Contents:
User provisioning is a digital Identity and Access Management (IAM) process that involves creating employee/user accounts and their profiles and giving them appropriate rights and permissions across the IT infrastructure. User provisioning is also known as account provisioning.
In addition to the account creation and access permissions, this technology also ensures that user accounts are managed and monitored throughout the user’s employment.
User information such as name, job title, attributes, department, and other related data are available through account and access management, enabling organizations to give or deny access based on their needs. Provisioning solutions use a variety of approaches to help companies automate onboarding and other administration workforce procedures (such as new hires, transfers, or promotions).
So, user provisioning starts when new employees are onboarded, and a new account with relevant access permissions is generated for them. The account is managed and updated as they get promoted or transferred. Then, at the time of offboarding, we talk about another process called user de-provisioning.
What Is User Deprovisioning?
The process of de-provisioning involves deactivating or removing a user’s access to apps and systems. This process usually entails disabling the user’s account, revoking their permissions, and excluding them from any groups they have been part of or roles they previously had. Deprovisioning typically takes place when an employee exits an organization or when a user’s access is no longer required.
Within the privileged access management process, it is crucial to carefully handle user provisioning and de-provisioning to prevent breaches and compliance-related issues. Check this set of PAM best practices to find out more about how to safeguard privileged access across your organization.
User Provisioning and Deprovisioning Use Cases
Onboarding. Users who are newly employed need to have their profiles set up with rights according to their roles and ranks. It entails creating new user accounts, configuring an email account, and giving access to programs, data repository, and group memberships, among other things.
Promotion/Transfer. When employees move into new roles, their permissions and rights may change. By granting them the appropriate access permissions, user provisioning helps them to have a smooth transition.
One-off access. Organizations may hire individuals or entities outside the organization who might require temporary access to emails or other resources. They must ensure that one-time user provisioning is handled quickly and that deprovisioning is implemented as soon as the one-off event is completed.
Offboarding. When an individual decides to leave a company, their user account needs to be immediately disabled and deleted from the system. Keep in mind that allowing former employees access could seriously jeopardize your security plan.
Support or technical problems. In the event that a new hire forgets their password or runs into an issue with their account, then the account will need to be provisioned once again. When this happens, the previous account of the same user should be disabled and deleted.
Types of User Provisioning
Types of user provisioning include:
Self-service user/account provisioning
Users are responsible for some parts of the user provisioning process, like changing and managing their passwords.
Discretionary user/account provisioning
Users are given access to corporate resources such as data and apps by an IT admin.
Workflow- based user/account provisioning
User access to applications and data is allowed depending on workflow requirements after obtaining the necessary permissions.
Automated user/account provisioning
User accounts are handled according to a predetermined set of rules via a centralized user provisioning solution. This way, IT administrators are able to quickly and thoroughly oversee user accounts and access levels.
The User Provisioning Process
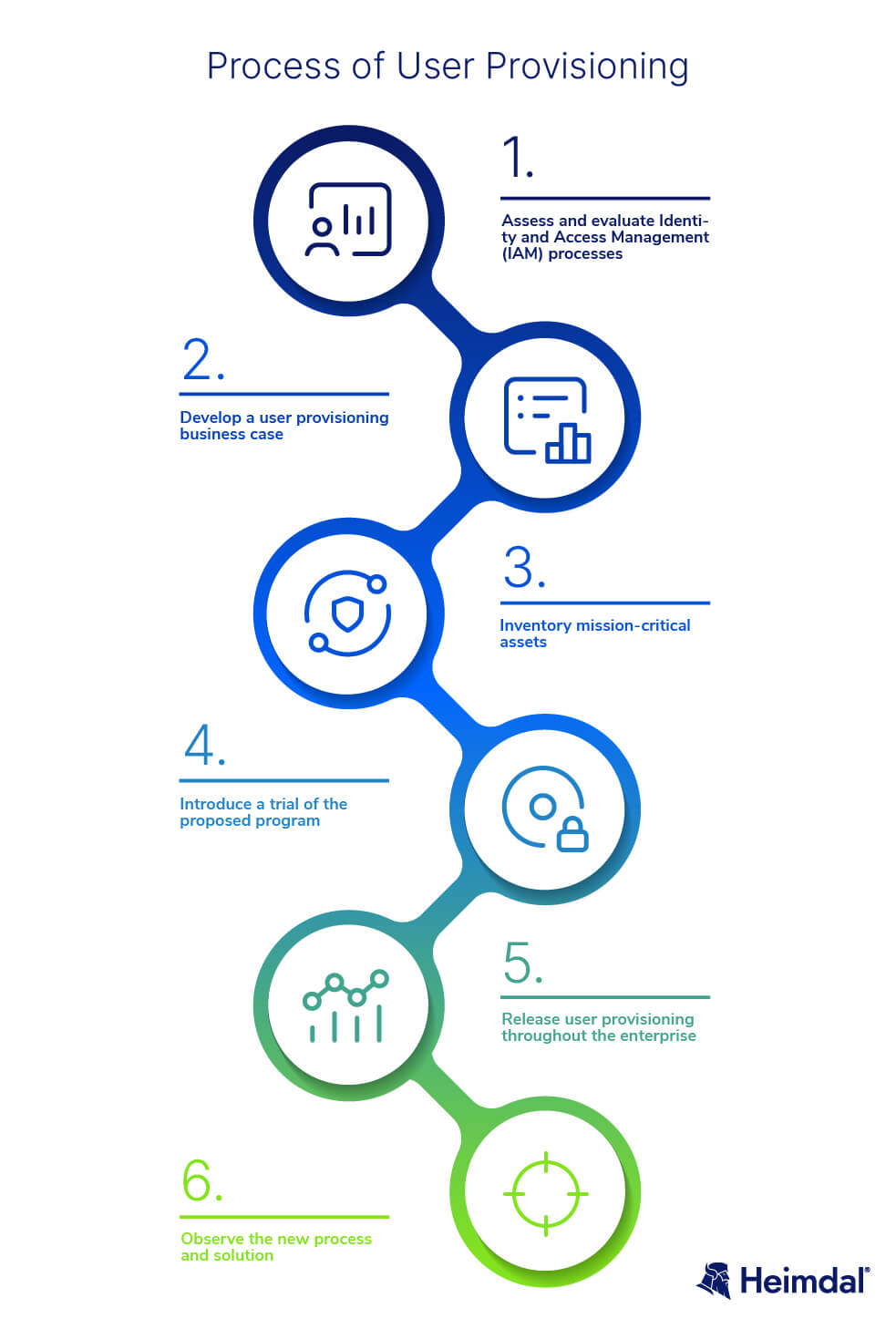
The steps illustrated in the picture above can be used to set up a user provisioning process or to reorganize an ineffective or non-scalable initiative. Let’s take a closer look at the process:
- Assess and evaluate Identity and Access Management (IAM) processes
Take into account maturity level, effectiveness, security, as well as responsiveness, and usability.
- Develop a user provisioning business case
A business case should cover a thorough analysis of how a user provisioning tool will help the company increase security, reduce risks, and boost productivity. It’s critical to develop a compelling business case that supports the organization’s risk management and goal to save money and time.
- Inventory mission-critical assets
Before moving forward with the process, make a list of the organization’s most crucial applications and critical systems.
- Introduce a trial of the proposed program
Engage employees at all organizational levels, including executives, and gather feedback to factor in before the launch.
- Release user provisioning throughout the enterprise
Keep the process rolling by using checklists, status meetings, and the identified internal resources.
- Observe the new process and solution
Monitor user provisioning requests and responses, evaluate KPIs, and iterate to upgrade the initiative as you scale while removing the old process.
Benefits of User Provisioning
Improved security
There may be situations when employees are given the wrong access privileges. In the event that these user accounts are compromised, extremely confidential data may be lost. User provisioning allows for a more flexible setup by making sure that employees have access only to those assets they are permitted to use, safeguarding the network from illegitimate usage.
Reduced costs
The cost of identity and account management processes is reduced thanks to onboarding and offboarding operations being automated.
Increased efficiency for IT admins
User provisioning solutions minimize the time needed to configure and update system access controls while also allowing to update user access or temporarily suspend a user. It saves your IT professionals a lot of time and allows them concentrate on more important tasks.
Reduced complexity
IT admins can use a centralized system to automate provisioning and handle a significant number of application accounts, thus minimizing human error and complexity.
Provides Role-based Access Control (RBAC)
It is hard to foresee which systems an employee will access without having someone to keep an eye on the usage. It’s a common issue in user access configuration that user provisioning technologies address. The system makes sure that access rights are only given based on the user’s position/role inside the company.
User provisioning enables the distribution of granular role-based access controls while helping an organization tailor access depending on internal laws and regulations.
Efficient auditing
Legal authorities can effectively perform audits thanks to the consolidated repository of user access data and information on both inactive and active users provided by user provisioning solutions. Also, compared to conventional systems, which could take days to conduct audits, automated user provisioning solutions can complete them in just a few hours.
Better user experience
By automating the process of setting up access, user provisioning enables employees to swiftly ramp up in a new environment and saves a significant amount of time. This significantly improves user experience and reduces the number of requests to the help desk for access to various applications.
Allows integration with Single Sign-On (SSO)
User provisioning and Single Sign-On (SSO) can be consolidated if they are both from the same vendor. It cuts down on human errors and significantly reduces security administration time.
Protects sensitive data
It’s important for companies to have control over their employees’ access levels. By implementing user provisioning, IT departments can track and keep tabs on which devices are being accessed, by whom, and from what location. By doing so, security risks are addressed, and critical data is protected and kept secure.
Also, when a worker decides to leave an organization or is fired, no one can predict their behavior. Having continued access to critical programs and information even after leaving the company could easily result in data theft or a security breach. User provisioning quickly disables former employees’ access to applications, protecting the company’s private data.
Makes password management simple
Malicious actors can easily breach an organization’s security perimeter by taking advantage of weak passwords. With user provisioning systems, organizations can rest assured that the right password policies are in place and guidelines about the complexity, expiration, and reuse of passwords are followed.
User Provisioning Best Practices
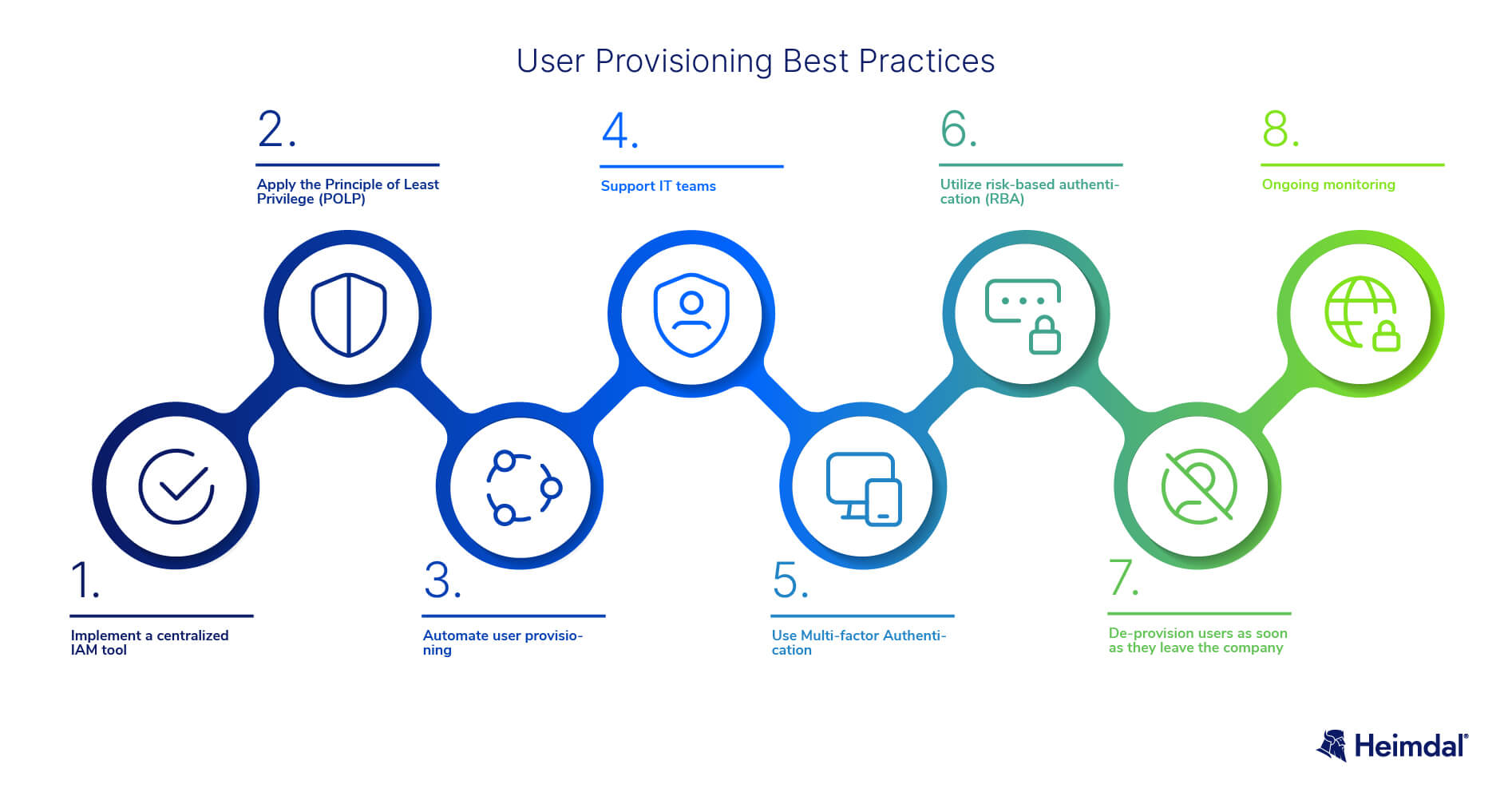
Implement a centralized IAM tool
Your Identity and Access Management system will keep track of new accounts and determine which privileges are used by employees. It will also notify the IT admins regarding the privileges that are not being used so that they can remove them.
Apply the Principle of Least Privilege (POLP)
According to the principle of least privilege, users should only be given access rights to the IT assets they absolutely require and only for as long as is necessary for them to complete their tasks.
Automate user provisioning
For most companies, manually managing user provisioning is ineffective in terms of security and wastes valuable IT resources.
Support IT teams
Create policies for sharing and limiting access, forms for team members to complete when joining, leaving, and transferring, and provide clarity regarding responsibilities and the access that each needs to the company resources.
Use Multi-factor Authentication
This authentication technology known as Multi-factor Authentication (MFA) requires two or more verification factors for gaining access to apps, devices, and other IT resources.
Utilize Risk-Based Authentication (RBA)
Through RBA you can determine the risk when a user performs a specific action; block the user and alert the IT team when potential issues are detected.
Implement deprovisioning as soon as someone leaves the company
Ideally, your admin should be able to de-provision users as soon as they leave the organization, which would include deleting them from the directory and instantly deactivating their accounts for all resources controlled by the directory.
How to Choose the Best User Provisioning Product for Your Company?
Below you can find some key features you should be aware of when choosing a user provisioning solution for your organization.
- Is comprehensive and scalable;
- Provides a positive, straightforward user experience;
- Offers automated features with self-service where possible;
- Has capabilities that help with regulatory compliance needs;
- Reduces the cost of the technology through internal improvements;
- Includes comprehensive analytics and reporting.
What Does Heimdal® Bring into the Whole Identity Security Landscape?
As we saw, both user provisioning and user deprovisioning are components of the Identity and Access Management (IAM) framework and cater to such needs successfully by controlling and tracking the access rights and privileges of various users.
Heimdal recommends integrating Privileged Access Management within your IAM strategy and comes up with a cutting-edge PAM solution – Privileged Access Management – that helps organizations easily handle user rights, while enhancing their endpoint security. As it’s the only tool to auto-deny/de-escalate admin rights on infected machines (if you add the Application Control module into the mix), it substantially increases the cybersecurity in your organization.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Conclusion
Organizations that implement user provisioning solutions are able to properly provision and de-provision access to data and applications, thereby lowering the risk of data breaches, which are costly and can have protracted consequences for the company’s image and brand.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










