Contents:
A Google ads malvertising campaign was found using KoiVM virtualization technology to install the Formbook data stealer without being spotted by antiviruses.
MalVirt loaders are promoted by threat actors in advertising that appears to be for the Blender 3D program. The downloads presented by the fraudulent sites try spoofing Microsoft, Acer, DigiCert, Sectigo, and AVG Technologies USA`s digital signatures.
Although Windows will not display these incorrect signatures as being signed, the MalVirt loaders still contain capabilities to evade detection. Cyber researchers explained that:
Some samples patch the AmsiScanBuffer function implemented in amsi.dll to bypass the Anti Malware Scan Interface (AMSI) that detects malicious PowerShell commands.
Further, in an attempt to evade static detection mechanisms, some strings (such as amsi.dll and AmsiScanBuffer) are Base-64 encoded and AES-encrypted.
Querying specific registry keys, the loaders would stop if they detected running in a virtualized environment, so they won`t be spotted.
What Is KoiVM and How Was It Used?
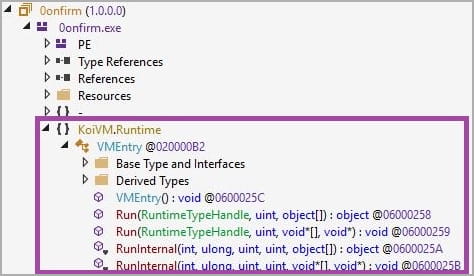
The KoiVM plugin for ConfuserEx.NET protects programs by obfuscating their opcodes so that only the virtual machine can decode them. The virtual machine transforms the opcodes back to their original form when the application is started so that it can be run.
According to cyber researchers:
Virtualization frameworks such as KoiVM obfuscate executables by replacing the original code, such as NET Common Intermediate Language (CIL) instructions, with virtualized code that only the virtualization framework understands
The virtualized code is executed by converting it into the original code at runtime using a virtual machine engine.
When hackers use virtualization, it complicates malware investigation and also shows an effort to elude static analysis tools. For one of the analysed Google Ads campaigns the adversary pushed the Formbook data-stealing malware as virtualized .NET loaders dubbed ‘MalVirt,’ to help spread the final payload but go unnoticed by the antivirus.
Although KoiVM virtualization is largely employed for hacking tools and cracks, deploying malware is not its usual goal. This unusual way of using KoiVM could be one of the side effects that came up after Microsoft disabled macros in Office.
Formbook`s New Tricks
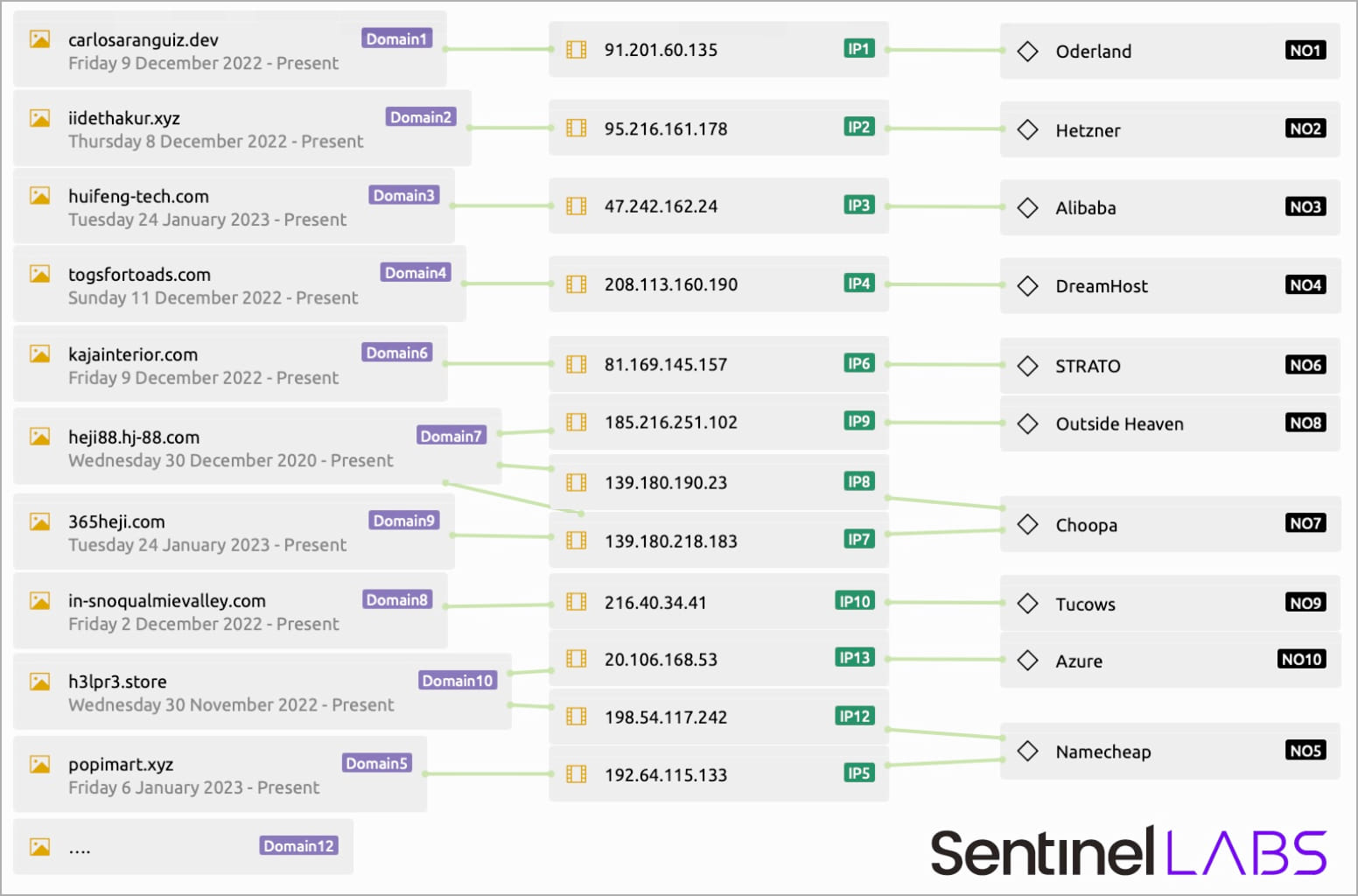
Formbook also was discovered using a new trick for covering its real C2 (command and control) traffic and IP addresses. The data-stealing malware combines its actual traffic with a variety of “smokescreen” HTTP requests, each of which has its content encoded to blend in with the background traffic. The malware randomly selects these IPs from a hardcoded list of domains hosted by multiple companies and interacts with them.
According to researchers, Formbook pretended to be communicating with 17 domains, while only one of them was the C2 server. The other ones were just used to trick network traffic monitoring tools.
Since the number of malware distribution attempts through Google Advertising is on the raise, users are advised to beware when clicking links in search results and enforce their endpoint security policies.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security