Contents:
The global market leader in chemicals and ingredients distribution Brenntag disclosed additional details on what information was accessed and taken from its network by DarkSide ransomware operators following an attack that targeted the company’s North America division.
The worldwide chemical distribution organization Brenntag is headquartered in Essen, Germany operating in more than77 countries around the world. The distributor has 17,000 employees spread out across 670 sites worldwide.
Their two global divisions, Brenntag Essentials, and Brenntag Specialties provide a full-line portfolio of industrial and specialty chemicals and ingredients as well as tailor-made application, marketing and supply chain solutions, technical and formulation support, comprehensive regulatory know-how, and digital solutions for a wide range of industries.
Medical Records and Other Sensitive Information Stolen
The distributor stated that it became aware on April 28, 2021, of an information security incident impacting some of its computer systems. As soon as they learned about the attack, they disconnected affected systems from the network to limit the threat.
Our investigation confirmed that Brenntag systems were accessed without authorization starting on April 26, 2021, and/or that some information was taken from our system.
The German organization confirmed that the information taken may include date of birth, driver’s license number, medical records, and social security number.
However, the chemical distributor said there is no evidence that any information was misused for fraudulent purposes as a result of the ransomware attack.
In addition, third-party cybersecurity forensic specialists were immediately engaged to help with the investigation and law enforcement was notified.
Those affected by the DarkSide ransomware attack were asked by the organization to review their account statements and pay attention to their free reports in order to recognize identity theft or fraud attempts.
If you find any transactions you do not recognize, contact the business or institution issuing the statement.
Brenntag Paid a $4.4 Million Ransom in Bitcoin
Bleeping Computer has confirmed that after negotiation the chemical distribution enterprise paid the requested ransom on May 11, but is important to say that the DarkSide ransomware hackers demanded a $7.5 million ransom at first.
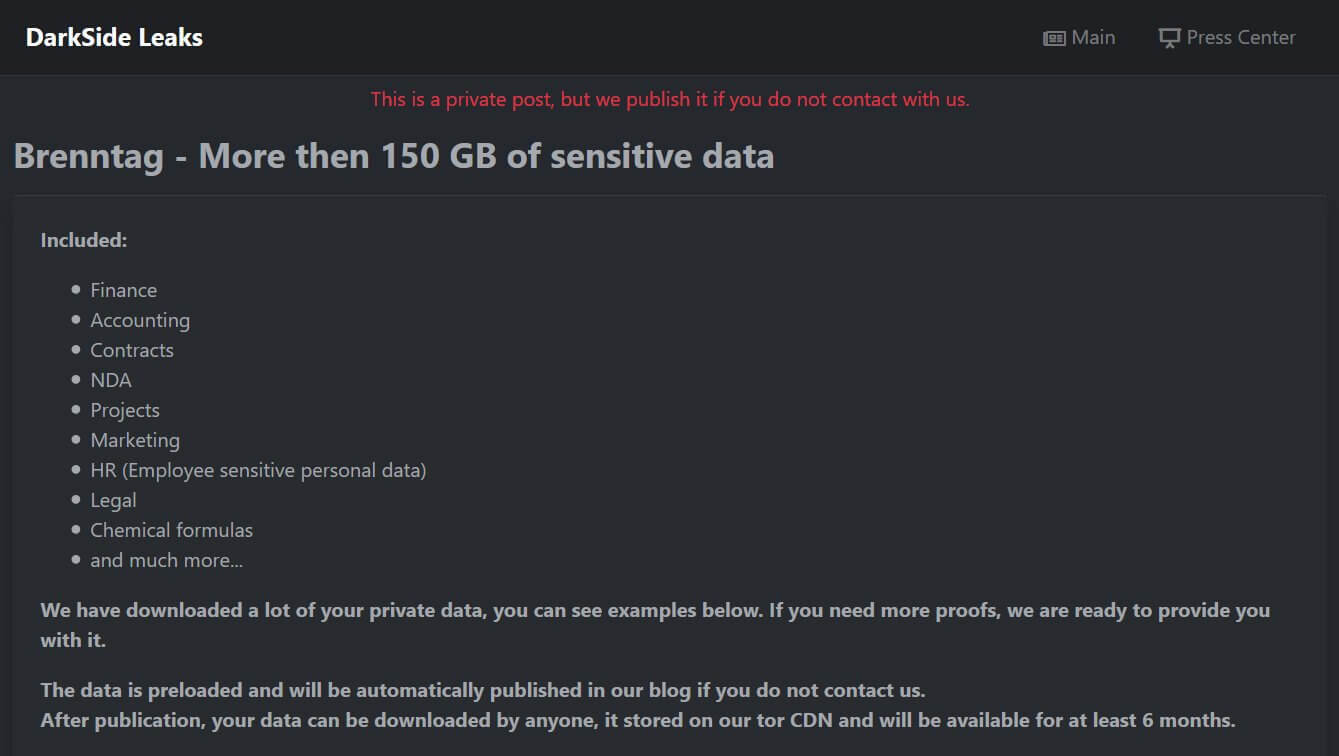
The Darkside ransomware threat actors claimed to have stolen 150GB of data when the attack occurred.
In order to prove it, the cybercriminals created a private data leak page that included a representation of the types of information that were stolen and screenshots of some of the files.
DarkSide Ransomware operates under the form of a Ransomware-as-a-Service (RaaS), in which the gains are shared between its holders and partners, or affiliates, who allow entry to companies and execute the ransomware. The DarkSide ransomware gang gets around 25% of a ransom payment, and the rest is taken by the affiliate who organized the assault.
Usually, in a ransomware negotiation, the affiliate has to reveal how they acquired access to the victim’s data. This can be done in the form of a multi-page security audit report or just a paragraph in the Tor chat screen describing how they obtained access.
In Brenntag’s case, the DarkSide affiliate said they have obtained access to the network after purchasing stolen information, but didn’t know how the credentials were obtained, to begin with.
Since learning of the ransomware attack, Brenntag has been taken steps to further protect and strengthen the security of their systems.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security