Contents:
South Korea seems to be a target of a new malicious campaign that propagates RAT malware camouflaged into a game for adults. The way it is distributed happens via torrents and also webhards.
The types of RATs cybercriminals use in this campaign are njRAT and UDP RAT. They are hidden into a seemingly game package (it could be a different program too). Then they will be loaded into the webhards.
RAT Malware: the Way It Self-Propagates
The ASEC researchers were the ones who addressed this matter in a report. As described by them, the new RAT malware works like this:
- UDP RAT is distributed via webhards;
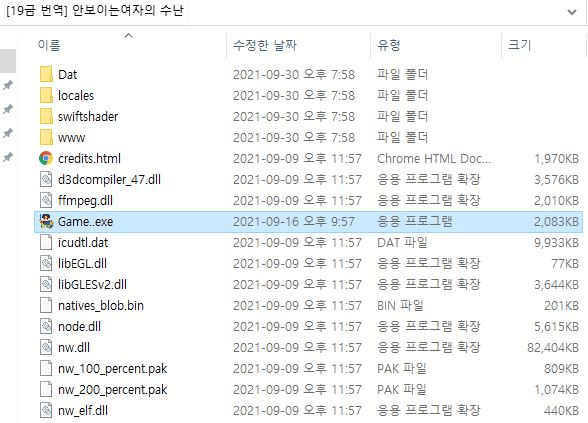
- However, it doesn’t come in its real shape but disguised as a ZIP file with an adult game inside;
- After the archive gots extracted, it can be seen that this contains a ‘game.exe’ launcher;
- The ‘game.exe’ launcher represents basically the UDP rate malware;
- The file is executed and delivers a Themida-packed RAT;
- Then it hides with the goal to produce another Game.exe file;
- The second executable will have the real game inside, so no suspicion from the victim’s side;
- The ‘C:\Program Files\4.0389’ folder is the place where malware executables will be dropped;
- njRAT poses a threat as it can perform sensitive data theft (e.g. keystrokes or credentials);
- It can also change the Windows Registry to ensure its domination through a registry key that enables the C2 server regular connection.
What Are Webhards Though?
And now comes the question: what are webhards used for? WebHard stands for a very well-known Korean online storage service through which you can directly download various files. No one takes care to check the uploaded content, so users should pay attention to what they download from there.
ASEC researchers also warned in June about “Lost Ruins”, a game through which another malware was being dropped.
What Is a RAT?
As our colleague, Cezarina thoroughly explained in her article called “What is a Remote Access Trojan?”, a RAT stands basically for a malware type. Threat actors can use this type of malware to achieve complete system control. RATs normally join legitimate files and through its means, a cybercriminal can achieve access to local files or other sensitive info at their convenience. The connection could also be made use of for virus downloading with the goal to ensure malware propagation.
How to Stay Safe?
The cybersecurity landscape registers all types of malware on and on nowadays. You cannot be the winner in a malware fight without the right tools. We at Heimdal™ know what excellence means so we recommend you our very own Heimdal™ Threat Prevention that has just won the Cloud-Delivered Security Solution of the Year Award. Stop hidden threats and move beyond traditional detection with our one and only Threat Prevention.
If you enjoyed this article, you’ll surely enjoy other pieces of content too. To make sure you do not miss a thing follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security