Contents:
The ransomware invasion has increased significantly in the last few years with a big impact and causing data leakage and important financial loss for both organizations and individuals. It continues to dominate the threat landscape and also affects important sectors such as hospitals, banks, universities, government, law firms, mobile users.
In this article, I will discuss CryLock Ransomware, a dangerous infection that can encrypt your personal files. I will go into what CryLock ransomware is and what separates it from its predecessor, Cryakl. Technical analysis will ensue afterward, followed by actionable advice on how to prevent an attack.
What Is CryLock Ransomware?
Before discussing CryLock Ransomware, we first need to take a look at its predecessor, Cryakl. First seen in early 2014 spreading via email, Cryakl Ransomware works like most ransomware by encrypting files and demanding a ransom for file retrieval. However, the malware requires victims to contact its operators via email in order to find out the ransom amount to be paid. With this method, there is also the opportunity to upload test files for decryption verification and, in some cases even negotiate the price for file restoration.
Based on the same malicious code, CryLock Ransomware is in fact a new version of the Cryakl Ransomware infection, employing the same distribution tactic. It uses a technique called cryptoviral extortion, which basically means extorting money from victims by encrypting their files and demanding a ransom for their decryption.
CryLock Ransomware MO
How does CryLock Ransomware spread around? It most likely travels via spam, unsecured RDP, and malicious downloads. Thus, users download and install such infections willingly because they do not recognize the potential threat.
According to 2-Spyware, CryLock ransomware assigns extensions and file changes a bit differently than other strains – it appends a random three-letter string or no extension at all. What’s even more interesting is that it also uses a contact email and the user ID. Below you can find two such examples:
- doc.[darkmask@mailfence.com][fervis].[98252B9E-3FE98E00]
- doc.[flydragon@mailfence.com][sel4auto].[A15F580C-524AC4DB]
This infection can encrypt a variety of files (documents, archives, audio files, videos, images, etc.) with a complex algorithm and demand a ransom for their decryption.
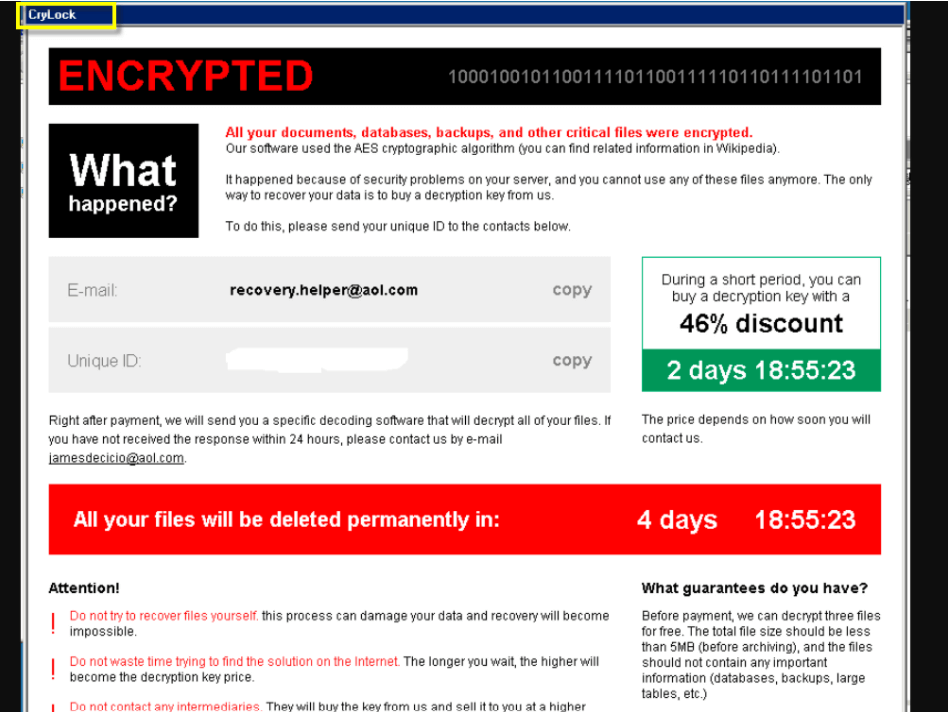
Image Source: 2-Spyware
After the encryption process is completed, a ransom note pop-up window appears on the victim’s device. Within it, CryLock operators state that they have the required tool for decryption and that the victims will have to pay a ransom to receive it. To prove that such a tool exists, the cybercriminals offer the victims to send them up to three files (no more than 5 MB) for test decryption.
On the Desktop, CryLock Ransomware drops a file dubbed “how_to_decrypt.hta.” It opens a message, with which the attackers are trying to convince you to get in touch with them.
A unique ID is also provided to the victims, along with two timers: one that indicates the time left to pay the ransom, and one that shows how much time is left until the files are permanently lost.
In addition, CryLock warns its victims not to rename the encrypted files or try using any third-party decrypting software as that may lead to data being undecryptable.
One thing is for certain – the CryLock operators are the only ones that can unlock the encrypted files. But dealing with the criminals is the worst option a victim can do. As always, I advise both individuals and organizations to never pay the ransom. Most likely, it will lead to a lose-lose situation where the unfortunate users will not only lose money but never regain access to their data too.
Today’s organizations live and breathe data, which is why ransomware victims are inclined to pay. One may think that as a result of paying the ransom the issue will simply disappear, however, this will not always be the case. In fact, studies have shown that half of ransomware victims who pay the ransom never get their data back. Here are the top three reasons why you should never give in to such demands:
- There’s absolutely no guarantee that all your data will be decrypted. It could only be partially recovered, or not at all.
- You will never find out if your data has already been sold on the dark web.
- This practice fuels future attacks – in a nutshell, this is why ransomware attacks still work.
CryLock Ransomware Removal Instructions
When you’re dealing with any ransomware infection, a quick response is crucial. Therefore, the initial action you want to take is to isolate the infected device to prevent CryLock from spreading to other computers that operate in the same local network.
Below you will find the three stages that you need to follow to ensure that the infected machine is completely offline.
- Disconnect the machine from the Internet by unplugging the Ethernet cable. If your computer is coupled to a Wi-Fi network, I recommend disabling the connection from your computer’s Control Panel.
- Eject any external storage devices by going to My Computer, right-clicking the drives in question, and selecting the Eject option. This will stop CryLock ransomware from encrypting them as well.
- Log out from the cloud to prevent cybercriminals from hacking applications and data stored there as well.
After completing all these steps, you can proceed with the removal process.
- After you’ve ensured that the infected device(s) is no longer connected to others in the network, it’s time to ascertain the extent of the damage that was done. In the case of a CryLock ransomware attack, doing so is relatively easy. If you can find the {random name}.exe file that launched the infection, right-click it and choose Delete.
- Move to the Desktop and then right-click and Delete the file named hta.
- Once you think that all malicious files are gone, quickly Empty Recycle Bin.
- Implement a legitimate malware scanner to help you scan your system and check for malware leftovers.
Another option would be to look for a CryLock decryptor. I suggest getting your decryptors from verified sources only. For example, you can check our very own blog article on free ransomware decryption tools. We also vouch to keep you posted regularly and we’ll add the CryLock ransomware decryptor there as soon as it will become available. In the meantime, what you can do in the case of infection is to contact the relevant cybercrime authorities in your region or reach out to competent third-party vendors that can help you deal with mitigation.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Wrapping It Up…
When we’re dealing with ransomware attacks, we have to understand that prevention is the most important thing. We have to be able to recognize the malware distribution patterns so that we could prevent CryLock Ransomware from entering target systems.
If you receive suspicious emails with attachments, you have to either delete these messages immediately or at least scan the attached files before you open them. While it might seem that those files are important documents, in most cases they’re just scams. I recommend investing in a licensed antispyware tool that will help you screen the received files, and thus minimize the chances of a ransomware attack.
With reference to cybersecurity tools, I suggest you check out Heimdal™’s Threat Prevention suite, which proactively offers DNS, HTTP, and HTTPS filtering at the perimeter and endpoint level. Our proprietary technologies, DarkLayer™ GUARD and VectorN Detection™ act jointly to enhance the DNS filtering process with AI-based behavioral analysis and detection. As part of our endpoint cybersecurity suite, but also of our perimeter-based solution, they offer excellent defenses against complex cyber aggressions. Additionally, Heimdal Patch & Asset Management module helps organizations fix software vulnerabilities, achieve compliance, and uniquely prevent and stop ransomware, APTs, data leaks, exploits, and more.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










