Contents:
Cybersecurity experts have released an analysis which links threat actors behind the Black Basta ransomware group to the use of the Qakbot trojan in deploying the Brute Ratel C4 framework as a second-stage payload in recent attacks.
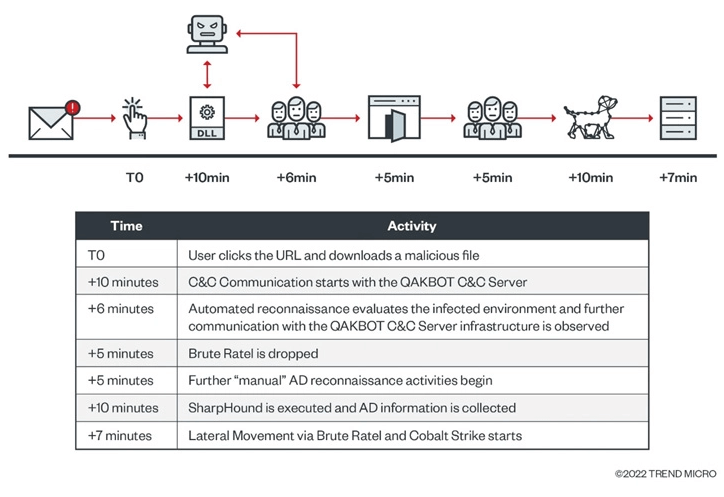
According to Trend Micro, the intrusion was achieved via a phishing email containing a weaponized link and further entailed the use of Cobalt Strike for lateral movement.
The ZIP file in the email contains an ISO file, which, in turn, includes a LNK file that fetches the Qakbot payload. The attack, however, was stopped before any malicious action could be taken by the threat actor. In another Qakbot execution chain spotted by the cybersecurity company, the ZIP file is delivered through an increasingly popular method called HTML smuggling, resulting in the execution of Brute Ratel C4 as the second stage.
Going Further into Detail
Black Basta is ransomware as a service (RaaS) that was first spotted in April 2022 and based on a threat assessment, had been compromising and extorting over 75 organizations by August.
Qakbot, also known as QBot and QuackBot, is a banking virus active since 2007 that steals user data and banking credentials, but it acts as a downloader, so it was turned into a means for dropping additional malware.
The Brute Ratel C4 (BRc4), like Cobalt Strike, is an attack simulation tool released in December 2020 and it`s being used in legitimate testing activities by organizations that seek to improve their ability to detect and respond to real cyberattacks.
According to the researchers at Palo Alto Networks, it wasn`t long before these tools fell in the wrong hands and began being used by threat actors. Brute Ratel attracts a lot of interest from cybercriminals due to the fact that it allows them to engage in malicious activities while unnoticed for longer periods of time.
The Qakbot-to-Brute Ratel-to-Cobalt Strike kill chain is associated with the group behind the Black Basta Ransomware. This is based on overlapping TTPs and infrastructure observed in Black Basta attacks.
As The Hacker news points out, these findings coincide with a resurgence of Qakbot attacks in recent months by using techniques such as HTML file attachments, DLL side-loading, and email thread hijacking. the latter involved harvesting emails from ProxyLogon attacks aimed at Microsoft Exchange servers.
Diversified Delivery Methods
The researchers from Trend Micro argue that the ZIP file which contains an ISO file, which, in turn, includes a LNK file that fetches the Qakbot payload, proves the threat actors are adapting their tactics in the aftermath of Microsoft’s decision to block macros by default for documents downloaded from the web.
Another cybersecurity company`s researchers have also noticed the recent increase in the distribution method of malware through ISO files, not limited to Qakbot, but also Emotet, IcedID, and BumbleBee. For example, in September, Unit 42 revealed the discovery of a malicious Microsoft Compiled HTML Help (CHM) file being used to deliver the IcedID malware.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









