Contents:
As time passes, threat actors are getting sneakier in their efforts. Security researchers discovered that lately a lot of fake websites impersonating popular free and open-source software have started to pop up in the sponsored section on Google search results.
Crypto Influencer Stripped of NFTs
At least one well-known cryptocurrency user claims to have been a victim of the operation, which allowed hackers to take control of both their personal and professional accounts as well as all of their digital crypto assets.
The crypto influencer known as NFT God fell victim to the hackers’ efforts after launching a fake executable for the Open Broadcaster Software (OBS) video recording and live streaming software they downloaded from a Google ad in search results.
Yesterday afternoon I went to download OBS onto my personal desktop computer.
OBS is industry standard video streaming software. I was excited to live stream some video games for the first time in my life.
What I didn’t realize was I clicked the sponsored link on google
— NFT God (@NFT_GOD) January 15, 2023
Sharing the experience on Twitter, the influencer said that “nothing happened” when they accessed the EXE. However, friends informed them that their Twitter account had been hijacked a few hours later.
NFT God had no idea that this was probably data-stealing software that had taken their saved browser passwords, cookies, Discord tokens, and cryptocurrency wallets and delivered them to a distant attacker.
Later, the influencer would find that their OpenSea account has also been compromised by the info-stealing malware, and a different wallet was listed as the owner of one of their digital assets. Their Gmail, Substack, Discord, and cryptocurrency wallets also fell under the hackers’ control.
Malicious Ads In Google Search Results
BleepingComputer conducted an investigation to find out if the case was isolated or not. The research revealed that OBS is one of several software that threat actors pretend to be in order to promote malicious downloads in Google Ads search results.
A Google Ad search result for Rufus, a free tool for making bootable USB flash drives, is one example BleepingComputer’s team identified. Threat actors duplicated the majority of the authentic site up to the download section by registering domains that seem similar to the official one.
They attempted to entice victims by promising a larger range of program features in one instance, using the generic top-level domain “pro”.
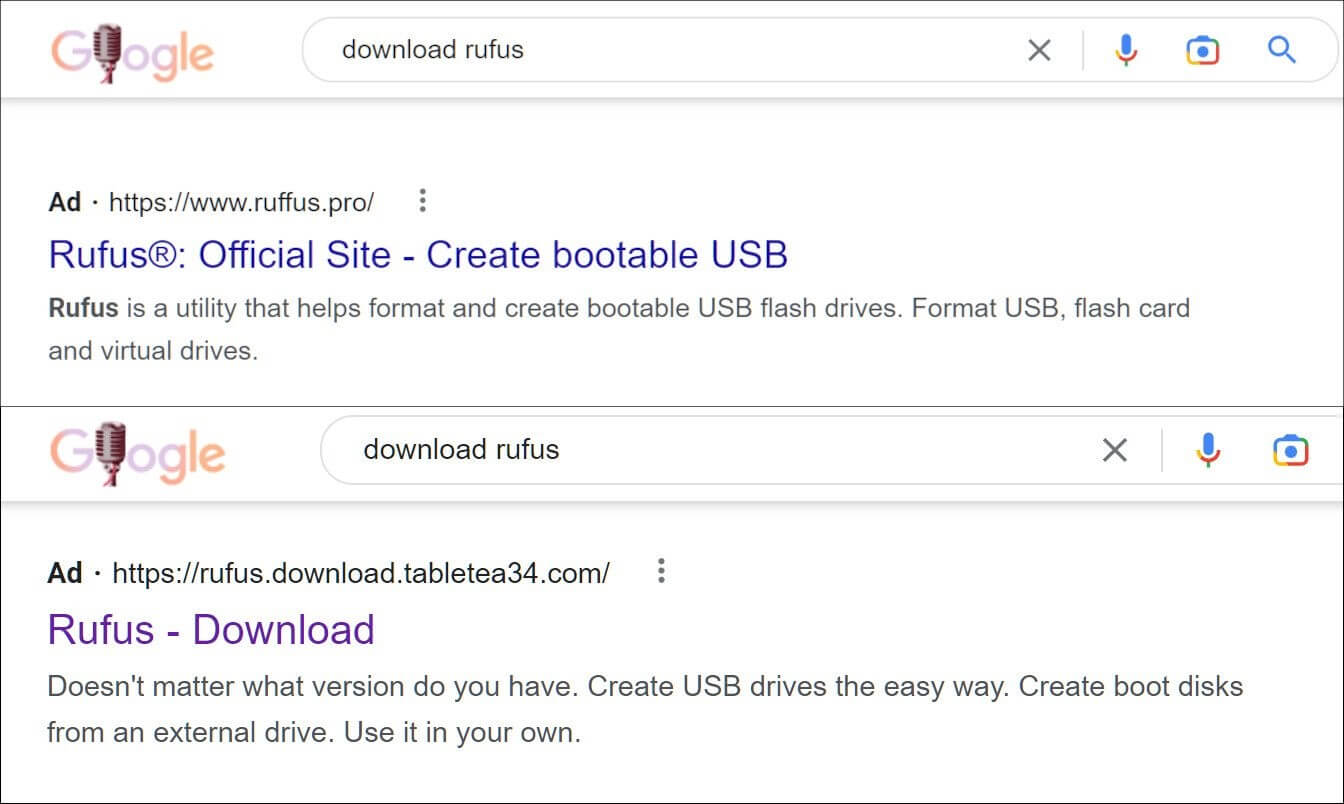
Malicious Rufus downloader pushed by Google Ads (Source: BleepingComputer)
The text and source code editor Notepad++ is another well-known application that is imitated. The threat actor created a domain that was similar to the actual one from the official developer via typosquatting.
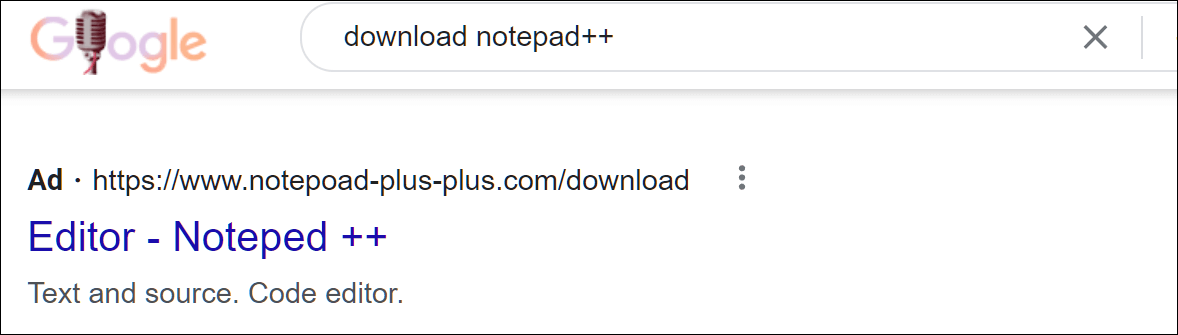
Fake Notepad++ Download Link (Source: BleepingComputer)
Additionally, a website offering bogus software downloads that are only offered through Google Ads search results was discovered. The website pretends to be Zensoft Tech, an allegedly authentic web design firm in India. Unfortunately, the downloads couldn’t be verified if they were malicious but given that the domain is a typosquatted URL we can assume so. There is clear evidence of fraudulent activity when a website prevents search engines from indexing material and promotes downloads only through adverts in search results. Some of the software discovered on the website are malicious copies of popular software WinRar, 7-Zip, and VLC.
A malicious version of the CCleaner software was found advertised from a different domain. It appears that the hackers tried to outbid the legitimate developer in order to place their ad above everyone else’s. The legitimate CCleaner website is shown underneath the fraudulent advertisement, as can be seen in the image below. This website provided a CCleaner.zip file that installed the data-stealing malware RedLine.
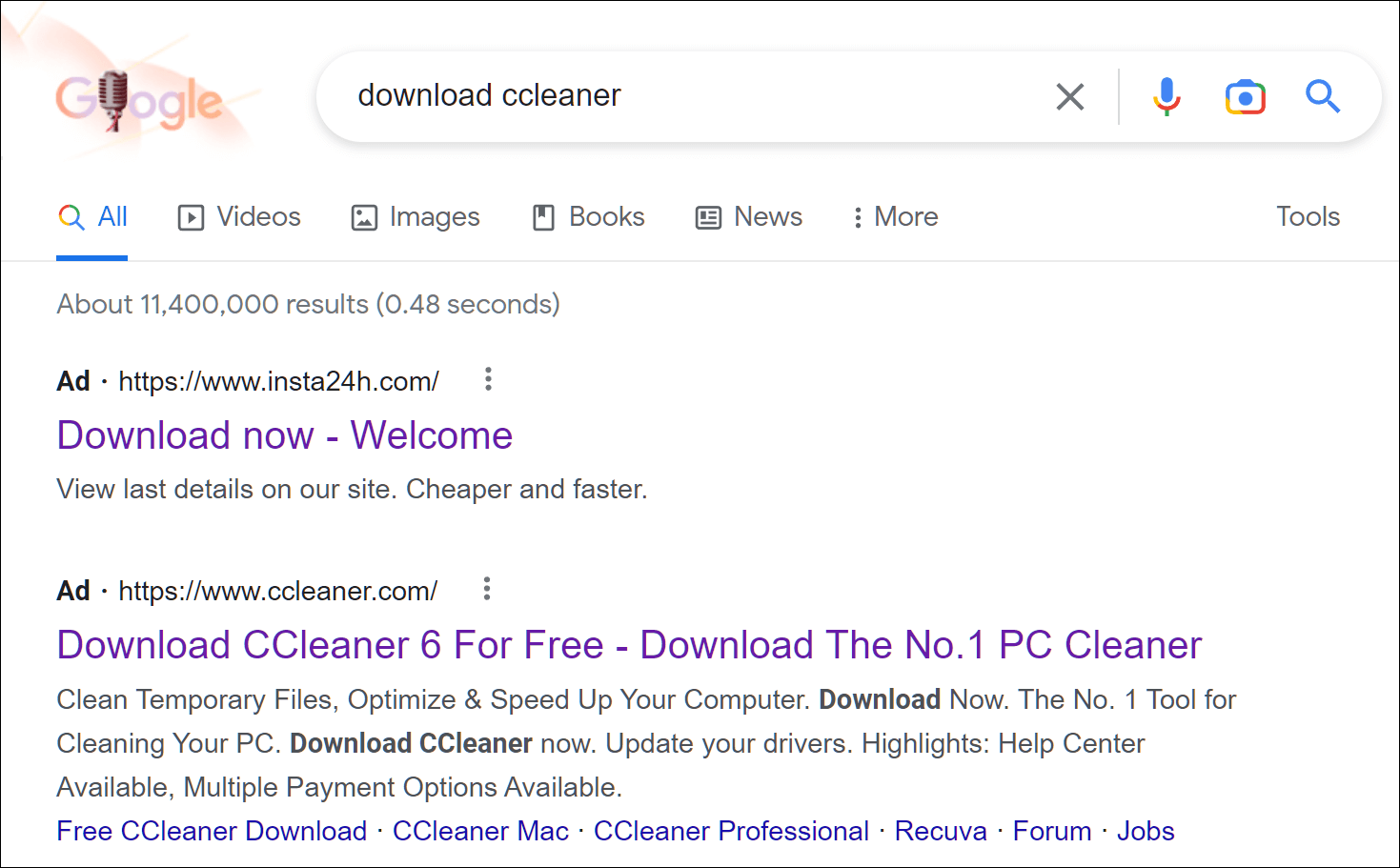
Malicious CCleaner downloader pushed above the legitimate software via Google Ads (Source: BleepingComputer)
Although BleepingComputer was unable to verify the malware sent in every instance, in some cases the payload was the RedLine Stealer that we observed on the bogus CCleaner website. This malware gathers private information from browsers, such as usernames, credit card numbers, and information from autocomplete fields, as well as information on the system’s hardware, location, and security software.
Another cybersecurity expert, Germán Fernández discovered that one threat actor used phony downloads for the Audacity digital audio editor to spread the .NET-based remote access trojan SectoRAT, also known as Arechclient2.
The researcher also discovered the malicious Blender 3D downloads promoted in Google Search that delivered the Vidar information-stealer. Vidar specializes in gathering private data from browsers and has the ability to steal cryptocurrency wallets.
To avoid being a victim of this amplifying operation, check thoroughly the URL of a download source. Additionally, installing an ad-blocker should increase the level of protection against this type of threat exponentially.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










