Contents:
If you’ve used to store your credentials in the browser, you might want to consider it twice! An information-stealing malware dubbed RedLine is targeting browsers like Chrome, Opera, or Microsoft Edge.
The researchers at AhnLab ASEC, who wrote a report about this, describe it as follows:
Redline Stealer is an infostealer that collects account credentials saved to web browsers, which first appeared on the Russian dark web in March 2020. A user under the name of REDGlade uploaded a promotional post explaining the various features included in Redline Stealer and selling the hacking tool for $150-$200.
How RedLine Works
As per BleepingComputer, RedLine targets a file called “Login Data” present on all Chromium-based web browsers. This represents basically an SQLite database that serves the purpose of credentials storage (username and password).
Even if users do not choose to store their credentials in the browser, an entry will still be added by the password management system that will point out that that certain website is “blacklisted”. Even if the hackers will not have access to the “blacklisted” account’s passwords, this will be a hint for them about the existence of such an account, meaning that they can decide to perform social engineering/phishing attacks or credentials stuffing attacks.
After the collection of credentials happens, cybercriminals can do two things with them: either use them to perform further cyberattacks or make money out of them on the web market.
What Information Does RedLine Collect?
In the same report, the AhnLab ASEC researchers provided a sketch with the main features of ReadLine Stealer emphasizing the information it collects:
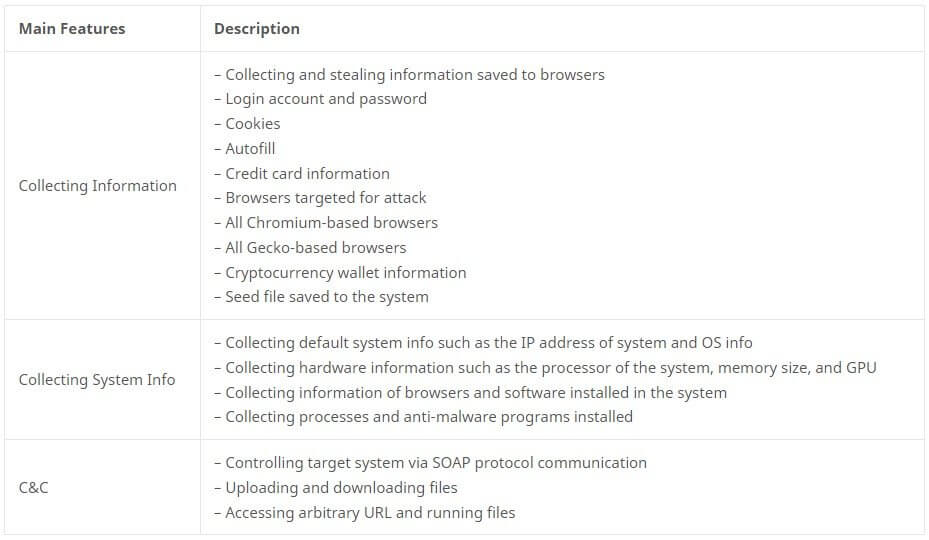
Redline Malware Examples
The experts also depicted a case on how the hackers behind RedLine managed to hack a company’s network by means of the VPN credentials of a remote employee.
The company where the damage occurred provided VPN service to employees who were working from home to give access to the company’s internal network, and the employees connected to the VPN on the provided laptops or their PCs. The targeted employee used the password management feature provided by the web browser to save and use the account and password for the VPN site on the web browser. While doing so, the PC was infected with malware targeting account credentials, leaking accounts and passwords of various sites, which also included the VPN account of the company. The leaked VPN account was used to hack the company’s internal network three months later.
Another case where RedLine was involved and that we wrote about at the beginning of this month is when hackers used Excel XLL files and distributed them through a website contact form spamming campaign. This had the role to install and download the RedLine malware by means of website contact forms or conversation forums.
How to Stay Safe
As you can see, storing your credentials in the browser poses a security risk that might even lead to a breach of the corporate network. That’s why it’s better to avoid this, even if it represents a convenient solution. A password manager would be useful in this case, as passwords can be kept in a vault that is encrypted and its unlocking can be done only with the master password. Multi-Factor Authentication (MFA) might be yet another prevention solution.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










