Contents:
Researchers warn Cactus Ransomware exploits VPN Flaws to compromise networks and encrypts itself to avoid detection.
The new ransomware strain targets large commercial entities that use remote access services and scans after unpatched vulnerabilities for initial access. According to the ransom note, Cactus plans to reveal the stolen data unless the victims contact them.
How Is Cactus Ransomware Different?
Much like other ransomware, Cactus also employs double extortion tactics to steal sensitive data prior to encryption. However, until now it doesn`t seem to use a data leak site.
Unlike other operations, Cactus uses file encryption to evade antiviruses. To that end, the adversary uses a batch script to obtain the encryptor binary, also employing the notorious 7-Zip compression tool.
After extracting the binary, the hacker eliminates the initial ZIP archive. Consequently, the ransomware binary is run with a certain parameter that makes threat detection harder.
When getting ready a file for encryption, Cactus changes its extension into ”.CTS0”. After the encryption process succeeds, the extension changes to .CTS1.
Cactus Ransomware Way of Working
Researchers claim there are three main ways of execution: setup (-s), read configuration (-r), and encryption (-i).
The -s and -r arguments allow the threat actors to set up persistence and store data in a C:\ProgramData\ntuser.dat file that is later read by the encryptor when running with the -r command line argument.
For the file encryption to be possible, though, a unique AES key known only to the attackers must be provided using the -i command line argument.
This key is necessary to decrypt the ransomware’s configuration file and the public RSA key needed to encrypt files. It is available as a HEX string hardcoded in the encryptor binary.
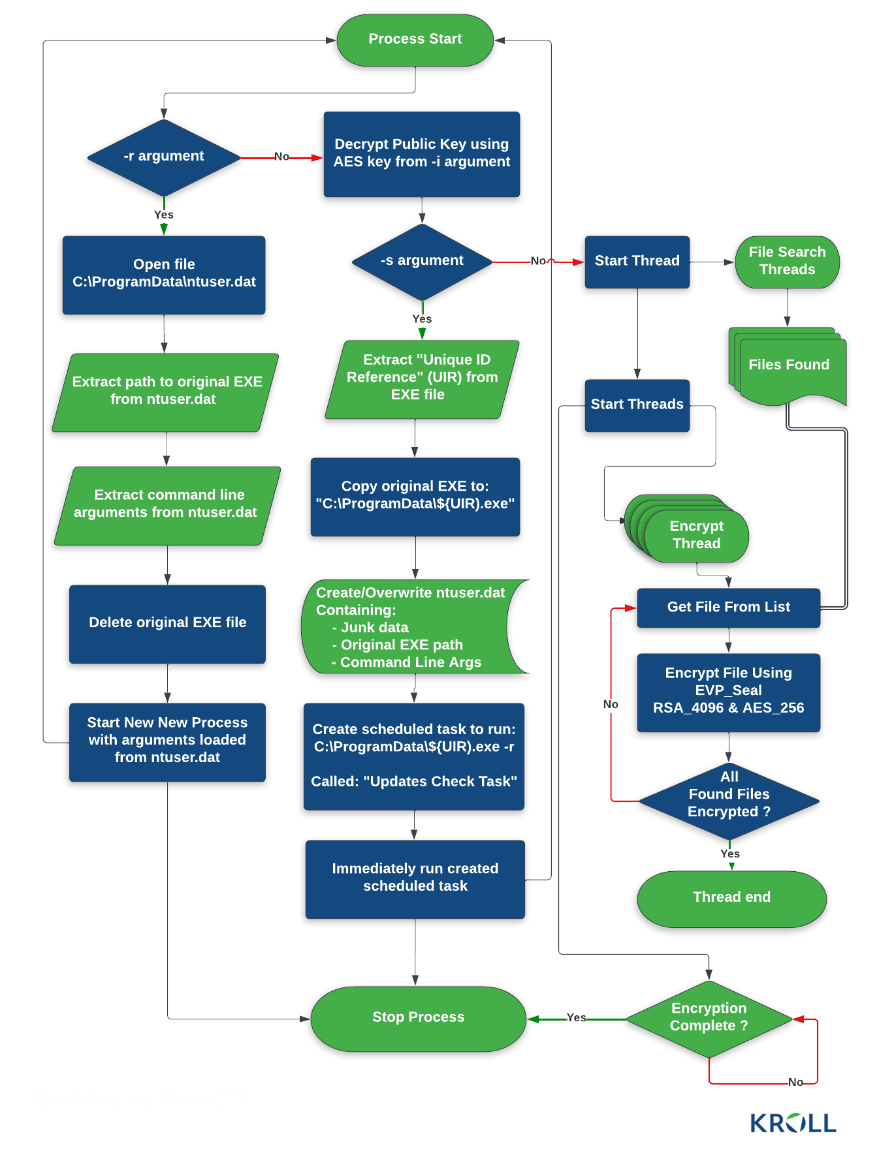
Additionally, researchers revealed the malware uses multiple extensions for the files it targets, as related to the processing state.
Once they gain initial access to the network, hackers use a scheduled task for persistent access. They employ an SSH backdoor they will later be able to reach from a command-and-control server.
According to the cyber researchers, Cactus used SoftPerfect Network Scanner to pick its targets. For in-depth reconnaissance activities, threat actors used PowerShell commands to list endpoints, ping remote hosts, and identify user accounts.
Cactus ransomware also employed a custom variant of the open-source PSnmap Tool, a PowerShell equivalent of Nmap. Cactus attacks also used Cobalt Strike and the Chisel network tunneling tool, as well as other legitimate remote monitoring and management software: AnyDesk, Splashtop, SuperOps, etc.
Prevention Measures Against a Cactus Ransomware Attack
Data theft is a common goal for hackers, since successful ransomware attacks bring them money.
Just like any other ransomware threat actor, these ones also threaten victims with data leakage unless they get paid.
At the moment there is no public information about the ransoms that Cactus demands from its victims but BleepingComputer has been told by a source that they are in the millions.
According to the ransom note, even if they did not create a leak site, like other hackers do, the Cactus Ransomware authors do plan to publish the stolen data.
In order to avoid being a victim of Cactus ransomware attacks, cybersecurity specialists recommend:
- Network monitoring – watch out for big data exportation tasks,
- Run penetration testing programs constantly, to find in time potential vulnerabilities in your network.
- Enforce DNS filtering in order to block communication with and data exfiltration to C&C servers,
- Never miss a patch. Automated patch management is the best choice for enterprises with hundreds of endpoints to protect.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









