Contents:
What is Ryuk Ransomware?
Widely known for targeting governments, academia, healthcare, manufacturing, and technology organizations’ cybersystems, Ryuk is a ransomware-as-a-service (RaaS) group that’s been active since August 2018. It typically encrypts data on an infected system, rendering the data inaccessible until a ransom is paid in untraceable bitcoin. The operators behind Ryuk are known for running a private affiliate program where affiliates can submit applications and resumes to apply for membership. By the end of 2020, the operators behind Ryuk netted a total of $150 million.
Ryuk is at the top of the RaaS rankings, having payloads delivered by its affiliates. The gang’s affiliates were attacking approximately 20 companies every week in the last months of 2020, and, beginning with November 2020, they coordinated a massive wave of attacks on the US healthcare system.
Origins
According to cybersecurity researchers, Ryuk was developed and is currently operated by the GRIM SPIDER APT (Advanced Persistent Threat group), a splinter group traced back to WIZARD SPIDER, the criminal mastermind behind TrickBot. Russian in origin, GRIM SPIDER embraces WIZARD SPIDER’s big-game hunting ideology, whereas big trophies can be claimed by attacking big targets.
The APT group’s voracity for HVTs has left behind countless victims – the Chicago Tribune, the Baltimore Sun, Orlando Sentiment, and the San Diego Union-Tribune are among Ryuk’s most ‘popular’ victims.
Ryuk Over Time
Below you will find a brief timeline of incidents involving the Ryuk ransomware gang:
- December 2018 – Tribune Publishing attack with Ryuk ransomware right before the Christmas holidays. The internal IT team managed to overcome the first Ryuk wave by patching the vulnerabilities and restoring stolen data from backup. The solution proved to be futile, as Ryuk managed to reinfect the network. Tribune asks the FBI to intervene. A resolution comes after a couple of days. The FBI and Tribune refused to release any details pertaining to the solution found.
- March 2019 – Jackson County’s infrastructure attacked. Damages: $400,000 (22 BTC).
- April 2019 – Imperial County’s IT infrastructure gets hit by Ryuk. The attackers demanded $1.2 million (65 BTC). Victims refused to pay.
- June 2019 – Lake City systems locked by ransomware. Victims had to pay $460,000 (25 BTC) to regain control over their systems.
- July 2019 – La Porte County public institutions hit by the Ryuk ransomware. Victims had to pay $130,000 (7 BTC).
- August 2019 – Rockville Centre school district affected by Ryuk. The municipality had to pay $100,000 (5 BTC) to regain control.
- October 2019 – Ryuk creators take down a hospital chain administrated by the National Veterinary Associates. Over 400 clinics experienced downtimes on payment systems and patient curation systems. The NVA refused to offer any details on how the situation was resolved.
- November 2019 – Ryuk operators launch attacks against several HVTs: Louisiana Office of Technology Services, Prosegur (i.e. Spanish security company), Cadena SER (the largest radio station in Spain), and T-System (E2E healthcare and emergency solutions providers).
- January 2020 – Ryuk operators attacked gas and oil facilities. In addition, the same operators were found to be involved in several other incidents targeting healthcare providers.
- September 2020 – Universal Health Services (UHS) healthcare providers have reportedly shut down systems at healthcare facilities after a Ryuk ransomware attack. The incident resulted in about $67 million in lost operating income, labor expenses, and overall recovery costs.
- January 2021 – A new version with “worm-like” capabilities was identified. The new Ryuk variant can spread automatically/without intervention through infected networks.
- March 2021 – Ryuk targeted the systems of SEPE, the Spanish government agency for labor. The systems were taken down following a ransomware attack that affected more than 700 agency offices across Spain.
- April 2021 – New Ryuk hacking techniques were revealed. What’s more, the threat actors’ personal favorite initial infection vector continues to be the targeted phishing emails for malware delivery.
- May 2021 – Ryuk ransomware infects Bio Research Institute after a student installs pirated software. The attack occurred because the student didn’t want to pay for a license, causing a week’s worth of research data.
Ryuk Ransomware Attack Mechanism
This section will offer more insight into how the Ryuk ransomware chooses its victims and what happens before and after the encryption process. Before we begin, let’s take a step back and look at Ryuk’s kill chain.
MITRE and Palo Alto Networks have synthesized Ryuk’s attack cycle in the following framework:
| Initial access | Execution | Persistence | Privilege Escalation | Defense Evasion | Discovery | Impact |
|---|---|---|---|---|---|---|
| Spearphishing/ phishing - malicious email attachment | Native API | Registry Run keys or startup folder | Process injection | Match real names and locations | System network config discovery | Services stopped and\or disabled |
| Valid account – credentials obtained through social engineering | Windows Command Shell | Valid accounts | Registry keys or startup folder | Process injection | Directory and file discovery | Data encryption |
| - | - | - | Valid accounts | Modify or disable tools | Process discovery | Disable system recovery |
| - | - | - | Access token manipulation | Valid accounts | - | - |
| - | - | - | - | Access token manipulation | - | - |
The Ryuk – Emotet – TrickBot Trinity
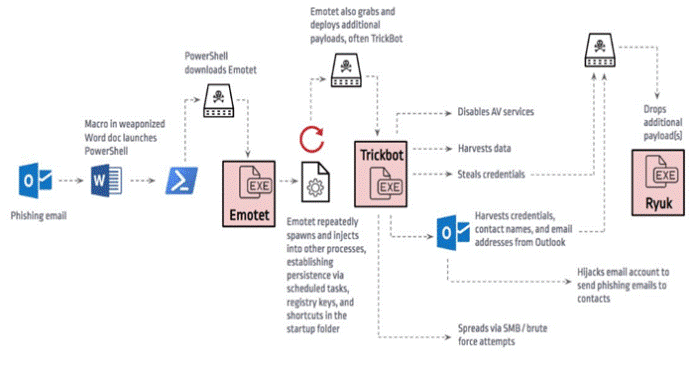
One running hypothesis suggests that Ryuk doesn’t infect a network on its own. According to GBHackers on Security, in some ransomware campaigns, Ryuk has been observed to work alongside Emotet and Trickbot in order to cover up all attack vectors and increase the likelihood of a positive outcome for the attackers – data encryption.
Now, based on the hypothesis, Emotet can be used to spawn dummy systems processes or to inject evil code into other processes for persistence purposes. This phase is achieved through various techniques such as registry keys, scheduled tasks, and shortcuts created within the startup folder.
After his phase is over, Emotet will download and install Trickbot, which will be used in the pre-encryption process. Trickbot is utilized to disable AV-related services, critical system processes, harvest data, steal credentials, and more. Interestingly enough, TrickBot’s not only used to deploy Ryuk but also to tap into the victim’s email address.
This serves two purposes: (1) to download an additional malicious payload, which in this case is Ryuk, and (2) to send phishing emails to the victim’s contact list. Compared to the Emotet phase, which uses the eponymous kit for the sole purpose of spawning and injecting dummy processes, TrickBot will act as a gateway for Ryuk and for lateral movement via brute-force attacks and Server Message Block Relay Attacks. These steps are summarized in the picture below.
Image courtesy of GBHackers on Security
Ryuk Ransomware Behavioral Analysis
Breaking the Ryuk ransomware down to the basics, the following pattern can be observed: (1) Dropper & Ryuk binary ops (2) Process enumeration, persistence, and privilege escalation, (3) Code injection and task-killing, (4) Encryption, and (5) Ransom.
(1) Malware dropper & Ryuk binary ops
The dropper’s loaded onto the victim’s machine via a PowerShell, C2C retrieval. Once the dropper lands on the machine, it will automatically check for the version of the target Operating Systems by calling the MajorVersion property (i.e. 0x00000004 to 0xFFFFFFF).
If MajorVersion is equal to five, then the dropper will place the ransomware executable into the C:\Documents and Setting\Default User folder. That’s the default ransomware download file for Windows Server 2003, XP, and Windows 2000.
If the value’s not equal to five, the dropper will place the ransomware in the C:\Users\Public folder. The ransomware’s saved as a five-lettered file (i.e. the letters appended to the file are randomly generated, thus unique to each infection).
Research has revealed that Ryuk has a failsafe in case the file creation process failed – Ryuk’s executable is dropped in the same folder as the dropper. To differentiate itself from the dropper, the letter “V” is appended to the executable.
The next step would be to call the IsWow64Process function. This call determined whether to drop the X86 or X64 version of the executable. If IsWow64Process’s value is TRUE (i.e. machine’s running on a 64-bit architecture) the 64-bit ransomware binary is written to the disk. Before the dropper’s deleted, it will call up the ShellExecuteW function to ‘jumpstart’ the ransomware’s executable.
(2) Persistence, privilege escalation, and process enumeration
Persistence
As persistence is sine qua non condition for any malware, Ryuk taps into Windows’ Registry to ensure post-reboot execution. To achieve persistence, Ryuk will overwrite the Run registry key which controls what happens after the machine reboots. The malware will set a new value under the following key name: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\svchos
The instruction is “/v “svchos” /t REG_SZ/d “. This line allows the malware to run after every login.
Privilege escalation
Ryuk will obtain further permissions by modifying the SeDebugPrivilege argument of the AdjustTokenPrivileges () functions. SeDebugPrivilege allows Ryuk to move unhampered – modifying the value allows the user to adjust the memory of processes running under a different account and enforce debugging. Basically, this process lets the attack attach a debugger to any process or even to the kernel itself.
Process enumeration
In preparing for the code injection phase, Ryuk will ‘put together’ an array of structures. This array will be populated with entries pertaining to each processes’ identity. All the array will be assembled into a list, which Ryuk will go over and over again, trying to inject the code.
The evil code will be injected in between the spaces between the process’s address. Furthermore, the code injection mechanism will disregard any system process named “crsss.exe”, “lsaas.exe, “explorer.exe”, and anything that is currently being run under the NT AUTHORITY.
(3) Code injection, task-killing, imports, and backup deletion
Code Injection
In essence, Ryuk employs a rudimentary code injection technique. The malware targets the space in a process’ memory with VirtualAllocEx(). Ryuk then writes its own process to that specific allocated memory using the WriteProcessMemory () function.
To complete the process, Ryuk will finally create a separate thread in the process using the CreateRemoteThread () argument. This will ensure that Ryuk’s newly-created thread will run within the injected process.
As for the rest of the process, the malware will go through all of the machine’s running process and store its data in an array that contains the following info: ProcessType (0 for System, 1 for Custom, and 2 for Inherited), ProcessID, and ProcessName.
Once the array’s created, Ryuk will loop through the data and begin injecting the code. As I’ve mentioned, code injection will ignore the following systems processes: explorer.exe., crss.exe, and lsaas.exe.
Task-Killing
Ryuk ransomware will kill or put to sleep up to 180 system and AV-related services and up to 40 processes. The services and processes are killed using the net stop and taskkill /IM commands. The list is, most likely predefined. Some of the processes disabled by Ryuk:
- Excel.exe;
- Firefoxconfig.exe;
- Infopath.exe;
- Isqlplussvc.exe;
- Mspub.exe;
- Mydesktopservice.exe;
- Outlook.exe;
- Powerpnt.exe;
- Onenote.exe;
- Oracle.exe;
- Steam.exe;
- Syntcime.exe;
- Wordpard.exe;
- Winword.exe;
- Mbamtray.exe, etc.
Resource importation
For the pre-and post-encryption phases, Ryuk will dynamically load all the necessary functions. These functions are retrieved using the GetProcessAdress() and LoadLibraryA() arguments. Here is a shortlist of imports:
- advapi32.dll;
- kernel32.dll;
- ole32.dll;
- Shell32.dll;
- mpr.dll;
- Iphlpapi.dll.
Backup deletion
Before the encryption process begins, Ryuk will run a script to delete all backups and shadow copies. The script is located in the C:\User\Public folder and it is a batch executable. Once the backups and shadow copies are gone, the script will be deleted.
(4) File encryption
To obtain faster encryption rates, Ryuk’s creators use a multi-threaded symmetric block encryption scheme. As observed in the paper by Adi A. Maaita and Hamza A. Alsewadi, the multi-threaded approach in PRNG (pseudo-random number generator) increases the key generation complexity.
At the same time, PRGN implemented in AES and DES algorithms have shown a 36% increase in avalanche error computation over the traditional approach.
Ryuk will start by enumerating the soon-to-be-encrypted tiles. It does that using the FindFirstFileW() and FindNextFileW(), both arguments imported from the kernel32 Dynamic-link library. Each file name is slingshotted to another encryption thread.
Using the WindowsCrypto API for file encryption, Ryuk will commence creating encryption threads. An AES-256 key will be created for each thread. Encryption is done in a loop. All the files, with the exceptions of those containing the extensions .exe, .ini, .hrmlog, .lnk , and .dll, are encrypted in chucks (average chunk size is 1MB).
The next steps involved creating a 274-byte metadata block. This is placed at the end of each file. Keep in mind that the first six bytes of the metadata block will contain the keyword “HERMES”. The keyword would later be used for verification purposes – Ryuk will double-check at the end of the encryption process to see if all the files were encrypted. The “HERMES” tag appended to the end of the file means that the file has been encrypted. If not, Ryuk will iterate the process.
During the final part of the encryption process, Ryuk encrypts the newly-generated AES key with a public RSA key. The AES key will be appended to the end of the file. It’s later exported using the CryptExportKey() function, imported from the advapi32 Dynamic-link library.
The result is a 12-byte binary large object (B.L.O.B) plus another 256 bytes. This two-pointer will be the encrypted key. The encryption process ends with the implementation of the RSA in the executable. The key’s imported using the CryptImportKey() function, which can be found under the advapi32 Dynamic-link Library. This key will also be slingshotted to each thread.
Ryuk ransomware will also encrypt network shares. The process is very similar to the file encryption mechanism. To encrypt network shares, Ryuk starts by enumerating all network shares using the WNEtEnumResourceA() and WNetOpenEnumW() both arguments found under the mpr Dynamic-Link Library. When a resource is discovered, it will be appended to a list. All the items on the list will be encrypted using the same technique as in the case of machine files.
(5) Ransom
After the file encryption phase is completed, Ryuk will drop ransomware in the folder that contains the executable. According to VirusBulletin’s article on Ryuk, this ransomware strand drops two types of ransom notes – a (very) explicit one and a shorter version. Both versions of the ransom note are redacted below.
Ransom note #1
Gentlemen! Your business is at serious risk. There is a significant hole in the security system of your company.
We’ve easily penetrated your network. You should tank the Lord for being hacked by serious people, not some stupid schoolboys or dangerous punks. They can damage all your important data just for fun. Now your files are encrypted with the strongest military algorithms RSA4096 and AES-256. No one can help you to restore files without our special decoder. Photorec, RannoDecryptor, etc. repair tools are useless and can destroy your files irreversibly.
If you want to restore your files write to emails (contacts are at the bottom of the sheet) and attach 2-3 encrypted files (Less than 5MB each, non-archived and your files should not contain valuable information (Databases, backups, large excel sheets, etc.)). You will receive decrypted samples and our conditions how to get the decoder.
Please don’t forget to write the name of your company on the subject of your e-mail. You have to pay for decryption in Bitcoins. The final price depends on how fast you write to us. Every day of delay will cost you additional +0.5 BTC.
As soon as we get bitcoins you’ll get all your decrypted data back. Moreover, you will get instructions on how to close the hole in security and how to avoid such problems in the future + we will recommend special software that makes the most problems to hackers. <<how considerate of them!>>
Attention! One more time!
Do not rename the encrypted files. Do not try to decrypt your data using third party software.
P.S. Remember, we are not scammers.
We don’t need your files and your information. But after 2 week all your files and key will be deleted automatically. Just send a request immediately after infection. All data will be restored absolutely. Your warranty – decrypted samples.
Contact emails
(random)@tutanota.com or
(random)@protonmail.com
BTC wallet:
(wallet handle)
No system is safe.
Ransom note #2
(random)@protonmail.com
(random)@protonmail.com
<html
RYUK
Balance of shadow universe
An interesting aspect of the post-ransoming process. The same VirusBulletin article mentioned something about an IP blacklisting system. Introduced in the summer of 2020, this system allows Ryuk’s creators to ‘blackball’ the IP addresses belonging to former victims. It goes to show that even criminal masterminds have a shred of common human decency.
How Is Ryuk Ransomware Distributed
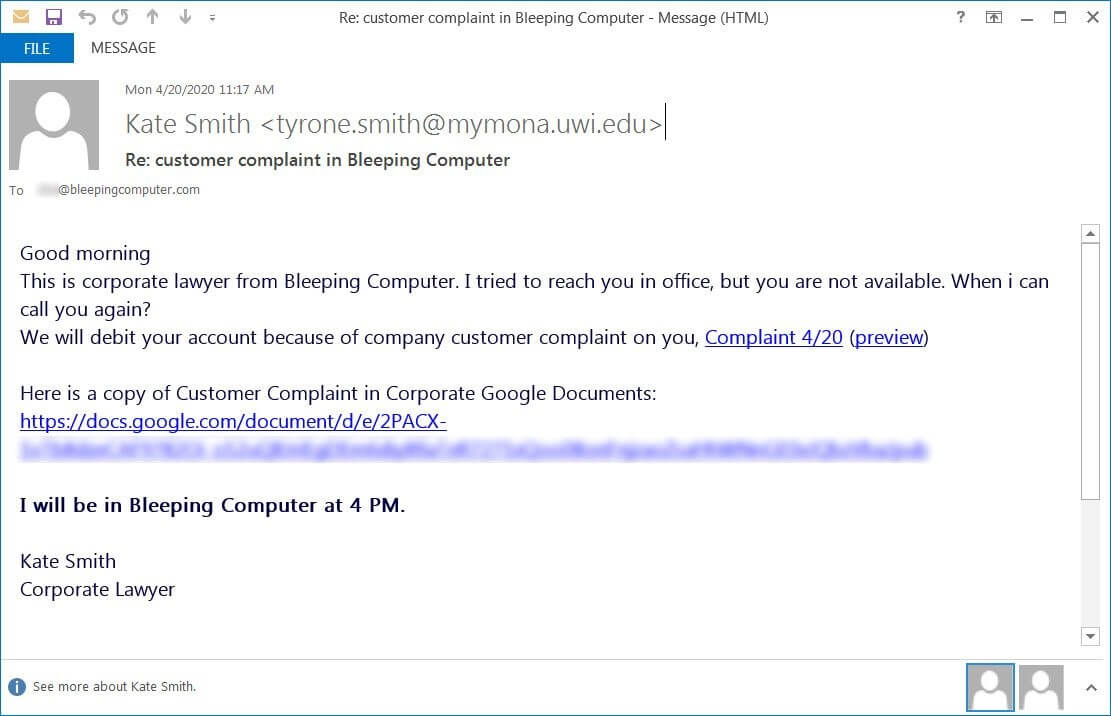
Just like Emotet and its ilk, Ryuk infects its victims via phishing emails preloaded with weaponized macro attachments. As observed in many instances (e.g. NVA hospitals, CDC COVID-19 phishing campaign, payment remittance phishing campaign, etc.), the ransomware operators employ social engineering techniques to trick the user into opening a seemingly benign email attachment (i.e. document, spreadsheet, pdf). Since the auto-run macro is turned off by default, and appending a mechanism to trigger the macro would alert the AV, Ryuk creators instead choose to include a flashy instructions banner.
At the same time, an MS Office alert would appear on the screen, informing the user that some of the document’s active content has been deactivated. Normally, we would be inclined to click on the Enable Content button in order to be granted full access to the document.
Even this step, which would otherwise be considered trivial, is social engineering. Let me give you an example – if someone emails you a .docx file, Office will open it in Protected View. To make any sort of modifications to the document, you are required to click on the ‘Enable Editing’ button.
Please commit this to memory – “Enable Content” = (malicious) macro, while “Enable Editing” is a normal part of the document editing process. Do not get these mixed up unless you’re willing to pay a hefty ransom to regain control over your endpoints and, presumably, your entire network. Bleeping Computer’s article on Ryuk overtaking the hospital industry provides some ‘wonderful’ examples of weaponized phishing emails.
Image courtesy of BleepingComputer
Hermes and Ryuk: Similarities & Differences
According to MITRE’s ATT&CK classification, Ryuk shares several code similarities with the Hermes, a ransomware family who claimed the 2017 attack on the Taiwanese Far Eastern International Bank. Both Ryuk and Hermes were detected in 2018. At that time, cybersecurity researchers erroneously claimed that they are one and the same.
The subsequent behavioral analysis revealed a filiation between Ryuk and Hermes, the former being a highly modified and improved version of the latter. WIZARD SPIDER is not the only APT that employs Ryuk to conduct clandestine operations.
FIN6, the APT responsible for the 2019 E-commerce platform compromise and the Anchor strike of 2020, has also used Ryuk for access token manipulation, network config scanning & enumeration, file & directory discovery, and more.
As I’ve mentioned, Ryuk’s creators share the same hunting philosophy with WIZARD SPIDER – going after bigger prey. Since its creation, Ryuk has been observed to go after restaurant chains, public institutions, news outlets, and technology vendors. I will highlight the most important Ryuk incidents at a later time.
Concerning code similarities, Itay Cohen and Ben Herzog of Checkpoint have pointed out that Ryuk’s and Hermes’ similarities become highly visible when looking at how both generate and check the encryption markers (i.e. these markers are used to ascertain if a file was encrypted or not prior to the session). I will be covering this in the upcoming section that deals with the behavior, attack patterns, obfuscation, and ransom notes.
While there are similarities between the two, let us not forget that Ryuk has been specifically engineered to achieve better results compared to Hermes. Certainly, they’re both ‘big-game hunters’, and, in some cases, those who hunt together reap the benefits together. For instance, Hermes can be used as bait, while Ryuk stalks the prey, waiting for the right moment to make the kill.
It’s a hypothesis – so far, Ryuk and Hermes haven’t been seen keeping each other company. Still, Ryuk keeps some interesting companions. Remember GBHackers on Security’s kill-chain, with Emotet and TrickBot paving the way for Ryuk? In the curious case of the October 2017 Far Eastern International Bank attack, Hermes was used as part of a diversionary stratagem intended to make the victims lower their guard so other malware can zero in and make the kill.
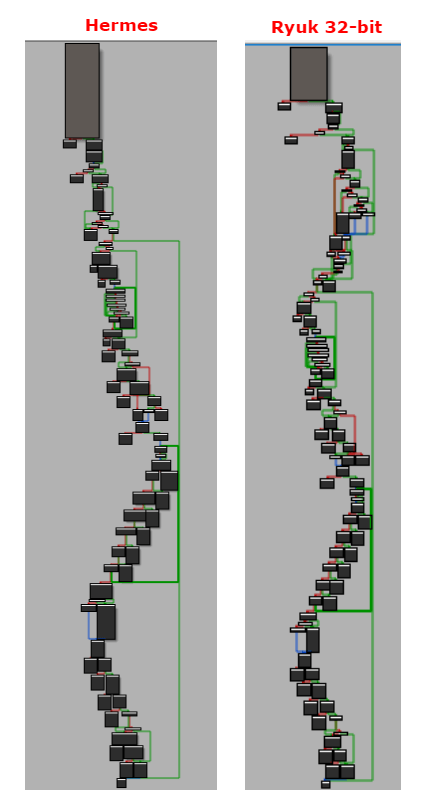
Tautology, filiation, or the filiation of tautology? All and anon – Ryuk shares many similarities with HERMES: the same call flows, same encryption algorithms (AES-256 and RSA-2048), using binary large objects to store keys, and encrypting shared network. Checkpoint researchers Cohen & Herzog remarked that Ryuk 32-bit’s encryption marker is the same as Hermes’. The long-winded list of similarities ends with folder whitelisting (i.e. both Ryuk and Hermes will skip the encryption process for Recycle Bin, anything related to Microsoft products, and Internet Explorer). Below you’ll find the head-to-head comparison between the call flows of Ryuk and Hermes.
Image courtesy of HHS Security
Protecting Your Endpoints Against Ryuk Ransomware
Due to the tenacity of the new Ryuk variant, prevention is a more effective tool than mitigation or remediation once Ryuk takes hold in a system
- The new variant also lacks any exclusion mechanisms, such as a Mutual Exclusion Objection (MUTEX), to prevent multiple Ryuk processes from running on a single machine
- Reinfection of the same device is possible once the initial infection is cleared
Because Ryuk infections most commonly begin with the deployment of a form of “dropper” malware as a foothold in the victim’s machine, we include these mitigations from CISA’s Alert (AA20-302A) on Ransomware Activity Targeting the Healthcare and Public Health Sector:
- Patch operating systems, software, and firmware as soon as manufacturers release updates;
- Check configurations for every operating system version for HPH organization-owned assets to prevent issues from arising that local users are unable to fix due to having local administration disabled;
- Regularly change passwords to network systems and accounts and avoid reusing passwords for different accounts;
- Use multi-factor authentication where possible;
- Disable unused remote access/Remote Desktop Protocol (RDP) ports and monitor remote access/RDP logs;
- Implement application and remote access to only allow systems to execute programs known and permitted by the established security policy;
- Audit user accounts with administrative privileges and configure access controls with POLP in mind;
- Audit logs to ensure new accounts are legitimate;
- Scan for open or listening ports, and mediate those that are not needed;
- Identify critical assets such as patient database servers, medical records, and telehealth and telework infrastructure; create backups of these systems and house the backups offline from the network;
- Implement network segmentation. Sensitive data should not reside on the same server and network segment as the email environment;
- Set antivirus and anti-malware solutions to automatically update; conduct regular scans;
- Regularly back up data and air gaps, and password-protect backup copies offline;
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, secure location;
- Focus on end-user awareness and training about ransomware and phishing;
- Ensure that employees know who to contact when they see suspicious activity or when they believe they have been a victim of a cyberattack. This will ensure that the properly established mitigation strategy can be employed quickly and efficiently.
In dealing with the novel Ryuk ransomware, Heimdal™ Security also recommends the following:
- Access Governance to limit access to sensitive network-shared resources. Remember that Ryuk also encrypts everything that’s shared over the network. Deploying an IAM will severely decrease the chances of over-the-network encryption and lateral movement.
- Cloud backups. Ryuk removes backups and shadow copies stored on the machine. Regularly backing up to your cloud provider and having a disaster recovery plan in place makes it easier to retrieve your data in case of ransomware encryption.
- Perimeter protection. A perimeter solution decreases the likelihood of Ryuk landing on your machines. Heimdal™ Threat Prevention Network uses DarkLayer Guard™, the company’s proprietary DNS traffic-filtering engine, to ensure your company’s assets, resources, and devices are protected around the clock.
- Email security. Email security products are capable of identifying malicious attachments. Heimdal™ Email Fraud Prevention analyzes over 100 attack vectors to determine if an email is legitimate or fake.
- Cybersecurity education. We believe that (continuous) cybersecurity education is the right way to prevent such occurrences. In this case, my advice would be to stay away from suspicious emails. If you do encounter one, refrain from opening attachments or clicking on links. Check and double-check an email’s authenticity, especially if the email instructs you to conduct any kind of money-related operations.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Conclusions
The cases I’ve highlighted throughout the article prove that Ryuk’s creators have the tenacity, the drive, and, why not, the audacity to strike anywhere and everywhere. As to what happens after the post-encryption process, my only advice to you is how head on straight to the authorities.
Do not pay the ransom and under no circumstance should you attempt to restore the data from backups before the ransomware is purged from your machines and network. Paying the ransom will only encourage the hackers to intensify their efforts, attacking even bigger targets. Ryuk borrowed and refined many infectious and encryption mechanisms from Hermes. However, they’re not on the same, as proven by the technical analysis. The only way to protect yourself against Ryuk and its ilk is to improve your cyber-protection and practice good online hygiene.
Last edited by Cezarina Chirica on October 1st, 2021


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security