Contents:
In this comprehensive guide, we’ll take a closer look at Extended Detection and Response (XDR Software).
Whether you’re seeking to strengthen your personal cybersecurity or your organization’s digital defenses, by the end of this article, you will know:
- What XDR software is
- How XDR software functions
- How adopting a proactive and complete approach to threat detection can safeguard you.
- How is XDR different from other security tools?
- Benefits of XDR.
- Challenges of XDR.
- XDR implementation .
- The difference between XDR and MXDR.
- How to choose an XDR Solution.
- Frequently Asked Questions (FAQs).
What is XDR?
XDR is an abbreviation of Extended Detection and Response.
It’s a cybersecurity solution that unifies threat detection, investigation, and response.
By seamlessly integrating data from diverse security components like endpoints, servers, cloud applications, and emails, XDR offers a rounded defense against cyber threats.
Heimdal XDR is the best tool. It’s a unified and proactive approach to security. Your security team can detect, respond to, and mitigate advanced threats across the entire digital landscape.
Nabil Nistar, Head of Product Marketing
Key Components of XDR
XDR isn’t just a tool; it’s a strategic approach that addresses the complex challenges of modern security.
At its core lie several key components, with each serving as a vital piece in the puzzle.
1. Data Collection and Integration
Using the data gathered from diverse sources such as endpoints, networks, and cloud environments, now you can:
- Establish centralized data storage and management for seamless access.
- Integrate logs, events, and alerts for a comprehensive overview of the environment.
2. Detection and Analysis
By including advanced threat detection techniques like behavioral analysis, AI/ML, and threat intelligence, now you can:
- Correlate data to uncover intricate attack patterns that might go unnoticed individually.
- Perform real-time analysis to swiftly identify and respond to emerging threats.
3. Investigation and Response
With deeper context to detected threats, enabling thorough understanding and assessment, now you can:
- Automate and guide investigation workflows to streamline the response process.
- Equip security teams with actionable insights, empowering effective countermeasures.
4. Adaptive Response
With the help of adaptive response, now you can:
- Execute both automated and manual response actions to neutralize threats effectively.
- Isolate compromised systems promptly to prevent further spread of attacks and damage.
When should you buy XDR?
Deciding when to invest in XDR depends on your organization’s unique cybersecurity needs and readiness.
Consider these factors to determine the right timing:
1. Growing Businesses
As your company scales, so does the potential attack surface.
Now that you’ve decided to invest in XDR during periods of growth, you can fortify your defenses before vulnerabilities become glaring risks.
2. Highly Targeted Industries
If your industry is a prime target for cyberattacks (e.g., finance, healthcare, critical infrastructure).
By adopting XDR early, now you have proactive protection against sophisticated threats.
3. Limited Visibility
If your current security tools provide limited visibility into your IT environment.
With XDR you can now have comprehensive coverage across endpoints, networks, and cloud environments.
How does XDR help businesses?
Here’s how XDR can empower businesses:
Compliance and Regulations
For companies bound by strict compliance regulations (GDPR, HIPAA, etc.), XDR can help maintain adherence by detecting and mitigating threats that might compromise data security.
Now, you can confidently navigate complex compliance requirements while fortifying your data security.
Post-Incident Reassessment
After facing a security breach, reevaluating your cybersecurity strategy is crucial.
XDR can provide the enhanced visibility and automated response capabilities needed to prevent future incidents.
Now, you possess the tools to rise stronger after adversity.

How is XDR different from other security tools?
The two tools most often compared to XDR tools are EDR and SIEM.
Here’s how XDR is different not only from EDR and SIEM, but also from SOAR, NDR, and MDR.
XDR vs. EDR
Extended Detection & Response goes beyond the scope of EDR by integrating insights from across your entire digital environment, including networks, cloud, and more.
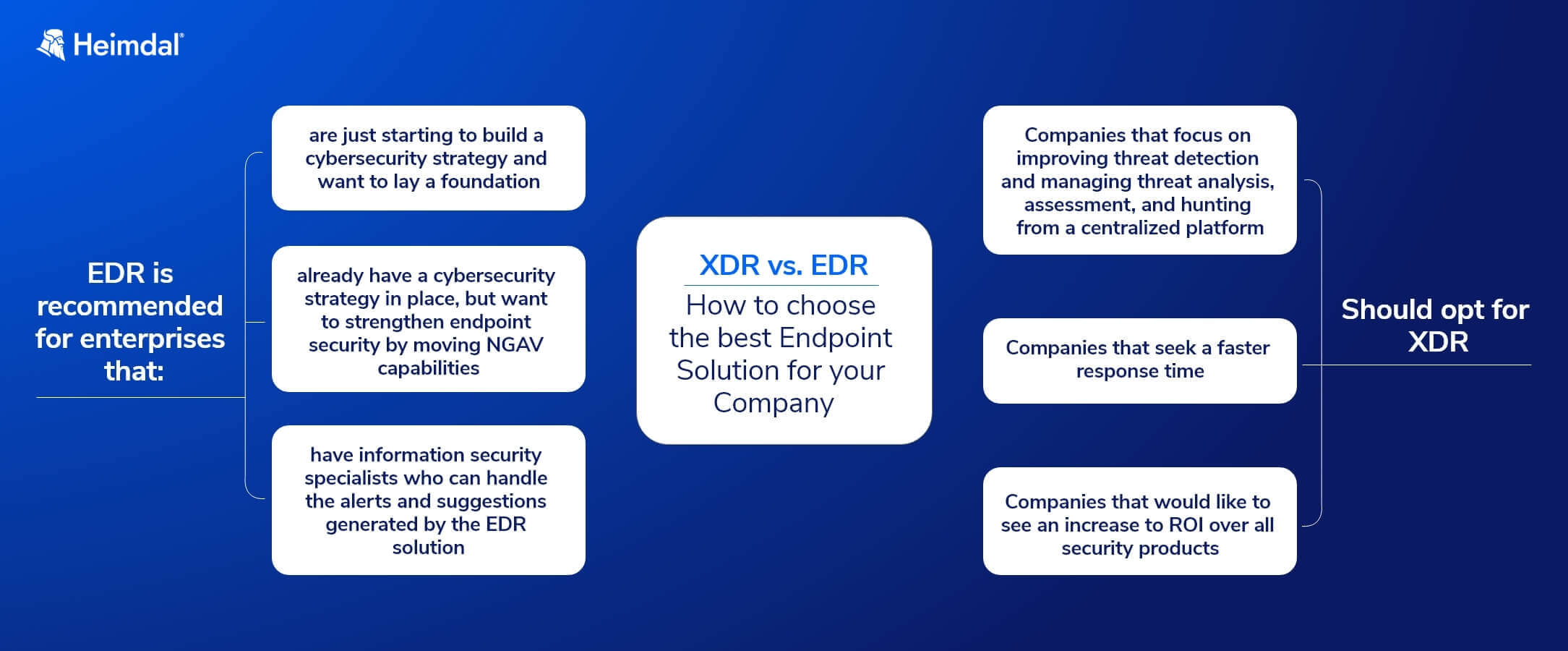
This comprehensive approach provides a more holistic view of potential threats, allowing for better correlation of data and quicker response times.
XDR vs. SIEM
XDR is a way of boosting the detection and response that SIEM currently provides.
In fact, SIEM can work hand in hand with XDR, helping gather, sort, and evaluate massive amounts of data for SOC analysts.

XDR vs. SOAR
While XDR and SOAR target security event analysis and response, they do so in fundamentally different ways.
XDR vs. NDR
NDR’s area of focus is on the network and the traffic between devices.
However, it can be bypassed by APT, ransomware, and more.
This is where XDR steps in, as it combines insights from various sources like endpoints, networks, and more.
XDR vs. MDR
XDR and MDR are both proactive solutions that mitigate threats and send important alerts to the SOC team for in-depth research.
Benefits of XDR
XDR offers a range of security benefits that gives you, flexible, and efficient protection against threats:
Detects more advanced threats
One key benefit of XDR solutions is traffic monitoring in the entire network.
In this way it can detect anomalies, and block them.
Now you can identify and stop all known threats and also new and unknown threats.
Analyzes data from several sources
XDR collects data while monitoring the traffic and then analyzes it, correlating all telemetry.
This way, your security solution has better visibility into your company’s weak points and abnormal activities can be spotted faster.
Reduces alert fatigue
The automated response means that no human intervention is needed to react to certain threats.
Now your IT team will have to deal with fewer alerts that they have to go through and triage
Boosts productivity
Because this cybersecurity solution is uniting multiple tools under one dashboard, they are easier to handle.
Finding them all in one place can be time-saving for your team, making the whole workflow so much smoother.
Restores rapidly after an incident
If an incident occurs, now you can rely on your Extended detection & Response solution to isolate and mitigate it as fast as possible.
This way the downtime for your systems is reduced to a minimum as well as the risk of other areas getting compromised after the initial infection.
Reduces overall costs with cybersecurity
Not only that this security solution is more advanced and saves your employees time, but it will also save you money.
Not having overlapping products could now be a way for you to reduce costs related to cybersecurity and maximize your resources.
Challenges of XDR
XDR offers a promising pathway for enhancing cybersecurity, however, its implementation comes with a set of challenges that you must navigate to fully realize its benefits.
Here are some of them:
Initial Investment
Implementing XDR requires financial investment for technology acquisition, training, and deployment.
Vendor Selection
Choosing the right XDR vendor involves careful evaluation of features, scalability, integration capabilities, and support services.
Integration Complexity
Integrating XDR with existing security infrastructure and tools can be complex.
Alert Overload
While XDR aims to reduce alert fatigue, improper configuration can lead to an overwhelming number of alerts.
Developing efficient triage processes is necessary to prioritize and respond to critical threats.
False Positives/Negatives
Fine-tuning detection algorithms is crucial to minimize false positives (incorrectly identifying harmless events as threats) and false negatives (failing to identify actual threats).
Striking the right balance requires ongoing optimization.
Skill and Knowledge Gap
Operating XDR effectively requires specialized skills and knowledge.
Security teams must be trained to understand XDR’s capabilities, configure detection rules, and interpret complex threat patterns.
What does XDR implementation look like?
I recommend thinking of XDR as a strategy, instead of as a single, specific product.
The first step you need to do is to, assess your existing security infrastructure and identify gaps. Then, you need to select a suitable XDR vendor.
Choose an XDR provider that naturally blends with the majority, if not all, of your data sources.
This ensures that essential data can seamlessly flow into the XDR platform and be organized consistently.
The next steps are deploying the solution, configuring detection rules, and fine-tuning the system for optimal performance.
Remember, the ultimate goal is to establish a comprehensive defense mechanism that unifies threat detection, analysis, and response across multiple fronts.
XDR vs. MXDR: What’s the difference?
MXDR is essentially XDR purchased as a service.
The primary advantage of MXDR is its ability to swiftly recognize and mitigate threats, all without requiring extra workforce resources.
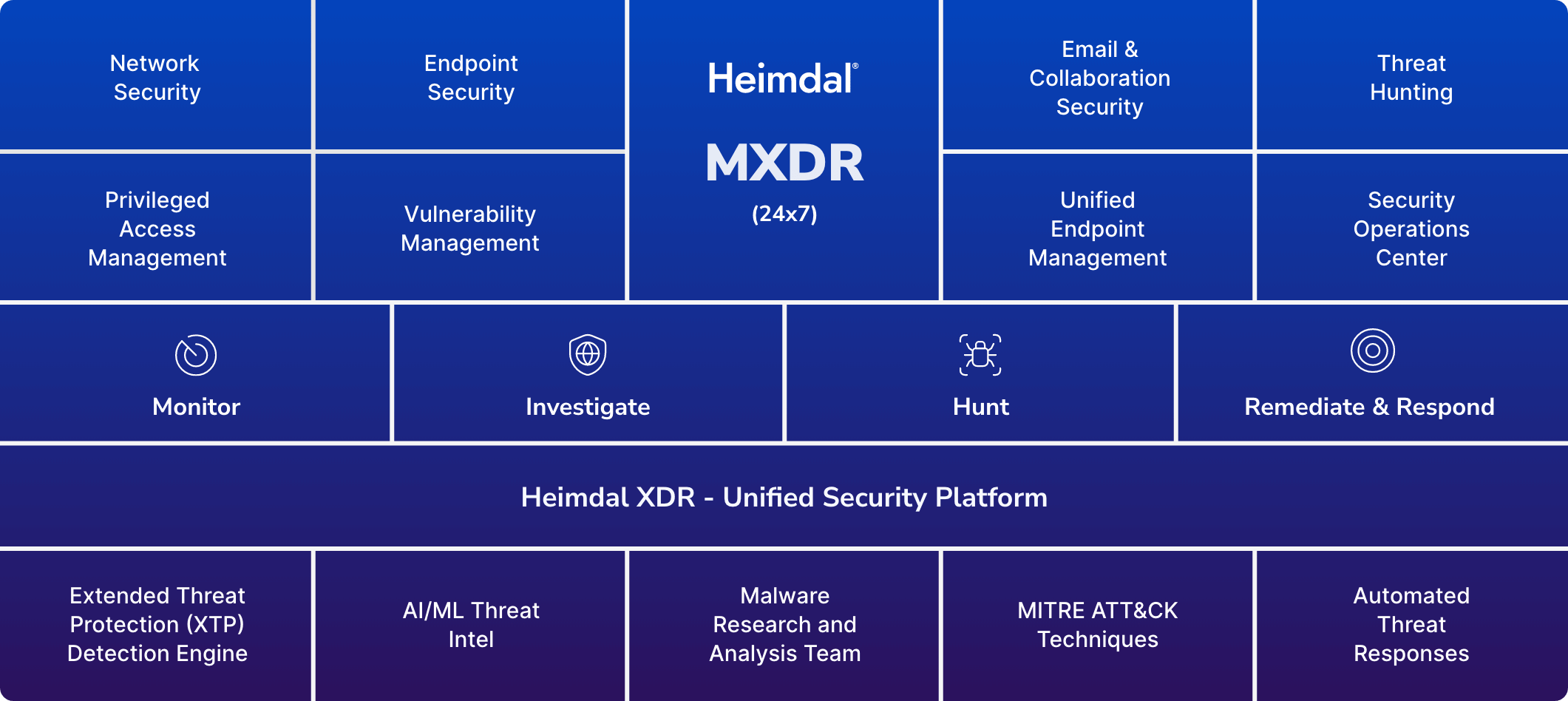
The solution usually includes a Security Operations Center (SOC) that provides event monitoring, threat investigations, extended threat hunting, and forensics.
If you are interested in finding out more about MXDR, we have prepared for you a A Webinar Insight on the Solution for Overcoming Short Staffing in Cybersecurity.
Use Cases
To truly deliver on the idea of easy, automated, and ready-to-go threat detection, investigation, and response, Extended detection & Response solutions must incorporate clear and focused steps for addressing threats.
A dependable XDR should encompass all the capabilities for swift and thorough handling of various scenarios.
Embracing security automation is a pivotal aspect of modern security operations, and vendors must provide step-by-step directions and workflows to tackle specific threats, ensuring their solutions are precisely tailored to yield successful outcomes for different types of threats.
How to use XDR for Monitoring:
To give you a complete grasp of an alert’s context, Heimdal XDR offers the Alert Panel view, allowing you to swiftly conduct a comprehensive analysis.
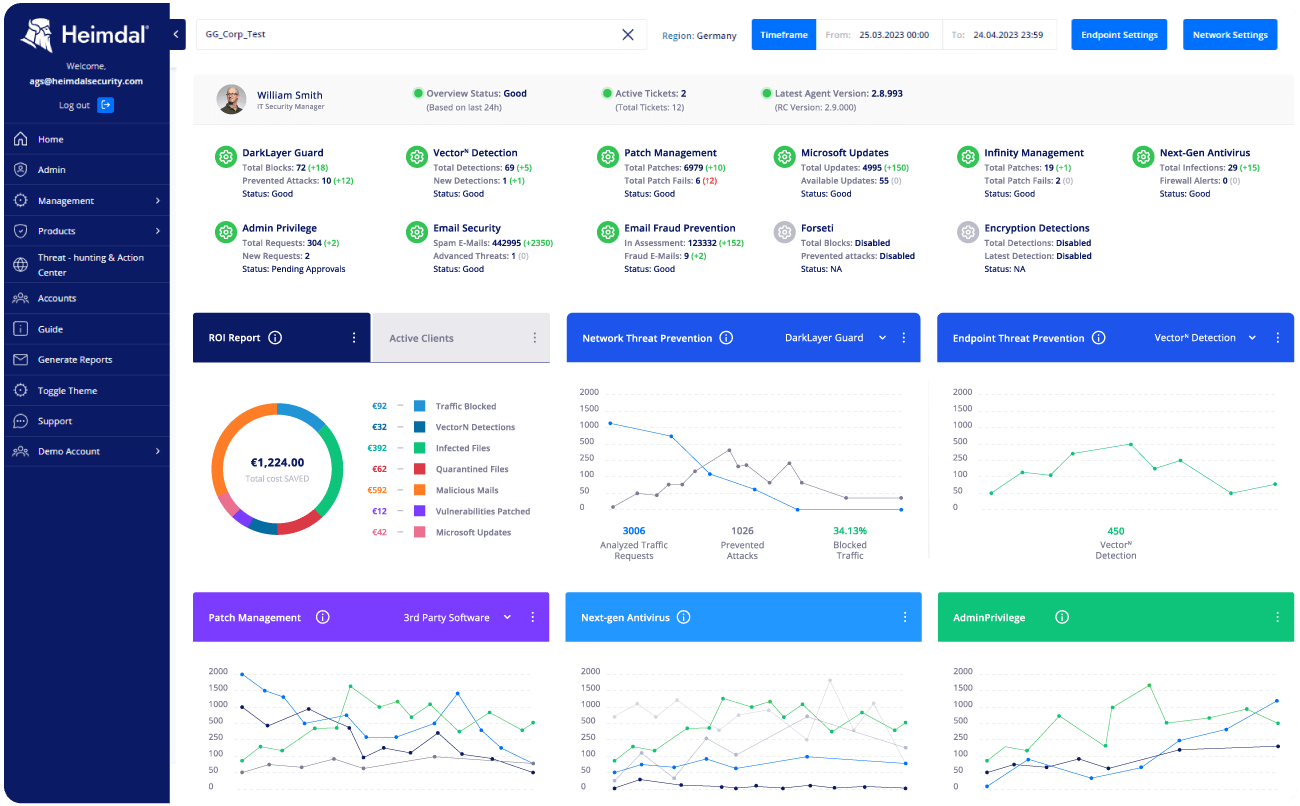
Having one portal to access all your security alerts makes management and issue tracking incredibly convenient.
Now you have a consolidated system that streamlines the process of overseeing and addressing security matters, providing an efficient and user-friendly platform.
How to use XDR for Investigation:
Be at the forefront of security with our bi-lateral telemetry and meticulous triaging details.
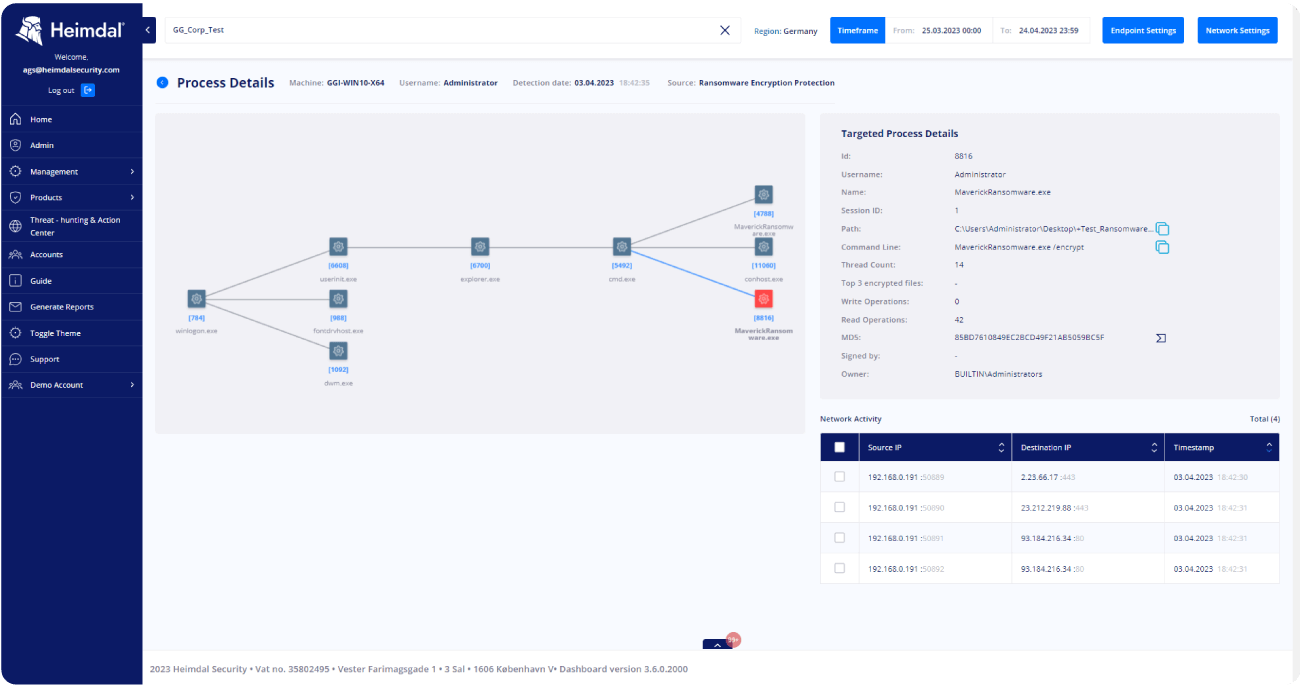
By linking process correlations, forensic analysis, and contextualized insights throughout your entire organization, you now possess the resources necessary to meticulously explore events and possible threats.
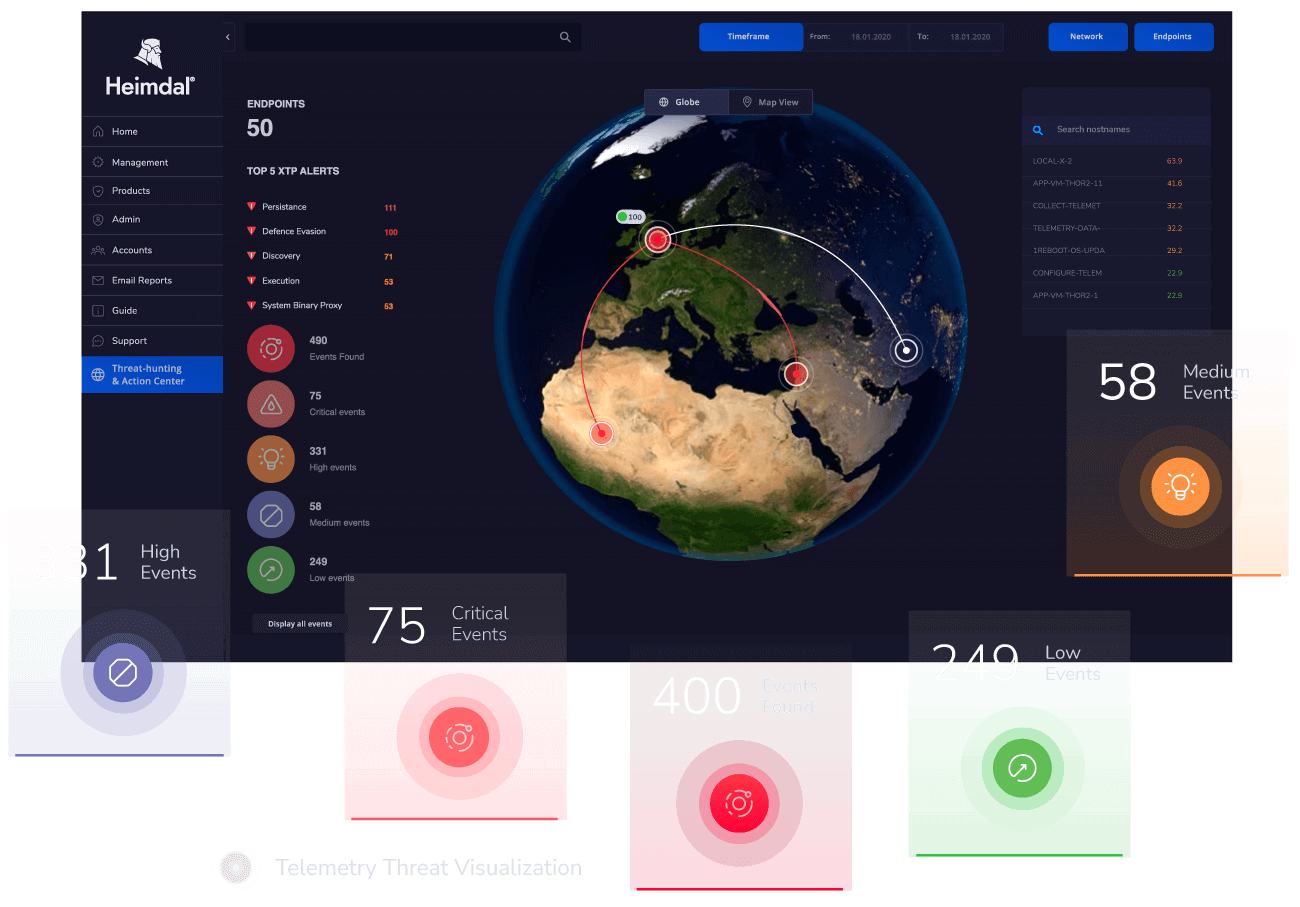
How to use XDR for Threat Hunting:
Our advanced unified platform includes an Action Center, streamlining one-click automated and assisted actions across your digital environment.
Now you are empowered to swiftly and effectively counter potential threats, ensuring the safety and security of your business and data.
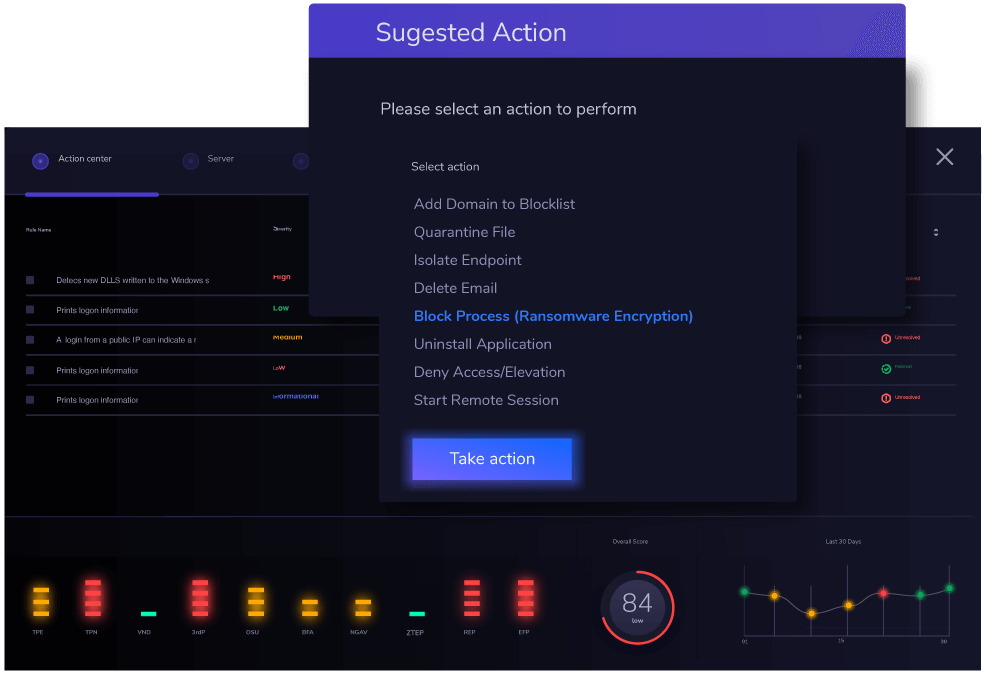
How to use XDR for Remediation and Response:
Simplify your security procedures using our unified Heimdal Extended Detection & Response platform.
Whether you lean toward manual or automated responses, you can now execute them seamlessly within the platform itself.
The user-friendly interface and intuitive design ensure you can effortlessly monitor potential threats and respond promptly as needed.
How to choose an XDR Solution
Here are three key points to consider when choosing the right XDR platform for your needs:
- Choose an XDR provider that effortlessly integrates with most, if not all, of your data sources. This guarantees a smooth flow of crucial data into the XDR platform.
- Look for advanced threat detection techniques, like behavioral analysis and AI/ML, that reduce false positives and ensure accurate identification of complex attacks.
- Research the reputation and track record of the XDR solution provider. Consider factors like customer reviews, support services, and the vendor’s commitment to continuous updates and improvements.
The best XDR software and tools
Extended detection & Response solutions consolidate diverse security tools, simplifying the detection and resolution of security concerns.
Therefore, it’s crucial to assess their effectiveness, compatibility with your current systems, and the level of support they provide.
How Can Heimdal® Help?
With the Heimdal XDR, you can eliminate the complexity of managing multiple security solutions and gain the peace of mind that comes with having a comprehensive, integrated approach to cybersecurity.
Whether you’re dealing with complex, multi-vector attacks or advanced malware infections, our platform has you covered.
Don’t wait until it’s too late – now you can experience the power of our unified, cloud-delivered XDR platform and protect your organization from cyber threats.
While challenges certainly exist, they’re eclipsed by the advantages: of precise threat identification, automated responses, streamlined operations, and the constant evolution of your security stance.
As you navigate the cybersecurity world, remember that XDR isn’t just a tool, but a strategic ally.
Frequently Asked Questions (FAQs)
What is the XDR method?
Extended Detection and Response offers a panoramic view into the intricate web of data spanning networks, cloud environments, endpoints, and applications.
By harnessing the power of advanced analytics and automation, XDR not only identifies and analyzes existing threats but also proactively hunts for emerging risks.
How do you implement XDR?
To conquer this obstacle, take these proactive steps:
- Shift your perspective on XDR. Consider it not as a singular product, but rather as a comprehensive strategy.
- Underpin your XDR approach with a well-defined set of prerequisites tailored to your security program’s distinct demands.
- Avoid fixating on product labels, and focus on the essence of what Extended Detection & Response can achieve.
What should I look for in an XDR solution?
A robust XDR solution should offer a comprehensive response framework that spans multiple layers of defense.
The capability to automatically prevent a wide array of threats, from common malware to sophisticated ransomware attacks.
Also, look for a solution that extends its protection across endpoints, network entities, and user identities.
Another crucial aspect is the ability to analyze threats in real-time.

- End-to-end consolidated cybersecurity;
- Complete visibility across your entire IT infrastructure;
- Faster and more accurate threat detection and response;
- Efficient one-click automated and assisted actioning










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security