Contents:
Google Ads have become increasingly used by malware operators to spread malware to unsuspecting users searching for popular software products.
The products impersonated in these campaigns include Grammarly, MSI Afterburner, Slack, Dashlane, Malwarebytes, Audacity, μTorrent, OBS, Ring, AnyDesk, Libre Office, Teamviewer, Thunderbird, and Brave.
By cloning the official websites of the above projects, threat actors distribute trojanized versions of the software.
Malware delivered this way includes variants of Raccoon Stealer, Vidar Stealer, and IcedID malware loaders.
BleepingComputer reported recently that a ‘typosquatting’ campaign used over 200 domains to impersonate software projects. Another example used fake MSI Afterburner portals to infect users with RedLine stealers.
A piece of information that has now become known is how users were exposed to these websites. These malicious websites are promoted through Google Ad campaigns.
Abuse of Google Ads
By using Google Ads, advertisers can promote pages on Google Search, placing them high in the list of results as advertisements, often above the project’s official website.
Users looking for legitimate software on a browser without an active ad blocker will see the promotion first and likely click on it since it looks very similar to the actual search result.
As soon as Google detects a malicious landing page, the campaign is blocked, and the ads are removed, so threat actors must use a trick to bypass the automated checks.
It involves redirecting victims to an irrelevant but benign site created by the threat actor and then redirecting them to a malicious site posing as the software project, according to Guardio and Trend Micro.
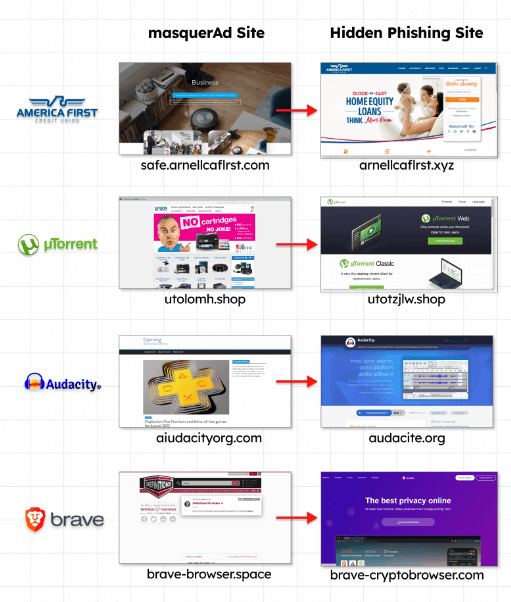
According to Guardio Labs, once targeted visitors visit those “disguised” sites, the server immediately redirects them to the rogue site and, from there, to the malicious payload.
Those rogue sites are practically invisible to visitors not reaching them from the actual promotional flow, appearing benign, unrelated, to crawlers, bots, occasional visitors, and to Google’s policy enforcers.
Source: Guardio Labs.
As a result, the payload is downloaded from reputable file-sharing and code-hosting services such as GitHub, Dropbox, or Discord’s CDN. This ensures that antivirus programs won’t block the download.
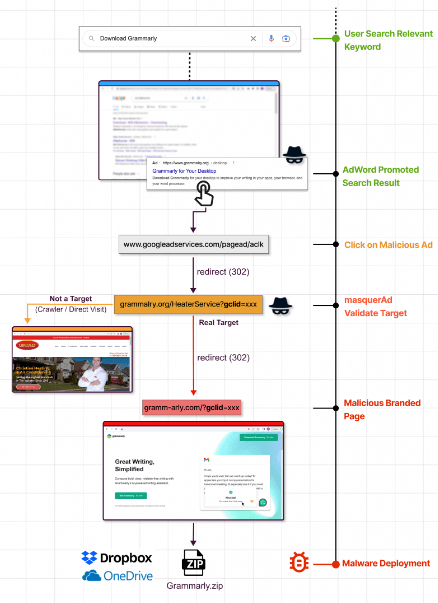
In a campaign Guardio Labs observed in November, a trojanized version of Grammarly delivered Raccoon Stealer to users. The malware was bundled with legitimate software and silently installed by users.
According to Trend Micro’s report on the IcedID campaign, attackers are abusing Keitaro Traffic Direction System to determine if a website visitor is a researcher or a valid victim before redirecting them.
Keep Away from Harmful Downloads
Internet users should be cautious when dealing with promoted search results since they carry all the signs of legitimacy. In addition, the FBI recently issued a warning about this type of ad campaign.
An ad-blocker on your web browser will filter out promoted results from Google Search, helping you block these campaigns.
If you need clarification on the official domain, you can find it on the Wikipedia page of the software project you’re looking for.
For direct access to a particular software project’s website, bookmark the URL if you visit it frequently. In most cases, abnormal file size indicates that the installer you’re about to download is malicious.
Another sign of foul play is the domain name, which may resemble the official one, but has swapped characters in the title or a single mistaken letter, known as typosquatting.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










