Contents:
Initially employed as a bank Trojan, Trickbot is now one of the most powerful tools available to cybercriminals who can gain remote access to infected machines to deliver their own malware, including ransomware.
No Sign of Slowing Down
In May 2021, security researchers Bogdan Botezatu and Radu Tudorica noticed their monitoring systems started to pick up an updated version of the vncDll module used by Trickbot against select high-profile targets.
According to their report,
This module is known as tvncDll and is used for monitoring and intelligence gathering. It seems to be still under development, since the group has a frequent update schedule, regularly adding new functionalities and bug fixes.
Botnets are entire networks of computers controlled and instructed to do a lot of things, such as attack other computers, send spam or phishing emails, deliver ransomware, spyware, and many other similar malicious acts. They are formed when hundreds or thousands of hacked devices are enlisted into a network run by threat actors, which are often then used to launch denial-of-network attacks to pummel businesses and critical infrastructure with bogus traffic with the aim of knocking them offline.
Trickbot is pretty much the same. The Russia-based transnational cybercrime group behind the operation, Wizard Spider, uses Trickbot, Ryuk, and Conti ransomware as their primary tools while constantly improving their infection chains by adding new functionality modules to increase its efficiency.
It is believed that the Health Service Executive cyberattack in Ireland could’ve been conducted by this very organization. The cybercrime group has been known to have a tendency towards wire fraud previously when they also used Diavol and Conti threat payloads in ransomware attacks back in early June this year.
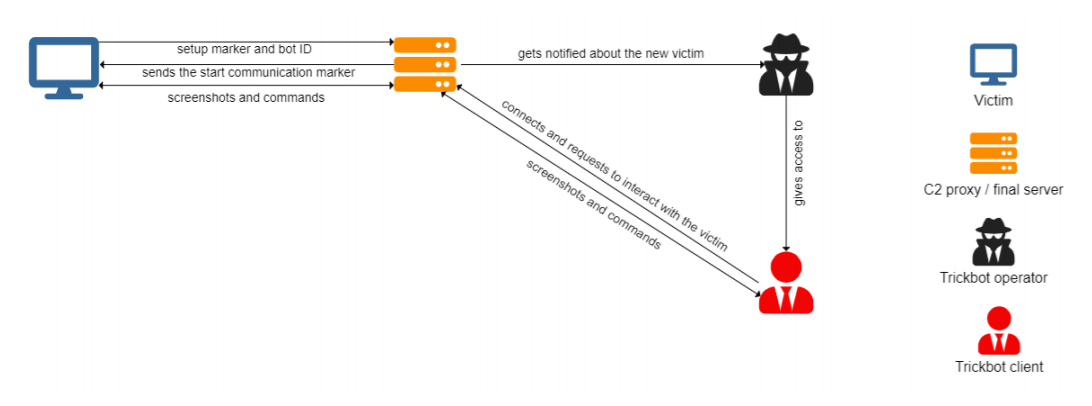
Complex Infrastructure
Last October, contributions from Black Lotus Labs revealed that
TrickBot has evolved to use a complex infrastructure that compromises third-party servers and uses them to host malware. It also infects consumer appliances such as DSL routers, and its criminal operators constantly rotate their IP addresses and infected hosts to make disruption of their crime as difficult as possible.
Now, the threat actor is actively developing an updated version of the “vncDll” module – “tvncDll”, that it employs against select high-profile targets for monitoring and intelligence gathering.
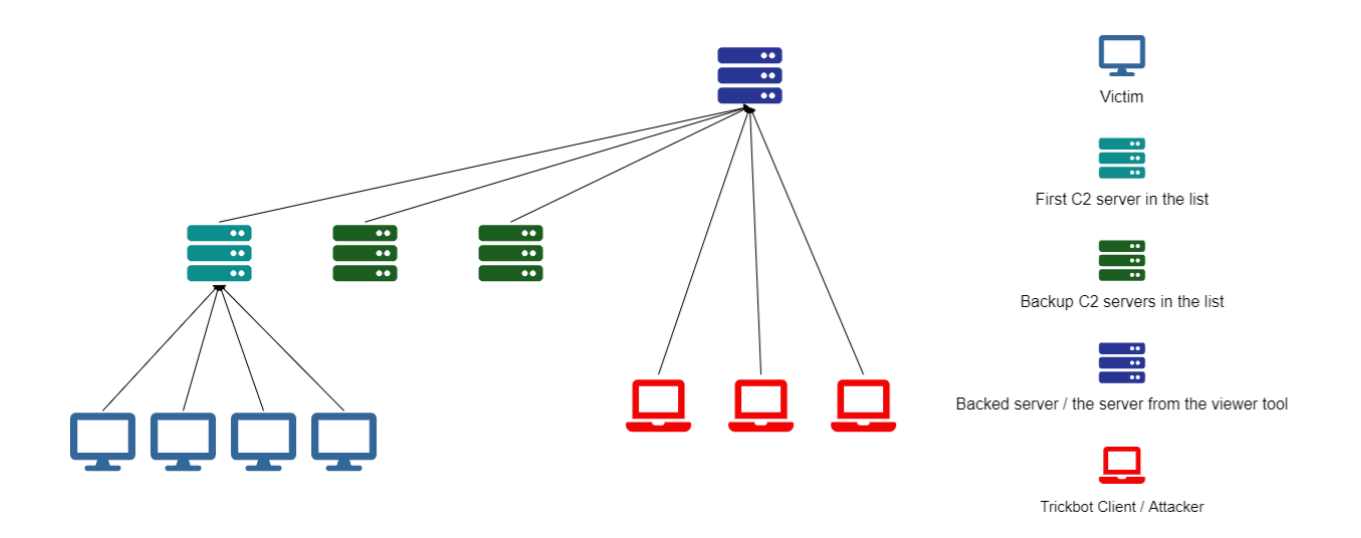
According to the researchers, this new module uses a custom communication protocol, which only makes it harder to understand what data is being transmitted without prior knowledge. What’s more, the module communicates with the C2 servers defined in its configuration file called vncconfand which includes a list of up to nine IP addresses. These servers act as mediators between the victims and attackers, one of their roles being to enable access to victims behind firewalls.
As the report shows, Trickbot’s C2 servers spread on almost all continents, with the largest number located in North America – 54. The number of C2 servers has increased significantly this year, jumping from around 40 in January to over 140 in June.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security