Contents:
Google advertisements have been exploited to distribute various types of malware over the past few months. To trick unsuspecting users into downloading malware onto their systems, threat actors often used the platform to promote fake websites on legit software and application updates.
One such malware family observed during this recent spike is called LOBSHOT. It continues to collect victims while remaining undetected. Researchers claim that the infrastructure belongs to TA505, the well-known cybercriminal group associated with Dridex, Locky, and Necurs campaigns.
Shedding Light on the Campaign
Earlier this year, Elastic Security Labs observed a multiple infection chain campaign that targeted users searching for legitimate software downloads on Google. Attackers promoted their malware using an elaborate scheme of fake websites through Google Ads and embedding backdoors in what appears to users as legitimate installers.
For example, a malicious ad promoting the AnyDesk remote application was found circulating on the Google search engine. The landing pages looked very similar to that of the original website and included a ‘Download Now’ button. Once the users clicked on the button, it launched the execution of the LOBSHOT malware.
With its hVNC (Hidden Virtual Network Computing) component, LOBSHOT offers a number of core capabilities. This feature allows for direct and unobserved access to the machine. It continues to be effective in bypassing fraud detection systems and is often built into many popular families as a plugin.
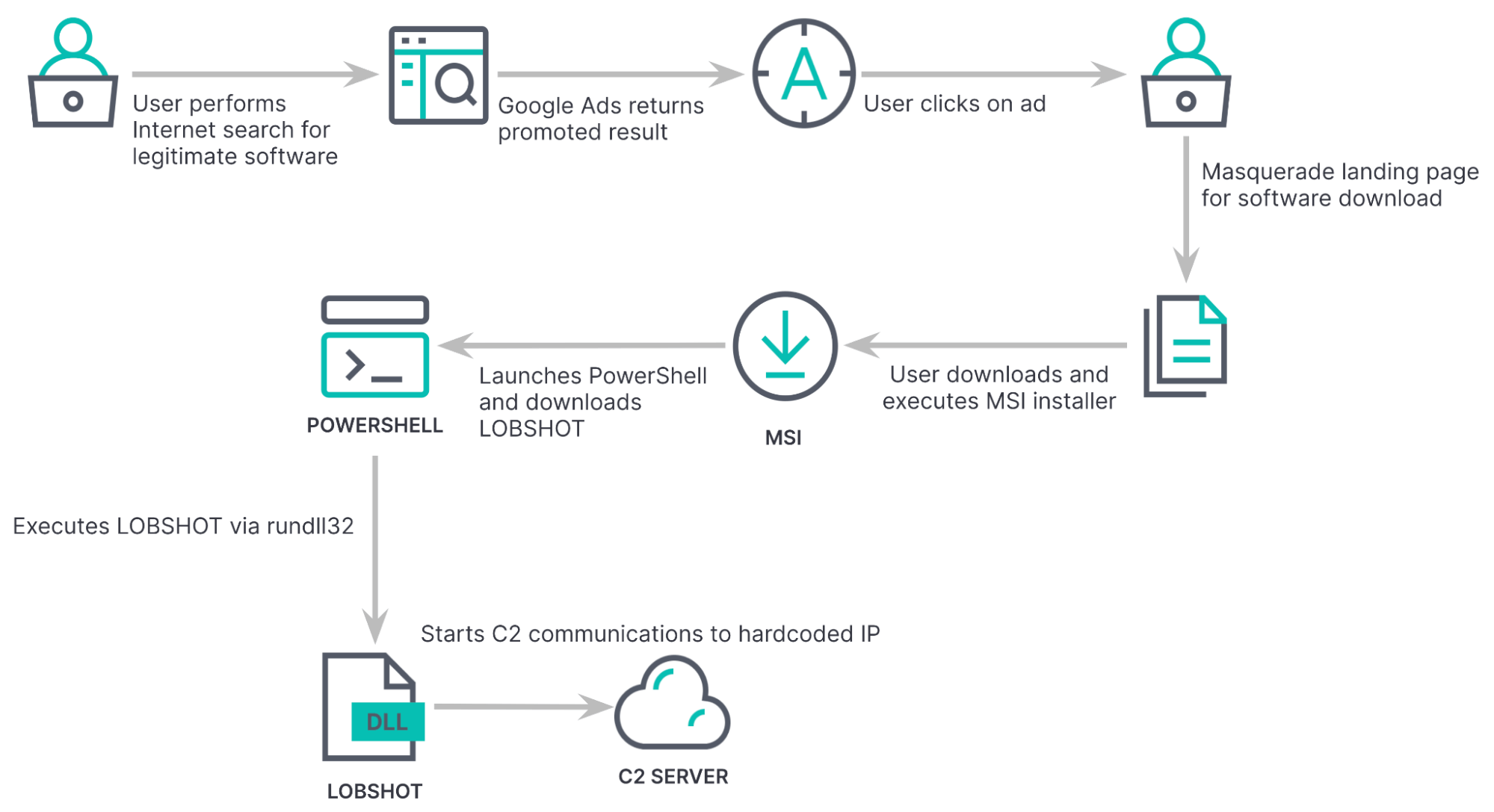
According to the report, upon loading the initial libraries, LOBSHOT performs a Windows Defender anti-emulation check. This is achieved by verifying if the computer name matches the string HAL9TH and if the username matches JohnDoe, which are hard-coded values within the emulation layer of Defender. If they are present, the malware immediately stops running. This kind of verification has been incorporated in many other stealers including Arkei, Vidar, and Oski.
Further, after LOBSHOT is executed, it moves a copy of itself to the C:\ProgramData folder, spawning a new process using explorer.exe. This way, it terminates the original process and deletes the original file.
You can review the extended report here.
With banking trojans, cryptocurrency, and information-stealing capabilities, LOBSHOT appears to be used for financial purposes. There are 32 Chrome extensions, nine Edge wallet extensions, and 11 Firefox wallet extensions that are targeted, allowing threat actors to steal cryptocurrency assets.
Why Do We Still Deal with Malvertising?
Malvertising campaigns are a popular way for cybercriminals to distribute malware, indicating that they will continue to use the technique in the future. While malware such as LOBSHOT might seem small and is yet to expand its attack scope, it ends up packing significant functionality, which assists threat actors in moving quickly during the initial stage, allowing them to gain full control over systems remotely.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







