Contents:
Ransomware has come to be a customary instrument in the arsenal of cybercriminals who routinely attack individuals and organizations. Under such circumstances, their victims experience financial damage either by owning up to large ransomware payouts or by bearing the price of recovering from attacks.
There are times when ransomware victims can decrypt their files with free ransomware decryption tools but sadly, there isn’t a decryptor available for all the ransomware strains out there. This sometimes leads to companies paying the ransom, being desperate to get their business back up and running.
Top 5 Ransomware Payouts of All Time
Unfortunately, ransom demands can sometimes be in the millions of dollars. Below, you will find the most significant confirmed ransomware payouts of all time to illustrate just how costly falling victim to this kind of attack can be.
Keep in mind that some rumored ransomware payouts were a lot higher than what you will find on this list. Examples include Garmin paying $10 million in 2020, or CNA Financial giving into a whopping $40 million ransom following an attack in 2021. However, as the companies themselves have not verified these rumors, I will focus on confirmed transactions only in this article.
#5 University of California San Francisco (UCSF)
AMOUNT PAID: $1.14 MILLION
RANSOMWARE: NETWALKER
The University of California at San Francisco paid a ransom demand of $1.14 million to recover files encrypted by ransomware. The institution was attacked on June 1, when ransomware was discovered in the systems of the UCSF School of Medicine. The IT staff attempted to isolate the infection, which prevented the malware from extending to the core UCSF network and producing additional damage.
The school said the attack did not affect their patient care delivery operations, overall campus network, or COVID-19 work. However, the UCSF servers used by the school of medicine were encrypted. The Netwalker ransomware gang was believed to be responsible for the attack.
The BBC closely followed the Dark Web negotiation made between Netwalker and the UCSF. The malicious hackers first asked for a ransom of $3 million, which was disputed by the UCSF with a $780,000 proposal.
The university’s offer was declined and negotiations eventually led to the agreed figure of $1,140,895, paid in Bitcoin. The threat actors offered a decryption key and said they would erase data stolen from the servers. However, it is uncertain whether the attackers kept their promise or not.
#4 Travelex
AMOUNT PAID: $2.3 MILLION
RANSOMWARE: SODINOKIBI
Following a ransomware attack on New Year’s Eve, Travelex, a London-based foreign currency exchange that does business in 26 countries, paid $2.3 million to regain access to its records. The event crippled the company for weeks. Travelex’s payment and the sum were not announced until April 2020, but the company reported the ransomware attack shortly after it happened.
The Sodinokibi gang claimed to have accessed and then copied and encrypted 5 GB of data from Travelex’s network. Initially, the cybercriminals allegedly requested $6 million to decrypt the information.
Travelex agreed to pay a $2.3 million ransom after several weeks of negotiation and consulting its partners and associates. Sources said they confirmed the payment in an online conversation with members of the Sodinokibi group.
#3 Brenntag
AMOUNT PAID: $4.4 MILLION
RANSOMWARE: DARKSIDE
In May of 2021, the North American division of chemical distributor Brenntag was the victim of a DarkSide ransomware attack. Even though the damage was limited to just one segment of the company, a total of 150GB of data was stolen as a result of the incident.
The incident caused a huge disruption in Brenntag’s activity. The distributor later came out and declared that the stolen data consisted of sensitive details such as dates of birth, driver’s license numbers, medical records, and social security numbers of its employees.
DarkSide, the malicious actor behind the attack, initially demanded 133.65 bitcoin in ransom, which amounted to roughly $7.5 million. This would have made it by far the largest confirmed ransomware payout in the history of the Internet.
However, after negotiating with the hackers for several days, Brenntag lowered the price to $4.4 million, that were subsequently paid in Bitcoin. Unfortunately, they weren’t the only company to pay such a price to the DarkSide gang in exchange for data decryption.
#2 Colonial Pipeline
AMOUNT PAID: $4.4 MILLION
RANSOMWARE: DARKSIDE
While DarkSide was busy attacking Brenntag, the cybercriminal group was also involved in the Colonial Pipeline ransomware attack, one of the most crippling cybersecurity incidents of 2021. Hackers targeted the company’s business network, including its billing system. This meant that staff had no means to track fuel distribution across the country and invoice customers.
In addition to this, the company had to take its operational technology network offline to prevent ransomware from spreading further into the network. This infrastructure controlled the entire pipeline, which meant a widespread service disruption across North America.
As the largest fuel pipeline operator in the United States of America, the Colonial Pipeline carries refined gasoline and jet fuel across a long route spanning from Texas to New York. In exchange for data decryption, operators asked for the same sum as in the Brenntag case, $4.4 million.
However, after the Colonial Pipeline paid the ransom, DarkSide got a taste of their own medicine. The group’s servers were taken offline shortly thereafter and their accounts were drained. As a result, the malicious actors released a decryption tool for all their victims to use, even those who hadn’t paid the ransom.
#1 CWT Global
AMOUNT PAID: $4.5 MILLION
RANSOMWARE: RAGNAR LOCKER
According to a record of ransom negotiations seen by Reuters, the US travel services company CWT paid $4.5 million to malicious hackers who stole vast amounts of their confidential business files and said they had taken 30,000 computers down.
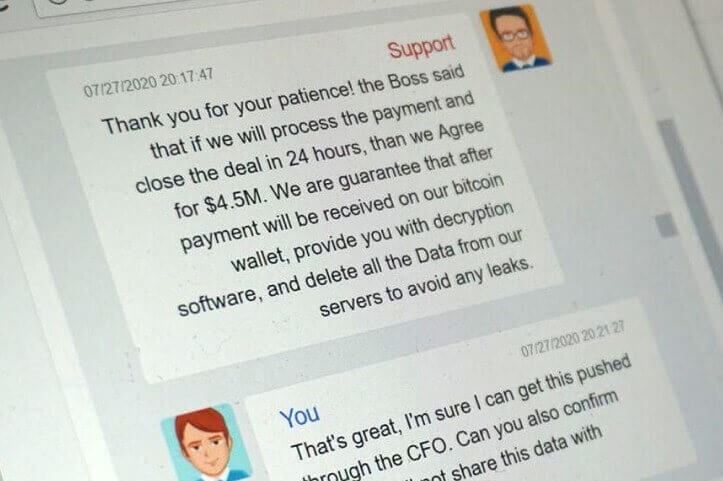
A type of ransomware dubbed Ragnar Locker was used by the attackers, which encrypts data files and makes them unusable until the user pays for access to be recovered. In an anonymous chat room, the ongoing discussions between the hackers and a CWT official remained publicly open, offering a remarkable glimpse into the complex connections that can be created between cybercriminals and their victims.
CWT said it had notified U.S. law enforcement and European data privacy agencies immediately. A source familiar with the investigation believed the number of compromised machines was significantly smaller than 30,000.
According to the messages inspected by Reuters, the hackers initially requested a ransom of $10 million to recover CWT’s files and erase all the stolen data. In the talks, the CWT official, who said that they were speaking on behalf of the Chief Financial Officer of the company, said the organization was severely affected by the COVID-19 pandemic and agreed to pay $4.5 million in Bitcoin.
The hackers reported having stolen two terabytes of data, including financial records, security documentation, and personal details of employees such as email addresses and salary information. Whether the data belonging to some of CWT’s customers (including Thomson Reuters) was hacked was not known.
Ransomware Payout Stats and Trends
2019 Ransomware Stats
- Two-thirds of ransomware attacks targeted state and local governments. (source)
- Over 500 US schools were affected by ransomware attacks in 2019. (source)
- Nearly 70 US government organizations were infected by ransomware since January 2019. (source)
- A total of 140 US local governments, police stations, and hospitals have been infected with ransomware. (source)
- In the third quarter of 2019, the average ransomware payouts increased to $41,000. (source)
2020 Ransomware Stats
- 51% of businesses were targeted by ransomware. (source)
- There was a 40% surge in global ransomware, reaching 7 million hits. (source)
- By the end of 2020, ransomware costs reached $20 billion for all businesses. (source)
- The average ransomware payout demand was $233,817in Q3 2020. (source)
- 1 in 5 SMBs and 4 in 5 MSPs were targeted by ransomware attacks. (source)
2021 Ransomware Stats
- 37% of IT organizations across 30 countries were hit by ransomware in the last year. (source)
- As of May 25, 82 ransomware attacks targeted the healthcare sector alone this year. (source)
- The average mitigation cost of a ransomware attack was $1.85 million. (source)
- Companies experience 21 days of downtime on average following a ransomware attack. (source)
- 80% of victims who gave into ransom payouts experienced another attack soon thereafter. (source)
2022 Ransomware Stats
- In the first half of 2022, there were 236.1 million ransomware attacks worldwide. (source)
- Overall, ransomware attacks decreased rapidly between the second and fourth quarters of 2021, going from nearly 189 million cases to 133 million. (source)
- In 2022, ransomware was the most prevalent form of malware due to its ability to extort large sums of money while posing a low risk to criminals. (source)
- After phishing, ransomware is the second leading cause of data breaches in Q1 2022. (source)
- There were 707 ransomware attempts per organization during the first half of 2022. (source)
Average Ransomware Payouts Trend
Between 2018 and 2020, average ransomware payouts costs per incident nearly doubled from $4,300 to $8,100. And with 2021 being the most prolific year for ransomware operators yet, these numbers are projected to skyrocket by the end of the year.
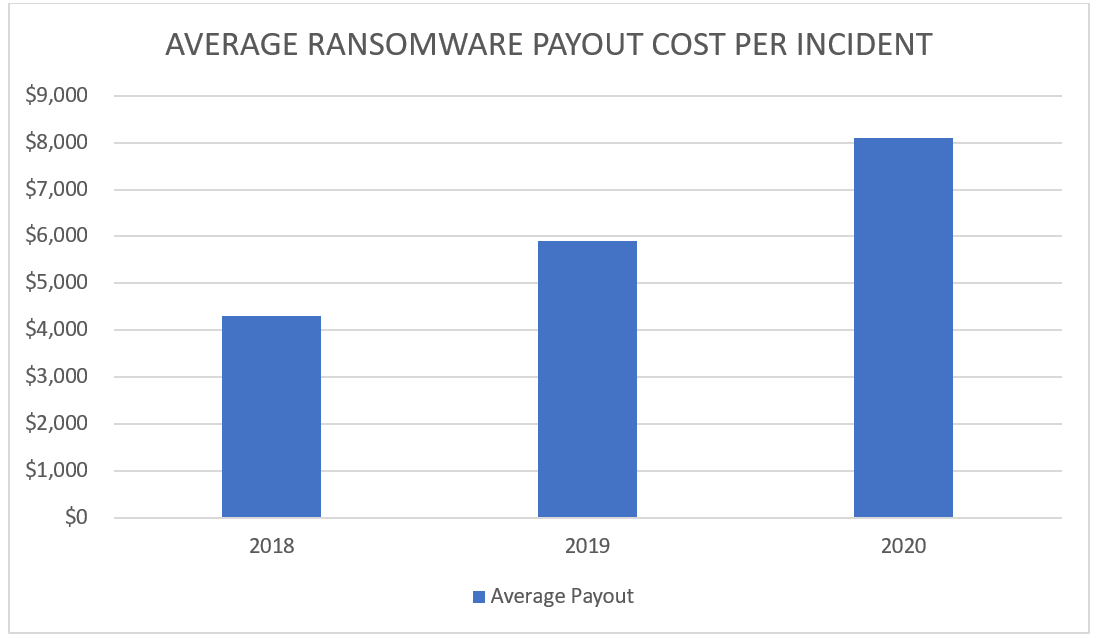
In fact, demands already grew tremendously in 2021. The average cost of ransomware payouts among medium-sized organizations this year so far was $170,404, according to Sophos. In addition to this, the National Security Institute registered a tremendous increase in payment requests between 2018 and 2020, with sums jumping from $5,000 to $200,000.
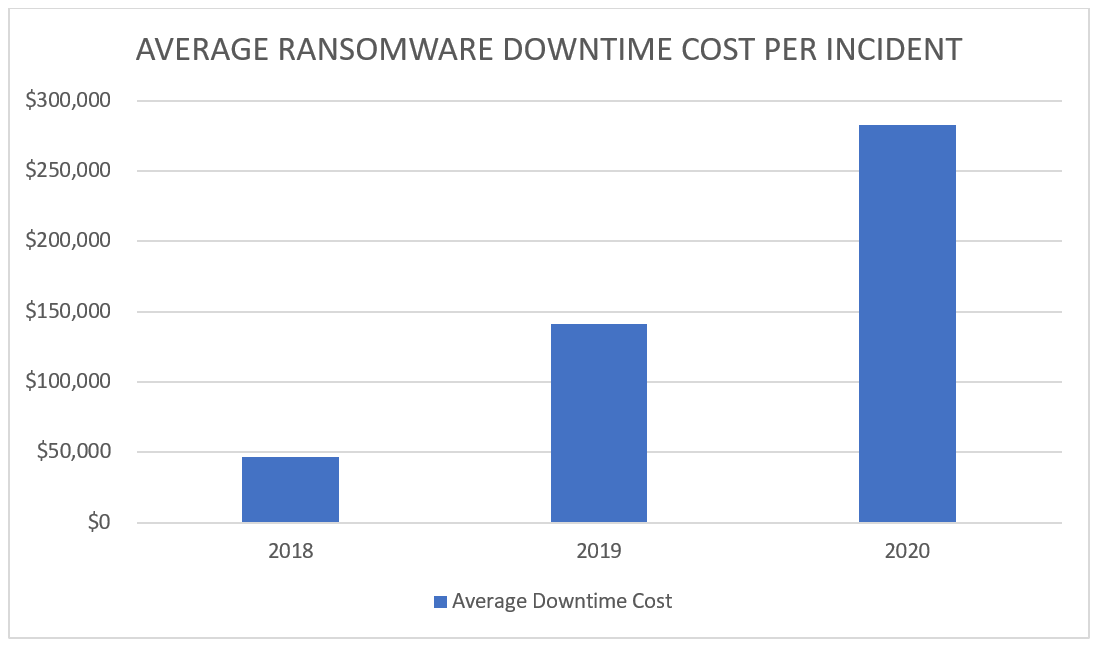
Besides the expenses associated with ransomware payouts, there is another hidden price to pay if your company falls victim to an attack: downtime. Taking servers offline and mitigating damages is a steep affair, even if you respond quickly to the incident. These costs have also been on the rise between 2018 and 2020, jumping from $46,800 to $283,000.
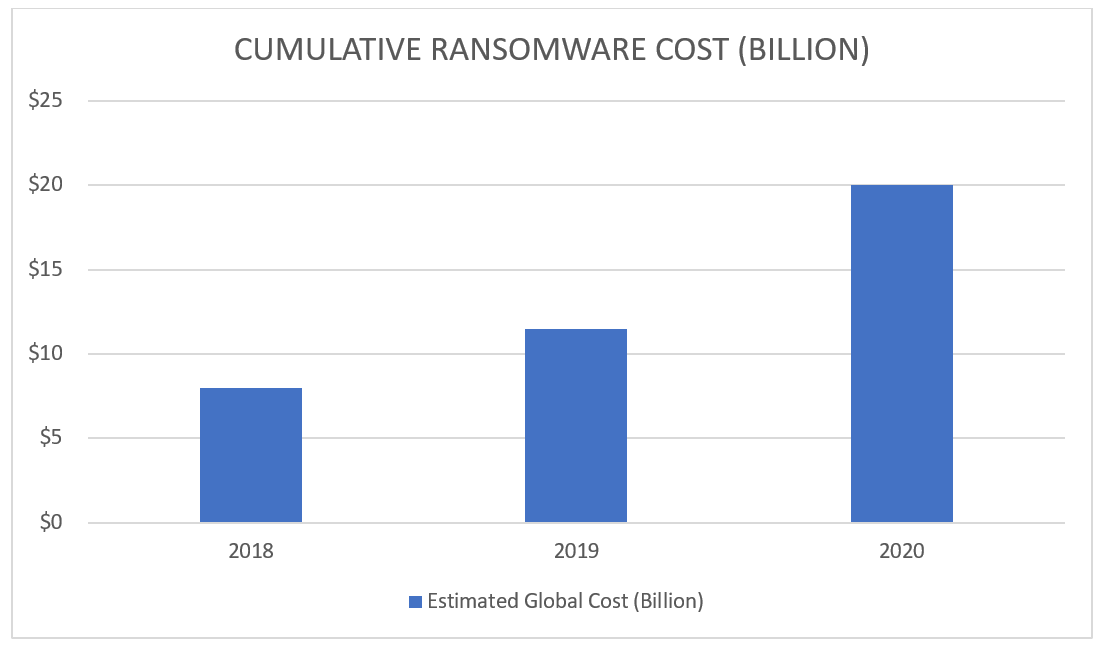
Cumulative Ransomware Payouts Trend
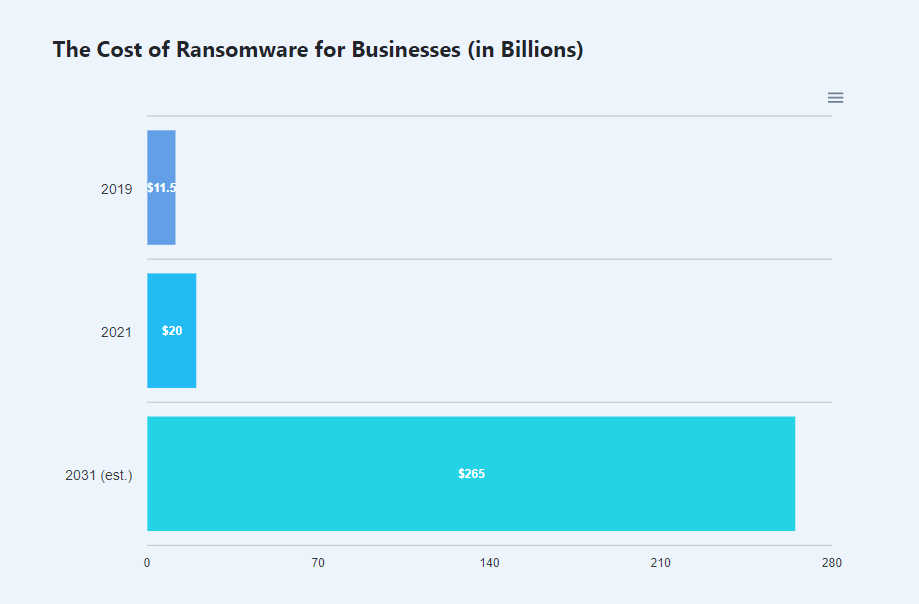
The clearest indicator of how much the cost of ransomware payouts has risen over the last few years is the cumulative number. Over just three years, global estimates went from $8 billion in 2018 to $20 billion by the end of 2020.
What Will Ransomware Cost Businesses in the Future?
The future is not promising. If ransomware attacks continue to grow at their current rate, the total cost of ransomware damages worldwide is expected to reach a staggering $265 billion by 2031.
In some cases, businesses have had to shut down entirely after being hit with ransomware. Ransomware can cause financial loss, data loss, and reputational damage.
Costs associated with downtime in the aftermath of a ransomware attack, such as lost opportunities and reduced production or operating efficiency, can be as high as the ransom paid.
For example, in 2020, the average cost of downtime was $283,000. This represented a nearly 100% increase over 2019 when downtime costs averaged $141,000. (source)
And now the obvious question is…
To Pay or Not to Pay the Ransom?
Today’s organizations live and breathe data, which is why ransomware victims are inclined to pay. One may think that as a result of paying the ransom the issue will simply disappear, however, this will not always be the case. In fact, studies have shown that half of ransomware victims who pay the ransom never get their data back. Here are the top three reasons why Heimdal always advises both individuals and organizations to never pay the ransom:
- There’s no guarantee that all your data will be decrypted. It could only be partially recovered, or not at all.
- You will never find out if your data has already been sold on the dark web.
- This practice fuels future attacks – in a nutshell, this is why ransomware attacks still work.
In addition, if you’re a US-based company, paying the ransom might also get you in trouble with the federal government. On October 1st, 2020, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) released an advisory indicating that paying ransoms may be unlawful in certain situations. All entities that pay could breach the OFAC legislation and thereby be subject to investigation and stiff penalties, regardless of whether the victim or a third party (such as a cyber insurance company) arranged the payment.
For this reason, it’s better to invest the money you would spend on ransomware payouts in your cybersecurity and prevent an attack instead of mitigating it. Heimdal Ransomware Encryption Protection can help you with that.
Heimdal™ Ransomware Encryption Protection
A 100% signature-free component that is compatible with any antivirus solutions on the market, Ransomware Encryption Protection adds revolutionary detection and remediation of any type of ransomware to your company network. Furthermore, it is effective against any strain, both fileless and file-based.
Are you considering adding groundbreaking ransomware prevention to your suite of cybersecurity solutions? Feel free to drop us a line over at sales.inquiries@heimdalsecurity.com and let’s chat about it.
Wrapping Up…
Ransomware payouts and the attacks that lead to them are on the rise yet again in 2021. And while paying the ransom is an expensive affair in itself, mitigation after the fact is even costlier. For this reason, your top priority for your enterprise this year should be ransomware prevention. Don’t wait until it happens to you. Keep your digital assets safe today.
This article was initially published by Alina Georgiana Petcu and was updated by Gabriella Antal on January 20th, 2023.
Do you work for an NHS Trust? Heimdal is giving you free ransomware licenses to combat growing cyber attacks.
Get your free ransomware protection here.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









