Contents:
The researchers at FortiGuard Labs linked a new ransomware strain dubbed Diavol ransomware to Wizard Spider.
It looks like Diavol and Conti ransomware payloads got deployed on different systems in a ransomware attack that was blocked back in June.
The researchers believe that the two ransomware families’ samples are cut from the same cloth, as both make use of asynchronous I/O operations for file encryption queuing to using virtually identical command-line parameters for the same functionality (i.e., logging, drives and network shares encryption, network scanning).
It’s interesting to note that the researchers couldn’t find a direct link between Diavol ransomware and the Trickbot gang as some significant differences are making the high confidence attribution impossible.
To begin with, there are no built-in checks in Diavol ransomware that are meant to prevent the payloads from running on Russian targets’ systems as Conti does.
Another interesting difference is the fact that no evidence of data exfiltration capabilities before encryption was found.
What Can Diavol Ransomware Do?
Diavol ransomware’s encryption uses the user-mode Asynchronous Procedure Calls (APCs) with an asymmetric encryption algorithm, this being the factor that sets it apart from other ransomware families.
Diavol ransomware lacks obfuscation because it doesn’t use packing or anti-disassembly tricks, but still manages to make analysis harder by storing its main routines within bitmap images.
The Diavol ransomware extracts the code from the images’ PE resource section and loads it within a buffer with execution permissions as the extracted code amounts to 14 different routines that will execute in the following order:
- Create an identifier for the victim
- Initialize configuration
- Register with the C&C server and update the configuration
- Stop services and processes
- Initialize encryption key
- Find all drives to encrypt
- Find files to encrypt
- Prevent recovery by deleting shadow copies
- Encryption
- Change the desktop wallpaper
Right before Diavol ransomware is finished, will change the encrypted Windows device’s background to a black wallpaper with the following message:
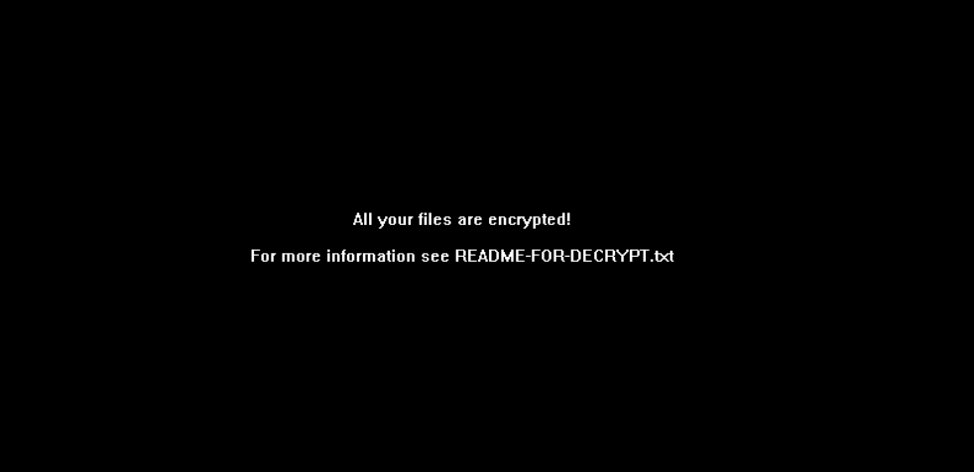
At the time the source of intrusion for Diavol Ransomware remains unknown:
Currently, the source of the intrusion is unknown. The parameters used by the attackers, along with the errors in the hardcoded configuration, hint to the fact that Diavol is a new tool in the arsenal of its operators which they are not yet fully accustomed to.
There might be a link between Diavol and Egregor ransomware as some lines in the ransom note are identical, but this is not enough to be certain in regards to this connection, as this could be just a red herring that Diavol’s authors planted.
Even if there’s a high possibility for a link between Wizard Spider and Diavol Ransomware to exist at this moment it remains unknown if Diavol is connected to the threat actor behind Conti, and Twisted Spider.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










