Contents:
Affiliates of Black Basta gang are notorious for employing the banking trojan known as QakBot for initial access and almost immediately deploy ransomware in IT systems belonging to worldwide organizations. However, researchers concluded that U.S. companies have been targeted by a more aggressive campaign that leads to Black Basta ransomware infections on compromised networks.
Researchers at cybersecurity company Cybereason have issued a report claiming that Black Basta takes advantage of QakBot‘s backdoor-installing features that allow gang affiliates to drop ransomware on the intended organizations and proceed to extort them.
This is a wide scale attack against many companies in the U.S. and just within the past two weeks we have mitigated the risk with more than 10 of our customers.
The report adds that the campaign operators disabled DNS services, on order to lock the victims out of their networks, a move that has severe consequences for users and administrators. Another argument for the high severity of the attacks is the speed at which the gang members operated, the campaign taking around 12 hours from using QBot for initial access, to exfiltrating sensitive data and deploying ransomware.
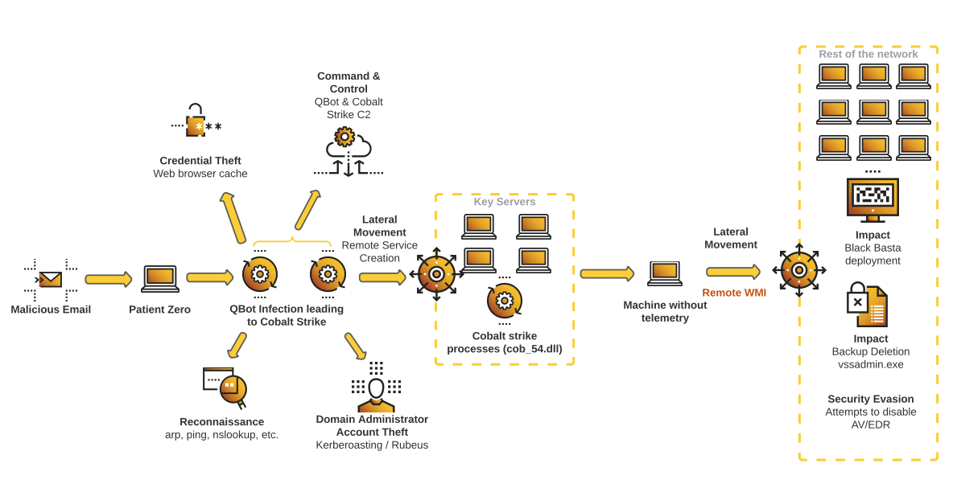
Upon a Closer Look
Black Basta is ransomware as a service (RaaS) that was first spotted in April 2022 and had been compromising and extorting over 75 organizations by August. The threat actors have been observed using Qakbot to deliver the Brute Ratel C4 (BRc4) framework, which was further leveraged to drop Cobalt Strike.
However, as The Hacker News explains, this time the intrusion activity cuts out Brute Ratel C4 from the equation, using Qakbot to directly distribute Cobalt Strike on machines in the infected network.
The attack chain starts with a spear phishing email that contains a malicious disk image file. Opening it will initiate the Qbot execution, which further connects to a remote server to retrieve the Cobalt Strike payload. Next, credential harvesting and lateral movement activities are carried out on several servers, before breaching as many endpoints as possible and launching the ransomware.
We concluded that the attacker uses an IMG file (Disk Image File, similar to the ISO format) as the initial compromise vector. We also identified other QBot infection vectors starting from ISO files, depending on the campaign.
The report also states that Black Basta generates a ransom note file in each folder it has infiltrated, after which the actual file encryption process begins.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









