Contents:
Hashes are the result of a mathematical function that converts a text string (no matter the length) into an encrypted string of a fixed length. For every given piece of data input, algorithms such as MD5 (Message Digest 5) or SHA (Secure Hash Algorithm) fundamentally generate a unique, fixed-length string – the hash value.
How Do Hashes Work?
Hashing is basically a one-way cryptographic function. Because hashes are irreversible, knowing the output of a hashing method does not allow you to recreate the contents of a file. It does, however, allow you to assess whether two files are similar without knowing their contents.
As a result, the concept of hashes is based on the assumption that the result is unique. We’d have a “collision” if two separate files produced the same digest, and we’d be unable to utilize the hash as a trustworthy file identification.
Taking into consideration that there is no limit to the number of key/value pairs, a hash function can be used to map the keys to the size of the table, thus making the hash value become the index for a specific element.
index = key \text{ } MOD \text{ } tableSizeindex=key MOD tableSize
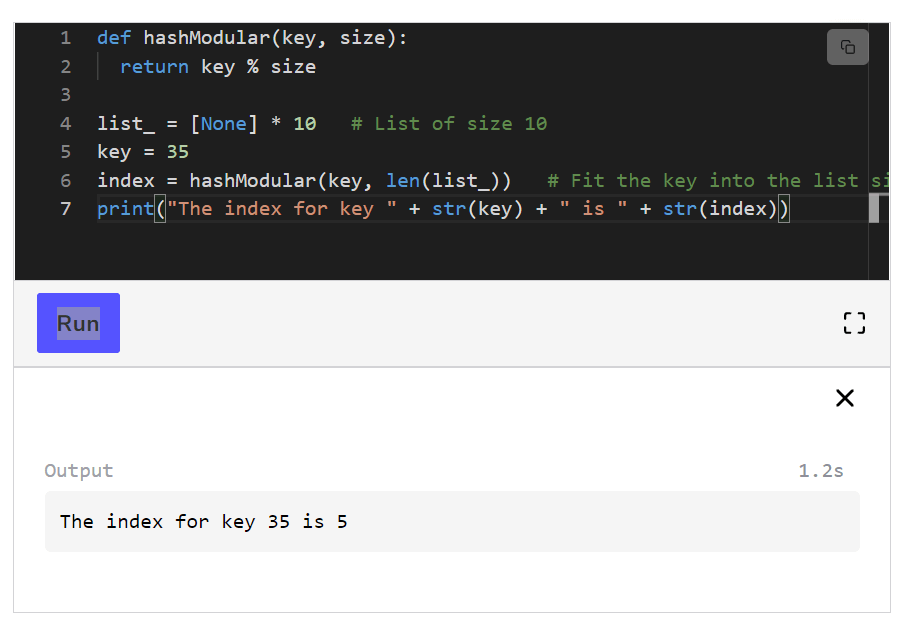
As you can see, by using the hashing function in this situation the hash resulted as output is within the limits of the table size.
What Is Hashing Used for?
We may utilize a file’s unique identifier in a variety of ways once we get it. Some older antivirus software relies solely on hash values to detect whether or not a file is dangerous, without looking at its contents or behavior. This is accomplished by maintaining an internal database of hash values associated with known malware. When the AV engine scans a system, it produces a hash value for each executable file on the user’s PC and compares it to its database.
In the early days of cyber security, this must-have appeared like a clever approach, but in hindsight, it’s easy to see the problems in hash values dependence.
The use of hashing in cybersecurity and web authentication is a common practice. For example, it can be used to securely store passwords in a database, but can also ensure the security of other pieces of data including files and documents.
What Are Hashing Algorithms
Hashing algorithms are as abundant as encryption algorithms.
It’s important to note that there are a few that are being used more often than others, like MD5, SHA-1, SHA-2, NTLM, and LANMAN.
MD5
This is actually the fifth version of the Message Digest algorithm.
MD5 works by creating 128-bit outputs and was a commonly used hashing algorithm.
This changed when, unfortunately, weaknesses in the algorithm started to surface, with most of the weaknesses manifesting themselves as collisions, thus MD5 started to be phased out.
SHA-1
This is the second version of the Secure Hash Algorithm standard, SHA-0 being the first. SHA-1 creates 160-bit outputs. SHA-1 is one of the main algorithms that began to replace MD5 after vulnerabilities were found. SHA-1 gained widespread use and acceptance. SHA-1 was actually designated as a FIPS 140 compliant hashing algorithm.
SHA-2
This is actually a suite of hashing algorithms. The suite contains SHA-224, SHA-256, SHA-384, and SHA-512. Each algorithm is represented by the length of its output. SHA-2 algorithms are more secure than SHA-1 algorithms, but SHA-2 has not gained widespread use.
LANMAN
The Microsoft LAN Manager hashing algorithm is known as LANMAN.
Legacy Windows systems utilized LANMAN to store passwords. The hash was created by LANMAN using DES methods.
The problem with LANMAN’s implementation of the DES algorithm is the fact that it isn’t particularly secure, therefore making the hash vulnerable to brute force assaults, and allowing malicious actors to break the LANMAN passwords in just a few short hours.
NTLM
The NT LAN Manager algorithm is also known as NTLM.
This algorithm works by hashing passwords during the authentication. NTLM is the LANMAN’s successor.
NTLMv2 was used after NTLM. For hashing, NTLMv2 employs the HMAC-MD5 method.
Wrapping Up
Hash values also assist with threat hunting since they’re handy when you find danger on one computer and want to check your whole network for the existence of that file.
When comparing hashes, we save significant time and processing power, as opposed to analyzing and comparing entire files, which is cumbersome, if not impossible.
Hashes are an important tool in computer security because they can accurately inform us whether two files are identical, as long as safe hashing methods are used to avoid collisions.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










