Contents:
Endpoint Privilege Management ensures that end-users have the least privilege when running trusted applications. EPM also determines whether an application should run, and under what privilege conditions.
By using EPM, organizations can prevent and contain attacks on desktops, laptops, and servers. Thus, they reduce the risk of information being stolen or encrypted and held for ransom.
Gartner analyst Lori Robinson defines endpoint privilege management as the combination of privilege management and application control:
Endpoint privilege management (EPM) technologies combine application control and privilege management to ensure that only trusted applications run and that they run with the lowest possible privilege. With EPM, organizations can remove local admin access with minimal impact on end users.
When explaining what endpoint privilege management is, Robinson says that by employing on-demand privilege elevation, EPM provides users with the privileges necessary to run trusted applications and conduct authorized tasks. EPM further protects and enables end-users by empowering them to get access to operations for which they were not previously approved.
In short, with endpoint privilege management employees are not granted permissions for more than what is required of their role. In cybersecurity, we define this as the “principle of least privilege”.
Benefits of Using Endpoint Privilege Management
Within any organization, privileges are usually split between two levels of hierarchy: standard users and administrators. The highest privilege level is often provided to Domain Administrators who can modify and gain access to all standard user machines. On the other hand, local administrators have full access to a particular endpoint and the potentially sensitive data within.
In addition, administrators have exclusive privileges to run certain applications with elevated privileges.
When a standard user needs to run an application that only works in administrator mode, organizations can provide the user with admin credentials. Another way to solve the problem is elevate the entire organizational-level privilege of that particular user.
However, this would not only give them access to that particular application but also to all the top-level privileges the admin has. With Endpoint Privilege Management, organizations can empower high-end users safely.
The advantages of implementing EPM solutions don’t stop here. Let’s have a look at the list of benefits they offer:
#1. EPM removes administrator rights from users
Privileged accounts are often the target of malware. Hackers need elevated privileges to gain initial access and infiltrate into corporate networks. Endpoint Privilege Management allows you to remove administrator rights from users that not usually need them to do their jobs. Apply the Principle of Least Privilege (PoLP) and only grant standard users admin rights when absolutely necessary. This way you`ll be able to enhance endpoint security without compromising productivity.
#2. EPM assigns privileges to applications
Endpoint Privilege Management assigns the necessary privileges to the user when the application is launched. The mechanism is invisible to the end-user and allows the latter to remain productive using their standard account. They will not gain administrative privileges unless they need that to do their job.
#3. EPM provides simple and centralized management
Allowing an application to run with privileges has never been easier. Declare applications in policies and configure identification options. Then assign the applications to the users in question, and configure any options (warning messages, audit and monitoring, etc.). The policies are automatically converted to group policies and deployed during the next application cycle.
#4. EPM ensures application control
In addition to controlling the privileges assigned to applications, Endpoint Privilege Management can also be used to control which applications a standard user is authorized to install or run. Policies can be configured as a “whitelist” listing approved applications on a system. Unauthorized applications, including installers and scripts, can be blocked.
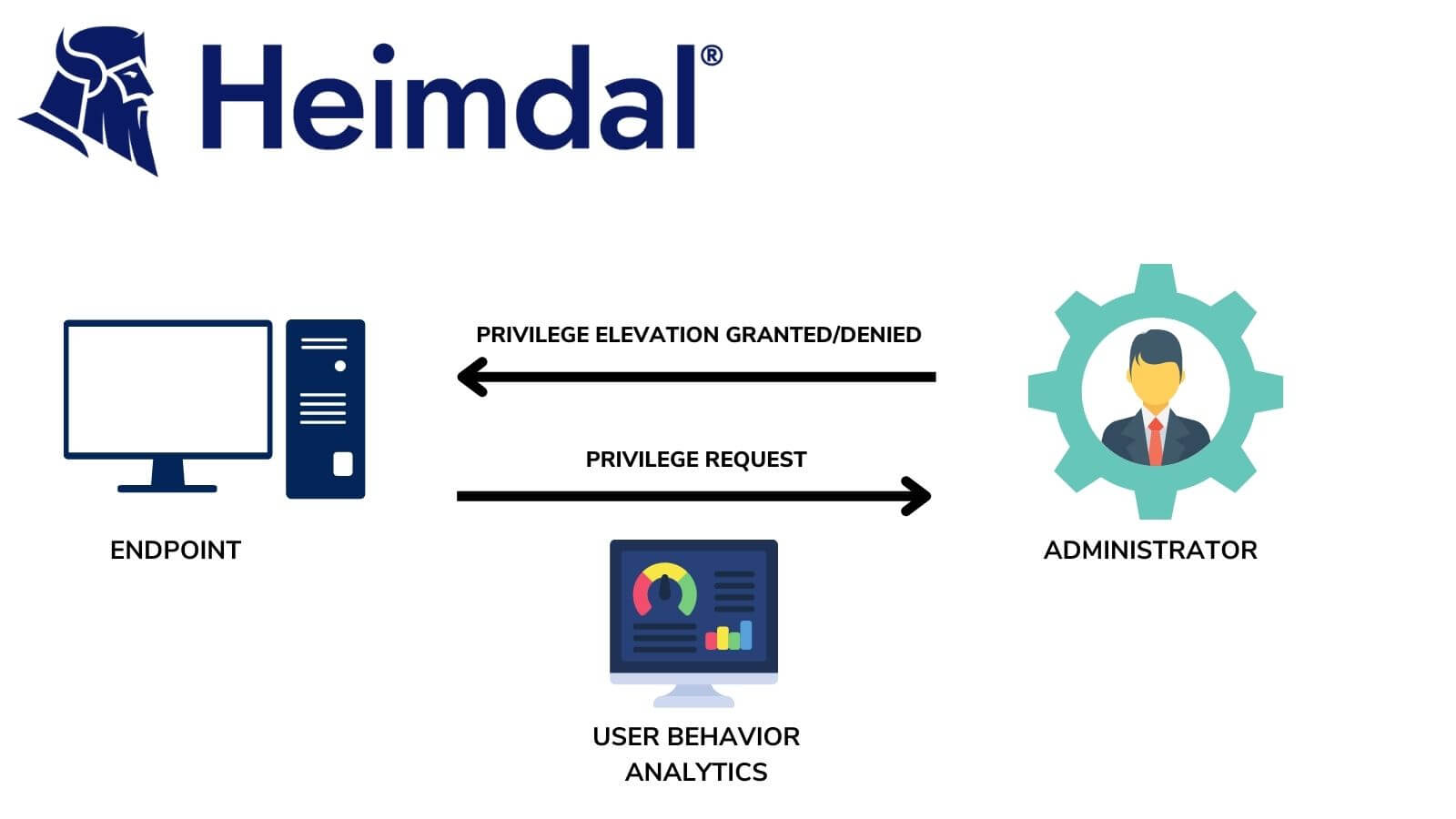
#5. EPM offers on-demand elevation
For the most demanding users, Endpoint Privilege Management solutions offer the option of “on-demand” elevation. The user logs in with a standard account and can elevate an application from a right-click in the context menu. Elevated applications are audited, to ensure that users do not abuse these elevated privileges.
#6. EPM upgrades ease of deployment
Thanks to its predefined rules, Endpoint Privilege Management innovates by its ease of installation. The various pre-configured scenarios make it possible to cover the various needs of your users and thus reduce deployment costs.
How Can Endpoint Privilege Management Prevent Attacks
EPM helps security managers enforce Zero trust best practices as it ensures greater privilege endpoint visibility. Applying a zero-trust policy and the principle of the least privilege reduces the attack surface and bolsters security posture.
Misused local admin access can compromise network security. That can further result in data loss, high support costs, and poor user experience. Users with unfiltered local admin privileges have full control of the endpoint. Consequently, they can
- perform file system changes,
- run unauthorized processes/ apps,
- disable security settings,
- install malware that exploits privileged access,
- change desktop configuration settings.
Although local admin rights are not as powerful as domain-level privileges, they shouldn’t be overlooked. Hackers can exploit local administrative privileges to gain access to network controls. After breaking into an endpoint system, they use the passwords and privileges to further intrude the most valuable assets.
EPM can keep cyberattacks restrained to users’ devices. By using privilege escalation, users can reduce lateral movement by eliminating or decreasing local admin privileges on endpoints.
However, EPM doesn’t replace firewalls or anti-viruses, which can block endpoint attacks. Therefore, for comprehensive endpoint security, I advise you to integrate an EPM solution with additional technologies.
Heimdal’s Endpoint Detection and Response (EDR) brings you real-time proactive security via DNS filtering, smart threat hunting, proactive behavioral detection, automated patch management, a next-gen Antivirus, and a module for automated admin rights escalation/de-escalation procedures. Thus, we deliver multi-layered security within a single and lightweight agent.
Our customers get access to next-gen endpoint threat prevention and protection from both known and undiscovered threats. In addition, they benefit a market-leading detection rate and compliance, all in one package.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Final Thoughts on What Is Endpoint Privilege Management
Security breach incidents such as theft of credentials, corporate espionage, and swiping of sensitive data arise from unprotected connected devices. IT administrators often find it difficult to keep a weather eye on every activity performed from endpoint privileges, causing a lack of IT oversight.
Organizations use endpoint privilege management solutions to make sure access restrictions don`t obstruct productivity, but also to maintain endpoint security. Providing local admin rights or top-level privileges to standard users can enlarge the attack surface, which could bring unwanted challenges to security teams.
However, an EPM solution alone is no substitute for good administrative control. Only when used together with proper technologies, it becomes a powerful tool that automatically de-escalates user rights, should any threats be detected on the machine.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










