Contents:
Security researchers at Sentinel Labs have analyzed the tools used by the Black Basta ransomware gang and uncovered evidence that links it to the financially motivated group FIN7, aka Carbanak.
The researchers found signs that a developer for FIN7 also authored the EDR (Endpoint Detection and Response) evasion tools used exclusively by Black Basta since June. Further evidence links the IP addresses and specific TTPs used by FIN7 in early 2022 which were seen months later in Black Basta attacks.
We assess it is highly likely the BlackBasta ransomware operation has ties with FIN7. Furthermore, we assess it is likely that the developer(s) behind their tools to impair victim defenses is, or was, a developer for FIN7.
Black Basta, has been attributed to a ransomware wave that has claimed over 90 organizations as of September 2022. However, as per the researchers, there have been no signs of its operators attempting to recruit affiliates or advertising RaaS (ransomware-as-a-service) on the underworld forums or crimeware marketplaces. This either means that gang cut out affiliates from the chain and deploys the ransomware through their own custom toolset or, on the contrary, they work with a close set of affiliates, potentially a private group.
Black Basta was observed deploying a custom EDR evasion tool used to displays a fake Windows Security GUI and tray icon which leaves users with the fake impression that Windows Defender is working properly, while in fact it has been disabled, along with EDR and antivirus tools.
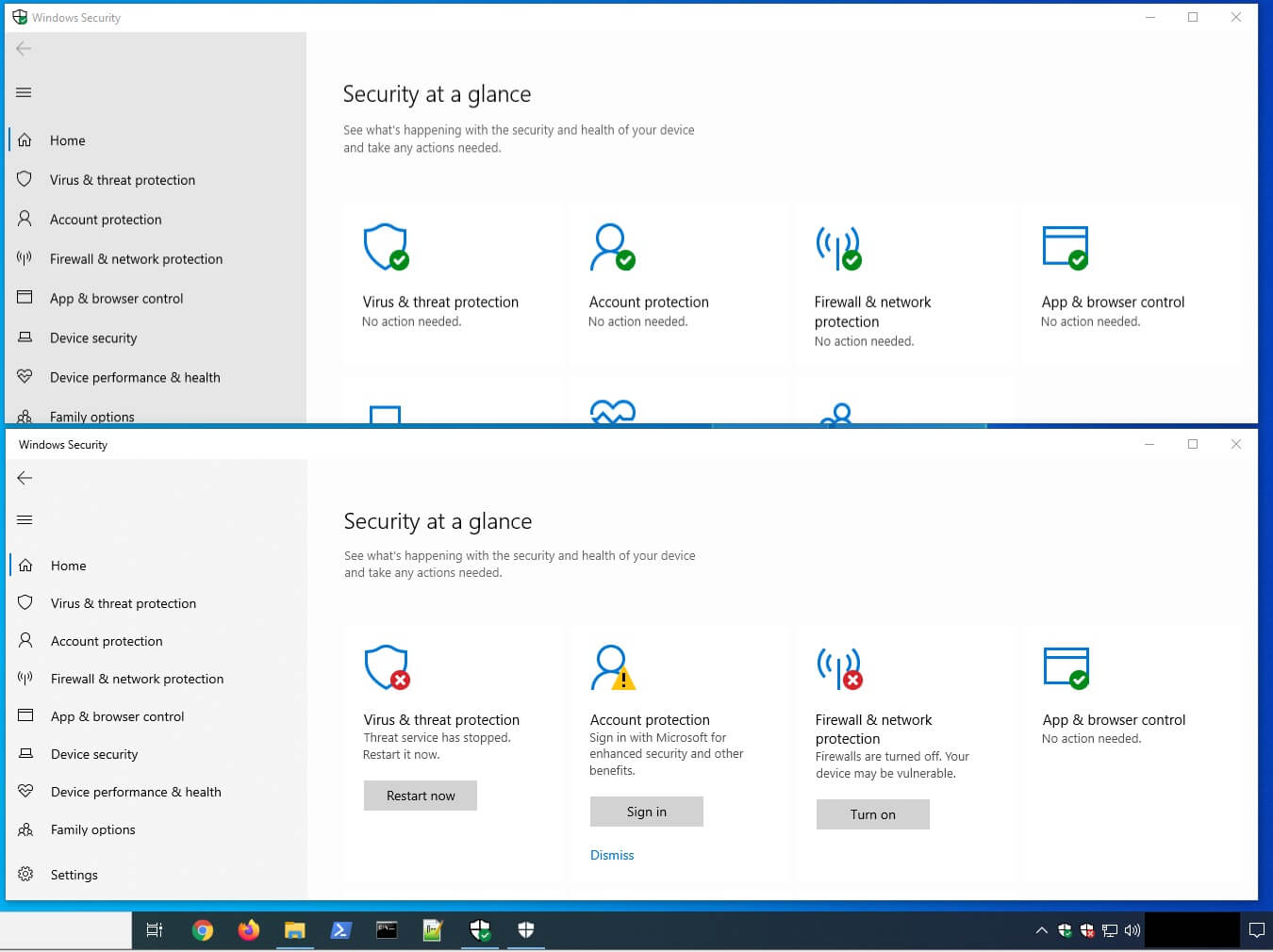
The fake Windows Security GUI WindefCheck.exe
Furthermore, SocksBot a backdoor specific to the FIN7 group has been discovered connecting to a C2 IP address belonging to pq.hosting, a hosting provider that is also used regularly by FIN7.
FIN7 Previous Activity
Active since 2013, FIN7 used Point of Sale (PoS) malware for financial fraud, only switching to ransomware two years ago, when they adopted a strategy that included their own RaaS, Darkside.
In 2021, Andrii Kolpakov, the supervisor of the FIN7 hacking group had been sentenced to seven years in prison, while this year Denys Iarmak, another member and “pen tester” for the hacking group, received five years in prison for breaching victims’ networks.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









