Contents:
In 2022 HTML files are still one of the most prevalent attachments used in phishing scams, indicating that the method continues to be successful against spam detection software and works well on the targets themselves.
As per Wikipedia, the HTML (HyperText Markup Language) is the standard markup language for documents developed to be displayed in a web browser. It can be aided by technologies like Cascading Style Sheets (CSS) and programming languages such as JavaScript.
HTML documents are received from a web server or local storage by the web browsers and rendered into multimedia web pages. HTML describes the structure of a web page semantically and originally included cues for the appearance of the document.
HTML files are frequently used in phishing emails to lead victims to malicious websites, download files, or even show phishing forms locally within the browser.
Because HTML is not malicious, attachments are often overlooked by email security software, resulting in a successful delivery to targets’ inboxes.
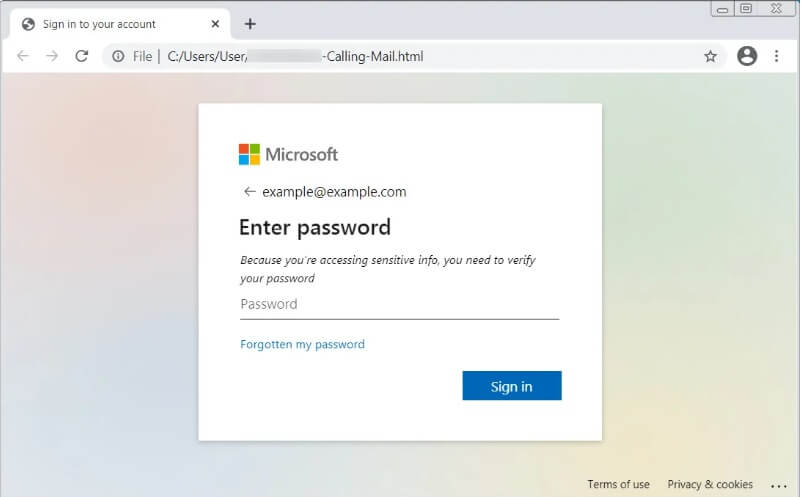
How HTML Avoids Detection
In HTML attachments, phishing forms, redirection techniques, and data-stealing components are usually implemented using several tactics, varying from simple redirects to obfuscating JavaScript to conceal phishing forms.
When attachments are present in email messages, they are base64 encoded, enabling secure email gateways and antivirus solutions to check them for malicious URLs, scripts, and others.
In order to avoid being detected, cybercriminals frequently include JavaScript in HTML attachments that will be used to create the malicious phishing form or redirect.
As explained by BleepingComputer, the use of JavaScript in HTML attachments to conceal malicious URLs and behavior is known as HTML smuggling and has become a widespread method in recent years.
To make malicious scripts even more difficult to identify, hackers obfuscate them with tools that are available for free and can accept custom configuration for a unique, and therefore less probable to be spotted, result and thus remain undetected.
To Keep in Mind
Even though HTML attachment distribution had its “glory days” in 2019, it is critical to remain vigilant as this method remains a favorite of threat actors in phishing attacks. Keep in mind that accessing these files can cause JavaScript to run on your system, potentially resulting in automatic malware assembly on the disk and the evading of security products.
Because security solutions fail to identify a malicious attachment, receivers are more likely to open it and have their systems compromised.
It is recommended that you always think of HTML attachments as highly suspicious, even if your email protection software doesn’t issue any alerts.
How Can Heimdal™ Help?
Heimdal Email Security will keep your inboxes clean and lean as it uses an entire array of technologies to detect and block spam, malware, and ransomware threats before they compromise your IT system through malicious emails. The advanced spam and malware filter Heimdal Email Security is also compatible with Heimdal Email Fraud Prevention, a module especially designed to combat the growing threat of Business Email Compromise (BEC) attacks.
With our Email Security module, your business and employees will be spared from:
- The pervasive, evolving threat of phishing.
- Email exploits & botnet attacks.
- Unwanted content.
- The again-growing threat of ransomware.
- The frustration of having to click away through never-ending spam emails.
- Botnet attacks through email.
- Malicious links and attachments.
- Emails coming from infected IPs and/or domains.
- Advanced spam.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










