Contents:
Single Sign-On (SSO) is an authentication method that allows a user to securely authenticate with multiple applications and websites by using solely one set of login information (eg. username & password).
In a nutshell, SSO simplifies the user authentication process. It happens when a user signs in to an app and is automatically authenticated with other related applications, no matter the domain, platform, or technology they are using. For instance, when logging into Google, the user’s credentials are instantly authenticated across connected services like Gmail and YouTube without having to sign in separately.
Enterprises, small and midsize businesses, and even individuals can adopt SSO to make managing multiple usernames and passwords across various accounts and services easier.
How Does Single Sign-On Work?
Single Sign-On systems perform identity verification, a critical Identity and Access Management (IAM) function, which is a set of policies, processes, and technologies that help organizations manage the users’ identities and devices, verify these identities for access to data or other assets and keep track of who has accessed what. This is essential for granting user access permissions and making sure users only have the level of access they require to successfully perform their responsibilities.
SSO functions by sharing and confirming login information between identity and service providers. A Service Provider (SP) is usually a seller who offers products, solutions, and services to users and companies, like a website or application, whereas an Identity Provider (IdP) is a system component that creates, manages, and stores digital identities and provides authentication services to verify users.
These trusted providers allow users to utilize SSO to access websites and apps and improve the user experience by reducing the need to remember an excessive number of passwords (an issue commonly known as password fatigue).
SSO services don’t keep track of user IDs or data. In lieu, they typically operate by comparing data from an identity management service or database with login credentials provided by a user.
Here’s how the process usually looks like:
Step 1: The user navigates to the website or program they want access to, also known as the Service Provider.
Step 2: As part of a request to verify the user, the SP provides the SSO system, also known as the Identity Provider, a token containing some user information, such as the email address.
Step 3: Before granting access to the Service Provider app, the Identity Provider determines whether the user has already been authenticated.
Step 4: When the Identity Provider confirms the provided credentials, it returns a token to the Service Provider, indicating that the authentication was successful.
Step 5: The Service Provider receives this token through the user’s browser.
Step 6: The token received by the Service Provider is validated based on the trust relationship established during the initial configuration between the SP and the IP.
Step 7: The user gets access to the Service Provider.
Single Sign-On Authentication Types
Federated identity
Federated Identity Management (FIM) or federated SSO expands the scope of conventional SSO systems by bringing together more enterprises under a single authentication process. While standard SSO permits access to multiple systems within a single organization, federated identity allows access to multiple systems across many different organizations. Both methods, however, authenticate the user using only one identity.
Open ID
Open ID is a decentralized approach to SSO systems that operates on the idea of a Relying Party (RP) and an Identity Provider (IDP). The RP is the website or application that wants to confirm the user’s identity, while the IDP handles authorization by logging the user’s selected identity, which is represented by an URL identifier (OpenID).
OAuth
OAuth (Open Authorization) is an open standard authorization system that allows users to securely share account information with third-party services like Google and Facebook without revealing their credentials. The third-party service receives an intermediary (the access token), which then authorizes specific user data. The term used to describe this procedure is “authorization flow”.
Kerberos-based SSO
Kerberos is a computer network security protocol that verifies service requests sent between two or more trusted hosts over an insecure network such as the Internet. This system was designed to prevent malicious actors from entering a private network. It functions as a gateway between users and untrusted networks.
Smart-card authentication
Instead of using software to confirm the same set of credentials as in traditional SSO systems, hardware devices such as smart-cards can be utilized to achieve the same results.
Security Assertion Markup Language
SAML is an open federation standard that allows users to be verified by an Identity Provider, who can then provide an authentication token to another application (Service Provider). SAML enables the SP to work without performing its own authentication and passing the identity to integrate users from both inside and outside the company. It enables the exchange of security credentials with an SP over a network, which is frequently an app or service.
Advantages
In addition to being significantly easier and more efficient for users, SSO is generally thought to be more secure. Here are some advantages of SSO:
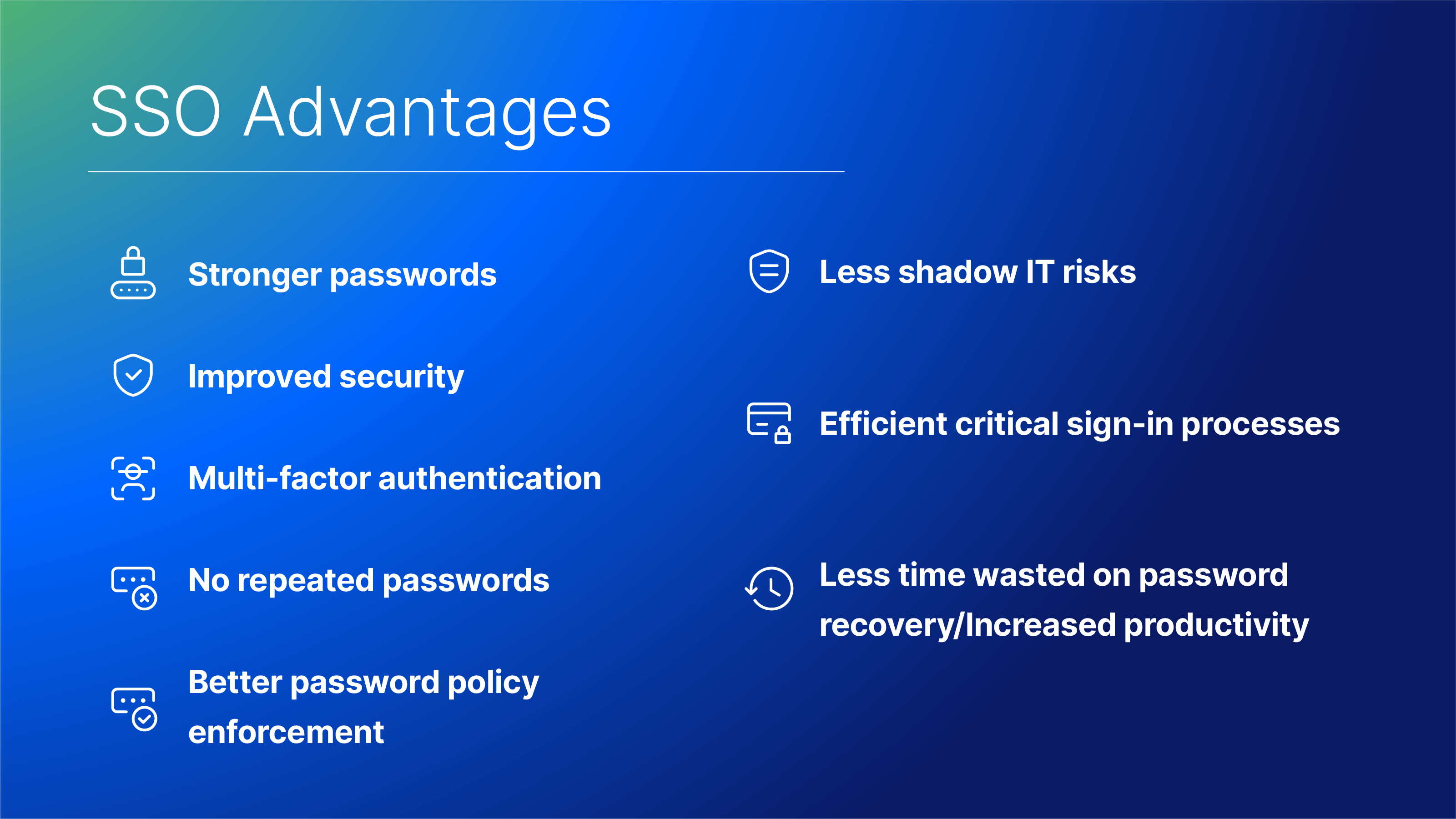
Stronger passwords
Because users only need to use one password, SSO makes it easier for them to create, memorize, and use more complex passwords. Researchers noticed that most SSO users actually create stronger passwords. With takes us to the next point…
Improved security
There are fewer attack vectors for cybercriminals due to the fact that SSO eliminates the need for numerous passwords. This reduces the risks for your business’s partners, clients, and employees as well, particularly when Multi-Factor Authentication (MFA) is added on top of Single Sign-On (SSO). Also, administrators can quickly see and update access levels, protecting your business from resentful former employees.
Multi-factor authentication
Multi-Factor Authentication (also known as MFA) is a security method that requires users to verify their identities by giving additional proof before gaining access to a resource such as an application or website. For instance, a user might be asked to provide a code that pops up on their smartphone in addition to the username and password. MFA is significantly more secure than relying solely on a password. SSO enables MFA to be activated at a single point rather than having to activate it for multiple applications, which may be inconvenient.
No repeated passwords
Users are more prone to reuse passwords across services when they have to remember them for multiple applications and sites, which is an issue known as password fatigue Using the same password for different services poses a significant security risk. If the password database for a service is breached, hackers can use the password to compromise all of the user’s other services. SSO prevents situations like these by reducing all logins to a single login.
Better password policy enforcement
With only one point to enter passwords, SSO gives IT teams a means to effectively enforce password security guidelines. For instance, many organizations mandate that users change their passwords on a regular basis. Password resets are simpler to implement with Single Sign-On since users just need to reset one password rather than often changing it across multiple apps and services.
Less shadow IT risks
Shadow IT takes place when users bypass their organization’s security protocols to use applications, devices, websites, or software that have not been approved for official use. SSO assists organizations in avoiding this by tracking which applications employees use, reducing the likelihood of identity theft or data loss, and enforcing compliance rules.
Efficient critical sign-in processes
According to some studies, users spend a lot of time entering and resetting passwords. Although this may seem unimportant, it matters when split-second decisions must be made, as in the case of sectors like healthcare or law enforcement. Users who have SSO enabled have immediate access to the applications they need to manage any critical situation.
Less time wasted on password recovery/Increased productivity
In addition to the security benefits mentioned above, SSO reduces wasted time for internal teams. IT spends less time assisting users in recovering or changing their passwords for multiple applications, while users spend less time logging into numerous apps to complete their tasks. This could increase business productivity.
Single Sign-On Cons
Although SSO has its benefits, let’s also take a look at the main disadvantages:
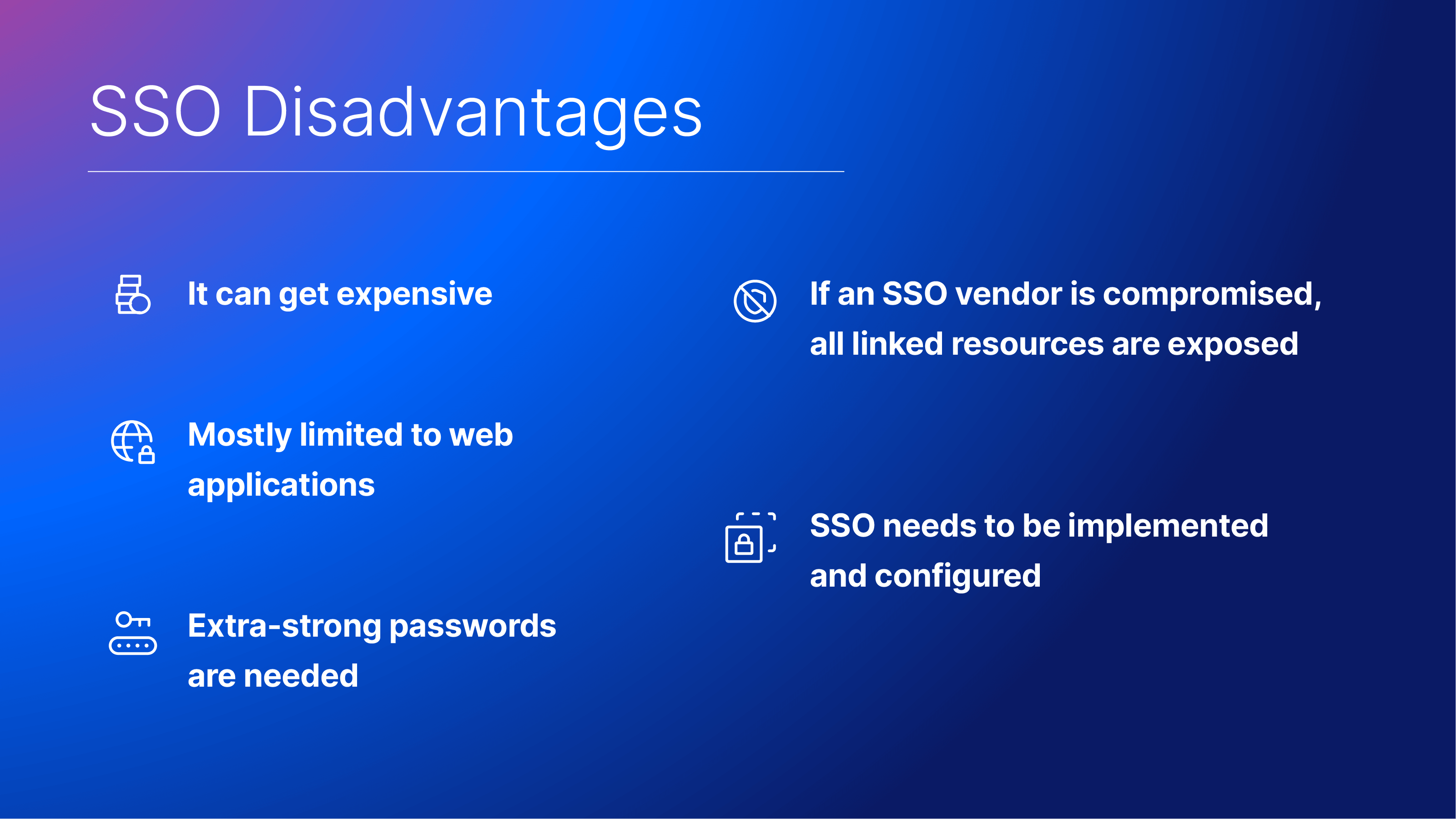
It can get expensive
Simply put, having an SSO system in place can quickly become costly. SSO can be extremely helpful for smaller businesses, but it may also prove to be a significant financial burden. Some SSO providers charge per feature, and the majority of the core features are add-on charges, so the fees can quickly add up.
Mostly limited to web applications
Identity Access Management (IAM) is a vast field that encompasses many of IT’s responsibilities. IAM includes much more than just controlling access to web apps with SSO, thus IT administrators must use a variety of other technologies in addition to web app SSO to develop a comprehensive IAM solution. Users still need to be able to access their computers, WiFi networks, file servers, on-premises software, and many other things. SSO for web applications can’t help with those IT assets.
Extra-strong passwords are needed
SSO only requires end users to remember one password, but it is ideal if that password is lengthy, hard to guess, and well-protected. Although this typically improves identity security as a whole, it also increases the risk that a user will forget or disclose this password, rendering the advantages of SSO useless.
If an SSO vendor is compromised, all linked resources are exposed
Since Single Sign-On is connected to multiple important resources, entire user bases would be exposed in the event that an SSO provider was the target of an attack. If an end user’s SSO portal is impacted, their access to those apps is also jeopardized if MFA is not used.
SSO needs to be implemented and configured
As with many other IT technologies, IT administrators must devote the necessary time and effort to implement and customize their SSO service to their company. In addition to the applications needing to be configured, using a third-party IdP makes integration difficult and complex.
How Can Heimdal® Help?
Centralized authentication systems, such as SSO, are critical components of implementing a zero-trust strategy. Zero-trust security ensures that only the right users have the appropriate access level to the right resources, while also making the access process easier for them.
This is exactly what Single Sign-On does, allowing users to authenticate once and get access to multiple services, all while improving security by eliminating password reliance and incorporating additional security measures such as multi-factor authentication (MFA).
It’s about time to tell you that Heimdal comes with an amazing solution that facilitates zero-trust implementation effortlessly: it’s called Privileged Access Management and supports a zero-trust function.
PAM is an automated tool that permits you to escalate and de-escalate user rights, giving you full control and protection over privileged permissions within your organization.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








