Contents:
Security research and consulting firm SRLabs exploited a vulnerability in the encryption algorithm of a specific strain of Black Basta ransomware to develop and release a decryptor tool named Black Basta Buster.
This tool, released in response to the activities of a prolific cybercriminal gang, can decrypt files affected by the malware.
However, the decryptor’s effectiveness varies; it may only partially recover some files encrypted by the gang, with limitations on the extent of recovery depending on the plaintext requirements and the size of the files, as noted by the researchers.
The Black Basta decryptor, as described on SRLabs‘ GitHub page, allows for the recovery of individual files if the plaintext of 64 encrypted bytes is known.
However, merely knowing 64 bytes is not enough; these known plaintext bytes must be in a part of the file that the malware targets for encryption. This recovery is more feasible for specific file types, such as virtual machine disk images, where knowing 64 bytes of plaintext in the correct position is possible.
Additionally, the decryptor can restore files ranging in size from 5,000 bytes to 1 gigabyte. For files larger than 1GB, the first 5,000 bytes will be irretrievable, but the rest of the file can be recovered.
It’s important to note that this decryptor targets a specific vulnerability in a variant of the Black Basta ransomware. Organizations affected after the group patched this vulnerability in mid-December, as reported in a Jan. 2 Malwarebytes blog post, are unlikely to find success using this tool for decryption.
Despite these limitations, the decryptor may still benefit at least 153 victims. These victims had their data leaked on Black Basta’s Dark Web site when the decryptor was effective, making them potential candidates for file recovery using this tool.
Exploiting Encryption Vulnerabilities
In April 2022, the ransomware group Black Basta emerged as a dynamic and double-extortion operator. It attacked over 90 targets within five months with a complex encryption method.
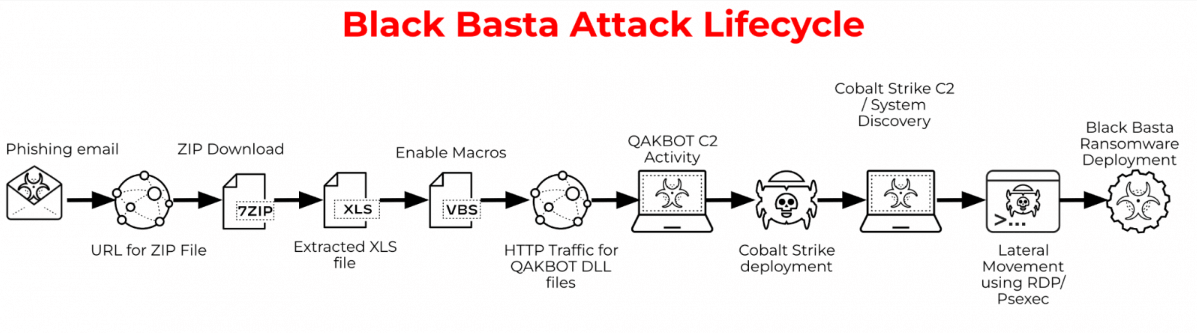
Each victim received unique binaries, a strategy highlighted by Trend Micro. Researchers link Black Basta to FIN7, a cybercrime group believed to have stolen over $1.2 billion since 2012.
The Black Basta Buster tool exploits a weakness in the basic ChaCha keystream used by Black Basta. This keystream XOR-encrypts 64-byte segments of the targeted files, as detailed on SRLabs’ GitHub.
Here’s how Black Basta’s ransomware works: It encrypts the first 5,000 bytes of a file. Then, it repeatedly uses the same 64 bytes for XOR encryption of subsequent segments.
Here’s a webinar snippet where our Cyber-Security and Heimdal® Product Expert & Head of Pre-Sales showcase how Black Basta ransomware encrypts devices and does a quick analysis on it.
The initial 5,000 bytes are securely encrypted by Black Basta, leading to their loss in larger files. However, the following chunks are less secure, allowing plaintext recovery.
SRLabs
Recovery chances are highest for virtualized disk images. The researchers point out that their data partitions and filesystems usually begin further into the file.
For organizations using the decryptor, locating a zero sequence in the file is the simplest method to determine recoverability.
Decrypting large files without substantial zero-byte segments [data-less strings] is feasible but requires an unencrypted version of the file. Often, this negates the purpose of decryption.
However, in rare situations, a previous file version might meet decryption requirements without containing the desired information.
To prevent the need for ransomware decryption, organizations should strive to avoid breaches.
This means blocking typical attacker entry points by promptly fixing vulnerabilities and disabling or strengthening remote access to thwart ransomware threats.
Additionally, organizations should deploy endpoint security software to block intrusions and use endpoint detection and response (EDR) and managed detection and response (MDR) systems to spot any unusual activities in case attackers infiltrate the system.

- End-to-end consolidated cybersecurity;
- Powered by the Heimdal XDR, Unified Security Platform
- Comprehensive enterprise security without any additional integrations
- 24x7 monitoring & prompt response delivered by our security experts
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security