Contents:
If you didn’t know by now, Extended Detection and Response (XDR) is no longer a luxury. It’s a fast becoming a cybersecurity essential.
Gartner predicts that by 2027, over 40% of organizations will have adopted an XDR solution, up from less than 5% in 2021.
But with so many options on the market, choosing the right solution can be overwhelming.
In this in-depth comparison, we’ll explore three top XDR platforms:
- SentinelOne Singularity XDR
- Sophos Intercept X with XDR
- Heimdal® XDR – a powerful and cost-effective alternative
Let’s break down their features, pricing, user reviews, and more to help you find the best XDR solution for your business in 2025.
What Is SentinelOne Singularity XDR?
SentinelOne Singularity XDR is an XDR solution which boasts a wide array of features to fight against cyber threats. It caters to businesses of all sizes, offering robust and proactive defense measures.
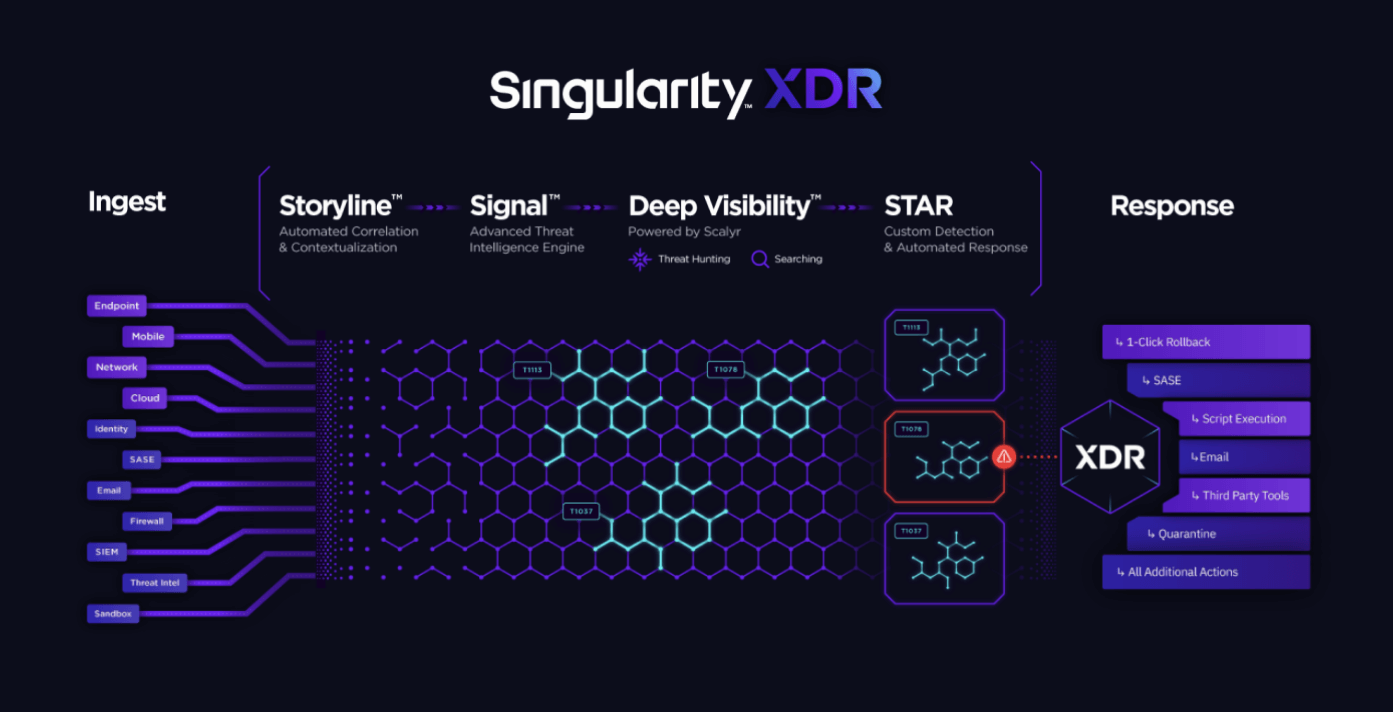
Key features:
-
AI-Driven Detection: Identifies threats using machine learning and behavior-based analysis.
-
Autonomous Remediation: Automatically isolates and mitigates compromised endpoints.
-
Cloud-Based Management Console: Unified visibility and control across all endpoints.
-
Zero-Trust Network Access (ZTNA): Enforces least-privilege access control.
-
Multi-OS Compatibility: Works across Windows, macOS, Linux, and cloud environments.
Ideal for enterprises seeking full automation and scalable protection across diverse environments.
What Is Sophos Intercept X?
Sophos Intercept X combines advanced endpoint protection with powerful XDR capabilities.
Known for its deep learning AI, it excels at preventing ransomware and advanced threats like fileless attacks.
Key features:
-
Deep Learning AI Engine: Detects and blocks both known and unknown threats.
-
Exploit Prevention: Protects against zero-day vulnerabilities.
-
Root Cause Analysis: Helps identify how threats entered your network.
-
Ransomware File Protection: Detects and halts unauthorized file encryption.
-
Sophos Central Console: Unified management for endpoints, firewalls, and servers.
Ideal for businesses already using Sophos products or those wanting strong anti-ransomware defenses.

Some features that set it apart include its deep learning AI capabilities, anti-exploit technology, and root cause analysis, enhancing threat detection and response capabilities.
User feedback highlights Intercept X’s effectiveness in thwarting complex threats, often surpassing similar products.
Feature-by-Feature Comparison: SentinelOne vs. Sophos
- AI-Powered Threat Detection: Leveraging advanced AI and ML algorithms, SentinelOne proactively identifies and responds to threats in real-time, ensuring swift mitigation of sophisticated cyberattacks.
- Behavioral Analysis: Through behavioral analysis, the platform monitors and scrutinizes the activities of applications and processes on endpoints, identifying abnormal behavior and thwarting potential zero-day attacks.
- Autonomous Threat Remediation: An exceptional feature is the platform’s capability to autonomously respond to threats. Upon detection, SentinelOne isolates and mitigates affected endpoints automatically, halting the spread of malware.
- Endpoint Detection and Response (EDR): Providing detailed visibility into endpoint activities, EDR empowers security teams to investigate incidents, track malicious behavior, and respond effectively, thereby reducing the time to remediation.
- Threat Intelligence Integration: Integration of threat intelligence feeds enhances the platform’s ability to identify and block known threats, safeguarding organizations against a wide array of known malware and attack vectors.
- Multi-Platform Support: Compatible with various operating systems including Windows, MacOS, and Linux, SentinelOne ensures comprehensive endpoint protection across diverse environments.
- Cloud-Based Management: The centralized cloud-based management console enables security teams to monitor and manage all endpoints from a single dashboard, streamlining administration and enhancing overall efficiency.
- Zero-Trust Network Access (ZTNA): With ZTNA capabilities, the platform ensures that only authorized devices and users can access critical resources, thereby reducing the attack surface and bolstering security.
- Real-Time Threat Hunting: Security analysts can proactively hunt for threats using the platform’s real-time capabilities, uncovering hidden threats before they can cause harm.
Sophos Intercept X Core Features
Sophos Intercept X offers a suite of core features designed to provide robust protection against advanced cyber threats:
- Advanced Threat Detection: Intercept X detects and prevents advanced threats, including zero-day malware and ransomware, ensuring comprehensive protection against evolving cyber threats.
- Real-time Threat Intelligence: By leveraging real-time threat intelligence from SophosLabs, Intercept X remains updated with the latest threat trends, enabling swift responses to emerging threats and offering comprehensive security coverage.
- Behavioral Analysis: Intercept X employs behavioral analysis to identify suspicious activities and anomalies on endpoints, enhancing security against novel threats, even if they haven’t been seen before.
- Ransomware Protection: Intercept X monitors file system activity, detects encryption attempts, and proactively stops ransomware attacks, safeguarding critical data from unauthorized encryption.
- Endpoint Detection and Response (EDR): With powerful EDR capabilities, Intercept X allows security teams to investigate incidents, track threat actors’ movements, and respond effectively to security breaches, enhancing overall incident response and threat hunting capabilities.
- Phishing and Exploit Prevention: Intercept X includes robust mechanisms for preventing phishing attacks and exploit attempts, identifying and blocking phishing websites, malicious email attachments, and malicious code execution attempts, reducing the risk of successful compromises.
- Centralized Management: Sophos Central provides a unified management console for Intercept X, simplifying deployment, configuration, and security monitoring across all endpoints, ensuring consistent security policies.
- User-friendly Interface: Intercept X features an intuitive and user-friendly interface that enables IT teams to efficiently manage security, reducing the learning curve and facilitating effective use of the solution’s capabilities.
- Optimized Performance: Intercept X minimizes system resource consumption, operating efficiently in the background to ensure that endpoint performance remains smooth and unaffected.
- Automatic Updates and Patching: Intercept X keeps endpoints protected with automatic updates and patching, ensuring that security measures are always up to date, reducing vulnerabilities associated with outdated software.
SentinelOne vs. Sophos: Pricing Comparison
Pricing Structure of SentinelOne Singularity XDR
Singularity offers two packages: Commercial provides foundational protection powered by AI for identities, endpoints, and the cloud, while Enterprise offers comprehensive protection, coupled with deployment services and threat intelligence, for a cost-effective solution.
Pricing Structure of Sophos Intercept X
Sophos Intercept X offers flexible pricing options tailored to your needs. It delivers cloud-managed endpoint security with rapid deployment, transparent per-user pricing, and no undisclosed fees.
With choices like Advanced, Advanced with XDR, and Advanced with MDR Complete, it guarantees thorough protection against breaches, ransomware, and emerging threats.
SentinelOne vs. Sophos: What Do Users Think?
SentinelOne Singularity XDR User Reviews
Users appreciate SentinelOne Singularity XDR’s end-point protection, especially its ransomware file rollback feature and lightweight yet powerful scanning capabilities.
We especially like this end-point protection that comes with the feature that we can roll back files even in case of a ransomware attack. This can be a lifesaver to get back files during a ransomware attack in case not covered by backup software. In addition, S1 has been a lightweight software with powerful protection against anything it scanned. The cloud portal also has a lot of info for reports, thread hunting, etc.
G2 User Review of SentinelOne Singularity XDR
However, the soft’s handling of faux malware attacks and other errors seems to be a concern for users. One talked about his company’s experience with the SentinelOne software:
When we first implemented SentinelOne, there was a faux malware attack spreading throughout our network. Thanks to their great support, we resolved it to being an old AV software fighting sentinel one. However in that time we got Thousands of email notifications and even more popups for the end user system. The software did not give any useful information other than the raw name it found. The dashboard, while good looking, is riddled with menus and sub menus, all using proprietary terminology that makes it difficult to understand right away. The installation process is quick, once you navigate 7-8 layers of menus to get the correct information to do so. I would like to see a more “straightforward” menu system that has less sub-menu and vague terminology.
G2 User Review of SentinelOne Singularity XDR
Sophos Intercept X User Reviews
The software’s EDR capabilities, proactive threat hunting, and Root Cause Analysis feature seem to be praised by its users. They appreciate its robust protection and centralized management ease. As one Intercept X user shares:
I likes its features of EDR in that it offers EDR capabilities allowing our organization to proactively hunt for threats, investigate security incidents and respond to breaches more effectively. Secondly I likes its Root Cause Analysis which helps us understand the root cause of attacks and improve our security posture. Overall, I appreciate its robust protection against a wide range of threats, Its proactive approach to threat detection and response, and its ease of management through centralized administration.
G2 User Review of Sophos Intercept X
Concerns include sluggish endpoints, lack of response for third-party integrations, and brief reports. As one user says:
It would be ideal to have response actions for all third-party integrations available with the product, rather than just a few. -More refined and detailed reporting on the XDR/EDR interface is necessary for detection. -There should be an option to run queries to detect vulnerabilities depending on CVE ID.
G2 User Review of Sophos Intercept X
What Does Reddit Think?
On Reddit’s r/sysadmin and r/cybersecurity forums, IT professionals weigh in:
SentinelOne is an easy choice between the two. Sophos is very limited in their XDR capabilities, and it’s a pain to do analysis especially when you’re trying to find IOC’s on other endpoints.
Reddit Review of SentinelOne and Sophos
Another user said in a Reddit thread comparing the two solutions:
SentinelOne! We moved from Sophos and it’s been so much easier to maintain. Don’t bother with Sophos unless you want all headaches and beta-like performance. I would have gone with defender ATP if we didn’t have such a diverse environment.
Reddit Review of SentinelOne and Sophos
SentinelOne vs. Sophos: How to Choose the Best Solution
Selecting the appropriate cybersecurity solution is essential for safeguarding your data and privacy. Here are some key factors to take into account:
- Security Features: Look for a solution that offers robust security features such as antivirus protection, firewall, intrusion detection, and encryption. Make sure it covers all aspects of cybersecurity that your organization needs.
Businesses should ensure the cybersecurity solutions they purchase reduce their risk, not increase it. This sounds like a no-brainer, but recent vulnerabilities—such as Citrix Bleed and coordinated attacks on firewalls at dozens of energy suppliers—show that there’s real risk. Look for solutions that have secure development practices and zero-trust policies in place so they can’t be leveraged as an attack vector.
- Ease of Use: Opt for a solution that is user-friendly and easy to manage. It should feature a simple interface and intuitive controls for easy security management.
The majority of cybersecurity incidents happen because of human error. Even the most advanced platform will be rendered useless if it’s not used effectively by your people. So businesses should prioritize ease of use and intuitiveness when selecting a cybersecurity platform, ensuring seamless integration with existing infrastructure as well as a quick onboarding process.
- Cost: Consider the cost of the cybersecurity solution, including upfront expenses and ongoing maintenance fees. Balance the cost against the level of protection it provides and the value it adds to your organization.
Another factor to consider when selecting a solution is its cost. While some solutions may have lower upfront costs, they often come with additional fees for maintenance or upgrades over time. Therefore, you need to determine what kind of financial commitment your organization is willing to make for the chosen solution.
Arun KL, Security Architect
- Compliance Requirements: Ensure that the solution meets regulatory compliance standards relevant to your industry. This is especially important for industries such as healthcare and finance, which have strict data protection regulations.
Ensure compliance with the privacy laws in your jurisdiction(s). In the U.S., make sure you’ll be compliant with California’s Consumer Privacy Act, and in the E.U., with the General Data Protection Regulation. Also, remember that the legal obligation you owe customers under some privacy laws becomes more strict as the sensitivity of the data you hold increases (for example, geographic data versus medical information).
- Reputation and Reviews: Research the reputation of the cybersecurity solution provider and read reviews from other users. Look for testimonials and case studies to gauge the effectiveness of the solution in real-world scenarios.
Review the vendor’s ability to attract and retain top cybersecurity talent (the type who actively avoids working on dated technologies). Also, assess the potential brand hit of being breached through the vendor’s specific solution—some tools provide stronger “due diligence” optics after an incident. Adopting limited-lifespan solutions raises costs due to the need for constant skill retraining, and you may risk negative public perceptions of your brand.
A Better Alternative? Meet Heimdal® XDR
If SentinelOne feels too complex or Sophos doesn’t fit your environment, Heimdal® XDR offers a third, often more practical, alternative.
Our solution stands out as a great alternative, offering comprehensive protection, advanced threat intelligence, and simplified security management.
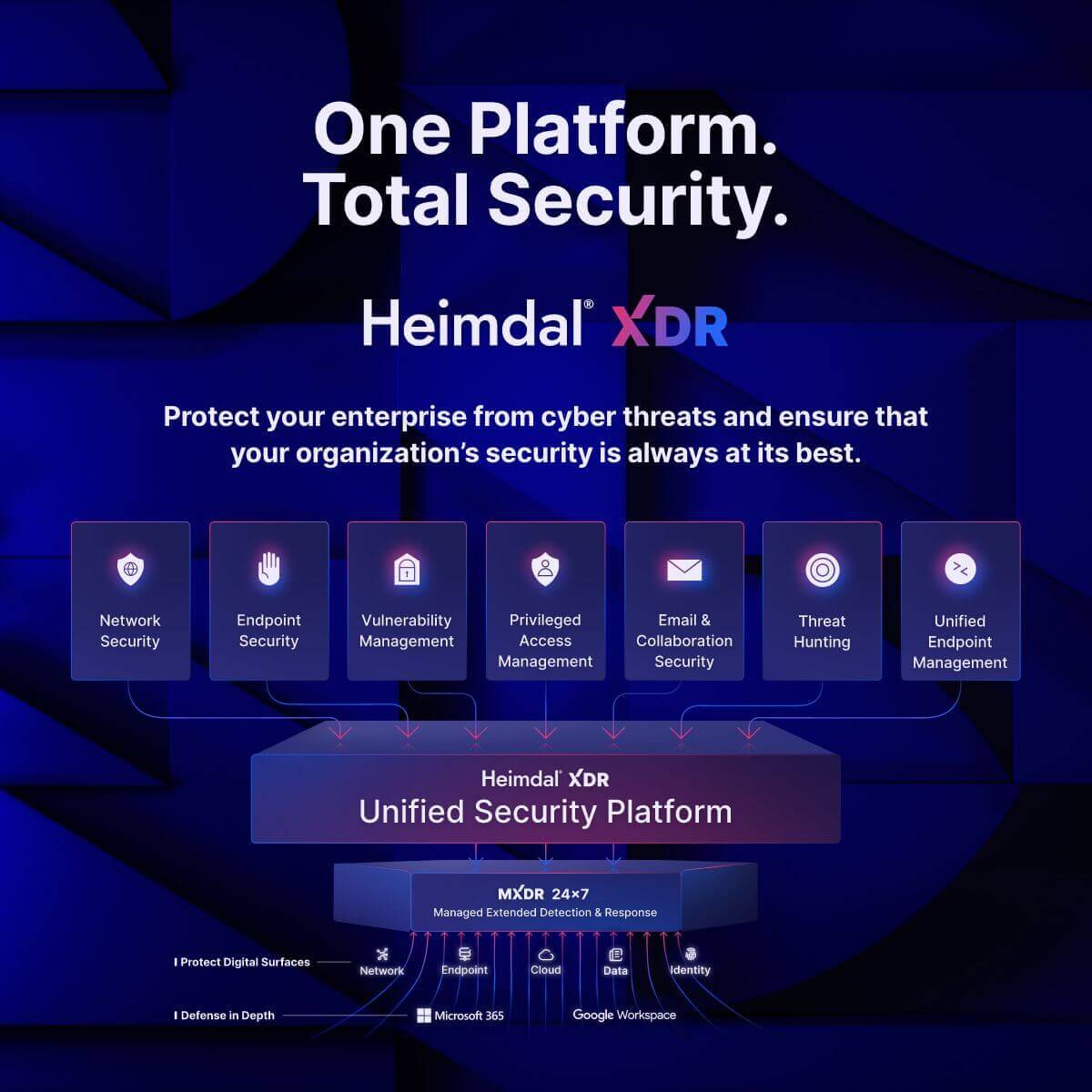
Heimdal® XDR is a comprehensive cybersecurity solution designed to protect your organization from a wide range of threats. Unlike traditional point security solutions, Heimdal® XDR provides end-to-end consolidated security, integrating seamlessly across your entire IT infrastructure.
This unified approach offers several key benefits:
- Unified Security: Heimdal® XDR eliminates the complexity of managing multiple security solutions by providing a single, integrated platform. This ensures complete visibility across your organization, leading to faster and more accurate threat detection and response.
- Superior Detection & Response: With advanced AI/ML-based detection capabilities, Heimdal® XDR can detect threats faster and more accurately than traditional security solutions. It offers a unified high-fidelity view of your IT enterprise, enabling automated response actions to be taken quickly.
- Cost and Complexity Reduction: By consolidating multiple security technologies into a single platform, Heimdal® XDR reduces complexity and costs associated with managing disparate solutions. This simplifies security management and optimizes the utilization of SecOps and IT resources.
Key Features of Heimdal XDR:
- Next-Gen Threat Intel: Heimdal® provides advanced threat intelligence, telemetry, and forensics details using AI/ML predictive models and MITRE ATT&CK techniques.
- Automated Remediation & Response: The Action Center enables one-click automated and assisted actions for quick, effective threat response across your digital enterprise.
- Integrated Threat Hunting: Empowers security teams with risk scores, indicators, and attack analysis for proactive threat hunting.
Compared to solutions like SentinelOne and Sophos, Heimdal® XDR offers several advantages:
- Unified Approach:Heimdal XDR offers a unified security platform, unlike SentinelOne and Sophos, which need multiple products for similar coverage.
- Advanced Threat Intelligence: Heimdal® XDR leverages advanced AI/ML-based detection capabilities and threat intelligence to provide superior protection against evolving threats.
- Simplicity and Efficiency: By reducing complexity and consolidating security technologies, Heimdal® XDR offers a more efficient and cost-effective solution for organizations of all sizes.
Frequently Asked Questions (FAQ)
What is better than SentinelOne?
Heimdal XDR offers a comprehensive cybersecurity solution that outshines SentinelOne in several key aspects. Unlike SentinelOne’s focus primarily on endpoint protection, Heimdal provides end-to-end consolidated security across multiple attack vectors.
With advanced threat intelligence, streamlined management, and proactive threat hunting capabilities, Heimdal ensures superior protection against evolving cyber threats. EDR protects endpoints, while XDR enhances threat detection by integrating data from multiple sources.
Does SentinelOne use AWS?
Yes, SentinelOne is an AWS technology, innovation and co-selling partner.
Which is better: EDR or XDR?
The choice between EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) depends on your organization’s needs. EDR focuses on endpoint security, providing detailed visibility and response capabilities. XDR, on the other hand, offers broader coverage across multiple security layers. EDR protects endpoints, while XDR enhances threat detection by integrating data from multiple sources.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











