Contents:
If you pay any attention to the world of cybersecurity, there’s a good chance you’ve heard the term ‘zero trust’ at some point over the last few years. In fact, the term is so ubiquitous that it’s often difficult to understand what it actually means and how you’d go about applying it to your security strategy.
As the Founder and Chairman of a cybersecurity company, I often encounter a lot of anxiety and confusion around zero trust, for precisely this reason. To be fair, it can be a vast and confusing topic. But the underlying principle is easy to understand, and there are plenty of changes you can make that are simpler than you might think. The key is to break the topic into manageable chunks so you can roll it out in a way that’s iterative, scalable, and non-disruptive.
So how do you do that? Keep reading to find out more.
What Is Zero Trust?
To understand how zero trust works, it’s helpful to take a step away from cybersecurity for a moment.
Instead, let’s picture a bank. Here, you’d expect there to be several different employees with differing roles; bank clerks, managers, first-line support staff – and more.
Each employee has a different set of privileges depending on the job they’re doing. First-line support staff might only need access to phone numbers, calendars, and basic customer information. The next level up, the team leader, likely has access to more sensitive data, like accounts, credit card details, and more. But only the branch manager has the keys to the vault – the highest level of access.
In each case, the logic is simple – no employee should have more than the minimum amount of privileges needed to complete their job. If every employee had the keys to the vault, the chances of it being breached are much higher.
This, in a nutshell, is how zero trust works. In the words of John Kindervag, the Forrester cybersecurity expert who coined the term, it boils down to four fairly simple words: “never trust, always verify.”
Why Do We Need Zero Trust?
In truth, these concepts are nothing new. Humans have been reducing unnecessary access to valuable assets for as long as they’ve needed securing. But in modern cybersecurity, zero trust (also called least privilege) has a more specific meaning that’s become increasingly important over the last decade.
Let’s look back to the IT environments of 20 ago. Then, most users logged in to a wired device through a unique login in a physical office. In this context, businesses generally relied on a ‘perimeter’ approach to security, which assumed that everything inside the IT environment was inherently trustworthy.
This approach may have worked 20 years ago, but it’s now largely unworkable. That’s because today’s IT environments are much more complex. Employees expect to log in from any time, device, or location.
And organizations rely on a whole complex range of different IT assets, including IoT devices, APIs, RPA workflows, smart devices, and much more. All of this makes it much more difficult to effectively verify that those inside your network are who they claim to be.
With perimeter security, there’s very little standing in an attacker’s way once they’ve gained access. This is why the zero trust strategy was first designed, and why it’s widely considered to be the default setting for effective security today.
Mythbusting Zero Trust: What Are the Biggest Misconceptions?
As the Chairman of Heimdal®, I spend a lot of time talking with clients about effective security. These organizations generally know exactly how important cybersecurity is and most have a good working knowledge of zero trust.
But beyond that, there’s often a lot of confusion about the topic. This can make it difficult to know where to start and result in organizations being reluctant to make any progress. Here are some of the most common misconceptions I regularly encounter:
1. It’s all or nothing
Many IT teams worry that implementing zero trust will be a mammoth task, costing thousands of dollars and causing huge disruption to the business. I see this fear a lot from IT teams who understand the importance of zero trust – but are wary of the business impact of implementing it.
Luckily, it’s not all or nothing. Applying zero trust to just one area is still better than applying it to none – and it’s much better to roll it out iteratively than to overhaul your IT environment in one go.
Think about where the biggest risks and vulnerabilities are in your business and start there. Ultimately, there’s nothing wrong with having different levels of zero trust applied to different systems at different times. Don’t make perfect the enemy of good.
2. Zero trust will seriously damage productivity
As the Chairman of a cybersecurity company, I’m uniquely aware of the tension between tight security and smooth business operations. Modern trends like remote working and the multi-device world all make security a challenge. But pretending the IT environments of 2003 are still viable is only going to result in high voluntary attrition and a (rightfully) angry HR team.
So how do you manage this balance?
Ultimately, most security controls will have some impact on ease of use. But increasingly, the best technology is looking to reduce that trade-off to an absolute minimum.
Take passwords for example. Traditional password security requires complicated, long, unique, and frequently changing passwords – which are a nightmare to remember. The result? That ‘forgot my password’ link ends up getting used more often than not.
Instead, today’s security tools prefer to use options like multi-factor authentication and passwordless verification. This is both better security and simpler for the user, because they just have to log in to a password manager or click a smartphone notification.
Generally, the best zero trust technology will use options like this to reduce friction without compromising security.
3. Zero trust requires expensive, complicated tech
Many companies assume that to roll out zero trust, they need the most expensive, all-encompassing, and sophisticated zero trust platform around. This can be an issue because the industry’s biggest players (CyberArk, BeyondTrust, and others) are really designed to be used by specialist security teams. They can be difficult to use, manage, and scale. The last thing you want is an expensive and complicated piece of software that you can’t actually use.
But there’s another issue: Providers tend to split their features between multiple confusing and overlapping products. The more you add, the more your licensing costs add up, and the more difficult it becomes to get one solution to speak to the next. These products can be a real poisoned chalice, so it’s important not to fall for the hype.
Instead, the best approach is to find a security platform with the broadest possible reach, so you can expand your zero trust implementation iteratively, over time. This means you can avoid costs and complexity spiraling out of control.
Spoiler alert: I think Heimdal® is by far the best example of this. But we’ll get into that in more detail below.
Four key elements of zero trust
There’s no single, objective way to break down or implement zero trust, and different practitioners will have different approaches. Generally, I like to break it down into four sections; files, networks, applications, and devices. This will cover the vast majority of actions and protections that the average organization needs to put in place.
1. File Access
File access is probably the easiest element of zero trust to understand, so it’s helpful to start here. The goal of this section is to reduce access to sensitive information to an absolute minimum.
But to do that effectively, you need to understand where that privileged information exists, and who might be attempting to access it. These can be difficult questions to answer – but you’ll struggle to effectively implement least privilege if you can’t.
Here are the main steps to getting it right:
1a. Inventory all user and service accounts
The best place to start is to understand the full scope of accounts that exist in your organization. This is complicated, because a single person may have multiple identities across different apps. At the same time, organizations are often full of disused or shadow accounts for employees who no longer need access.
Your goal here should be to remove unnecessary accounts and privileges and consolidate identities. This helps reduce the attack surface, making it more difficult for hackers to both penetrate and move through your environment.
Read more: What Is Privileged Access Management (PAM)?
But it’s not just about people. Today’s organizations rely on increasing numbers of machine identities for a whole range of processes. If an RPA workflow is programmed to view or edit sensitive information, it’ll need the same elevated permissions to access that data as an HR manager. This creates a whole new tier of identities that also need to be audited and understood before least privilege can be applied.
The simplest way to create this inventory is with a privileged access management (PAM) tool, which can automatically scan and audit all user and service accounts. Then, any unused or unnecessary accounts should be eliminated, and accounts with extra permissions should be revoked.
1b. Establish a centralized database of accounts
It’s important to ensure that there’s a single authoritative version of each identity in one location. It’s common for a single user to have multiple identities across different applications or cloud-specific directories. This is a big issue for security because duplication makes it harder for you to apply least privilege and offers a larger attack surface for hackers to target.
Generally, the solution here is going to be to migrate, merge, and centralize all your identities into the Active Directory or a cloud-based directory like Okta or OneLogin. Where possible, you should take advantage of single sign-on tools to reduce the number of separate login details associated with a single identity.
From there, it’s much easier to apply least privilege to the remaining accounts.
1c. Define sensitive data and where it exists
The next stage is to understand what sensitive information exists in your organization and who needs access to it. This is challenging because what counts as sensitive is specific to your organization. Here, you’re simply going to have to use your judgment.
Luckily, there are a few patterns. Anything involving personally identifiable information is going to be sensitive by default since it’s protected by strict compliance standards. The same is true for financial information of any kind.
The other category is more qualitative; confidential information and intellectual property. This can be anything from contractual agreements, product update plans, trade secrets, and more.
The consequences of losing this information can range from ‘disastrous’ to ‘a bit embarrassing’, so it’s important to think carefully about what the associated risk is to each individual asset.
1d. Organize files and assign privileges
It’s impossible to assign privileges to every file on a case-by-case. Instead, you need to group information together into logical categories.
The best way to do this is to establish different folders or directories of files, based on who is going to need access to them. There could, for instance, be separate folders for HR, finance, and sales teams.
While the product team might need access to upcoming feature plans, the HR team probably doesn’t. Where sensitive employee data is concerned, the reverse is true.
The goal here is to create a clear and logical structure for information, so you can effectively assign the right level of privileges to the right location. Then, it’s simply a case of reducing elevated permissions to only those who absolutely need it.
1e. Implement multi-factor authentication and password policies
Next, we’re going to assign stringent security policies to your accounts. This will make it as hard as possible for hackers to gain entry and move laterally.
By far the most effective tool here is multi-factor authentication. This is now commonly available through the Microsoft Active Directory, as well as single-sign on tools like Okta and OneLogin, and individual apps. Where multi-factor authentication is an option, it should be enabled.
There are also a number of policies you can implement to make passwords themselves more secure. The most effective of these take advantage of a range of ‘passwordless’ models of security that don’t require the end user to remember a password at all.
Instead, you could ensure all credentials are saved in a secure vault, with access given via a password manager, digital keys, or other forms of verification. By removing the need for the employee to remember the password, you can ensure the passwords themselves are both complex and regularly rotated, without affecting usability.
2. Network access
Zero trust network access applies to any number of networks in an organization. By its nature, much of this is going to refer to internet and DNS connectivity, since these connections are by far the easiest for hackers to exploit. But it can also include anything from WiFi or IoT networks, as well as VPNs, local or wide area networks (LAN, WAN), and more. Increasingly, these are also likely to be virtualized (ie, cloud-based), adding another level of complexity.
Whatever this includes, the goal is the same: to reduce the attack surface, segment networks, and reduce entry for unidentified users as much as possible.
Read more: Unified Endpoint Management (UEM) Explained
2a. Block DNS requests to known threats
A reasonably simple action that can make a big difference. The best DNS monitoring tools maintain a constantly updating database of known threat actors, compiled from realtime telemetry data.
Here’s how it works: when a hacker tries to make a connection, your DNS monitoring tool will compare the IP address and domain against their database. If flagged, the request can be immediately blocked or redirected.
This isn’t going to help with unknown threats, but it’ll help eliminate some of the biggest DNS threats without too much admin or hassle.
2b. Remove open ports and connections
When you first connect to a new website or app, the IP address is inspected to ensure it’s genuine.
But by default, subsequent connections to the same website are kept ‘open’, meaning they can be tampered with or altered without the same checks. In a zero trust system, all connections should be terminated to avoid this risk. There are several options here, but the most common is to use extensions like DNSSEC. In short, these ensure DNS requests are verified every time, not just the first.
For the same reason, it’s also important to eliminate any ‘open ports’. These are configured to accept any incoming connection by default, essentially giving hackers an open door to make connections. These open ports should be eliminated as much as possible.
The best approach is to take advantage of a Zero Trust Reverse Proxy tool. These can scan applications for open ports and let you remove them without completely revoking unverified user access. This is important since publicly-facing apps wouldn’t work if unverified users (also known as customers) can’t access them.
2c. Eliminate SSL-based connections
SSL connections were once the default internet protocol, but it’s now considered moribund. Its newer replacement, TLS, encrypts all data in transit, making it difficult to spoof or tamper with.
Many incoming connections still use the insecure SSL protocol, and it’s important to filter out and eliminate these as much as possible. The best approach here is to use TLS decryption tools. These allow you to define security policies to block or redirect incoming SSL-based connections.
2d. Segment networks
Lateral movement is one of the biggest risks to your IT environment. For this reason, it’s helpful to segment your networks to reduce the ability of hackers to progress from one to another.
The first step here is to separate guest networks from corporate networks. This could include public-facing websites and apps, as well as guest Wi-Fi networks – since these, by their nature, are open to everybody.
There should be no way to pass from one of these publically-facing networks to your corporate network. Firewalls are the best way to prevent this since they can block all traffic from a guest network to an internal one.
But you should also try and segment your internal corporate network, so an attacker doesn’t have free reign if they’ve already gained entry. You may choose to have different networks for each region your company operates in or to segment sensitive servers from other, non-sensitive assets.
3. Application access
For this next stage, we need to understand what applications are being used in the organization and who has access to them. The processes we’re following here are, in many ways, quite similar to the first section – we’re just exchanging files for applications.
In today’s SaaS-based world, an increasing amount of sensitive data is stored in line of business applications like CRMs, HR software, mortgage tracking software, and more. It’s important to apply least privilege to these apps in exactly the same way you would an Excel document saved in a folder. If not, you’re leaving open a hugely lucrative entry point for hackers to target. Here are the main points you need to consider:
3a. Inventory all corporate applications
As was the case with files, it’s important to understand what applications are in use in the organization. This is easier said than done because employees regularly use unsanctioned ‘shadow IT’ apps, which can pose a huge threat if unmonitored.
The best way to identify applications, including shadow IT, is by using a Secure Web Gateway or a Cloud Access Security Broker (CASB). These tools monitor traffic to identify all apps being used by users, both sanctioned and unsanctioned.
Now you’ve got an idea of the full scope of apps being used, you can start to apply least privilege.
3b. Enforce zero trust
The next stage is to block unsanctioned apps and reduce access to sensitive apps.
There are a number of tools you can use here that will be helpful. A CASB, for instance, can provide both visibility over applications being used and allow you to set policies to define who can use what. Unsanctioned applications can be banned entirely. You can also restrict access to applications with particularly sensitive information, such as mortgage software or CRMs.
Ideally, you should also aim to enable conditional or ‘just-in-time’ access here, ensuring even users that do need elevated permissions are given it on a case-by-case basis. Several modern authentication tools provide this functionality, generally by analyzing a range of behavioral signals that identify suspicious activity and revoking access where necessary.
3c. Establish phishing defenses
Email is another attractive entry point for hackers. The most popular form of attack here is phishing, in which employees are tricked into providing sensitive information or login details.
Hackers generally use phishing tactics to gain a foothold in your environment without being detected. Crucially, they’ll often target unprivileged accounts to do this, knowing they’ll be subject to fewer defenses. Then, they’ll use this foothold to move laterally.
It’s important, therefore, to establish robust defenses for all email accounts. There are a range of email security tools on the market that can do this, generally by using anomaly analysis to detect suspicious communications. These can then be removed entirely or filtered into an isolated browser for the security team to assess.
4. Device and endpoint access
If you’ve read the last three sections, this isn’t going to be much of a surprise, as much of the advice here takes a similar approach – only applied to devices instead of files and applications.
So what does this category include? It’s important to account for the full range of endpoints that a modern IT environment might include, such as IoT and smart devices, tablets, rugged devices, servers, and more. You should also include cloud devices like virtual machines.
Here are the main steps to take:
4a. Inventory all devices
Here, it’s important to get a clear understanding of your devices, so you can reduce access to the most sensitive endpoints and eliminate unnecessary access points.
Here, the tool of choice is Endpoint Detection and Response (EDR). These tools provide continuous monitoring of endpoints and the activities associated with them. This allows you to automatically detect (and block) when new devices connect to the IT environment.
4b. Remove unnecessary admin rights
There are a whole range of different account ‘types’ that each come pre-loaded with a different set of privileges. The most basic accounts have no administrative rights. These, by their nature, are the safest accounts and should be the default setting for most users. The vast majority of users, after all, do not need the ability to install and execute apps on their own devices.
Then, you have a series of privileged accounts, including domain admin accounts, local admin accounts, and root/admin accounts. All of these should be reduced as much as possible. But you should be particularly aware of the dangers that root or admin accounts can pose. These have virtually unrestricted control of a network and are usually reserved for the most senior IT staff.
If compromised, these accounts could give hackers complete control over servers, firewalls, networks, domains, and really anything that exists in your IT environment.
Where possible, root or admin accounts should be eliminated entirely. Instead, privileges should be split between separate accounts to avoid anyone having too much access. You should also aim to implement just-in-time access and similar protections here so that when users gain access, they do so on a case-by-case basis, and for strictly time-limited periods. This reduces the attack surface to the smallest possible amount.
4c. Implement mobile device management
In order to apply least privilege to endpoints, you need some form of remote device management tool. Unified endpoint management (UEM) is generally the best here since it combines functionality to manage all types of endpoint in one interface. But mobile device management (MDM) tools can also be popular and effective.
Read more: Unified Endpoint Management (UEM) Explained
The key functionality you need to look out for is the ability to remotely govern access to apps and devices. You should also be able to enforce policies like requiring passwords to be changed remotely, and the ability to wipe or lock the device in case of loss or theft. These features are now common in most MDM products.
4d. Implement endpoint protection
The next stage is to implement endpoint protection. These are a series of tools that monitor devices for realtime threats, such as viruses, malware, and other known threats. Malicious activity can often be spotted by algorithms due to strange or anomalous behavior, and that’s certainly the case here. Generally, they feature a range of tools to boost the device’s health and make it difficult for hackers to target.
But more than that, they also help eliminate issues like unpatched vulnerabilities that offer further entry points for hackers. In this case, they can be configured to install patches remotely or automatically, so devices don’t need to be brought to the IT team to be updated.
Heimdal® XDR: One Platform, Total Security
Getting the right technology is by far the easiest way to implement much of the advice I’ve discussed above. But not all tools are made the same.
Most cybersecurity vendors offer a complicated web of tools – ranging from privileged access management to endpoint protection, endpoint detection and response… the list goes on.
Here’s the issue: The more products you have, the more difficult they are to effectively use. A complicated network full of 10 state-of-the-art solutions that don’t talk to each is going to offer much less value than the sum of its parts.
So what’s the alternative? At Heimdal®, we take a different approach. We want to make zero trust as easy as possible to manage by integrating everything into one easy-to-use dashboard.
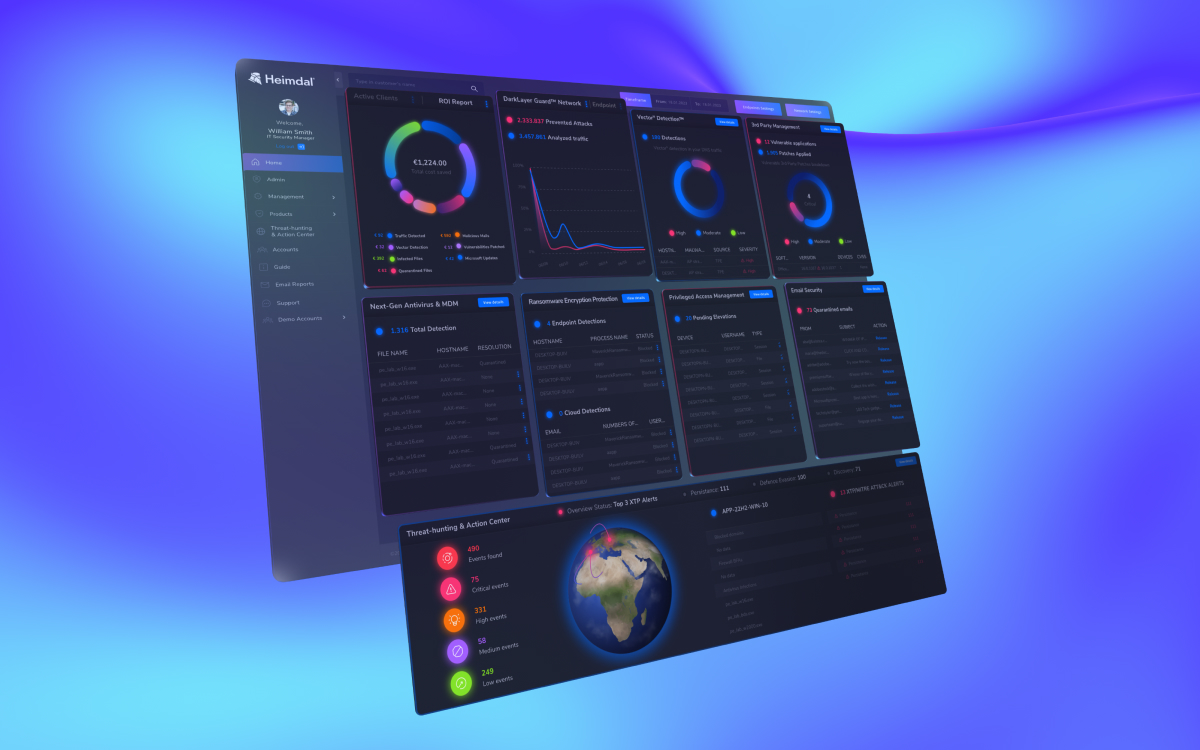
Crucially, with seven different modules, you can start small and grow your usage over time, without having to knit together multiple complex and siloed solutions.
Here’s how what the platform includes:
- Network security: A range of market-leading DNS security tools to help monitor, manage, and secure network-based connections.
- Endpoint security: Secure remote devices of all shapes and sizes through endpoint DNS security, next-gen antivirus, firewalls, and ransomware encryption protection.
- Vulnerability management: Create policies to automatically install patches and updates, so you can take the admin out of vulnerability management.
- Privileged access management: Define granular policies to govern who has access to what files, applications, and other devices. This includes tools to dynamically accept or deny access based on contextual signals – eliminating the need for standing privileges.
- Email and collaboration security: Detect and prevent incoming email-based threats, with advanced anomaly analysis to detect and repel even the most convincing phishing attempts.
- Threat hunting: Our threat detection platform allows IT teams to quickly detect and track anomalous behavior, together with risk scores and a forensic breakdown of the event, device, and associated applications. This makes effective and targeted responses much easier.
- Unified endpoint management: Manage devices of all shapes and sizes from one simple dashboard. No more clicking between disconnected apps to manage laptops, mobile devices, or BYOD devices.
Together, these seven modules offer a simple, comprehensive, and scalable approach to implementing zero trust. In our humble opinion, it’s by far the best place to start.
Zero Trust FAQs:
What is the zero trust security model in cybersecurity?
Zero trust is a cybersecurity model based on “never trust, always verify.” It requires continuous verification of every user and device trying to access resources. Zero trust uses strict access controls, multi-factor authentication (MFA), and other modern cybersecurity defenses to protect data. By treating every request as potentially malicious, it helps avoid unauthorized access and reduce data breach risks.
How does implementing zero trust improve security?
Zero trust enhances security by reducing the attack surface and enforcing strict access controls. It requires continuous authentication and authorization, minimizing insider threats and lateral movement. It aims to ensure that access is only given where needed, making it harder for attackers to effectively target and pass through your network.
What are the biggest zero trust misconceptions?
There are a few common misconceptions associated with zero trust. First, that it’s all or nothing. In truth, some level of protection is always better than none. Many also think that zero trust involves strict controls on everything. While this is sometimes the case, using the right technology can help alleviate friction in most places.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security