Contents:
On a computer, system access is gained based on privilege depending on each user`s role. For example, there are certain objects that only an administrator can access, while a regular user or someone logged in as a guest has limited access inside said system.
Where does the Access Control List (ACL) fit in all this? As we define the ACL and its purpose, we will better understand why exactly it is necessary and how it helps control access to network endpoints as well as traffic flow between internal networks, thus reinforcing your organization`s security policy.
Definition
An access control list, abbreviated as ACL, is a list of rules that outline which users or systems are granted or denied access to a particular object or system. The rules describe the packet matching conditions, such as the source address, destination address, and port number of packets.
Each ACL has one or more access control entries (ACEs) consisting of the name of a user or group of users. For each of these groups or roles, the access privileges are stated in a string of bits called access mask.
Access control lists can also be installed in routers or switches, where they act as filters managing which traffic can access the network. By placing them in multiple locations throughout the network you can ensure better protection from unwanted traffic.
Benefits of ACL
- Probably the most obvious benefit of using ACLs is preventing unauthorized access, which could further lead to information leaks or malware infection inside a network.
- Access control lists also help organize traffic to improve network efficiency, while giving network admins more control over users on their computer systems.
- Further, an ACL simplifies the way that users are identified, meaning that only approved users and traffic have access to the system.
Types of ACLs and How they Work
Basically, when a user makes a request to access an object, the machine’s operating system checks the ACL to verify if that person is indeed allowed to perform the action they desire. If the list dictates the user does not have clearance to open, use, or modify that particular object, access will be denied.
Further, you can also categorize the kinds of traffic you want to allow to access the network and then apply those categories to the ACL. Let`s say you are creating a rule that enables all email traffic to pass through to the network, you can choose to block out all traffic that contains executable files.
There are two main types of ACLs:
Filesystem ACLs
These manage access to files and directories. They give the instructions that establish user access permissions for the system and their privileges once the system has been accessed. A filesystem access control list relies on a table that informs the computer’s operating system which users have which access privileges. The table clearly states the users that are allowed to access specific objects, such as directories or files on the system. Every object on the computer has a security property that links it to its associated access control list. On the list, there is information for every user that has the requisite rights to access the system.
Networking ACLs
Networking ACLs are different in that they are installed in switches and routers by the administrator or even the manufacturer. In a nutshell, they act like traffic filters by managing access to a network. To do this, networking access control lists provide instructions to switches and routers as to the kinds of traffic that are allowed to interact with the network. They also dictate what each user or device can do once they are inside. These ACLs also specify user permissions once inside the network.
Furthermore, ACLs can be categorized by the way they identify traffic as standard or extended. A standard access control list will block or allow an entire protocol suite using source IP addresses and is usually implemented close to the destination that it protects, while an extended ACL blocks or allows network traffic based on a more differentiated set of characteristics including source and destination IP addresses and port numbers, as opposed to just source address alone. Extended access control lists are usually found implemented close to the source.
Components of an Access Control List
Based on the traffic they are meant to filter, ACL entries consist of several different components, such as:
- Sequence number – The sequence number shows the identity of the object in the ACL entry.
- ACL name – This identifies an ACL using a name instead of a number. In some cases, the router will allow both numbers and letters.
- Comments – Some ACLs enable users to add comments, as extra descriptions of the entry.
- Statement – A statement either allows or denies a source using a wildcard mask or address. A wildcard mask tells a router which bits of an IP address are available for a network device to examine and determine if it matches the access list.
- Network protocol – Enables admins to allow or deny traffic based on a network protocol, such as IP, Internet Control Message Protocol, TCP, User Datagram Protocol or NetBIOS.
- Source and destination – Defines a specific IP address to block or allow or an address range based on Classless Inter-Domain Routing.
- Log – Some ACL devices keep a log of objects that the access control list recognizes.
- More advanced ACL entries can specify traffic based on certain IP packet header fields, like Differentiated Services Code Point, Type of Service or IP precedence.
Placement of ACL
ACLs are well suited to network endpoints that require high speed and performance, not to mention security.
Network administrators may choose to place an access control list at different points in the network depending on its structure. ACLs are often placed on the edge routers of a network, giving the ACL a chance to filter traffic before it reaches the rest of the system.
Edge routers with ACLs can be placed in the demilitarized zone (DMZ) between the public internet and the rest of the network. A DMZ can be defined as buffer zone, with an outward-facing router that provides general security from all external networks. It also features an internal router that separates the DMZ from the protected network.
DMZs may contain different network resources, like application servers, web servers, domain name servers or virtual private networks. Placing an ACL between the internet and the DMZ as well as one between the demilitarized zone and the rest of the network will result in different configurations, with each setting being designed to protect the devices and users that come after each access control list.
Difference Between RBAC, ABAC and ACL
Role-Based Access Control (RBAC) is a method which limits system access to authorized users based on their role rather than their identity, and from a security standpoint, RBAC provides superior security to ACL. With an access control list, there is an entry for each user, which is linked to the security attributes of each object. Write access can be granted, but there is no way of controlling how exactly the user might change the file.
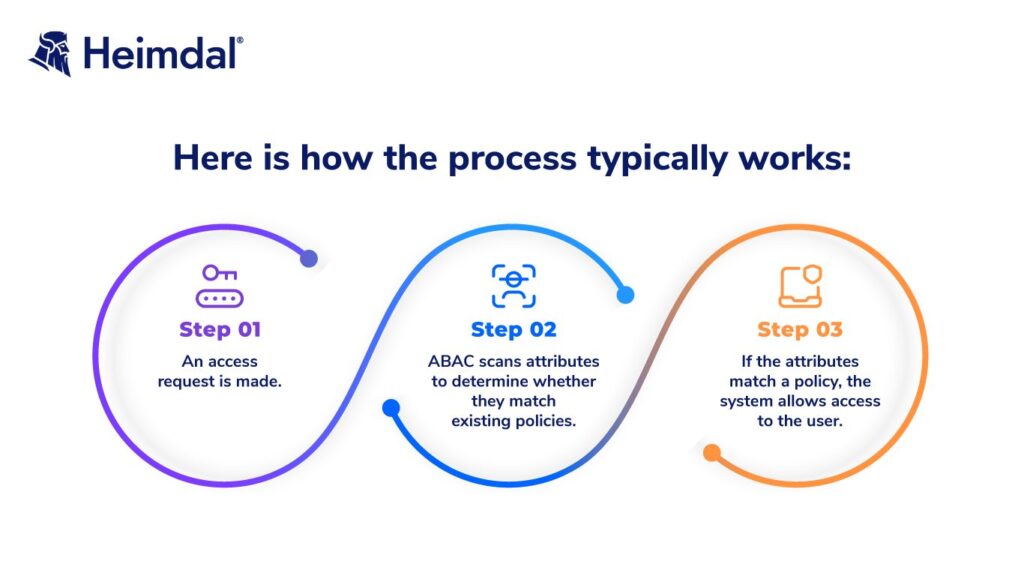
Attribute-Based Access Control (ABAC) detaches itself further from ACLs, as it is a system that determines user access based on attributes (or characteristics) rather than roles or specific user identity. It offers a more thorough authorization system that takes into account a larger number of factors, meaning it takes more time and resources.
How Can Heimdal® Help?
Understanding how traffic flows in and out of your network and managing user permissions allows you to implement the best solutions for keeping the organization safe from any kind of cyber threat, as well as keep the systems running as efficient as possible. Heimdal® Privileged Access Management allows administrators to apply the Principle of Least Privilege (POLP), meaning users and applications are given only the necessary access to complete their tasks. Your system admins will be able to approve or deny user requests from anywhere or set up an automated flow from the centralized dashboard.
Heimdal® Privileged Access Management is the only PAM solution on the market that automatically de-escalates on threat detection. Combined with our Application Control, which lets you perform application execution approval or denial as well as live session customization, your business`s safety is most efficiently ensured.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Wrapping up
Cybercriminals are always looking to find a way to obtain unauthorized access to vulnerable systems. Access control lists (ACL) are essential when it comes to securing data. Well implemented control lists will ensure that no unauthorized individuals can access business-sensitive information, thus helping to minimize the risk for a security breach. A powerful access management solution will help you set up your access control and review it regularly to ensure it still fits your organization`s needs.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







