Contents:
Privilege escalation happens when an attacker attempts to gain unauthorized access to high-level privileges on a system, network, or application.
Key takeaways of this article:
- Main types of privilege escalation
- What are the risks of a privilege escalation attack
- Privilege escalation techniques according to MITRE
- Attack types
- How to keep safe from privilege escalation attacks
How Privilege Escalation Works
To perform a privilege escalation attack, a threat actor should first infiltrate the targeted network. Hackers usually gain initial access by exploiting a vulnerability, using compromised credentials or social engineering techniques.
At this point, there are two possibilities. Hackers might take over a privileged account from the beginning, or they could only gain access to a standard user account.
In the second scenario, their next step would be to survey the network until they can continue the attack. To achieve their further goals, they will need to gain access to a privileged account. Privileged accounts grant users special rights, like access to critical data and infrastructure.
After gaining a foothold in the compromised system, the hackers will attempt to gain administrative rights. Thus, they will eventually be able to perform a series of actions on the operating system or the server:
- run commands
- change security configurations
- install malware
- move laterally
Further on, privilege escalation can lead to:
- business disruption
- compromising confidentiality, integrity, and access to sensitive data
- unauthorized access to system resources
- complete system takeover
Privilege Escalation Types
There are two types of privilege escalation: vertical and horizontal. In VPE (vertical privilege escalation), the attacker aims taking over an account that has system or root privileges. In HPE (horizontal privilege escalation) the hacker takes over an account and then tries to expand its control to other similar ones.
Threat actors can achieve both types of privilege escalation by taking advantage of existing operating system vulnerabilities.
Vertical Privilege Escalation
Vertical privilege escalation, also known as privilege elevation, starts from a point of lower privilege. Then the hacker tries to escalate privileges to a higher level. First, they gain access to a standard user account. The next step will be to try obtaining control over a superuser account or domain administrative account. Hackers can attempt vertical privilege escalation to move from a user access level to kernel access level. They could try to gain root privileges or kernel-level access. If they succeed, they’ll become an advanced persistent threat.
To succeed vertical privilege escalation, the threat actor could:
- use a misconfiguration to bypass privilege controls
- exploit unpatched vulnerabilities in the software or the operating system
- find and exploit zero-days
- use its current foothold to obtain privileged credentials
Horizontal Privilege Escalation
This privilege escalation type is also known as account takeover. First, the attacker gains privileged access to a standard user account. At this phase, they only have low-level privileges.
However, having access to a user account means they gained a foothold into the system. After that, the malicious actor can move horizontally through the network and gain new rights among same level of privileges accounts.
Intruders can use phishing or spearphishing attacks to obtain access to this standard user account. After they trick an employee to reveal username and password, they’ll be able to access certain files, web applications, subnetworks, etc.
Privilege Escalation Risks
Privilege escalation is one of the most dangerous types of attacks in cybersecurity because it can lead to attackers taking over the entire system.
Data breaching
A major risk associated with privilege escalation is compromising sensitive data. Having control over privileged accounts gives can enable hackers to view, edit, delete or exfiltrate data. Data breaches generate workflow disruption and a negative impact on the company`s brand.
Open path for other cyberattacks
A successful privilege escalation attack can be a starting point for other cyberattacks. Threat actors can use their newly gained high-level rights to deploy malware in the system they targeted. So, whenever you detect suspicious activities in privileged sessions, investigate further. Search deeper into the organization’s system to check for other signs of malicious activity.
The 14 Privilege Escalation Techniques
According to the MITRE ATT&CK knowledge base, there are 14 main privilege escalation techniques. Each has several other sub techniques that researchers observed.
- Abuse elevation control mechanism
- Access token manipulation
- Account manipulation
- Boot or logon autostart execution
- Boot or logon initialization scripts
- Create or modify system process
- Domain policy modification
- Escape to host
- Event triggered execution
- Exploitation for privilege escalation
- Hijack execution flow
- Process injection
- Scheduled task/job
- Valid accounts
Privilege Escalation Attack Examples
I’ve described above how generally privilege escalation works. Now, let’s illustrate a more practical part of this topic. Let’s see some privilege escalation attack examples depending on the operating system. In the following lines, I am going to give you examples of Windows privilege escalation attacks and also examples of Linux privilege escalation attacks. These examples come along with recommended mitigation measures.
Windows Privilege Escalation
Hackers can achieve privilege escalation in Windows in many ways. Here are 3 examples of Windows privilege escalation attacks and what you can do about them:
Windows Sticky-Key Attack
The threat actor can use the ‘enable sticky keys’ feature to bypass normal endpoint auth and gain system-level privileges. From here, he can create a fake admin account, install a secret backdoor, and much more.
Windows Sticky Key Attack Mitigation Measure: prevent the launch of sticky keys. Go to HKEY_CURRENT_USER\Control Panel\Accessibility\StickyKeys\Flags in your Windows registry and change the value from “510” to “510”. This will add encryption protection to your Windows partition.
Credential Dumping (Purloining Stored Credentials)
Credential dumping is a great way of recovering hashed credentials from key system locations. Compared to the sticky-key attack, credential dumping is a bit more challenging since it requires tools and time. So, how does this work? Well, all machines running Windows cache login credentials in various locations. Basically, if you know where to look, you can easily pull-out stuff like admin login passwords, master passwords for local passphrase vaults, and so on.
The hacker will still need to find a way to ‘unhash’ those passwords. Simply put, credential dumping is like searching every trash can in your city and hoping to find a piece of paper that holds the key code.
Credential Dumping Attack Mitigation Measure:
- increase password complexity
- enable PPL (Protect Process Light) for LSA
- check Domain controller backups
- add a user to the Protected Users list in your Access Directory
Access Token Manipulation
Through token manipulation, an attacker can use 3 types of privilege escalation methods:
- Token theft – an attacker copies an existing token using DuplicateToken(Ex). They can use this token to mimic a logged-on user’s security with ImpersonateLoggedOnUser, or assign it to a thread with SetThreatToken. This is useful when the target user is logged on but not over a network.
- Create process with a token – the attacker creates a new token with DuplicateToken(Ex). Then they use CreateProcessWithTokenW to start a new process under another user’s security context. This enables them to run processes as different users.
- Make and impersonate token – if an attacker has a username and password but the user isn’t logged in, they can create a logon session using LogonUser. This gives them a new session’s access token, which they can assign to a thread using SetThreadToken.
Access Token Manipulation Prevention Measure:
- ban user groups or users from creating tokens
- enforce the least-privilege principle and police admin accounts.
NTLM relay or Hot-Tater Attack
The Hot-tater attack is a highly sophisticated attack that involves exploiting vulnerabilities found in the NTML relay and the local NBNS Spoofer.
The goal is to obtain NT AUTHORITY\SYSTEM privileges on the victim’s machine. ‘Hot-tatting’ a target is a triphasic process:
- interrogating the NBNS spoofer
- requesting a fake WPAD proxy server
- MITMing the NTLM protocol
The result: the threat actor persuades the victim’s machine to authenticate via the NTML protocol. The auth process’s details are sent to the attacker. Thus, the hacker gains system-level privileges.
Linux Privilege Escalation
When talking about Linux privilege escalation, hackers use a process dubbed “enumeration”. This helps them detect vulnerabilities that will further permit the unfolding of a privileged escalation attack. To do that, they use a series of automated tools.
Threat actors get more knowledge about the system through port scanning, Google searches, or direct interaction. Another method is to look for available Perl or Phython, which are basically two high-level programming languages that will permit them to deploy an exploit code into the system.
There are two techniques associated with Linux privilege escalation: kernel exploit and SUDO rights exploitation.
Kernel Exploit
A kernel exploit attack is possible if there are flaws in the Linux kernel that let the hacker abuse them in order to achieve Linux root system access.
Kernel Exploit Mitigation Measure: According to MITRE ATT&CK, in this case, Linux updates and patches should be installed in a timely manner. You should restrict or remove files such as FTP, SCP or curl that permit file transfer actions. Or you could associate them with just a handful of users or IPs, to prevent an exploit infiltration.
SUDO Rights Exploitation
SUDO stands for a Linux program that will give different users the ability to run programs by means of privileged rights that belong to somebody else. Before they can do that, the privileged account owners must grant them access to do so. In this case, the risk is command execution with root privileges.
SUDO Right Exploitation Mitigation Measure: According to MITRE ATT&CK, compilers, interpreters, or editors should never be granted rights that allow access to programming language compiler. Neither should they be able to access other programs that facilitate a shell running action if they don’ t have these special rights.
Privilege Escalation Attack Indicators

The sooner you discover a privilege escalation attempt, the better. So, monitor systems and privileged sessions to catch any sign of suspicious activity in time.
Here are four key indicators of privilege escalation:
- malware detection on sensitive systems
- unusual network communications
- security features bypass
- suspicious activities in privileged session logins
How to Keep Safe from Privilege Escalation Attacks
For starters, I advise you to try an automated privileged access management solution to prevent privilege escalation attacks. Don` take my word for it. Read what CISA and the National Security Agency (NSA) have to say on the matter:
Privileged accounts require additional monitoring and control and should be separately managed using a Privileged Access Management (PAM) solution with strong identity governance.
Source – Identity and Access Management Recommended Best Practices Guide for Administrators
Besides that, there is a safe access checklist that you should include into your defense strategy.
Update and patch regularly
Hackers often exploit known vulnerabilities to achieve privilege escalation. Make sure you patch all software, including operating systems and 3rd parties, in time. A patch and asset management solution will help you automate the process and avoid human error. Missing legacy software or old hardware is a common entry point that hackers take advantage of.
Enforce the Principle of Least Privilege
The Principle of Least Privilege says users should only have the rights they need to do their jobs. This way, if a random employee falls victim to a phishing attack, the incident will be easier to contain.
Monitor and audit system activities
Check for suspicious activities inside the system regularly. Auditing tools will help you to track changes in system configurations and permissions. Revoke all permissions that are no longer needed to avoid users having unnecessary privileged rights.
Educate employees
Train your colleagues to identify a phishing email and be aware of other social engineering tactics. Compromised credentials are a common method that hackers use for initial access.
Secure configuration management
Ensure systems are securely configured. Avoid default setups and passwords, and regularly review configurations for potential vulnerabilities.
Enforce network segmentation
Segregate networks and use firewalls to limit the spread of a privilege escalation attack. Control the traffic between different segments of your network to detect malicious communication attempts.
Employ Multi-Factor Authentication
All elevated privileges accounts should use multi-factor authentication. In case the attackers succeed compromising credentials, MFA will stop their attempt to actually take over the account.
How Can Heimdal® Help?
Our Privileged Access Management solution stands out through the following characteristics:
- automatically de-escalates user rights, in case our Nex-Gen Antivirus detects any threats
- helps adopt the Zero Trust model by granting users and applications only the permissions they need
- has very efficient approval/denial flow
- our flexible PAM tool enables you to either escalate or de-escalate user rights remotely, no matter where you are
- offers settings in terms of AD group rights, escalation period customization, local admin rights removal, session tracking, system files elevation blocking
- easy to pull out reports enable you to prove NIST AC-5 and NIST AC-1,6 compliance. That will help build a trustworthy relationship with your partners.
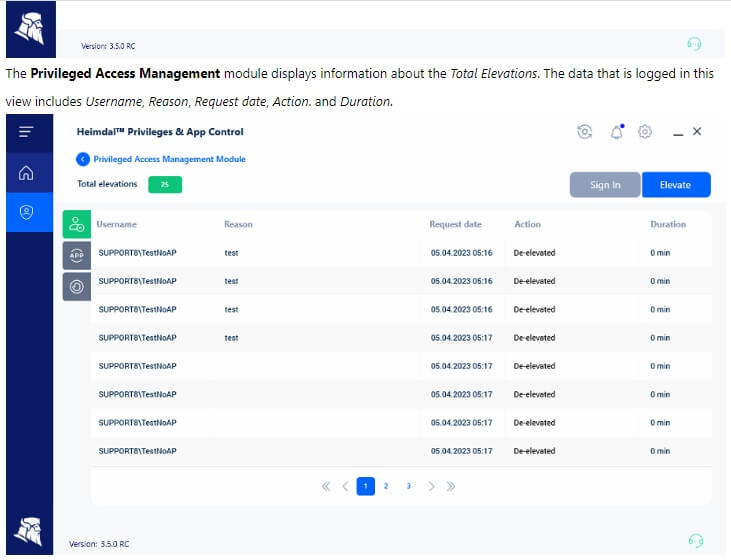
I recommend you use this tool along with the Application Control module. It will enable you to perform application execution approval or denial. The module also offers live session customization to further ensure business safety.
Managing privileges is a fundamental aspect of any cybersecurity strategy. Make sure you have the proper PAM tool and be a step ahead of hackers!

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Wrapping Up…
Privilege escalation attacks often result in data breaches. That brings along data loss, ransomware attacks, reputational losses and even fines. So, take the necessary safety measures to keep privileged accounts and sessions safe from malicious actors.
Privileged Access Management (PAM) security mechanisms are designed to prevent both internal and external threats. They are a trustworthy ally in your quest to keep end-to-end data and access safe.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security