Contents:
A ransomware outbreak called “Bad Rabbit” is spreading quickly around the world, with the damage epicenter being in the Eastern Europe.
It has been reported that this ransomware strain resembles in many ways non-Petya/Petya, and has already hit major organizations in Ukraine, Russia, Turkey and Bulgaria by causing business disruption.
What’s new about Bad Rabbit is that it saves the collected information, and apparently misuses them in trying to spread in internal networks. This makes Bad Rabbit more powerful than predecessors (non-Petya/WannaCry) of the same type.
How Bad Rabbit Spreads – Technical details explained
The infection is based on a fake update for Adobe Flash Player and dropped onto victims’ computers with a file named “install_flash_update.exe”.
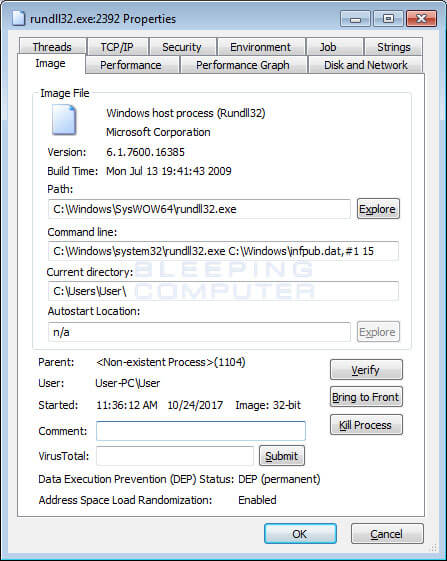
After that, the dropper will be copied to “C: \ Windows \ infpub.dat” and try to start this dll file at “rundll32”. The method used in this attack is brute-force, as the malicious hackers will begin to force their way into the local network in order to spread the ransomware into victims’ computers. To achieve this, they will use a combination of commonly used usernames and passwords, until they try to figure out the correct one.
Source: Bleeping Computer
The legitimate program DiskCryptor (an open source disk encryption program) is then downloaded via the site http: // diskcryptor [.] Net and used as a tool for encrypting files on the victim’s computer.
Video of #BadRabbit in action, from @anyrun_app (doesn’t show reboot) pic.twitter.com/3WpTj7f6qE
— Kevin Beaumont ? (@GossiTheDog) October 24, 2017
These files will be encrypted with what appears to be AES encryption key. This key used for encryption will then be encrypted with an embedded RSA-2048 public key. “It is not currently known where the final encrypted key is stored, but could possibly be added to the encrypted files”, said Bleeping Computer.
When Bad Rabbit encrypts files, it will not attach a new extension to the encrypted file’s name. Instead, it will add the file marker string “encrypted” to end of every encrypted file.
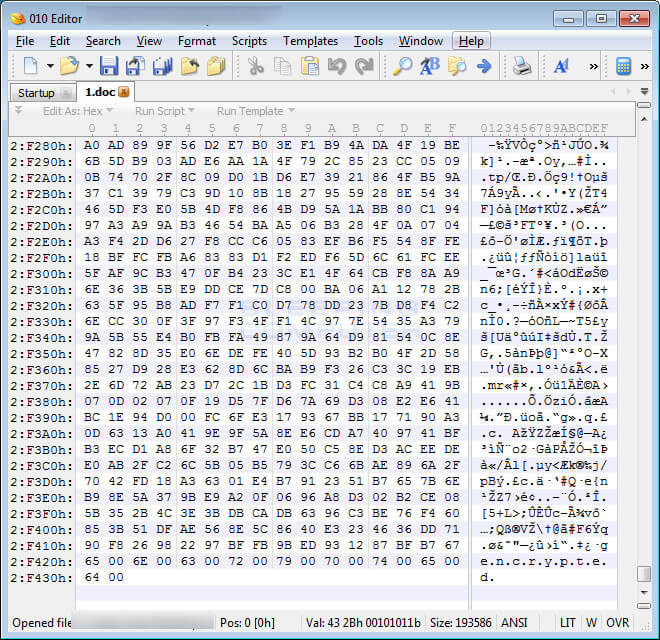 Source: Bleeping Computer
Source: Bleeping Computer
In order to mitigate the risk of infection with Bad Rabbit, we recommend you prevent the following files from being created and executed on your Windows endpoints:
c: \ windows \ infpub.dat
C: \ Windows \ cscc.dat
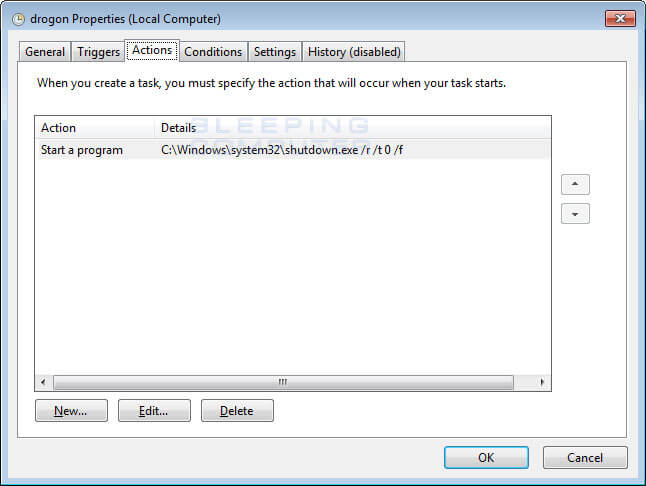
Additionally, Bad Rabbit ransomware creates scheduled tasks in the WIndows task manager, namely: Drogon, Rhaegal, and Viserion, the name of the three dragons from Game of Thrones.
Here’s how a task is displayed:
Source: Bleeping Computer
Bad Rabbit tries to encrypt all files with the following extensions: 3ds, 7z, accdb, ai, asm, asp, aspx, avhd, back, back, bmp, brw, c, cab, cc, cer, cfg, conf, cpp, crt, cs, ctl, cxx, dbf, dib, disk, djvu, doc, dwg, eml, fdb, gz, hd, hdd, hpp, hxx, iso, java, jif jpe jpeg jpg js kdbx, key, mail, mdb, msg, no.
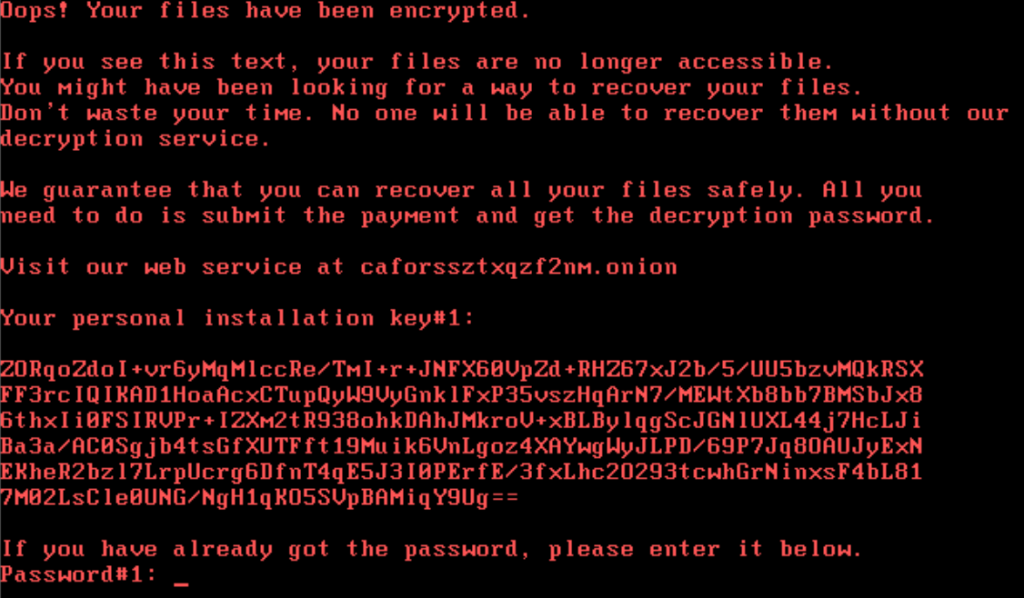
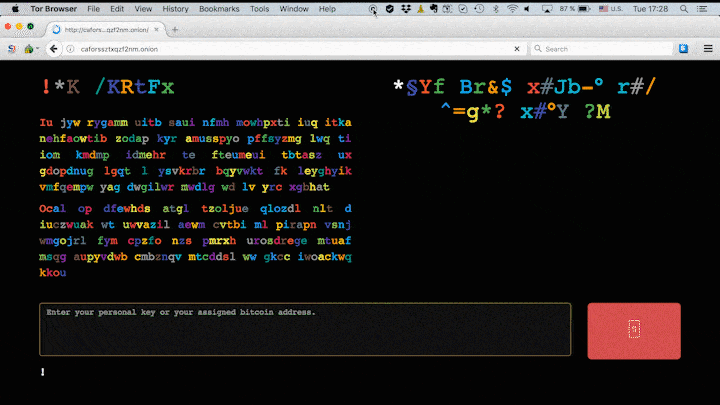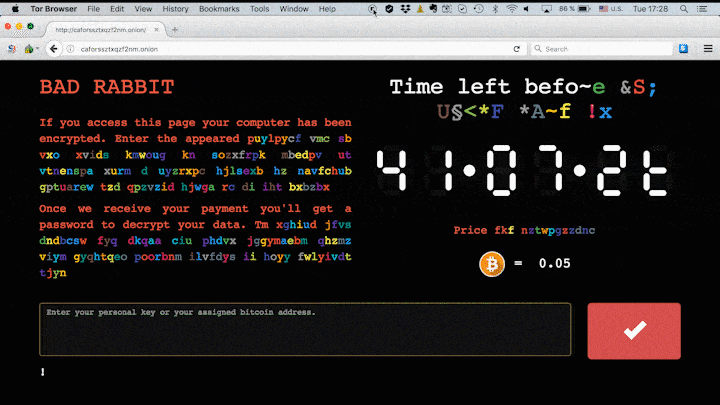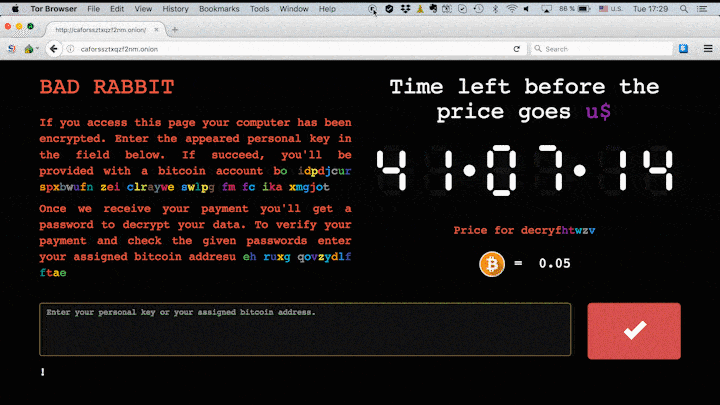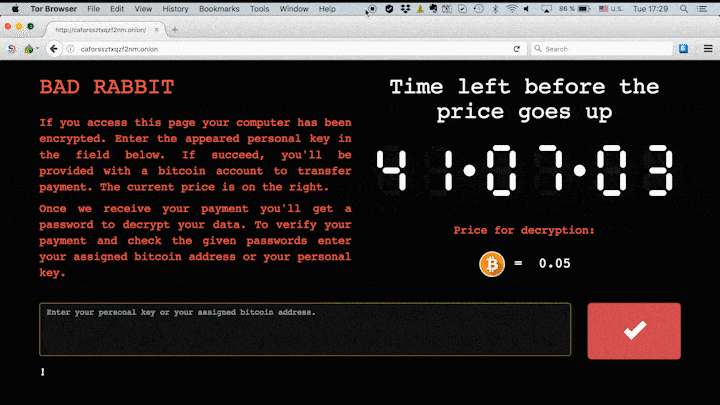
It then locks the computer, with no possibility for victims to access their data until a ransom is paid. When the job is completed, the following message will appear.
The malicious hackers behind this attack ask for 0.05 bitcoin as ransom, which is the equivalent of approximately $280.
Source: Kaspersky.com
UPDATE November 6, 2017
It appears that Bad Rabbit ransomware hid another quiet cyber attack happening in Ukraine. Serhiy Demedyuk, the head of the Ukrainian state cyber police, told Reuters that several Ukrainian institutions were targeted by severe phishing campaigns at the same time Bad Rabbit spread widely.
The main purpose of these campaigns were to compromise financial information and other sensitive data.
“During these attacks, we repeatedly detected more powerful, quiet attacks that were aimed at obtaining financial and confidential information,” said Demedyuk.
UPDATE October 30, 2017
New information about Bad Rabbit ransomware outbreak came to light. Researchers from Cisco Talos discovered that cybercriminals have been using the EternalRomance exploit to propagate in the network. It was also found that the Bad Rabbit ransomware used a modified version of an NSA exploit to spread infection.
Good news from the researchers at Kaspersky Lab team who analyzed the sample of this threat and discovered some flaws in the way online criminals have operated. Also, some users’ files encrypted by Bad Rabbit can be recovered by following a technical procedure including the AES key which is used for disk encryption.
“As part of our analysis, we extracted the password generated by the malware during a debugging session and attempted to enter this password when the system was locked after reboot. The password indeed worked and the boot-up process continued.”
Unlike Petya, Bad Rabbit is not destructive as a wiper. It encrypts information on the computer’s hard disk and modifies the bootloader by replacing the MBR (Master Boot Record). The ransom note also looks similar with the one used for (non)Petya attack.
It also differs primarily by spreading via Mimikatz (to extract credentials from the local computer’s memory) or via SMB and WebDav.
“We currently have no evidence that the EternalBlue exploit is being utilized to spread the infection”
said Martin Lee, Technical Lead for Security Research at Talos
As it appears now, the distribution of Bad Rabbit has been done via malvertising or script injection, and most of these detections were reported on popular Russian and Ukrainian websites. ESET researchers also said there are reports of computers in Turkey, Bulgaria and other countries are affected.
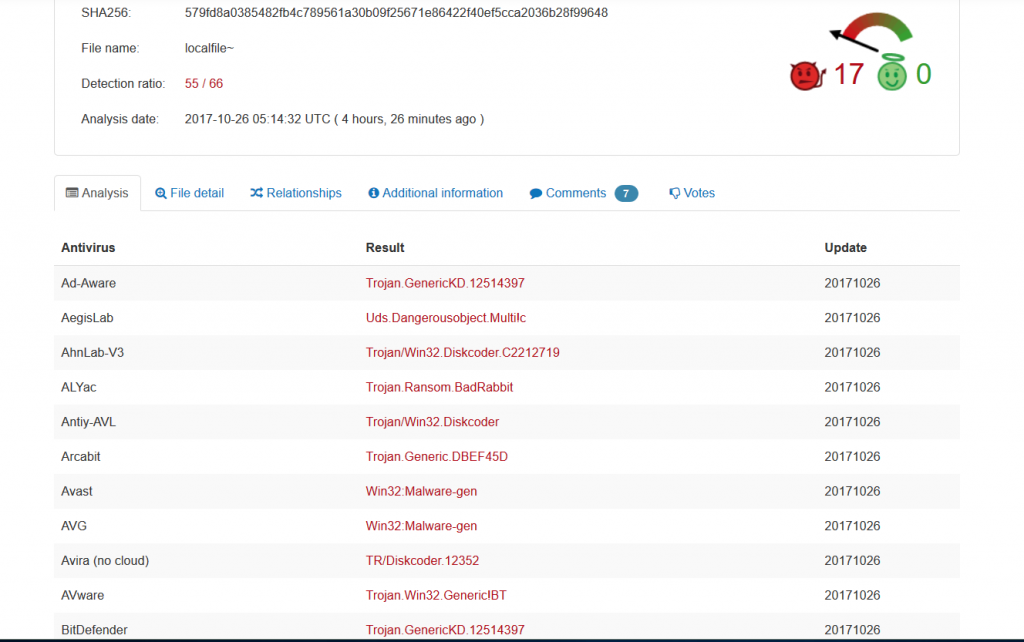
VirusTotal showed that 55 of 66 antivirus solutions were detecting this type of malware at the time this article was posted.
Source: VirusTotal
Who’s been affected?
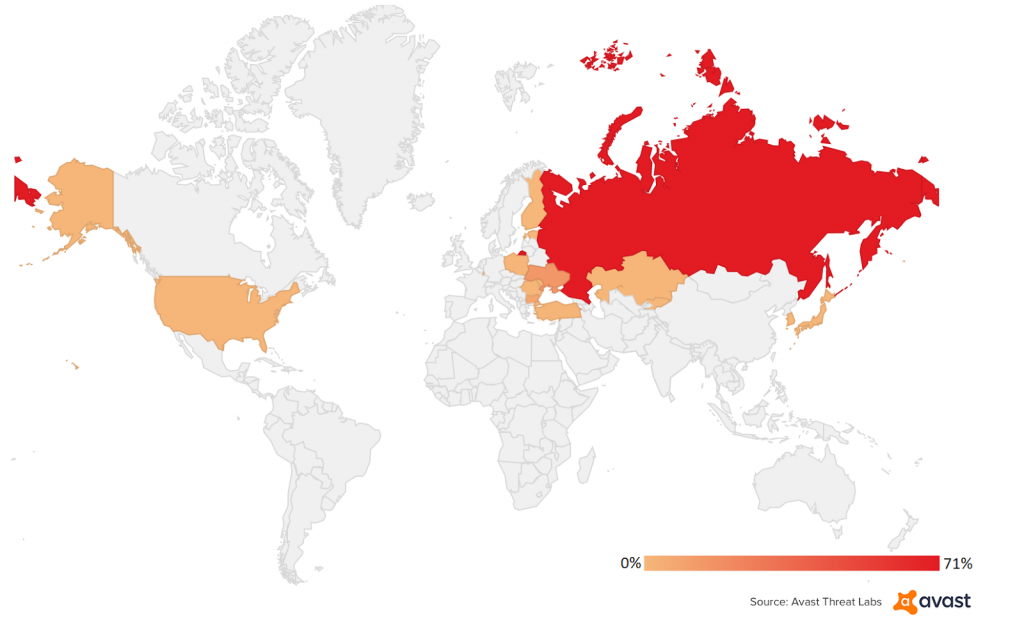
The bad news is that these ransomware strains spread fast and have (already) caused a lot of damage so far. Most of the targets are located in Russia with 65% distribution and infections detected, transportation organizations in Ukraine, such as the Kiev metro, the Odessa airport, as well as some governmental organizations and private businesses.
Similar attacks have been spotted in other countries: Ukraine, Turkey, Germany, Bulgaria, Poland, Romania and the United States as well. Here’s a map of Bad Rabbit attacks and global detection rate.
Source: Avast blog
Protection guide against ransomware attacks
It might look like a nightmare scenario, but you should not panic. Remain calm, be proactive and take all the measures needed to protect your important data and stay safe online.
Security researcher Amit Serper found a simple way to prevent the distribution of Bad Rabbit and the infection on your computer. Create the following files in Windows – c:\windows\infpub.dat & c:\windows\cscc.dat- remove ALL PERMISSIONS (inheritance).
If you are one of the victims of this ransomware attack, we strongly recommend not to pay the ransom. At this moment, there are no details if there’s any way to decrypt files locked by Bad Rabbit. However, there are some decryption tools out there that you can use/try. Also, this anti-ransomware checklist might help.
We recommend users to take the following protection guide against Bad Rabbit attack:
- Update your Windows system or any other operating system installed on your computer. It is important to install all the latest updates for all your apps too.
- Don’t keep your important data exclusively on your computer and make sure you have at least 2 backups of your valuable data on external sources such as a hard drive or in the cloud (Google Drive, Dropbox, etc.). This useful guide will show you how to do this.
- Try not to use the administrator account every day and remember to disable macros in the Microsoft Office Package.
- DO NOT open (spam) or download email (messages) from untrusted or unknown sources that could infect your device. Moreover, don’t click on suspicious links.
- Make sure you have a paid antivirus software which is also up to date, or consider having a proactive anti ransomware protection (here’s what Heimdal can do for you).
- It’s recommended not to use the administrator account every day and remember to disable macros in the Microsoft Office Package;
- When signing into your email or social accounts, you should always use two-factor authentication system for more security.
- Should you want to remember what is ransomware and how to keep your system protected, we strongly recommend reading this useful guide.
- The“it can’t happen to me” mindset doesn’t work and focus on education should be a top priority. Cyber security education is essential for everyone to have minimum cyber security knowledge, so they can easily discern the good from the bad, and be safer in the online landscape.
Have you been affected by Bad Rabbit ransomware? Share your thoughts in a comment below.
We’ll keep updating this article as new details emerge.
*This article features cyber intelligence provided by CSIS Security Group researchers.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security