Contents:
Organizations face an ongoing battle to protect their sensitive data and critical infrastructure in today’s increasingly sophisticated digital world. Security Information and Event Management (SIEM) has emerged as a powerful solution to help businesses detect and respond to security incidents effectively. Managed SIEM takes this concept a step further by providing outsourced security monitoring and management, allowing organizations to focus on their core operations while leveraging expert support to safeguard their digital assets. In this article, we will explore the world of Managed SIEM, its benefits, and how it works to fortify businesses against the ever-evolving threat landscape.
SIEM Overview
SIEM, an acronym for Security Information and Event Management, is a comprehensive approach that combines Security Information Management (SIM) and Security Event Management (SEM) functionalities. SIM involves collecting, analyzing, and correlating data from sources such as network devices, applications, and servers, while SEM focuses on real-time monitoring and alerting based on predefined rules. SIEM provides organizations with valuable insights into their security posture, helping them detect potential threats and respond swiftly.
SIEM Functions
A SIEM tool pulls log data from across the organization’s entire IT environment and consolidates it within a central platform for analysis and response. This can be achieved either through agents installed on infrastructure endpoints or physical/virtual machines deployed within the network, which act as log collectors.
Within the central platform, the log data is categorized into various security event types, such as malware, unsuccessful logins, suspicious devices, and other potential breach activities. When a threat is detected, an alert is generated, accompanied by a defined threat level based on predetermined rules. In this way, SIEM detects threats and creates security alerts.
The immense volume of data generated in an IT environment makes manual monitoring virtually impossible for a human alone. SIEM platforms take on the task of sifting through this data, differentiating between suspicious and normal activities.
If an activity is deemed suspicious, the SIEM software flags it for further investigation by a security analyst. This process helps security teams develop detection use cases to pinpoint attacks and respond to threats more rapidly.
Key Functions
- Collect: Gather data from infrastructure, devices, applications, and users across both on-premises and cloud environments.
- Detect: Identify threats while minimizing false positives.
- Investigate: Utilize business rules and pattern recognition to distinguish malicious activity from legitimate actions.
- Respond: Take appropriate actions and respond to incidents using automated responses, escalating when necessary.
The Evolution of Managed SIEM
Managed SIEM takes the foundational principles of SIEM and extends them by introducing a managed service provider (MSP) to handle the deployment, configuration, monitoring, and maintenance of the SIEM solution. This approach alleviates the burden on organizations to build and maintain an in-house security operations center (SOC) while benefiting from the expertise and resources of the MSP.
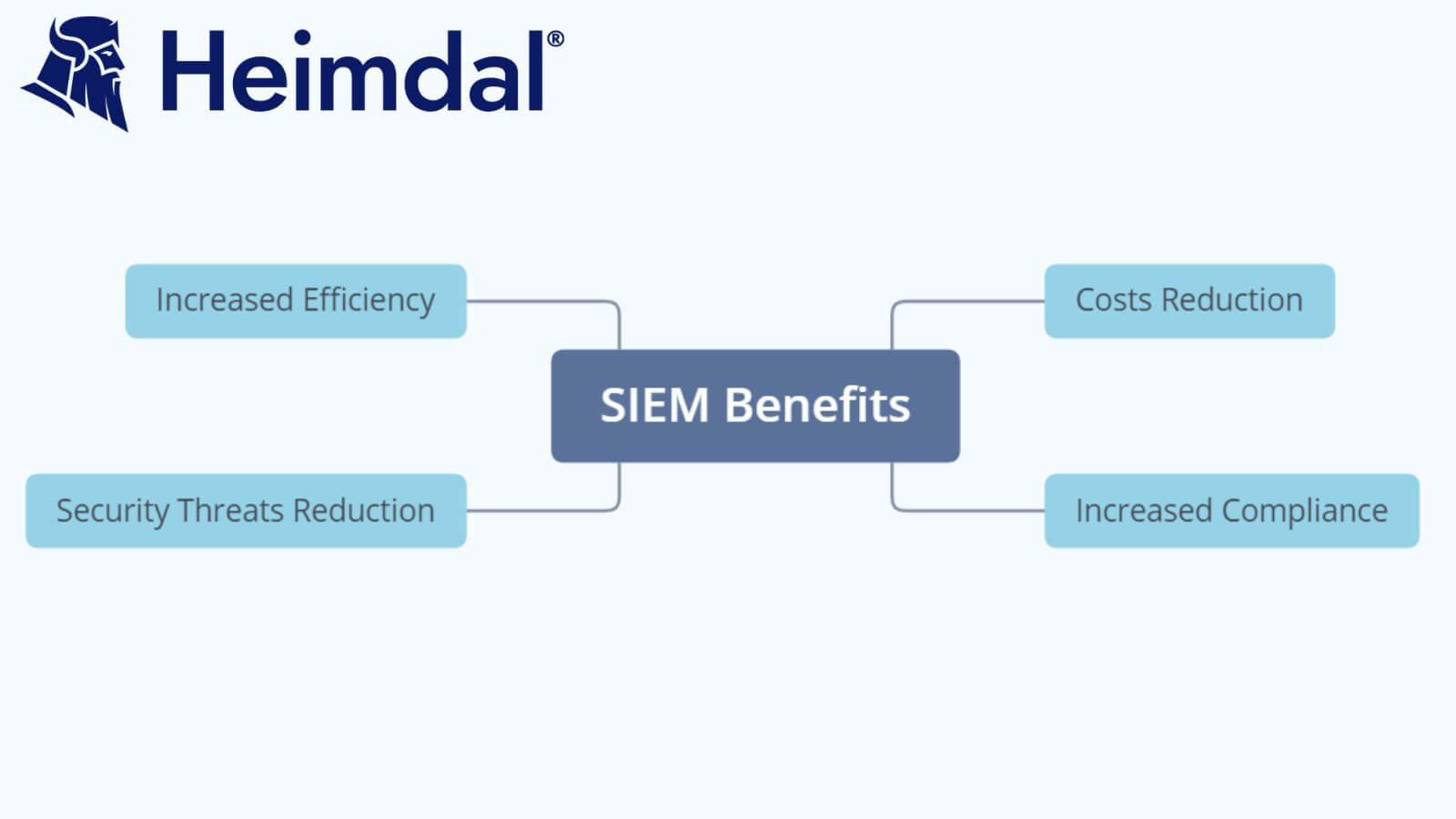
Key Benefits of Managed SIEM
- Enhanced Threat Detection and Incident Response: Managed SIEM combines advanced analytics, machine learning, and threat intelligence to identify suspicious activities and potential security incidents in real-time. By continuously monitoring and analyzing log data, it enables rapid incident response and reduces the time to detect and mitigate threats.
- Proactive Security Monitoring: MSPs employ dedicated security experts who continually monitor the SIEM environment, ensuring that any security events are promptly identified and addressed. This proactive approach enables organizations to stay one step ahead of cyber threats.
- Access to Security Expertise: Managed SIEM provides access to skilled security professionals who possess in-depth knowledge of the threat landscape and the latest security technologies. This expertise proves invaluable in fine-tuning SIEM rules, responding to incidents, and conducting forensic investigations.
- Cost-effectiveness: By outsourcing the management of the SIEM infrastructure, organizations can avoid significant upfront investments in hardware, software licenses, and personnel training. Managed SIEM services typically follow a subscription-based model, allowing businesses to scale their security operations without substantial capital expenditures.
- Peace of Mind: By outsourcing threat monitoring to a reputable managed service provider, organizations can gain peace of mind knowing that their security is in capable hands. Effective security tools operated by skilled professionals offer assurance that the organization’s digital assets are being protected.
How Managed SIEM Works
1. Initial Assessment and Deployment
The MSP conducts an assessment of the organization’s security requirements, infrastructure, and compliance needs. Based on this evaluation, they deploy and configure the SIEM solution, integrating it with existing security tools and data sources.
2. Continuous Monitoring
The MSP continuously monitors the SIEM environment, collecting and analyzing security event data from various sources. This includes log files, network traffic, and endpoint activities. Suspicious events trigger alerts and notifications for further investigation.
3. Incident Response and Remediation
When a potential security incident is detected, the MSP’s security analysts investigate the issue, classify its severity, and initiate an appropriate response plan. They work closely with the organization’s internal IT team to contain and remediate the incident, minimizing the impact on operations.
4. Reporting and Compliance
Managed SIEM generates comprehensive reports on security events, incidents, and trends. These reports aid in compliance with regulatory requirements and provide organizations with insights into their security posture and areas for improvement.
Why Choose Managed SIEM?
Implementing and maintaining an in-house SIEM solution can be a costly endeavor, both in terms of the SIEM tool itself and the recruitment and training of skilled analysts required for its monitoring. While larger companies may have dedicated internal teams to handle this, it is often unrealistic for smaller to mid-sized organizations to maintain an in-house SIEM team.
However, the need for security benefits provided by SIEM is crucial, especially considering the high number of attempted attacks on SMEs. Therefore, many organizations opt for a Managed SIEM approach as their preferred route to obtaining effective security measures.
Finding the Right SIEM
When selecting a SIEM tool that aligns with your organization’s needs, it is essential to assess whether the potential Managed Service partner’s chosen SIEM solution offers the following capabilities:
- Real-Time Monitoring and Alerts: Effective SIEM solutions should provide real-time monitoring and instant alerts. The ability to detect and respond to events as they occur is crucial, as attackers can swiftly maneuver through a network once inside.
- User Activity Monitoring: Not all threats originate from external sources. Internal user errors or misuse of privileges can lead to breaches. A robust SIEM should offer comprehensive visibility into user activity, enabling the prompt identification of potential risks.
- Comprehensive Threat Detection: Your chosen SIEM should have the capability to process and analyze data from all relevant sources in your environment, including databases, applications, devices, and web services. This ensures holistic threat detection across the entire infrastructure.
- Efficient Log Storage: SIEM solutions generate vast amounts of data, and certain industries may have legal requirements to retain specific log data. It is crucial to verify whether the SIEM can store the necessary data while excluding irrelevant information to optimize storage usage.
- Scalability: Businesses undergo changes and growth over time, which impacts data processing requirements. Ensure that the chosen SIEM solution offers scalability, allowing it to accommodate fluctuations in data volume effectively as your organization evolves.
- Seamless Integrations: Most organizations operate a diverse range of security systems, often leading to challenges in effective communication and information sharing among these systems. A suitable SIEM should seamlessly integrate with various security solutions, enabling comprehensive data aggregation and correlation.
- Robust Reporting Capabilities: Regular and relevant security reports are essential for compliance purposes, both for auditors and executives. A reliable SIEM should facilitate contextual report exports, saving time and effort in generating compliance reports that demonstrate adherence to multiple regulations.
By evaluating these critical factors, you can make an informed decision when selecting a SIEM solution that best suits your organization’s unique requirements. Collaborating with a Managed Service Provider that offers a SIEM solution with these capabilities ensures a more robust and efficient security infrastructure.
Conclusion
In an era where cyber threats are becoming increasingly sophisticated, businesses must prioritize proactive security measures to safeguard their digital assets. Managed SIEM offers a compelling solution by combining advanced security analytics, expert resources, and continuous monitoring to detect and respond to security incidents effectively. By partnering with a trusted MSP, organizations can enhance their threat detection capabilities, streamline incident response, and stay resilient against evolving cyber threats. Embracing Managed SIEM empowers businesses to focus on their core operations, confident that their security is in capable hands.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.

- Granular telemetry across endpoints and networks.
- Equipped with built-in hunting and action capabilities.
- Pre-computed risk scores, indicators & detailed attack analysis.
- A single pane of glass for intelligence, hunting, and response.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security