Contents:
ABB, a leading provider of electrification and automation technology, has been hit by a Black Basta ransomware attack, which has reportedly affected business operations.
As part of its services, ABB develops industrial control systems (ICS) and SCADA systems for manufacturers and energy suppliers. The company has approximately 105,000 employees and is expected to generate $29.4 billion in revenue in 2022. Volvo, Hitachi, DS Smith, the City of Nashville, and the City of Zaragoza are among the company’s customers.
According to the company’s website, “ABB operates more than 40 U.S. based engineering, manufacturing, research, and service facilities with a proven track record serving a diversity of federal agencies.” These agencies include the U.S. Army Corps of Engineers and the U.S. Departments of Defense, Transportation, Energy, the Coast Guard, and the Postal Service.
What Happened?
On May 7th, ABB fell victim to a ransomware attack led by the Black Basta, a ransomware gang that has been active since April 2022.
The breach affected their Windows Active Directory and hundreds of their devices. Anonymous sources confirmed for Bleeping Computer that the attack has caused significant disruption to ABB’s operations and projects, and impacted its factories.
After initially declining to comment on the news, ABB sent the following statement to Bleeping Computer:
ABB recently detected an IT security incident that directly affected certain locations and systems. To address the situation, ABB has taken, and continues to take, measures to contain the incident. Such containment measures have resulted in some disruptions to its operations which the company is addressing.
The vast majority of its systems and factories are now up and running and ABB continues to serve its customers in a secure manner. ABB continues to work diligently with its customers and partners to resolve this situation and minimize its impact.
Black Basta Ransomware
The infamous Black Basta ransomware gang stepped onto the stage in April 2022, with their ransomware-as-a-Service (RaaS).
In no time at all, they had already begun conducting double extortion attacks on multiple corporate victims.
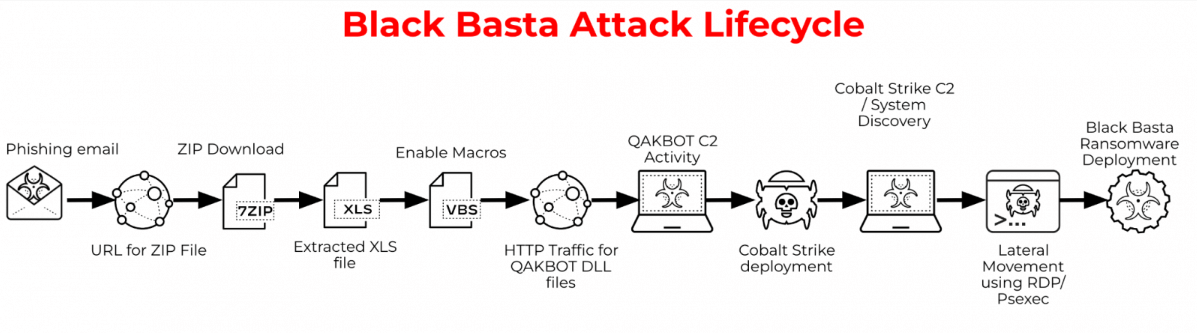
By June 2022, Black Basta had partnered with the QBot malware operation (QakBot) dropping Cobalt Strike on infected devices. From there, the hacker group used it to gain access and spread through corporate networks.
They also developed a Linux encryptor aiming at VMware ESXi virtual machines running on Linux servers, similar to other ransomware threats targeting businesses. Their links to the financially-motivated cybercrime organization FIN7 (Carbanak) have been noted by security researchers.
Since its appearance, Black Basta has maliciously infiltrated entities such as American Dental Association, Sobeys, Knauf and Yellow Pages Canada.
Most recently they attacked Capita – UK’s largest outsourcing company, and started leaking stolen info.
Technical Analysis
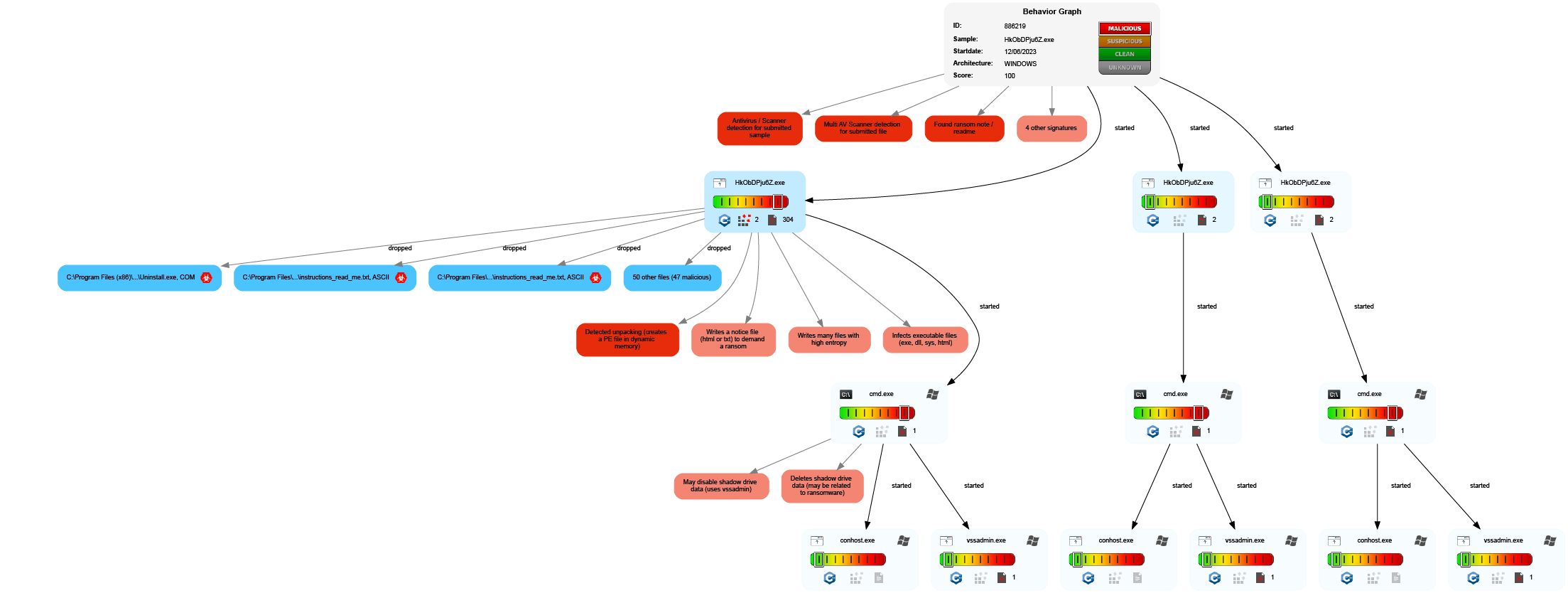
Advanced forensics performed on FOSO BlackBasta sample revealed the following information.
Behavioral analysis (via Hatching Triage)
- Interacts with shadow copies;
- Modifies registry class;
- Suspicious use of AdjustPrivilegeToken;
- Suspicious use of WriteProcessMemory;
- Uses Volume Shadow Copy service COM API;
- Drops file in Program Files directory;
- Adds Run key to start application;
- Modifies extensions of user files;
- Deletes shadow copies;
- Renames multiple (3088) files with added filename extension.
In-depth BlackBasta lifecycle analysis, by process-calling and associated operations (via Joe Sandbox)
- Detected unpacking (creates a PE file in dynamic memory);
- Found ransom note / readme;
- Found Tor onion address;
- Infects executable files (exe, dll, sys, html);
- Machine Learning detection for sample;
- May disable shadow drive data (uses vssadmin);
- Multi AV Scanner detection for submitted file;
- Writes a notice file (html or txt) to demand a ransom;
- Writes many files with high entropy.
Signature (via CAPE Sandbox)
- SetUnhandledExceptionFilter detected (possible anti-debug);
- Possible date expiration check, exits too soon after checking local time;
- A process attempted to delay the analysis task;
- Dynamic (imported) function loading detected;
- Creates RWX memory;
- Uses Windows utilities for basic functionality;
- Exhibits possible ransomware or wiper file modification behavior: mass_file_deletion;
- Likely virus infection of existing system binary;
- Attempts to delete or modify volume shadow copies;
- Harvests credentials from local FTP client softwares;
- Uses suspicious command line tools or Windows utilities;
- Yara rule detections observed from a process memory dump/dropped files/CAPE.
MITRE ATT&CK Matrix for BlackBasta (via Any.Run)
| Initial Access | Execution | Persistence | Privilege Escalation | Defense Evasion | Credential Access | Discovery | Lateral Movement | Collection | C& C | Exfiltration | Impact |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Command & Scripting Interpreter | N/A | N/A | N/A | N/A | Unsecured credentials | Software discovery | N/A | N/A | N/A | N/A | Data encryption |
| Windows Command Shell | Credentials in files | Query register | Inhibit system recovery. | ||||||||
| Steal web session cookies | System information discovery | ||||||||||
| Credentials from password stores; | |||||||||||
| Credentials from web browsers |
Top 10 Memory Dumps (via Joe’s Sandbox)
| Base Address | Type | Protect |
|---|---|---|
| 34E0000 | direct allocation | page read and write |
| 3220000 | direct allocation | page execute and read |
| 3600000 | direct allocation | page execute and read |
| 14EC000 | heap | page read and write |
| 1535000 | heap | page read and write |
| 14A1000 | heap | page read and write |
| 169B4100000 | trusted library allocation | page read and write |
| 148E000 | heap | page read and write |
| 150D000 | heap | page read and write |
| 153D000 | heap | page read and write |
Measures to Prevent Ransomware
To protect against ransomware attacks like Black Basta’s, cyber security specialists recommend the following measures:
- Network monitoring, to keep an eye out for large data exfiltration attempts.
- Implement DNS filtering to prevent communication with and data exfiltration to C&C servers.
- Enforce an anti-ransomware encryption solution – to stop unauthorized encryption attempts.
- Never skip a patch. For companies with hundreds of endpoints to secure, automated patch management is the best option.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
Heimdal® DNS Security Solution


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security