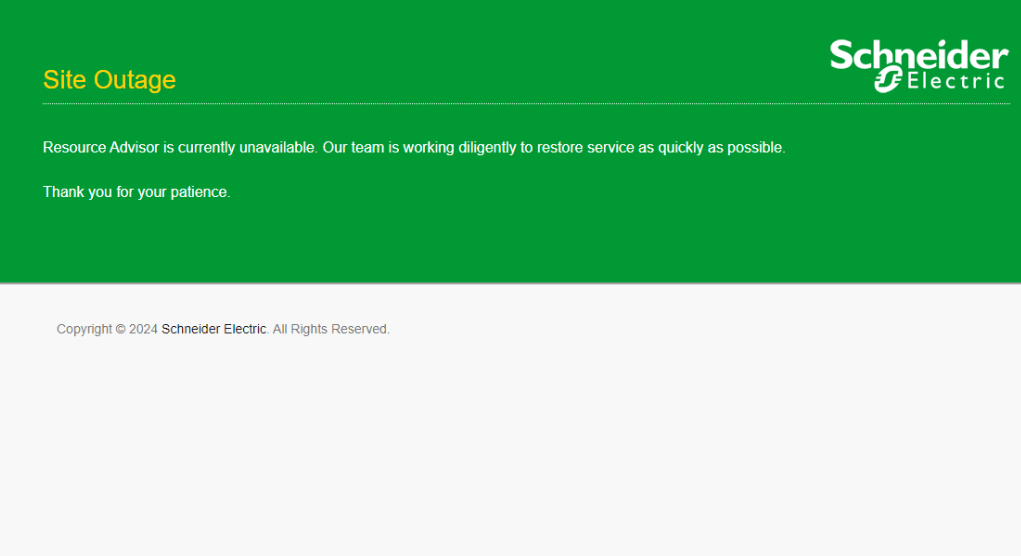
The Resource Advisory platform manages energy and sustainability data for more than 2000 companies worldwide. According to Bleepingcomputer.com, Allegiant Travel Company, Clorox, DHL, DuPont, Hilton, Lexmark, PepsiCo, and Walmart are on Schneider Electric’s customer list.
The energy giant confirmed that the hackers did get access to data. The Cactus ransomware gang said they’ve got hold of terabytes of corporate data. The plan is to leak it online if the company refuses to pay ransom.
Schneider Electric has informed the affected customers. They’ve also announced working on restoring the platform, which is still unavailable for the moment.
Cactus ransomware TTPs and prevention measures
Cactus ransomware has been operational for less than a year. However, they’ve already added over 80 companies on their data leak site.
According to security researchers, the group relies heavily on exploiting unpatched known vulnerabilities for initial access. Read more about how Cactus exploits VPN flaws to breach their targets’ networks.
Then they move further into the system, steal valuable data and encrypt files.
In order to prevent a Cactus ransomware data breach, apply these prevention measures:
- Evaluate your digital assets and patch vulnerabilities that pose a high risk to your business
- Use DNS filtering to prevent inbound and outbound malicious communication
- Use end-to-end encryption to protect sensitive data
- Make sure everyone in your company understands and uses strong passwords
- Enforce a clear PAM policy to limit unnecessary access to databases
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







