Contents:
TrickBot Trojan, initially known as a banking trojan, but resuming its activity to distributing malware lately, is now improving the features of its old banking module to share its malicious contribution to the financial cybercrime market again. The Kryptos Logic Threat Intelligence Researchers have revealed in a report that TrickBot Trojan is working on some brand-new capabilities known as MitB (man-in-the-browser). These target online banking credentials and bear precise resemblance to the Zeus pattern.
What Is TrickBot Trojan and How Did It Emerge?
A banking trojan is basically a piece of software threat actors use to steal financial information in order to perform identity theft, unauthorized transactions, or transfer users’ money to their malicious accounts. They can do it through keylogging, a method that has the role to track your keyloggers, a redirection link to a compromised page, scanning through files where users store credentials, or by capturing and recording the screen.
TrickBot Trojan first made its appearance in 2014 and it was classified as a banking trojan at that time. Then, it extended its actions and used them to spread malware distributed also via Emotet malware in 2017. It was created to gain access to private information such as social security numbers, credit card info, and credentials.
What Does This New Version of Trickbot Trojan Do?
The New Version of TrickBot Trojan Module follows the Zeus pattern, researchers explained.
Due to Zeus having been the gold standard for banking malware, Zeus-style webinjects are extremely popular. (…) It is not uncommon for other malware families to support Zeus-style webinject syntax for cross-compatibility (4Zloader, 5Citadel, to name a few).
TrickBot Trojan used to work via redirected links through its web-injecting module. A user could access a usual banking site and be immediately redirected to a malicious one belonging to threat actors. This functioned through 2 types of web injections, one was static and the other was dynamic. The static one could lead the user to the hacker’s website where his credentials were stolen, while the dynamic function worked a little bit more complex in a transparent way, the command and control server of TrickBot receiving the server response, the source being changed and filled in with malware and then returned to the user as though there was nothing wrong.
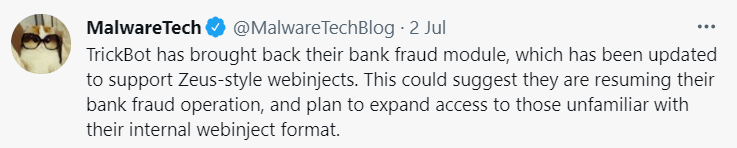
The new TrickBot Trojan version has a Zeus embedded flavor and it’s named injectDll. As Threatpost describes, it works like this:
- Local SOCKS servers are used;
- Threat actors carry out the web injection by proxying traffic through the above-mentioned servers and a packed payload is injected into the user’s browser;
- They modify the traffic that streams through the listening SOCKS proxy;
- This happens when users visit malicious URLs that are hardcoded into the module;
- This can be done through socket APIs and ‘CertVerifyCertificateChainPolicy’ and ‘CertGetCertificateChain’ that block any certification errors, thus the victims receive an accurate response;
- Thus, a self-signed TLS certificate is created that adjoins their certificate store.
This is an additional dynamic way to perform the web injection where malevolent code is inserted into the banking websites. TrickBot Trojan is being said to have similarities in code with the IcedID Banking Trojan too.
Since June 2021, TrickBot has been seen pushing a new module on infected computers. The new module contains a revamped version of its old banking component that tries to intercept credentials for e-banking websites.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security