Contents:
In the ever-evolving landscape of cyber threats, ransomware remains a pervasive and destructive weapon in the arsenal of cybercriminals. Among the various ransomware strains, Phobos has gained notoriety for its sophisticated capabilities and devastating consequences. This article delves into Phobos ransomware, exploring its origins, modus operandi, impact, and prevention measures.
What is Phobos Ransomware?
First detected in December 2018, Phobos ransomware is yet another cyber-threat that mainly targets organizations. However, unlike other cybercrime gangs that practice big game hunting, the malicious actors behind Phobos typically target smaller enterprises with fewer means to pay large ransoms.
Therefore, the average ransom demand from an attack is $18,755. Regarding its genetic makeup, Phobos ransomware is a heavily similar strain to the infamous Dharma variant.
Experts regard the former as a highly identical version (some would go as far as to say rip-off) of the latter. Moreover, according to Coverware, Phobos and Dharma seem inspired by the more prominent CrySis ransomware family.
A. Phobos Ransom Note
The first similarity between the two strains to stand out is the ransom note. Phobos ransomware essentially deploys the same HTA file onto the infected computers as Dharma, the only difference being its branding slapped onto the top and bottom of the HTA file. See the image embedded below for an illustration of the ransom note, courtesy of ZDNet and Coverware.
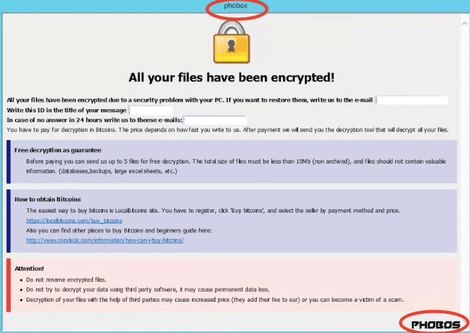
Image Source: ZDNet
On top of the HTA file, Phobos ransomware also drops a text document ransom note that is considerably shorter than its counterpart on the infected device. It reads as follows:
!!! All of your files are encrypted !!! To decrypt them send e-mail, to this address: [email address 1] If there is no response from our mail, you can install the Jabber client and write to us in support of [email address 2]
As you can notice by comparing the two, the latter does not contain relevant information such as the generated ID, nor is it that explicative in terms of demands. This means that less tech-savvy victims might have to resort to doing their research if the TXT file is the only one they recognize.
Nevertheless, HTA files are actually not difficult to maneuver at all. An HTA file is executable and can be run from an HTML document. It contains hypertext code, as well as VBScript or Jscript code readable by the Microsoft HTML Application Host. This means that you can easily open it in Microsoft’s Internet Explorer or Edge browsers by double-clicking it if your device operates on Windows.
B. Phobos Ransomware Encryption
Phobos ransomware encrypts files on the infected device through AES-256 with RSA-1024 asymmetric encryption. Therefore, on top of the copied and pasted ransom note, it is worth noting that both Phobos and Dharma employ the same RSA algorithm.
However, one notable difference is that Phobos operators implement it from Windows Crypto API, while the Dharma gang runs it from a third-party static library.
Furthermore, encrypted files names are created through the same process in both cases, namely by adjoining:
- The original file name;
- A unique ID number;
- The ransomware operator email;
- And the .phobos extension.
Therefore, if your data has been corrupted by it, your file names will read as follows:
- [filename].[ID][email address 1].[added extension]
While the .phobos extension is the most logical visual cue to look for, you should also be aware that it might not always be the one present in the eventuality of an infection. In an article she penned for the MalwareBytes Labs blog, malware intelligence analyst Jovi Umawing identified over 50 other file extensions used by the ransomware operators behind the operation:
- 1500dollars, actin, Acton, actor, Acuff,
- Acuna, acute, adage, Adair, Adame, banhu,
- banjo, Banks, Banta, Barak, bbc, blend,
- BORISHORSE, bqux, Caleb, Cales, Caley,
- calix, Calle, Calum, Calvo, CAPITAL, com,
- DDoS, deal, deuce, Dever, devil, Devoe,
- Devon, Devos, dewar, Eight, eject, eking,
- Elbie, elbow, elder, Frendi, help, KARLOS,
- karma, mamba, phoenix, PLUT, WALLET, zax.
How Does Phobos Ransomware Spread?
Much like other cyber-threats, Phobos ransomware infects devices and potentially spreads across the entire network in five main ways:
- Unprotected remote desktop protocol (RDP) connections,
- Brute-forced remote desktop protocol credentials,
- Stolen RDP credentials bought on the black market,
- Patch exploits and other software vulnerabilities,
- And phishing campaigns.
Once Phobos ransomware enters your system, it fully encrypts standard-sized files. Its algorithm differs for large files, however, partially encoding selected segments only. In this way, it manages to save time and maximize damage at the same time.
Most file formats are affected by the ransomware, including popular extensions such as .avi, .backup, .doc, .docx, .html, .jpg, .jpeg, .mkv, .mp3, .mp4, .pdf, .rar, and .zip. The following operating system files are not encrypted as a result of the infection:
- boot.ini
- bootfont.bin
- io.sys
- ntldr
- ntdetect.com
On top of encoding your files, Phobos also terminates active operating system processes to clear its path into your files. It also deletes local backups and shadow copies, similarly to Sodinokibi ransomware. Finally, it disables recovery mode and your firewall as well to further prevent you from rebooting the device and stopping the infection.
How to Decrypt Phobos Ransomware
As per the extensive list of decryption tools on the No More Ransom Project website, both Dharma and CrySis are decrypted by the Rakhni decryptor developed by Kaspersky Lab. What is more, CrySis can also be decrypted through a specialized tool created by Trend Micro. Unfortunately, no Phobos ransomware decryption tool has been made available as of yet.
However, we also keep an alphabetical tally of all the ransomware decryptors released into the wild, so you can also check back to our blog from time to time and see if one has materialized. Therefore, the only way you can receive a decryptor upon infection is by paying the ransom, which I do not recommend. As per a thorough investigation conducted by Coverware, the data recovery rate is around 85%, which means not everyone gets a decrypting tool after sending the required amount of money.
Thus, there is simply no guarantee that you will get your files restored. Plus, you will also fund cybercriminal activity in the process, which will allow the Phobos ransomware gang to wreak even more havoc in the future. So, long story short, don’t pay the ransom. Focus your funds and efforts on prevention instead.
Preventing a Phobos Ransomware Infection
#1 Educate Your Employees on Ransomware
As a small business owner targeted by Phobos ransomware, your employees are your first line of defense against an incoming cyberattack. This is why I recommend training them to be your priority in the context of a larger prevention plan. For example, good ol’ fashioned phishing campaigns were among the five main ways in which Phobos and other ransomware strains spread.
Therefore, teaching staff how to recognize suspicious links, malicious attachment, counterfeit branding, and other components of malspam constitutes a valuable security resource for your business. Of course, proper cybersecurity training should not end there. Members of your company’s personnel should be aware of all the complexities that come with a ransomware infection, as well as the other types of cyber-threats out there.
#2 Always Patch Software Vulnerabilities
As previously mentioned, Phobos spreads through patch exploits and other software vulnerabilities as well, among other things. This is why you should deploy system updates as soon as they are released by their respective developers.
However, this can become quite disruptive to your employees’ activity, which is why most of them will probably postpone patch deployment as much as they can. The Heimdal Patch & Asset Management automatic updater takes care of this issue efficiently, installing third-party patches in the background as soon as they are distributed.
In addition to software patching, Heimdal Threat Prevention benefits from proprietary DarkLayer Guard™ & VectorN Detection technology which filters traffic and detects DNS hijacking. By doing so, it effectively protects your endpoints from exploits, ransomware, data breaches, and other advanced threats. This enhances and complements your existing suite of cybersecurity solutions for round-the-clock protection.
#3 Create Online and Offline Data Backups
In the eventuality of a Phobos ransomware attack, having backups of your company data means that you can restore files without the need to pay cybercriminals for a decryptor. Our recommendation is to create both online copies in the cloud, as well as offline ones using external storage devices.
Nevertheless, please keep in mind that linked storage accounts and devices can also be encrypted via ransomware infection. For this reason, you will also need to respond quickly in case this happens to you and disconnect them as soon as possible.
Final Thoughts on Phobos Ransomware
Like its counterparts, Phobos ransomware poses a significant threat to individuals and organizations. Its evolution and adaptability make it a formidable adversary in cybersecurity.
However, with vigilant cybersecurity practices, regular backups, and a commitment to prevention, individuals, and organizations can significantly reduce the risk of falling victim to Phobos ransomware and other malicious threats in the digital realm. With the proper cybersecurity solutions, extensive employee training, and a reliable data backup source you can increase your odds in the battle against advanced online threats.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










