Contents:
A recent study by Cybersecurity Dive shows that nearly all companies (98%) use software integrations with third-party vendors that have suffered breaches in the past two years.
Since not a single company can maintain ops integrity by solely relying on in-house developed software, the stakes are higher than ever.
In this article, we’re going to talk about how to assess vendor vulnerabilities using standardized formats, calculate third-party risk using 3×3 matrixes, and how to develop stronger strategies for identifying and mitigating vendor vulnerabilities.
Key Takeaways
- Learn how to assess vendor vulnerabilities by leveraging the SAP’s SIG Questionnaire and NIST’s RMF (Risk Management Framework). Pros and cons of choosing the SIG Questionnaire. Pros and cons of choosing NIST’s RMF. How to complete the SIG Questionnaire and NIST’s RMF.
- Learn how to conducting assessments for common and uncommon third-party vulnerabilities.
- Learn how to assess and calculate risk associated with third-party vendors by leveraging a risk matrix.
- Learn how to apply risk score modelling to real-life scenarios.
- Learn the baseline strategies for Identifying and Mitigating Vendor Vulnerabilities.
- The best tools to help you assess and address vendor vulnerabilities.
- Heimdal®.
- BitSight.
- RSA Archer.
- RiskRecon.
- SecurityScorecard.
- Resolver.
- Prevalent.
- Tenable.
- Vendor Vulnerabilities Frequently Asked Questions (FAQs).
How to assess vendor vulnerabilities.
Tracking and managing vendor-specific vulnerabilities is a challenging and often overlooked aspect of vulnerability management.
According to a study by White Hat Security, throughout its lifecycle, a common application has an average of six critical vulnerabilities.
This number doesn’t mean much unless you use a wide(r) angle lens.
In a recently published e-paper, Abnormal Security revealed that organizations use, on average, approximately 300 third-party apps to cover the entire tech stack.
This includes ERP, Business Intelligence, Communications, Productivity, Finance, Revenue, and more.
Let’s take this exercise even further.
With an average of 6 critical vulnerabilities/app lifecycle and 300 applications deployed across key areas, your ITSec teams would need to deal with 1,800 critical vulnerabilities.
This becomes even more dramatic if we factor in the integration ratio.
A market study by Chief Marketing Technologist reveals that a SaaS app has an average of 15 integrations.
Let’s run those numbers again:
- 6 critical vulnerabilities per application lifecycle.
- Companies run, on average, 300 third-party apps.
- ITSec teams need to deal with 1,800 critical vulnerabilities.
- A SaaS app runs, on average, at least 15 integrations.
This boils down to one thing –your team needs a way to identify, assess, and address third-party vulnerabilities, based on severity and impact on your company’s digital assets.
The easiest way to overcome this challenge is to use standardized frameworks. In this article, I’m going to cover the Shared Assessments Program and NIST.
Leveraging the Shared Assessments Program (SIG) for Third-Party Vulnerabilities
Shared Assessments’ SIG (Standardized Information Gathering) Questionnaire is the go-to solution for conducting vendor risk assessments and identifying third-party vulnerabilities.
SIG is the best approach for companies that want to conduct thorough risk assessments, but have neither the experience nor the capacity or manpower to stage this operation.
Reasons to choose the SIG Questionnaire
- Customization. Shared Assessments Program is a Solution-as-a-Service vendor. The questionnaire can be tailor-made, accommodating your company’s requirements, scope, and infrastructure.
- Availability. Quick and easy assessment. Once you purchased the license, you can start the first third-party risk audit. All relevant documents will be sent over email.
- Alignment. The SIG Questionnaire is completely aligned with major industry and international regulatory guidance standards. This includes HIPPA, ISO, NIST, GDPR, and PCI.
- Extensive risk domain coverage. Shared Assessments’ questionnaire covers 21 risk domains, including Access Control, Application Security, Compliance Management, Human Resource Security, Supply Chain Risk Management, Threat Management, Network Security, and more.
- Extra resources. After purchasing a SIG assessment plan, you will be able to tap into additional resources. The company makes available a SIG manager to ease the pre- and post-assessment processes, a user procedure guide, an implementation workbook, a documentation artifacts request list, and on-demand training.
Reasons to skip the SIG Questionnaire
- Pricing. Shared Assessment’s third-party vulnerability assessment plans may not be a good match for a company with limited resources. To put things into perspective, a single one-year corporate license costs $6,500. For more info on Shared Assessments’ pricing tiers, check out their homepage.
How to complete your SIG Questionnaire
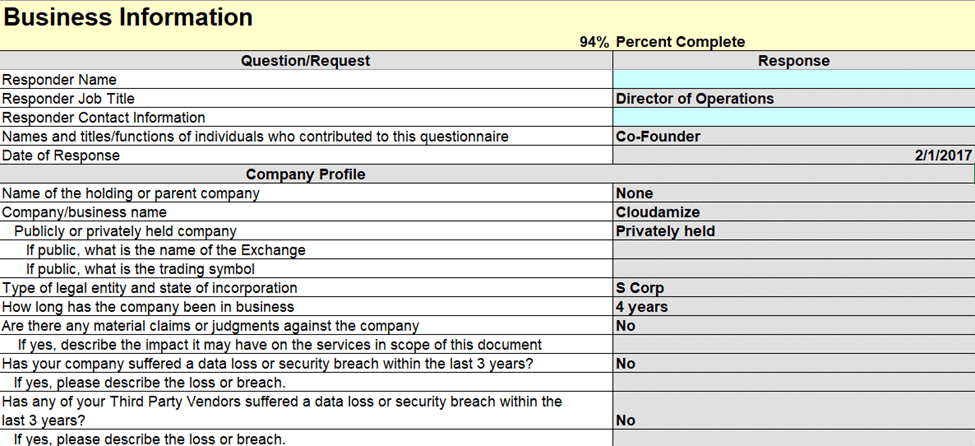
1. Fill out all light blue fields in the Business Information tab with detailed information, especially for Scope questions.
Business Information
Scope Information
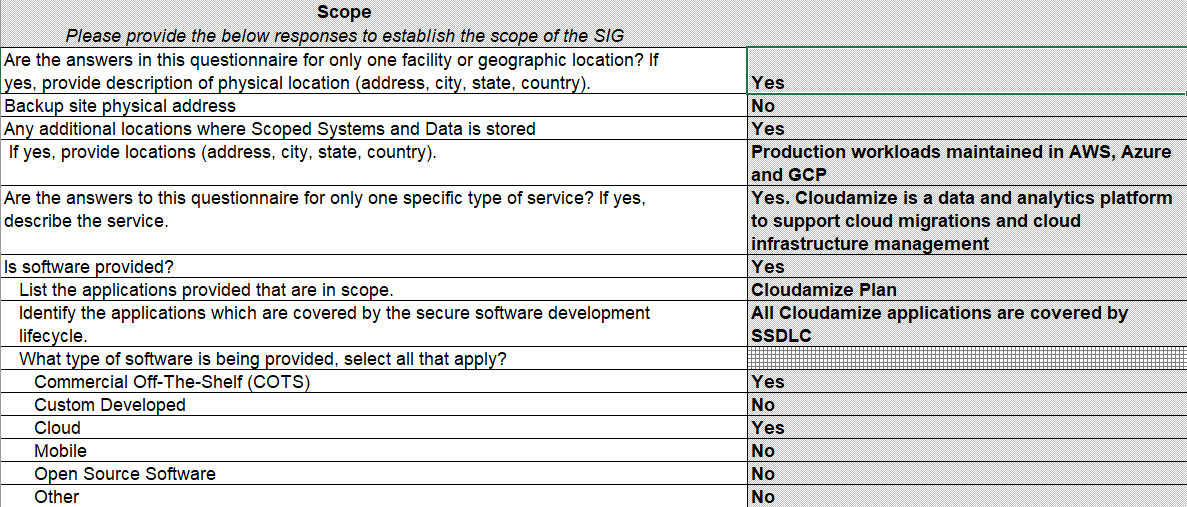
2.Review and gather corporate policies/processes listed in the Documentation tab, allowing for distribution outside the organization.

3. Enter document names in the corresponding field in the Documentation tab.
4. Switch to the Lite tab.
5. Answer each question, using color changes (green for Yes, purple for No, or N/A) and Excel macros to assist.
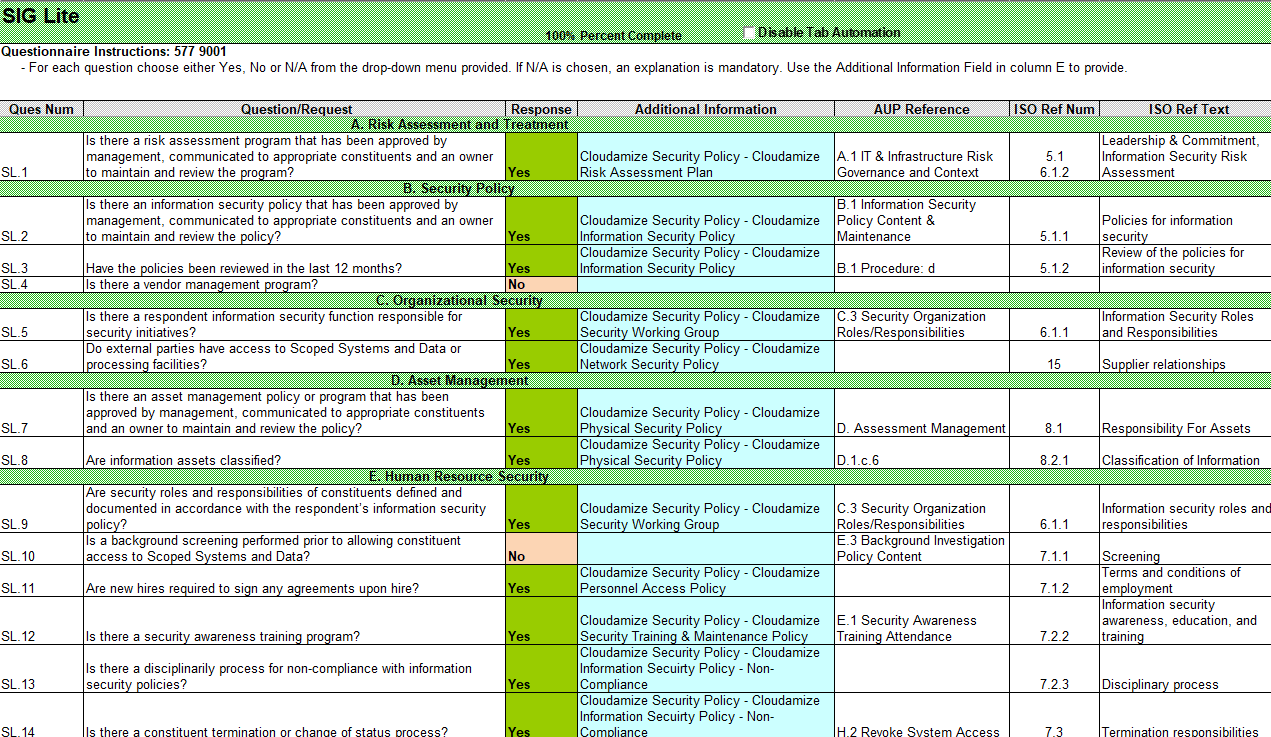
6. Move to the next tab and repeat until all tabs are completed.
7. Submit the completed SIG and policy/process documents to the issuer.
8. Collaborate with the issuer to address any identified issues.
Click here to download SIG Questionnaire Model.
Leveraging NIST for Third-Party Vulnerabilities
NIST’s RMF (Risk Management Framework) is a 7-step vulnerability and risk assessment program that aids companies in evaluating information security and privacy liabilities.
Companies can thoroughly review third-party assets and create stronger strategies by following NIST’s PCSIAAM guide.
Reasons to choose the NIST Third-Party Vulnerability Assessment Framework
- Guidance. NIST RMF offers comprehensive guidance and resources for effective risk management.
- Recognition. Widely recognized and adopted, promoting consistency in risk practices.
- Flexibility. Allows customization to fit organizational needs and adapt to changes.
Reasons to Skip NIST Third-Party Vulnerability Assessment Framework
- Complexity. Implementation can be complex and resource-intensive.
- Documentation. Emphasizes extensive documentation, adding administrative overhead.
- Resource Requirements. Requires dedicated personnel and investments, which may be challenging for some organizations.
How to complete your NIST Third-Party Vulnerability Assessment Framework

- Prepare. Lay the groundwork to manage security and privacy risks.
The full preparation guide is available on NIST.
2.Categorize. Classification of systems and information according to an impact analysis, detailing processing, storage, and transmission.
The full categorize guide is available on NIST.
3. Select. Choosing appropriate NIST SP 800-53 controls based on risk assessments to safeguard the system.
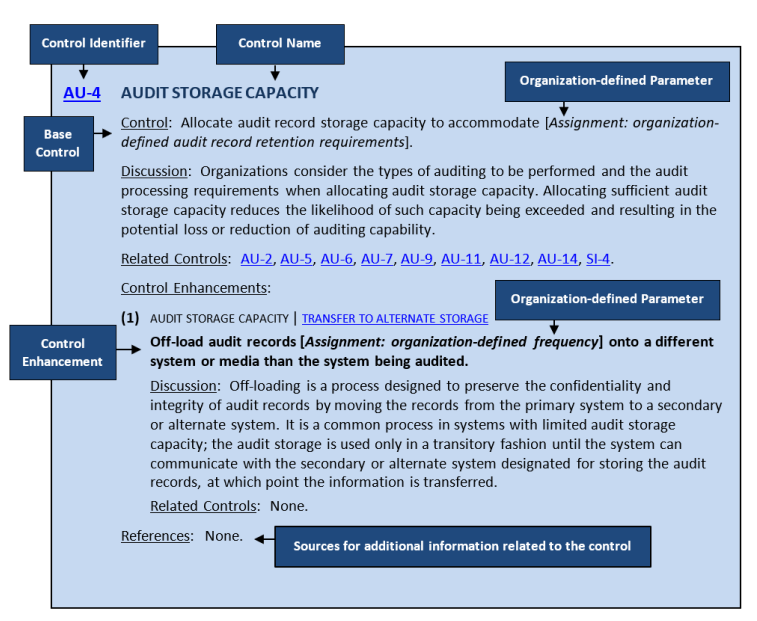
Full controls select guide available on NIST.
4. Implement. Deployment of selected controls, thoroughly documented to ensure proper implementation.
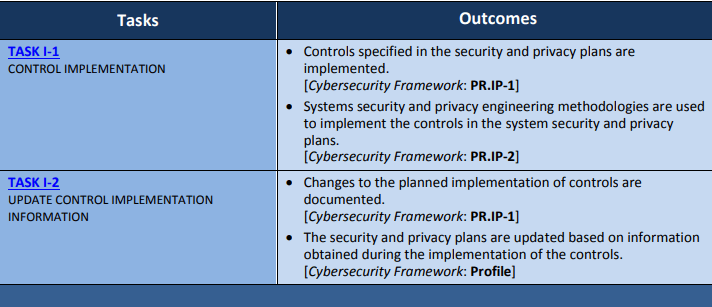
Full implementation guide available on NIST.
5. Assess. Regular assessment to verify control effectiveness, operational status, and attainment of desired outcomes.
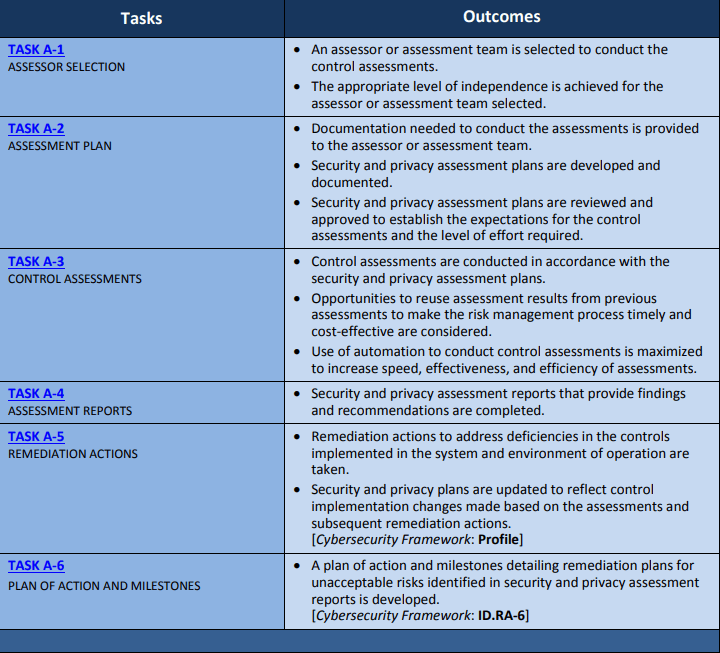
Full assessment guide available on NIST.
6. Authorize. Risk-informed decision-making by senior staff to authorize ops.
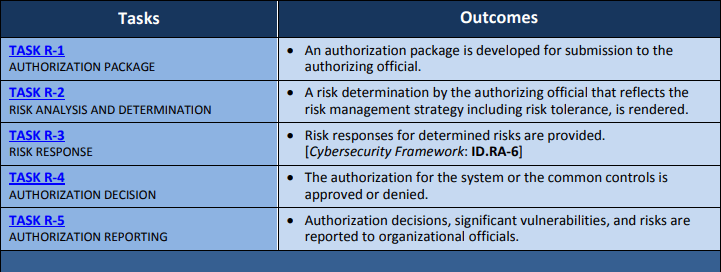
Full authorization guide available on NIST.
7. Monitor. Ongoing monitoring of control implementation and system risks to maintain security posture.
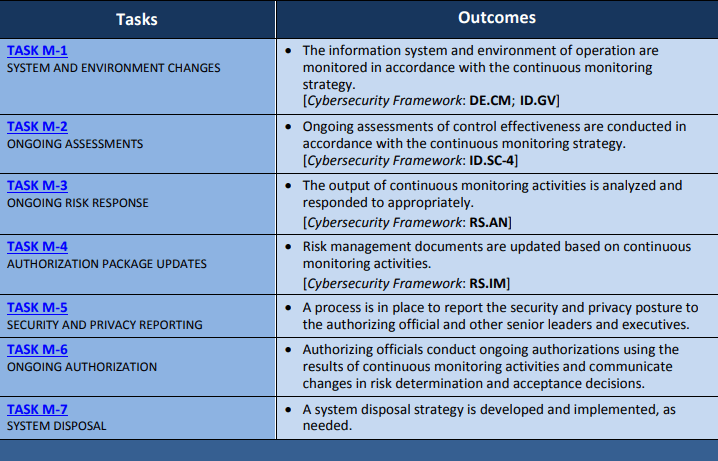
Full monitorization guide available on NIST.
Third-Party Vulnerabilities Risk Assessment
Before we tackle how to calculate risk for third-party vulnerabilities, we should consider the following aspects.
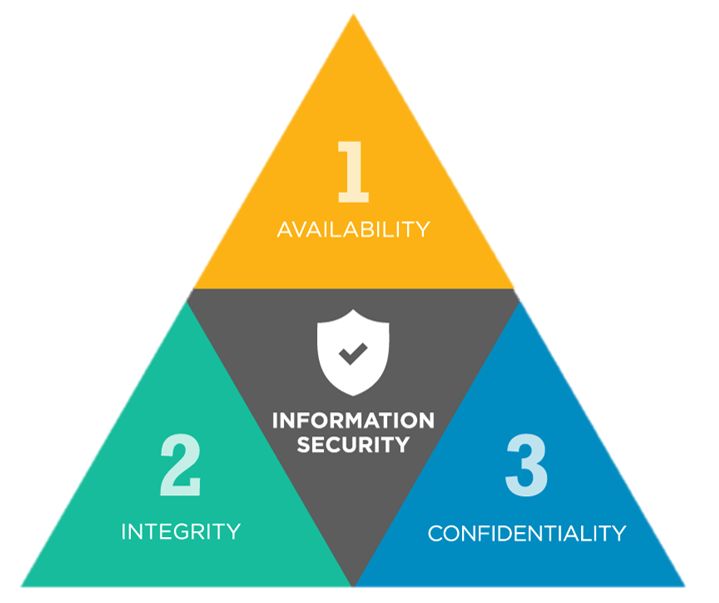
1. Increased velocity precludes maturity. An IT team rubberstamping integration will sacrifice confidentiality for integrity and availability. (see CIA triangle).
2. Wider MTTR-MTTD Gap. ITSec teams will find it more challenging to bridge the MTTD-MTTR gap when fast-deploying integrations or adding more applications to the digital infrastructure.
3. Vulnerability management equals auditing. Security teams need proper auditing rules such as templates, frameworks, rulebooks, and battle cards that are written specifically for third-party applications.
Conducting assessments for (un)common third-party vulnerabilities
A thorough assessment of third-party vulnerabilities considers the attack surface itself.
For instance, if you’re using software licensed by a vendor that doesn’t employ E2E encryption (End-to-End) encryption, it’s recommended to conduct an API-based assessment to determine if your company may be at risk by using a vulnerable API.
So, depending on the attack surface, here are the types of assessments you can conduct for third-party applications.
Assessing Network-centric vulnerabilities
This assessment phase focuses on network-based vulnerabilities and how they can be leveraged by threat actors. Examples include the following:
- Unsecured mobile devices.
- USB flash drives.
- Misconfiguration in firewall policies.
- SFA (Single-Factor Authentication).
- Weak passwords,
- Unsecured email services.
- Unsecured Wi-Fi connections,
- Outdated/legacy software.
Assessing Application-centric vulnerabilities
This process is focused on application-specific vulnerabilities. Examples may include the following.
- Security misconfigurations (could leave the company exposed to debilitating attacks, including supply chain attacks)
- Cryptographic failures.
- Authentication failures.
- Cross-site request forgery.
- Broken access control.
- Unvalidated redirects & forwards.
- Command injection.
- Insecure direct object references.
Assessing API-centric vulnerabilities
During this phase, the company focuses on identifying vulnerabilities in API communications. This includes:
- Broken Object Level authorization.
- Broken User Authentication.
- Broken Object Property Level Authorization.
- Server-side Request Forgery.
- Improper Inventory Management.
- Unsafe API composition.
Assessing endpoint-centric vulnerabilities
Focuses on rooting our vulnerabilities that are specific to hosts. Examples may include the following.
- SSL/TSL Certificate signed by a weak signature algorithm.
- Weak cipher suite.
- HSTS Missing.
- DistCC Remote Code Execution vulnerability.
- Anonymous FPT Login.
- Running outdated software and firmware.
- Running improperly secured applications.
Using the risk matrix to compute the global risk score
Based on the results of your vulnerability assessments, you can compute what is called a global risk scorecard using a matrix.
The risk matrix is a powerful vulnerability mitigation tool.
Companies can leverage these measurements to implement more robust cybersecurity measures, develop incident response plans, and, contain the impact the data breaches more efficiently.
Any risk matrix indicates two things: the likelihood of a cybersecurity incident and the impact and or severity. A standard risk matrix looks like this.
| Likelihood/Impact (Severity) | Low | Medium | High |
| Low | 1 | 2 | 3 |
| Medium | 4 | 5 | 6 |
| High | 7 | 8 | 9 |
Or like this.
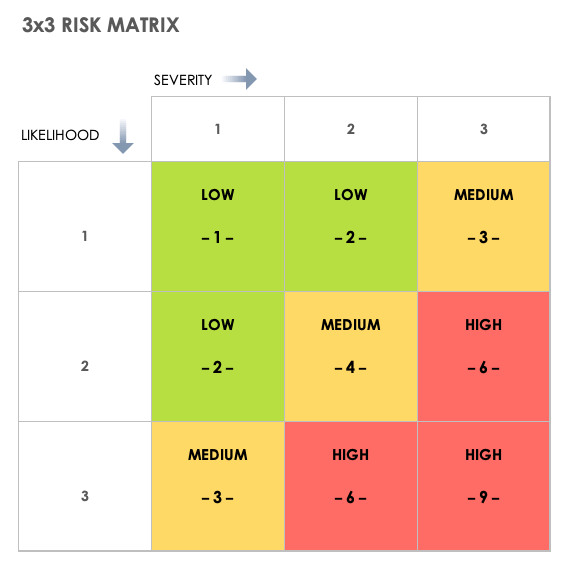
Deciphering the Risk Management Matrix
A bit more on the scoring system and how to read it efficiently.
Cell 1 Low Likelihood, Low Impact (Value: 1)
This means that the likelihood of such a scenario is low, and even if it occurs, the impact is minimal.
Cell 2: Low Likelihood, Medium Impact (Value: 2)
While the likelihood of an attack is low, a medium-impact scenario suggests that there may be some vulnerabilities or gaps in security measures.
Cell 3: Low Likelihood, High Impact (Value: 3)
Low likelihood, but high impact means that the potential consequences of an attack could be severe.
Cell 4: Medium Likelihood, Low Impact (Value: 4)
A medium likelihood – low impact scenario suggests that while the risk of an attack is moderate, the potential consequences are manageable.
Cell 5: Medium Likelihood, Medium Impact (Value: 5)
A moderate risk scenario where the likelihood of an attack is moderate, and the impact could result in moderate financial losses and operational disruptions.
Cell 6: Medium Likelihood, High Impact (Value: 6)
A medium likelihood combined with high impact indicates a significant risk where an attack could result in substantial financial losses, data breaches, and business interruptions.
Cell 7: High Likelihood, Low Impact (Value: 7)
A high likelihood, low impact scenario means that an attack may be imminent but with relatively low impact due to effective security measures and response strategies in place.
Cell 8: High Likelihood, Medium Impact (Value: 8)
A high likelihood combined with medium impact represents a significant risk where an attack could lead to significant financial losses and operational disruptions.
Cell 9: High Likelihood, High Impact (Value: 9)
This represents the highest-risk scenario where an attack is highly likely, perhaps imminent, and the potential impact could be severe, including extensive financial losses, data loss, and reputational damage.
Real-Life Risk Score Modelling
So, how does this apply to real-life events? Let’s consider three scenarios – a ransomware attack, a phishing attack, and a data breach.
Q: What is the risk score associated with a ransomware attack?
A: Using the matrix above, the computed risk score is 6.
This means medium likelihood and high impact. With ransomware attacks on the rise it’s only natural to assume that this event has a medium likelihood.
As for impacts, most (successful) ransomware attacks lead to financial losses, service disruptions, data breaches, and more.
Q: What is the risk score associated with a phishing attack?
A: The computed score is 8. This means high likelihood but medium impact.
Phishing remains the go-to attack resurface, in spite of its relatively low success rate.
Our computed score means that such an attack is bound to happen at any moment, but the impact on business ops and integrity is medium.
Q: What is the risk score associated with a data breach?
The computed score is 6.
Just like in the case of a ransomware attack, this is a medium-likelihood and high-impact scenario.
What this means is that such an incident is moderately likely and could result in substantial financial losses, regulatory fines, reputational damage, and legal consequences.
Strategies for Identifying & Mitigating Vendor Vulnerabilities.
Following your vulnerabilities & risk assessments for the third-party apps deployed across your environment, you can start enforcing rules and strategies.
These are meant to strengthen your cybersecurity posture.
Continuous Monitoring
Implement continuous monitoring processes to detect and assess vendor vulnerabilities in real time, using tools such as vulnerability scanners, threat intelligence feeds, and security rating platforms.
Vendor Risk Assessments
Conduct thorough vendor risk assessments, including security questionnaires, on-site audits, and contractual obligations, to evaluate vendors’ security posture and identify potential vulnerabilities.
Contractual Security Requirement
Employ specific security requirements and controls into vendor contracts, outlining expectations for vulnerability management practices, incident response procedures, and compliance with industry standards.
Vulnerability Remediation Plans
Establish clear procedures for addressing identified vulnerabilities with vendors, including timelines for patching or mitigating vulnerabilities, escalation paths for critical issues, and verification of remediation efforts.
Ongoing Communication and Collaboration
Foster open communication and collaboration with vendors to exchange security information, share threat intelligence, and coordinate vulnerability management efforts effectively.
Continuous Improvement
Regularly review and update vendor risk management processes, incorporating lessons learned from past incidents, emerging threats, and changes in regulatory requirements to enhance the effectiveness of vulnerability identification and mitigation strategies.
8 Best Third-Party Risk Management Tools
Here are the best tools to help you jumpstart your third-party vulnerability management journey.
1) Heimdal®
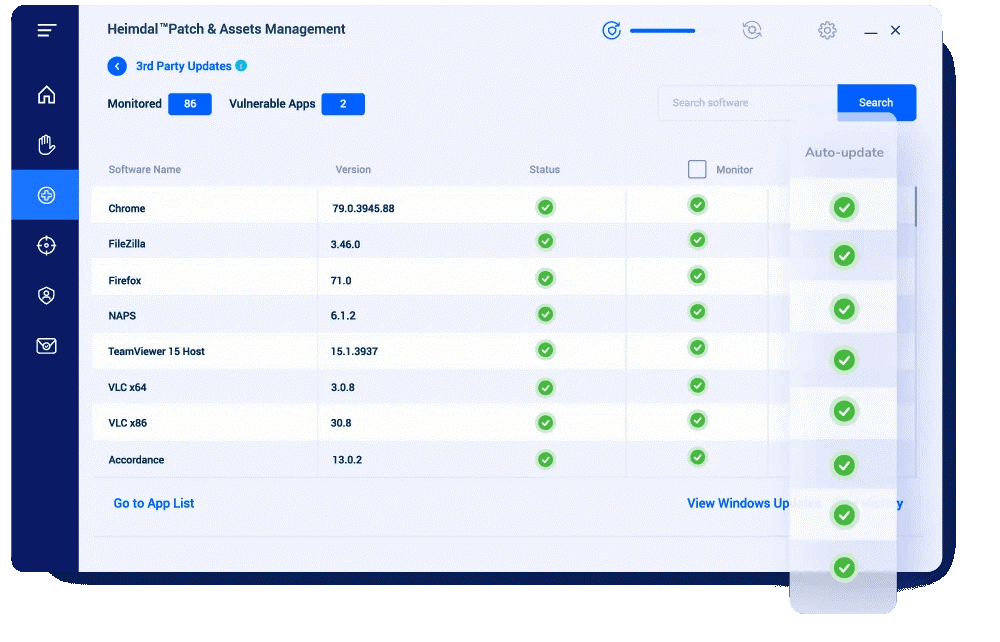
Heimdal® Patch & Asset Management streamlines the patching and vulnerability process, helping businesses save resources and shift from a reactive to a proactive security approach.
Pros
- Seamless Deployment & Integration. Heimdal’s deployment ease, combined with its ability to update a wide range of software, ensures consistent coverage for all teams.
- Top-Notch Customer Support. Heimdal’s service is widely acclaimed, emphasizing not just product quality but also strong customer relationships.
- User-Friendly Design. Heimdal’s intuitive dashboard and hassle-free deployment make it a top choice for ease of use.
- XDR Capabilities. The full Heimdal suite offers 10+ integrated solutions with Extended Detection and Response capabilities that include patch and asset management but also privilege access management, DNS security, next-gen antivirus, ransomware encryption protection, threat hunting, and a 24×7 SOC service.
Cons
- The admin portal can be a little difficult to navigate in the beginning.
2. BitSight
BitSight offers continuous monitoring and actionable insights for third-party risk management.
Pros
- BitSight offers thorough risk assessment and continuous monitoring.
- Specializing in third-party risk management, it provides actionable insights.
Cons
- Integration with other tools may be limited.
- Costs can be high.
- There’s a risk of false positives.
- Dependency on external data sources may pose limitations.
3. RSA Archer
RSA Archer provides a comprehensive platform for assessing, managing, and reporting on third-party risks.
Pros
- RSA Archer provides a centralized platform for risk management and compliance.
- It offers customizable workflows and reporting capabilities.
Cons
- Implementation can be complex and time-consuming.
- Customization may require specialized skills.
- It may be costly to maintain and scale.
- Some users report issues with the user interface and performance.
4. RiskRecon

RiskRecon delivers scalable risk assessment solutions with deep visibility into third-party ecosystems.
Pros
- Efficient in identifying any malware signature.
- Real-time monitoring.
- Access controls and permissions.
Cons
- Limited support for niche industries.
- Potential false positives in scoring.
- Pricing.
5. SecurityScorecard
SecurityScorecard offers continuous security ratings and vendor risk assessments for proactive risk management.
Pros
- Reporting Center.
- Precise security rating.
- Ease of use.
Cons
- Occasional inaccuracies in ratings.
- Limited customization options.
- Challenges in integrating with existing workflow.
6. Resolver
Resolver provides a flexible platform with customizable risk assessment templates and real-time monitoring capabilities.
Pros
- Real-time monitoring.
- Flexibility
- Customization
Cons
- Complexity in configuring advanced features.
- High implementation costs.
- Requires ongoing training.
7. Prevalent
Prevalent offers a comprehensive suite of third-party risk management solutions, including vendor risk assessments and compliance management.
Pros
- Variety in security questionnaires.
- Real-time risk calculation.
- Risk identification automation.
Cons
- Challenging integration.
- Non-intuitive UI.
- Pricing.
8. Tenable
Tenable offers vulnerability management solutions with robust asset discovery and continuous scanning for third-party risk assessment.
Pros
- PCI scanning.
- Reporting.
- Configuration file evaluation.
Cons
- False positives in vulnerability scanning.
- Requires additional integrations for comprehensive risk assessment.
Frequently Asked Questions (FAQ)
Q: What techniques are employed in third-party vulnerability discovery?
A: Third-party vulnerability discovery relies on techniques like dynamic and static analysis, fuzzing, reverse engineering, and protocol analysis.
These methods delve into codebases, binaries, network traffic, and system interactions to uncover potential security weaknesses.
Q: How are third-party vulnerabilities categorized and prioritized?
A: Vulnerabilities are classified based on severity, impact, exploitability, and affected assets.
Common classification systems include CVSS (Common Vulnerability Scoring System) and CWE (Common Weakness Enumeration).
Prioritization factors also consider factors like business criticality and regulatory requirements.
Q: What strategies can organizations adopt for patch management in third-party systems?
A: Patch management strategies involve evaluating patches for stability and compatibility, testing them in isolated environments, and deploying them through controlled rollout processes.
Automated patch deployment tools and vulnerability scanners aid in efficient patch management.
Q: How do organizations handle vulnerabilities in third-party dependencies within their software supply chain?
A: Organizations must maintain visibility into their software supply chain, tracking dependencies and monitoring vulnerability databases.
Remediation may involve upgrading dependencies, implementing workarounds, or isolating vulnerable components through containerization or virtualization.
Q: Can organizations effectively manage vulnerabilities in closed-source third-party software?
A: While challenging, managing vulnerabilities in closed-source software involves proactive communication with vendors, leveraging third-party security assessments, implementing compensating controls, and monitoring for emerging security advisories and patches.
Q: How do organizations mitigate risks associated with delayed or unavailable vendor patches?
A: Mitigation strategies include deploying virtual patches through intrusion prevention systems or web application firewalls, implementing network segmentation to isolate vulnerable systems, and employing runtime application self-protection (RASP) mechanisms.
Q: What role does threat intelligence play in third-party vulnerability management?
A: Threat intelligence provides context on emerging threats, including exploit techniques targeting third-party software.
Organizations leverage threat intelligence feeds and platforms to prioritize vulnerabilities, anticipate attack trends, and bolster defensive measures.
Q: How do organizations validate the effectiveness of third-party vulnerability remediation efforts?
A: Validation involves conducting post-remediation testing, including regression testing, to ensure that vulnerabilities are effectively addressed without introducing new issues.
Continuous monitoring and incident response exercises also validate the resilience of remediated systems.
Q: What measures can organizations take to ensure compliance with third-party vulnerability disclosure policies?
A: Organizations must adhere to vendor disclosure policies, which may include responsible disclosure timelines and communication protocols.
Establishing internal policies and procedures for vulnerability disclosure handling facilitates compliance and fosters positive vendor relationships.
Q: How can organizations enhance third-party vulnerability management through automation and orchestration?
A: Automation and orchestration streamline vulnerability scanning, patch deployment, and incident response processes.
Integrating vulnerability management tools with IT asset management systems and SIEM (Security Information and Event Management) platforms enables automated risk assessment and response workflows.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security