Contents:
It seems that Conti ransomware attacks are taken to another level. Two threat actor groups have started to collaborate, joining efforts for Conti ransomware deployment on targeted systems purposes. The first gang refers to the one dubbed Shatak or TA551 who has started cooperating with another threat actor group named ITG23, also known as Wizard Spider or TrickBot.
How Does This Partnership Between Threat Actors Unfold?
As per an IBM X-Force’s discovery, the two gangs started their collaboration during the month of July this year.
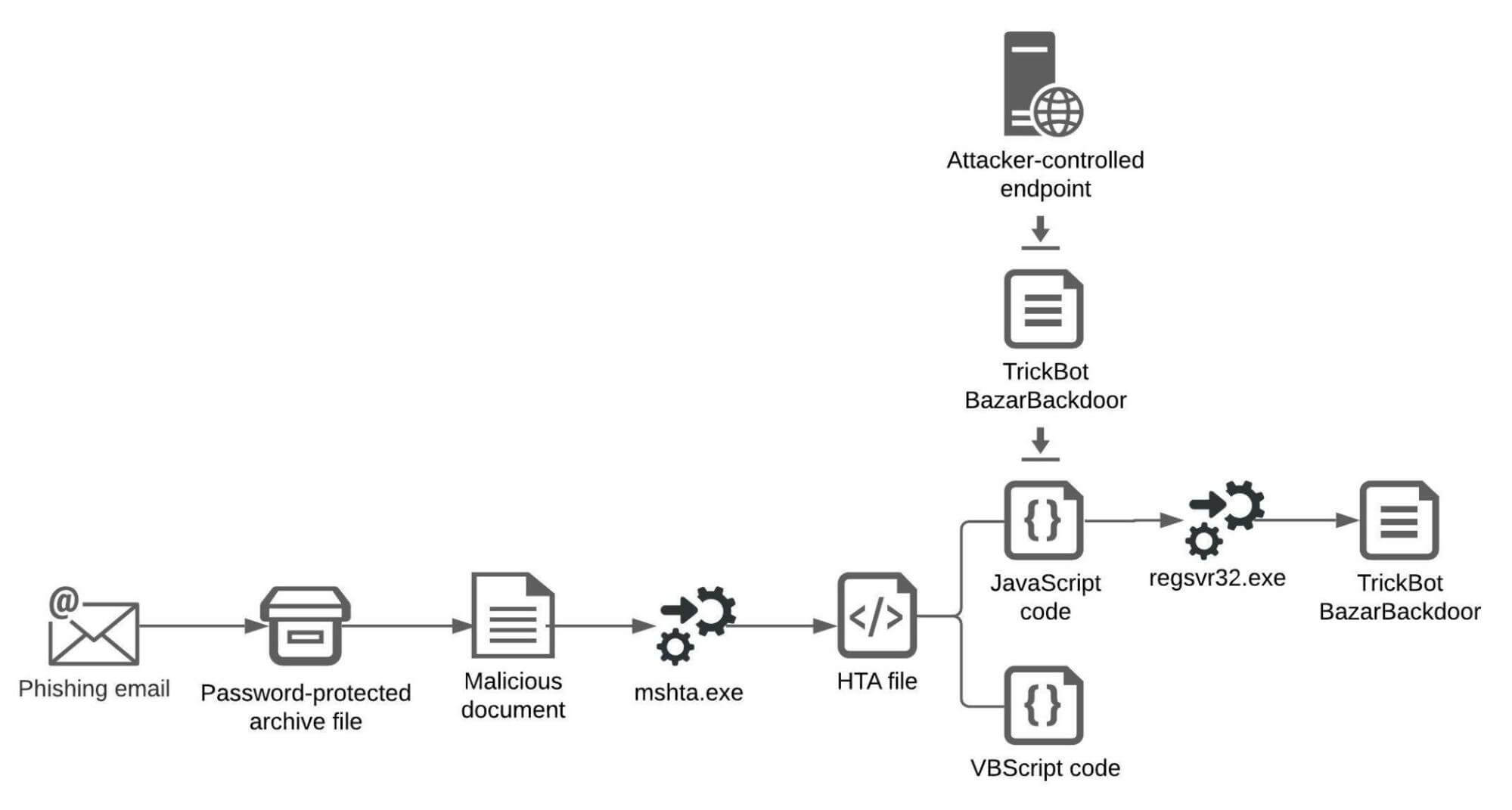
As BleepingComputer describes, the usual attack carried out through this partnership by the two gangs unfolds like this:
- Shatak is the one responsible to deliver a phishing email.
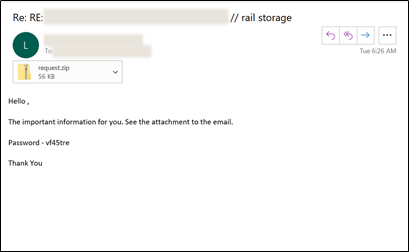
- Inside that malicious email, a compromised file can be found within an archive that can be accessed via a password.
- Common methods of Shatak attacks include stolen reply-chain emails supplemented by these kinds of attachments that are password protected.
- Inside the malicious attachments lie compromised scripts.
- What these scripts do is to perform code execution, code that is base-64 encoded and that will eventually result in the downloading from a remote website and the deployment of the TrickBot malware or the malware dubbed BazarBackdoor.
- After one of the above malware is dropped, it’s ITG23 turn to perform Cobalt Strike beacon deployment on that infected system for persistence purposes.
- Then follows the network reconnaissance by means of the BazarBackdoor dropping. This will help with information like shared computers and resources, users, and domain admins.
- What’s next is credentials, password hashes, and AD data theft, and an attempt to further spread laterally on the targeted network.
- The encryption process is strengthened by the fact that the monitoring feature of Windows Defender is disabled, so alerts will not interrupt the encryption phase.
- Data exfiltration precedes the file encryption stage though, as this is a known technique among ransomware gangs to perform double extortion on their victims.
- Through the data exfiltration process, they manage to transfer the stolen data to an attacker’s controlled remote endpoint and this is possible by means of the ‘Rclone’ tool.
- The final step is, of course, ransomware deployment resulting in the targeted devices being encrypted.
To better understand Shatak’s infection chain, Cybereason’s researchers, who published a report on this topic on the 9th of November, provided an illustration in this sense:
And here is also an image from IBM X-Force that shows what a Shatak phishing email containing the malicious attachment we mentioned above looks like:
It seems that this one is not the only cybercrime partnership out there. According to France’s CERT analysts, TA551 also seemingly partners up with a more recent ransomware gang dubbed Lockean. They were also using phishing email distribution techniques, however, this time the Qbot/QakBot banking trojan was distributed. This banking trojan facilitated the infection path of ransomware families like Egregor, DoppelPaymer, or ProLock.
How to Stay Safe Using Heimdal™’s Solutions?
It’s more and more obvious that ransomware represents a major threat to businesses and users alike. Besides data encryption, more advanced techniques like data exfiltration before blocking the user’s access have facilitated, unfortunately, a more efficient victims’ extortion. Besides the common sense of paying attention to e-mails coming from unreliable sources and containing a potential dubious attachment, Email Fraud Prevention and Email Security tools like ours can help you be a very step ahead of hackers.
Email Fraud Prevention is based on 125 analysis vectors that will build up the perfect shield against Business Email Compromise, CEO fraud, and phishing and Email Security keeps mail-delivered threats away through its spam filter. Combine them with Ransomware Encryption Protection for ultimate threat defense. Complex cyberattacks require complex and various protection tools.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security