Contents:
Cyberattacks have become a part of our reality, but have you ever wondered what might happen if your company gets targeted? You probably imagine that you would lose some money and a great deal of time, maybe fire an employee or too, lose a few clients and have your reputation tainted, or eventually even deal with a lawsuit. If these aren’t serious and bad enough for you to take cybersecurity seriously, let me tell you this: cyberattacks have also turned deadly.
What Is REvil Ransomware?
Discovered in April 2019, REvil/Sodinokibi ransomware (AKA Sodin) is a highly evasive and upgraded ransomware that encrypts files and deletes the ransom request message after infection. The message informs the victim that a bitcoin ransom must be paid and that if the ransom is not paid on time, the demand will double.
REvil is a perfect example of Ransomware-as-a-Service, a cybercrime that involves two groups teaming up for the hack: the code authors who develop the ransomware and the affiliates that spread it and collect the ransom. This aspect makes Sodinokibi ransomware dangerous for companies of all sizes. Also known as Sodin or REvil, Sodinokibi shortly became the 4th most distributed ransomware in the world, targeting mostly American and European companies.
As reported by SecurityBoulevard, REvil/Sodinokibi is apparently the successor to the GandCrab strain. GandCrab is thought to be responsible for 40% of all ransomware infections worldwide, according to security specialists. It has amassed a ransom of around $2 billion. The malware’s designers then declared the malware’s retirement early this year.
REvil/Sodinokibi Operating Mode
Most of the time, Sodinokibi ransomware is spread by brute-force attacks and server exploits, but it’s not uncommon either to get infected through malicious links or phishing. Exploiting an Oracle WebLogic vulnerability and often bypassing antivirus software, REvil/Sodinokibi downloads a .zip file with the ransom code, written in JavaScript, moves through the infected network, and encrypts files, appending a random extension to them. Particularly dangerous is the fact that REvil/Sodinokibi may reinstall itself as long as the original ransom code is not deleted.
When the encryption is complete, the ransom message is frequently the first thing users of infected systems notice. The ransom instructions can also be shown on the desktop.
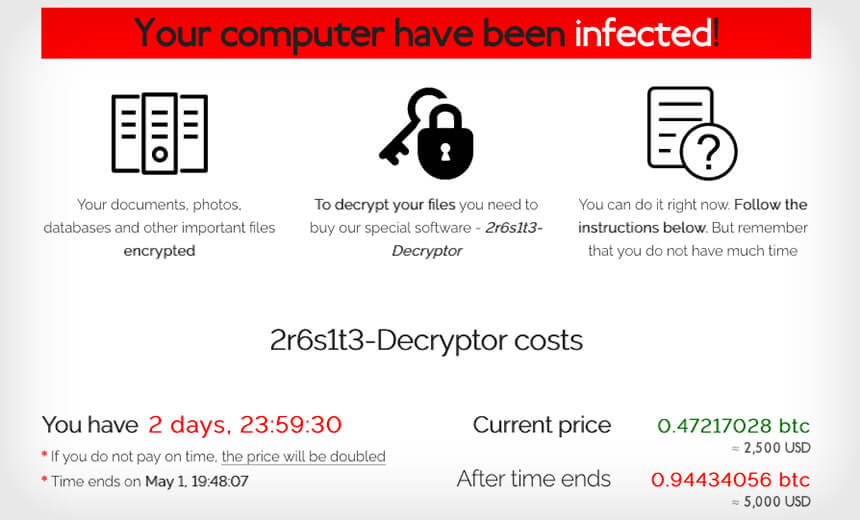
Image Source: Bank Info Security
After encrypting the data on the target machine, the virus attempts to communicate with a C2 server. It iterates over a list of domains set in the previously decoded configuration file to construct the URL for the C2.
The compromised systems are operational without backups, a rollback system, or other techniques to retrieve the encrypted files, but all of the vital information stored on them will be unavailable.
Using a combination of hard-coded and randomly generated strings, the virus generates numerous different URLs. REvil/Sodinokibi and GandCrab generate random URLs in similar ways, according to a recent Tesorion report, which increases suspicions of a possible joint author. The malware then sends encrypted computer data to each of the domains, including users, machine names, domain names, machine languages, operating system types, and CPU architecture.
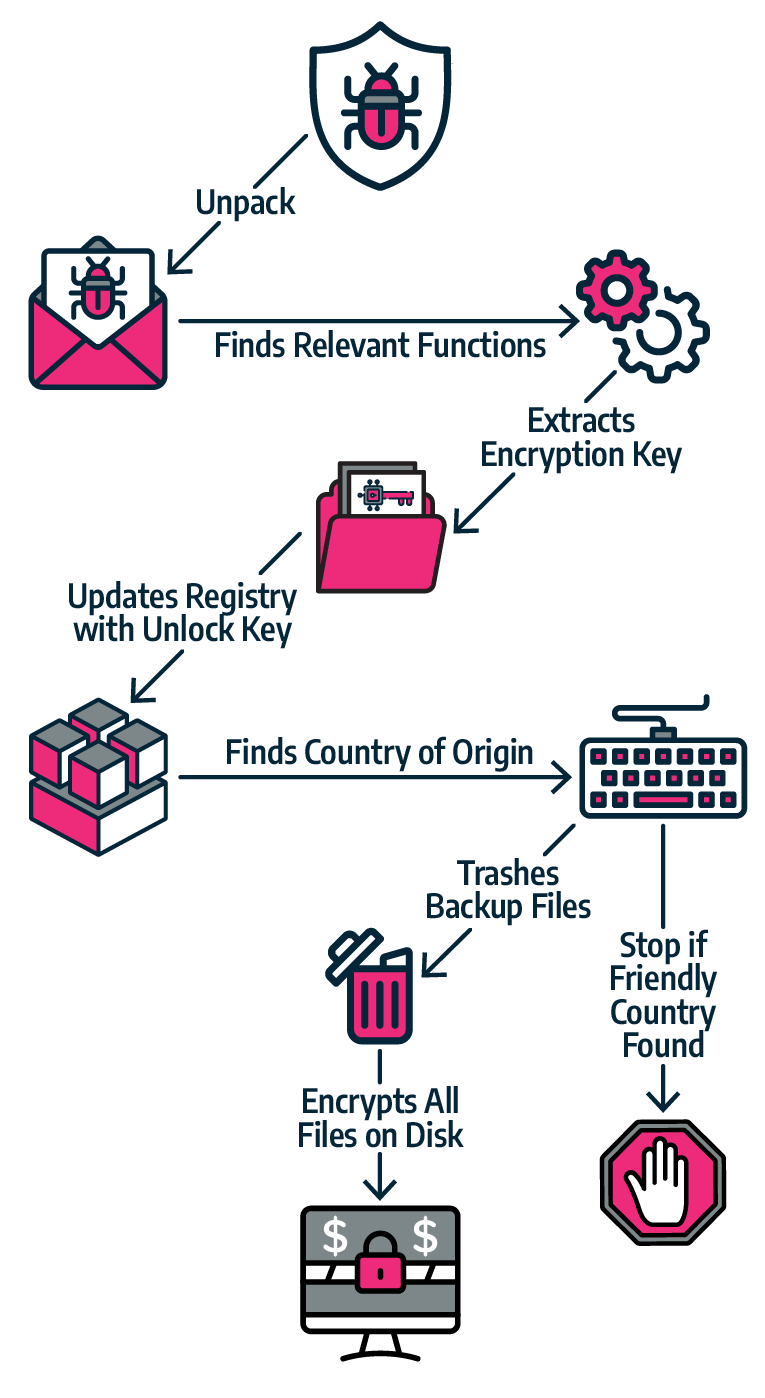
Image Source: VIRSEC
When a user enters the key on the ransom note, a page displays the sum in bitcoin they must pay to get their files back.
Based on findings detailed in the Tesorion report, such as similarities in the language and countries whitelist (Russian and Syrian Arabic-speaking countries), the spiteful targeting of an Ahnlab product for process injection, and the similarities in the URL-generation routine, this analysis supports the suspicion that the operators behind the REvil/Sodinokibi ransomware are the same allegedly retired threat actors who created the GandCrab ransomware.
Does REvil/Sodinokibi Ransomware Steal Data?
Stealing data from ransomware victims before encrypting devices and using the stolen files as leverage to get paid is a tactic that the Maze Ransomware operators have started to bring into force. Since then, REvil/Sodinokibi, DoppelPaymer, and Nemty followed their lead. According to BleepingComputer, until March 2020, the Sodinokibi ransomware operators had published over 12 GB of stolen data “allegedly belonging to a company named Brooks International”. Moreover, “other hackers and criminals have started to distribute and sell this data on hacker forums”, as you can see in the image below “where a member is selling a link to the stolen data for 8 credits, which is worth approximately 2 Euros”:
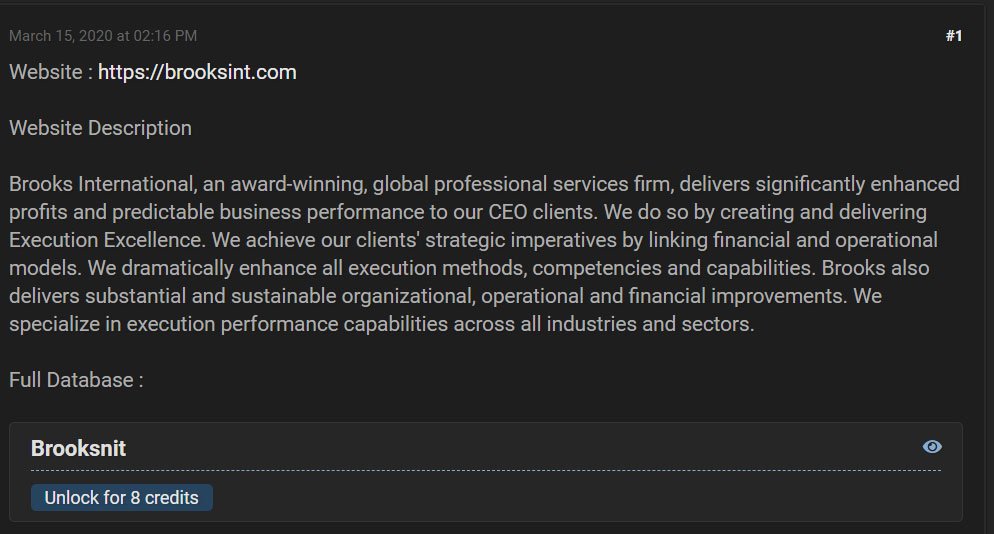
Source: BleepingComputer
REvil/Sodinokibi Ransomware Attacks
2019
May
Among the first victims of REvil/Sodinokibi ransomware were two Florida states. SecurityBoulevard describes the attacks from May 2019:
The City of Riviera Beach, Florida, agreed to pay $600,000 for the decryption key to unlock their files. Weeks later, the city of Lake City, Florida, relented to a $450,000 ransom payment as well. Each of these cities faced service disruption after being infected. Some of these services included email, phones, police records, the public works department, the library, 911 emergency, and general offices. Because these towns do not have the personnel or knowledge base to remediate these attacks, paying the ransom seemed to be the best bet.
These attacks were followed by another impressive one, against Texas:
In a highly coordinated attack, hackers were able to bring down 22 separate municipalities, including the cities of Borger and Keene. The perpetrators of the attack then asked for a collective $2.5 million to release everyone caught in the net. Fortunately, the infected Texas municipalities received state-issued resources from Texas A&M University and the Texas Military Department.
August
In August 2019, Sodinokibi operators targeted PerCSoft, a company specialized in backup services for UK dental offices: more than 400 dental offices were affected during the attack. PerCSoft claimed that no data was accessed during the attack they presented as a virus infection, but it would appear that “a private Facebook group of IT professionals serving the dental industry shared […] screenshots that hint that the victim firm has paid the ransom to decrypt the data.” The most notable example of a REvil/Sodinokibi ransomware attack is probably the one on Travelex, a famous currency exchange company. On this subject, SecurityBoulevard notes:
An unnamed source within Travelex disclosed to The Wall Street Journal (WSJ) that the company paid $2.3 million in Bitcoin in an effort to restore functionality to its systems following a ransomware attack. Travelex was hit with a ransomware attack on New Year’s Eve, and it took a couple of weeks to restore some of its basic services, with the consumer side having to wait until February. The breadth of the attack was staggering, as the hackers infiltrated the company’s infrastructure six months before attacking with ransomware. Hackers didn’t just linger around the network. They used the time to exfiltrate valuable information, 5GB in total, which they then used to blackmail the company after deploying ransomware. […] In the Travelex attack, the hackers used Sodinokibi ransomware and an unpatched critical vulnerability in Pulse Secure VPN servers. Companies were warned about this particular VPN vulnerability, but some companies didn’t update their systems in time.
2020
The threat actor is notorious for stealing nearly one terabyte of data from the legal firm Grubman Shire Meiselas & Sacks and demanding a ransom not to disclose it as part of their activities.
The ransom demand was initially established at $21 million, but when REvil discovered files relating to Donald Trump, it was raised to $42 million. The GSMS attack resulted in the loss of personal information belonging to Lady Gaga, Madonna, Bruce Springsteen, and Elton John. GSMS declined to pay the ransom, as advised by the FBI. Some of the stolen data has been recovered by the firm using privately hired individuals; nevertheless, much of the stolen data is still at large and available for online purchase.
2021
March
In March 2021, the UK multi-academy trust Harris Federation was the target of a REvil ransomware attack. Following the hack, Harris Federation disabled the devices given to pupils as a precaution, temporarily suspending email and telephone systems. As a result, the federation’s IT services were down for many weeks, affecting nearly 40,000 students.
Acer, the 6th-largest PC vendor by unit sales in the world, became the victim of a REvil ransomware attack the same month. The requested ransom was at the time the largest one to date, REvil asking for $50,000,000. The threat actors published images of allegedly stolen documents, like financial spreadsheets, bank documents, and internal communications.
April
In April, the ransomware gang publicly claimed that it had hacked Quanta Computer, a Taiwan-based third-party supplier that partners up with several large U.S. tech companies, including Apple, Dell, Hewlett-Packard, and Blackberry. As one of the largest laptop manufacturers in the world, Quanta assembles Apple’s products based on designs supplied by the Cupertino company. The gang has demanded that Apple pay for the stolen documents “by May 1st,” or else “more and more files will be added [to the leak site] every day.”
May
One month later, JBS Foods, the world’s largest meatpacking organization, was forced to shut down production at several sites all over the world following a cyberattack. The attack affected multiple JBS production facilities globally over the weekend, including those from the United States, Australia, and Canada. Following the incident, the FBI released a statement, attributing the attack to REvil Ransomware operation.
June
After REvil threatened to reveal humiliating facts about its wealthy chief executive, Michael Polsky, US-based renewable energy company Invenergy stated back in June that it had indeed been attacked but did “not intend to pay any ransom.”
July
REvil encrypted more than 1,000,000 systems in one of the most massive cyberattacks we’ve seen lately – the Kaseya Ransomware Attack. The threat actors decided that the price for decrypting all systems would be $70 million in Bitcoin in exchange for the tool that allows all affected businesses to recover their files. The attackers used the initial breach into the service provider in order to then hack as many of its customers as possible. The Kaseya hack resulted in the infection of hundreds of businesses with Revil Ransomware by the Sodinokibi gang.
The Coop supermarket chain had to close 500 of its stores after REvil had targeted managed service providers (MSPs) and their customers in the massive supply-chain attack in which they exploited a vulnerability of Kaseya VSA.
Lather that same month, security researchers reported that the threat actors’ payment site, the public site, the ‘helpdesk’ chat, and their negotiation portal are offline. This came after US President Joe Biden had asked Russian President Vladimir Putin during a phone call to act on the attacks against American organizations and infrastructure, adding that the U.S. will take “any necessary action” to protect itself against future attacks. Some security experts believe the gang may have shut down their own websites due to internal disagreements or fear related to increased law enforcement attention.
September
The Tor payment/negotiation and data leak sites reopened and became available on September 7th, allowing people to log in to the Tor payment site to negotiate with the ransomware group. Prior victims’ timers were reset, making it appear as if their ransom demands were left as they were at the time the ransomware gang stopped down in July.
According to VirusTotal, the new attacks were discovered on September 9th, when someone uploaded a new REvil ransomware sample that was generated on September 4th.
On September 22nd, researchers discovered a backdoor in the REvil software that allowed the original gang members to double-chat and defraud their affiliates of ransomware money. Affiliates who were duped allegedly submitted their claims on a “Hacker’s Court,” weakening affiliate trust in REvil. The backdoor was apparently disabled from newer versions of the REvil virus.
October
On October 18th, REvil ransomware had been taken down once more following a multi-country operation. Law enforcement and intelligence cyber specialists were able to penetrate REvil’s computer network architecture, gaining control of at least some of its servers. The REvil ransomware group appears to have recovered the infrastructure from backups, assuming that they had not been compromised. A faulty assumption, which is paradoxical given that malware makers make it necessary to keep clean backups.
How to Stay Safe from REvil/Sodinokibi Ransomware?
As Fernando Ruiz, head of operations at Europol’s European Cybercrime Center says, “Criminals behind ransomware attacks are adapting their attack vectors, they’re more aggressive than in the past – they’re not only encrypting the files, they’re also exfiltrating data and making it available”. In order to defend your company from such threats, you need to approach the matter from various angles:

The first one is education-oriented:
BACK UP YOUR DATA!
This might seem tech-related, but we think of it more like common knowledge: how could you not have backups for your essential data? You should store it both online and offline and take time to test your ability to revert to backups during a potential incident.
Train your employees!
User awareness is one of the most reliable methods to prevent an attack, so make sure you take the time to educate your employees and advise them to report to the security teams as soon as they notice something unusual. They should be aware of phishing techniques and other social engineering tactics cybercriminals may use to get into your organization.
The second one – technology-related:
Keep your systems up to date.
Updates help you close security holes that many viruses use to enter your computers. Since dealing with patches is a resource and time-consuming task, the best option for you to stay safe from REvil/Sodinokibi and other ransomware would be to deploy an automated patching solution.
The Heimdal™ Patch & Asset Management efficiently addresses this problem by applying Windows and third-party updates in the background as soon as they are released.
Protect your email.
Many hackers rely on you not paying attention to what your emails actually contain and hope you’ll get infected by opening a malicious attachment or clicking on a fake link. Try to always hover over the links you want to access to make sure they lead where they’re supposed to lead and never open attachments or access links received from unknown, unexpected, or unwanted sources. You should also think about an email protection solution, like our Heimdal™ Email Security.
Deploy multi-layered Cybersecurity.
Good antivirus software is essential for any company’s cybersecurity but to be as protected as you can, we recommend you use a multi-layered security approach. Heimdal™’s EDR Software uses multi-layered AI-powered protection that brings together threat hunting, prevention, and mitigation in one package, for the best endpoint protection.
Wrapping Up
Since there is no free decryption tool or a foolproof method that can completely decrypt REvil/Sodinokibi ransomware encrypted files (and paying the ransom to get your data back from the hackers shouldn’t be an option), prevention remains the most effective approach.
Heimdal™ Security offers the latest in cybersecurity protection against advanced cyberattacks. Our security solutions are designed to work with your company’s needs and budget.
If you enjoyed this article, make sure you follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything cybersecurity.
Heimdal™ Ransomware Encryption Protection


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











