Contents:
With cyberattacks seemingly increasing at a high rate, companies have to make sure their details and information are secured and safe from threat actors creeping around.
Today, we will talk about a popular approach used by companies to assess their cybersecurity posture effectively and securely, and gather information on attackers, red team vs. blue team.
What Is Red Team vs. Blue Team?
Red team/blue team is a drill based on military training exercises, that pits two teams of highly skilled cybersecurity professionals against one another. The red team attempts to compromise the environment using real-world adversary tactics, while the blue team is made up of incident responders who work within the security unit to recognize, assess, and deal with intrusions.
Red team/blue team simulations are crucial in protecting companies from a variety of attacks launched by today’s highly skilled threat actors. Through a red team versus blue team approach to cybersecurity, companies can:
- Find vulnerabilities;
- Identify areas of improvement in defensive incident response processes across every phase of the kill chain;
- Increase the organization’s practical knowledge on how to recognize and stop a targeted attack;
- Create response and remediation procedures to restore the environment to its original condition;
- Raise security awareness among staff members.
What Is Red Team?
A red team consists of security experts, usually ethical hackers, who simulate how a possible threat actor would attack a company’s cybersecurity defense. The red team has the objective to exploit, compromise, and circumvent the blue team’s defense so that the company employing them can evaluate its prevention, detection, and responding capabilities.
Red Team Responsibilities
If you want to be a red team specialist, the role’s responsibilities are the following:
- Determine a target, and do reconnaissance;
- Exploit weaknesses;
- Gather information through social engineering, system hacking, or physical entry into the location.
Red Team Activities
Being on a red team requires you to think like a hacker in order to compromise an organization’s security (with their permission). Red team activities frequently include:
- Social engineering;
- Penetration testing;
- Card cloning;
- Intercepting communications;
- Marking recommendations to the blue team on how to improve security.
Red Team Skills
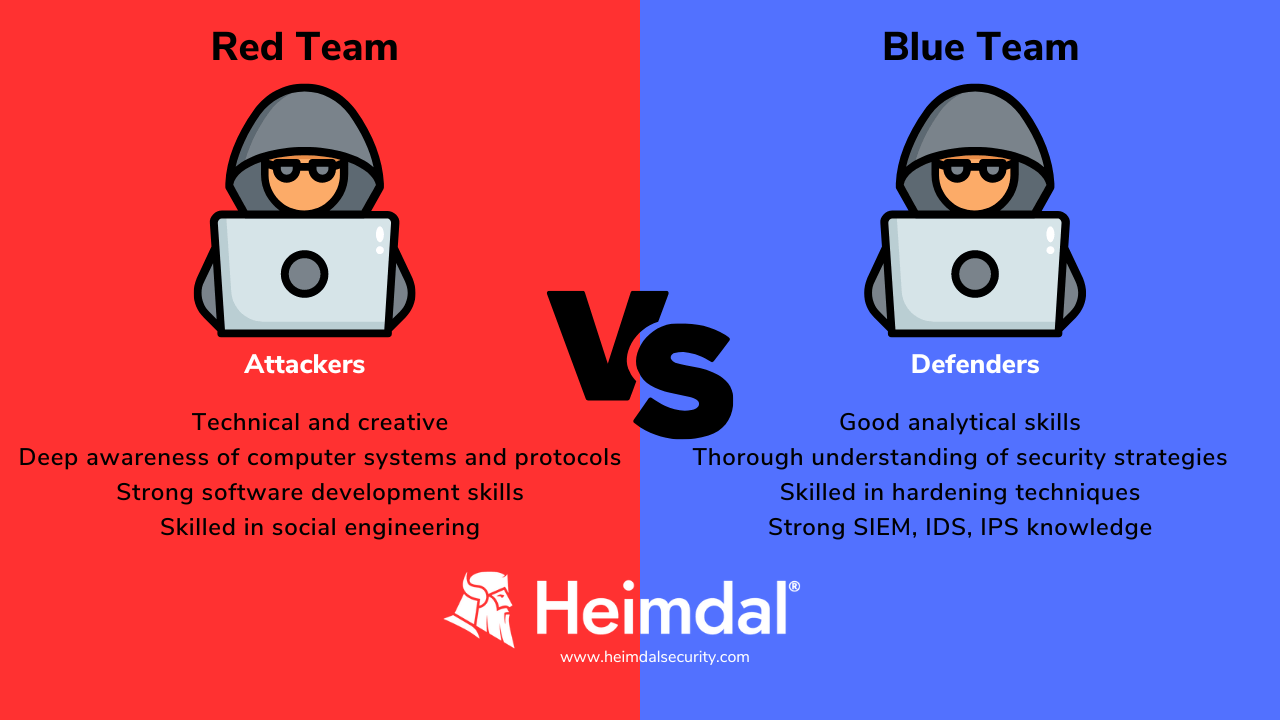
To successfully access the network and move discreetly across the environment, a red team member must be cunning in nature and adopt the mindset of a knowledgeable enemy. The ideal red team member must be both technical and creative, and should have:
- A deep awareness of computer systems and protocols, techniques, tools, and safeguards;
- Strong software development skills to create specialized tools to get beyond standard security measures and procedures;
- Social engineering skills to manipulate others into sharing information or credentials;
- Experience in penetration testing.
What Is Blue Team?
A blue team consists of incident response experts, which are responsible for defending an enterprise’s use of information systems by maintaining its security posture against attackers. If the red team is playing offense, then the blue team is the defense they have to pass in order to get to the organization’s critical assets.
Blue Team Responsibilities
The main responsibility of the blue team is to make the system as strong as they can, so that threat actors cannot breach in and wreak havoc. The blue team’s responsibilities include:
- Protecting the organization’s systems from attackers;
- Carry out risk assessments;
- Analyse network traffic;
- Gather data;
- Keep the security policies up to date.
Blue Team Activities
Your responsibility as a blue team member is to assess the organization’s current security posture and act to remediate any gaps or vulnerabilities. Being on the blue team also entails keeping an eye out for breaches and being prepared to act when they do. A few of these tasks are:
- Installing and configuring firewalls and endpoint security software;
- DNS audits;
- Digital footprint analysis;
- Using least-privilege access;
- Monitoring network activity.
Blue Team Skills
Being technically focused on defense, much of the job of a blue team member is proactive in nature. This team’s goal is to spot hazards and threats and eliminate them before they cause harm to the organization. Even the most qualified cybersecurity experts, however, find it virtually impossible to accomplish this due to the sophistication of attacks and adversaries.
Common skills for a member of the blue team are:
- Analytical skills to identify the most dangerous threats and prioritize responses accordingly;
- A thorough understanding of the organization’s security strategy;
- Hardening techniques necessary to reduce the attack surface;
- Knowledge of how to use packet sniffers, security and information management (SIEM) software, intrusion detection systems (IDS), and intrusion prevention systems (IPS)
How to Set Up a Red Team vs. Blue Team Exercise
Before setting up the exercise, it’s important to understand its objective. The goal of the exercise isn’t to only pinpoint security issues, but also to collect data that will aid in solving the issues identified.
It’s an opportunity to educate staff members about the value of being cautious and the necessity of incorporating cybersecurity into the development of goods and services. To plan an efficient red team/blue team exercise, you should take into consideration following steps:
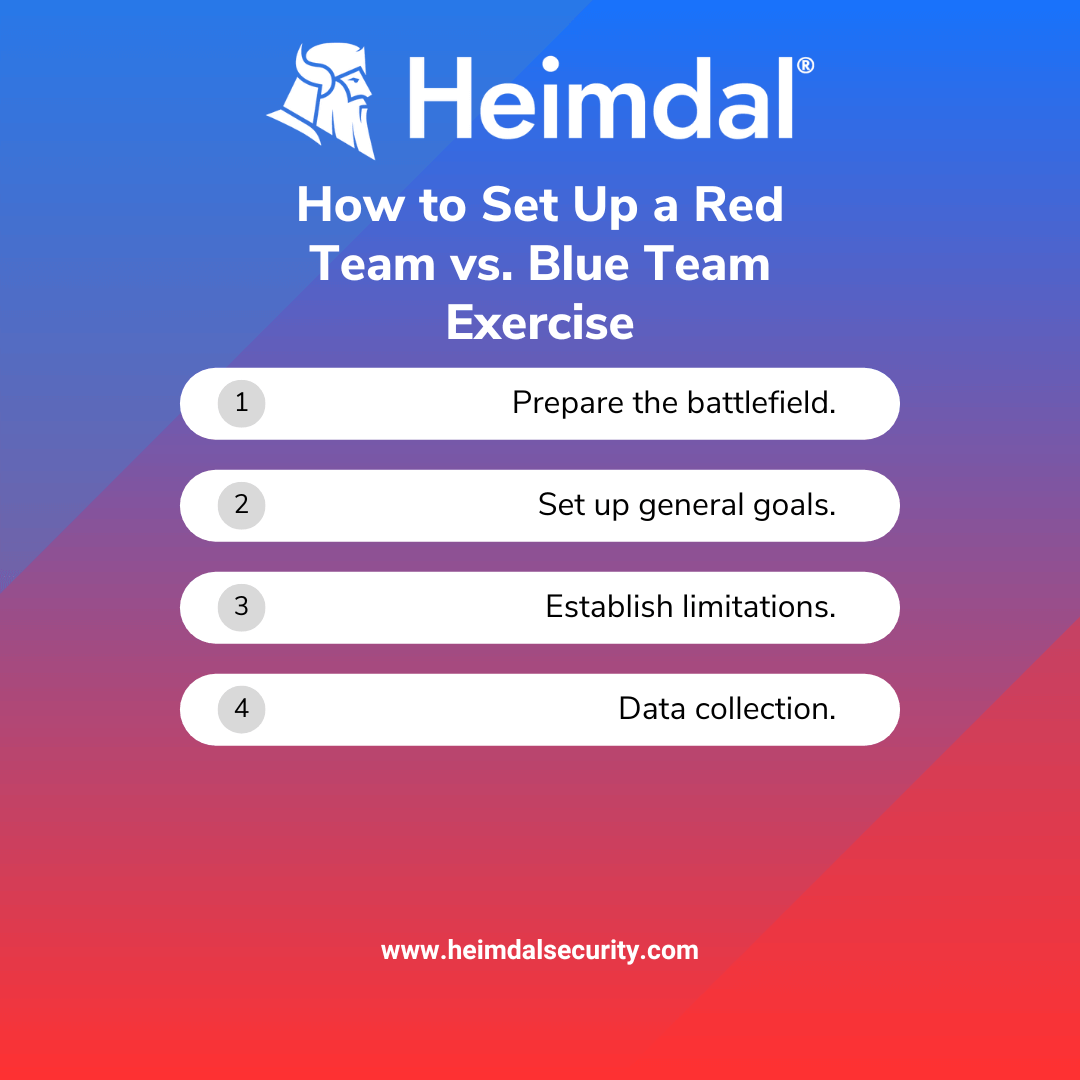
Step 1: Prepare the Battlefield
Preparation is key, so gathering both teams together and brainstorming on possible scenarios is recommended. It will give the teams a clear idea about what tactics should be employed to gather the best results.
Step 2: Set Up General Goals
An essential step before starting the exercise is to establish the goals you are trying to accomplish. Although increasing security is the ultimate objective of the exercise, it could be beneficial to focus on just two or three key issues.
Step 3: Establish Limitations
Setting boundaries before the game begins could be beneficial. Is there anything that won’t be allowed? How far will the red team go? How accurate can they make their simulations? Establishing fewer restrictions is usually the way to go since it mimics more realistically an actual cyberattack, but maybe your company has specific issues you want to address or scenarios you want to experiment with, so make sure both teams got everything right before starting.
Step 4: Data Collection
Decide how the exercise’s data will be gathered and shared. It is crucial to complete the task and guarantee that the organization profits from the entire experience. It is essential to plan how the data will be obtained and how the reports will be distributed.
How Can Heimdal® Help Your Business?
A threat actor’s way into your company’s systems is usually a vulnerability left exposed or unpatched. Although seeming to sound like a minor problem, you won’t believe how many big companies had sensitive information leaked, or whole processes interrupted due to a single vulnerability left unpatched on a server, or even an employee’s work machine.
Depending on the number of machines connected to your enterprise’s network, patching becomes increasingly challenging and time-consuming for your IT admins. Fortunately, there are solutions such as Heimdal®’s Patch & Asset Management solution that can fully automate the patching process, so that your business will always be safe from threat actors trying to exploit vulnerabilities.
Heimdal®’s Patch & Asset Management solution is a fully automated, customizable, and on-the-fly patching solution that allows you to deploy and patch any Linux, Microsoft, or 3rd party app from anywhere in the world, whenever you like it, with complete visibility and granular control over your entire software inventory.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...
Conclusion
In the end, we can see why the red team vs. blue team approach is crucial in cybersecurity for identifying vulnerabilities and defending against attacks. The collaboration between these two teams is essential for continuously improving security measures and ensuring the resilience of systems. By leveraging the insights gained from red teaming and the skills of blue teaming, organizations can effectively mitigate risks and stay ahead of potential threats.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










