Contents:
You probably spend most of your time on a PC browsing, whether that is Facebook, news or just blogs or pages that appeal to your particular interest.
If a malicious hacker wants to break into your computer and scramble the kilobytes that make up your digital life, his starting point will be to create a malicious website infected with malware or compromise an existing one to carry out the task.
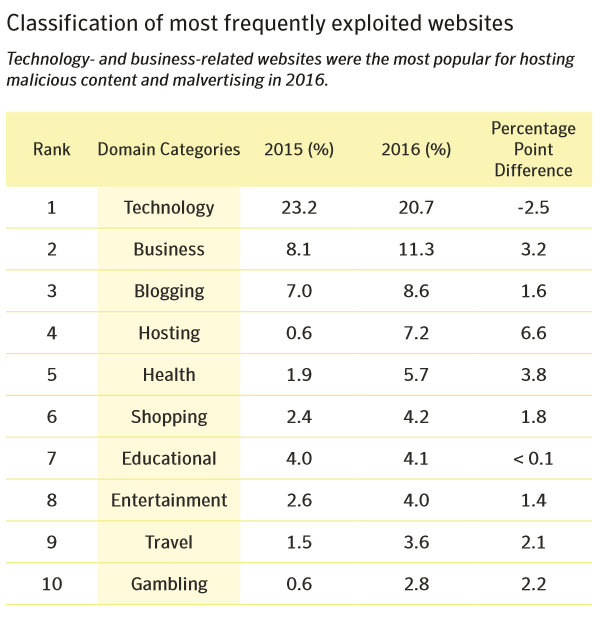
The most common types of websites infected with malware
You might think you don’t need to worry about phishing websites and the like because you only browse on safe and reputable pages such as Wikipedia.org or CNN.com.
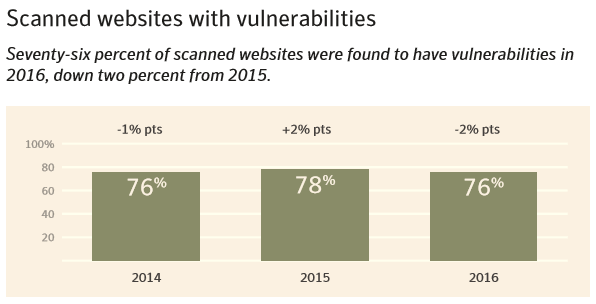
But 76% of these contain a vulnerability.
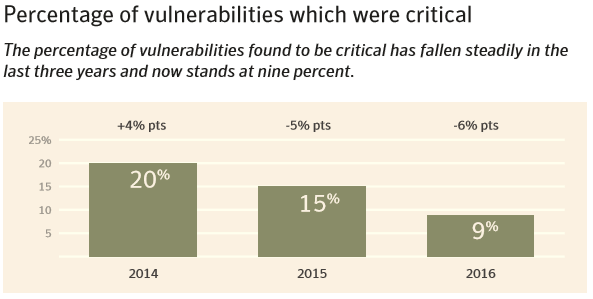
To make matters even worse, 9% of sites contain a vulnerability that is serious in nature, which would allow an attacker to infect a visitor’s PC, download malware, or even execute code on it.
So 1 out of every 11 sites you visit has such a critical vulnerability. Chances are you visit 11 new sites every week.
[Tweet “1 out of every 11 websites has a critical vulnerability. Here’s why that’s important.”]This chart below shows you the most frequently exploited types of websites. Most of them are general use that almost every user visits.
Our own experience with malicious websites
At Heimdal Security, we’ve dealt with this kind of site frequently enough to notice patterns when it comes to user infections.
1. Gambling, porn, gaming, and video streaming sites are the most frequent targets
You’ve probably dealt with these kinds of sites yourself. You visit a torrenting page, click on a link, and then 2-3 browser windows will pop-up in the background.
In other cases, you’ll get popups that ask you to download a new software or browser extension
These sites run on only two things: traffic and ad clicks. To maximize both, they will use shady software and ad networks in order to extract as many clicks as possible from you, the end user.
With just a handful of exceptions, this kind of online businesses have few economic incentives to keep their infrastructure safe, so they just use whatever software plugins are available to maximize traffic and user clicks. Malicious hackers will then exploit these weak plugins to infect the ads or popups, which in turn infects you, the end user.
2. Drive-by-downloads and similar threats are the majority of attacks that we block
Most of the malware threats that our products block are specifically designed to bypass clicks, and instead install themselves automatically on the users system. These types of drive-by-downloads are popular because they bypass an extra obstacle: the click.
By cutting down on that extra click, drive-by malware can infect ten or twenty times more users, meaning ten or twenty times the revenue.
3. Future trends
Due to their relative simplicity and straightforwardness, web-based attacks are only going to increase in the future.
Web applications, in particular, are prime targets, since they often process user information such as credit cards, log in details, files stored on the cloud and then spread to multiple machines.
How a phishing or malicious website compromise your PC
Most people think they can avoid infecting themselves with malware simply by avoiding clicks on strange links or refusing to download programs from suspicious sites. Well, they are in for a rude awakening, since there’s more than one way of infecting a visitor that doesn’t require him clicking on anything.
Websites infected with malware
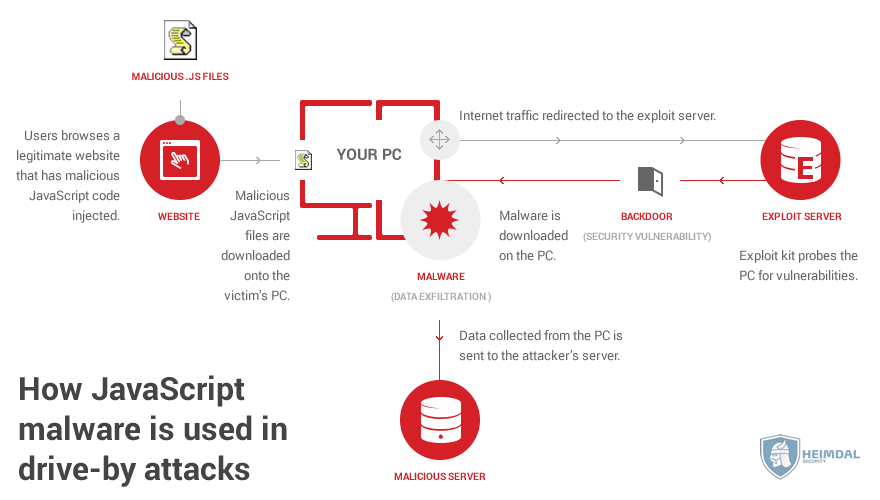
1. Exploit kits and drive-by-downloads
A drive-by-download works by automatically downloading malware on your computer when you visit a certain page. The malware downloads and installs itself without asking you for permission at any point.
How is it able to do that?
Exploit kits and outdated software. An exploit kit hides insides pages, scanning the computers of visitors, looking for any outdated software and vulnerabilities it might contain.
Once it finds a vulnerability, it downloads malware on the victim’s PC that is specifically designed to exploit that particular vulnerability.
2. JavaScript infections
JavaScript is the programming language that holds up a huge part of the Internet, such as Google Docs and many other web applications. Like any software technology, however, it comes with bugs and vulnerabilities that allow malicious hackers to misuse it.
Similar to exploit kits, pages infected with JavaScript malware will infect you by downloading a .js file, which your browser then executes.
Once on your computer, the malware will run code that can download other kinds of malware, or redirect your computer to other Internet locations.
3. Malvertising
Ads are everywhere these days, and there’s little chance of them stopping to multiply.
Ad networks are responsible for feeding these to user’s computers, and the big ad campaigns can reach millions of users.
This presents a convenient target for malicious hackers, who can hijack one of these ads, and then have the ad network spread it far and wide, infecting unsuspecting users that click on these.
Other times, the malicious hacker might set up his own ad. The first version is usually clean and malware free, but he later modifies the ad and targets it to one of his malicious websites.
To give you an idea of widespread this phenomenon is, check out this article by Google that presents just how many bad ads it blocked in the past year.
4. URL Injections
WordPress is the software that underpins nearly 60% of the blogs and websites out there, far outranking its competitors. Unfortunately, the architecture of WordPress, coupled with vulnerabilities and exploits allow an attacker to embed malicious URLs or even entire pages, all spread through the victimized page.
These URLs and pages can execute code on your PC, redirect you to other malicious websites or phishing websites, or download malware.
5. Malicious redirects
If a malicious hacker manages to successfully breach your site, he can alter its code so that it automatically redirects a user to a page of his choosing, which is usually infected with malware or phishing forms.
A redirect checker is a very useful tool in helping you discover this type of malicious behavior.
6. Browser hijackers
Some sites can infect you with browser hijackers – malware designed to compromise your browser so it can constantly redirect you to other pages, collect personal information, or act as gateways to rootkits or worms.
What are phishing websites
Another type of threat that malicious hackers use is phishing websites. Unlike the malware infection methods above, phishing relies on social engineering so that the user willingly gives his information to the cybercriminal.
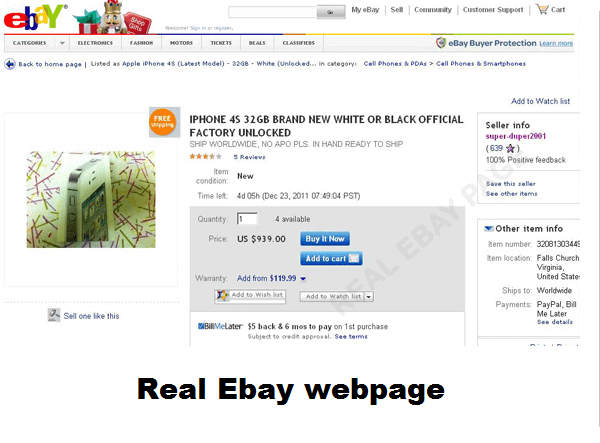
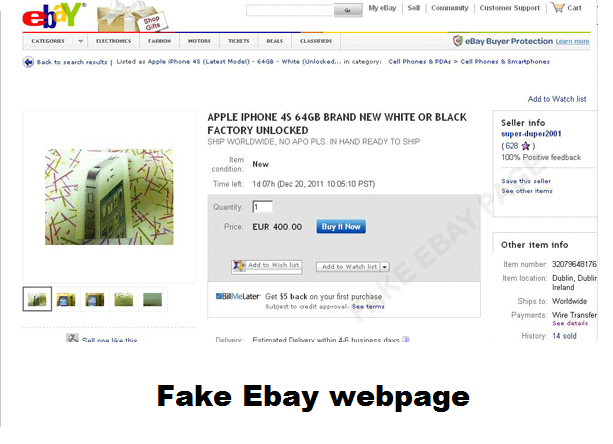
It can be tricky to detect phishing sites since they frequently look like a clone of a legitimate one. Online stores such as Amazon or eBay are prime targets, since users who visit those sites already have an intention to buy stuff, and most of them do that by using their debit card.
Here is a comparison between a fake eBay page, and the real thing.
Here are a few examples of various types of phishing websites, and how they work:
1. Typosquatting
Whenever you enter the name of web page manually in the search bar, such as www.example.com, chances are you will make a type, so that you end up with www.examlep.com .
A malicious hacker will exploit these small mistakes in a process called typosquatting. This involves creating phishing websites with similar names to the target site, hoping that users who manually type in the address will make a mistake and end up on the cybercriminals page.
Once there, he can infect you in any number of ways we’ve outlined above.
2. Domain shadowing
During domain shadowing, a malicious hacker will break into the login credentials of site administrators, such as WordPress owners, and then create subdomains that redirect visitors to the malicious hacker’s own page.
Not only will domain shadowing redirect users from a legitimate domain to a malicious one, but it will also bypass reputation-based filters, and make its traffic seem as legitimate.
3. Website spoofing
Site spoofing is extremely similar to general phishing. The major point of differentiation is in the purpose behind it.
Just like its bigger cousin, a malicious hacker who spoofs a site will practically clone an already existing one in order to trick users into confusing the two. However, the endpoint this time isn’t what you might call harmful criminal activity. Instead, the spoofer wants to create mischief and confusion, or potentially brand damage.
How to check a website for malware or phishing attempts
The best way to protect yourself from malicious and phishing websites is to know how to detect one and also, to be prepared and have all the tools you need in case still end up on one. Here are some useful tips that can help you with that.
1. Check if the page’s URL is genuine
Phishing websites, in particular, will use URL structures that are similar to the target webpage. For example, the link name might be www.facebok.com instead of www.facebook.com.
For this reason, we strongly suggest you always glance at a page’s URL and check for anything out of the ordinary.
2. Most malicious websites don’t use SSL or HTTPS
SSL, short for Secure Socket Layer, is a security certificate used in order to encrypt the communication sent between the browser and the site server.
Malicious websites, and even phishing ones for that matter don’t use SSL since they are an extra cost and hassle.
Whenever you land on a new site you haven’t heard about, look at its URL structure and see if it starts with “https://” , if it does, then it means the site is secure, and the communications sent between your browser and server are encrypted.
If it starts with “http://” , then the site owner hasn’t acquired an SSL certificate, which should put you on your guard when doing business on that page
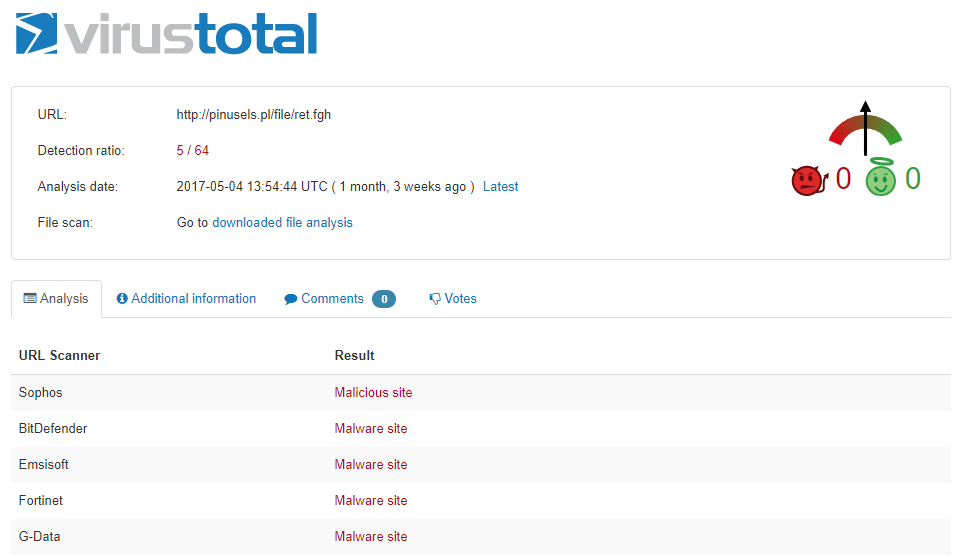
3. VirusTotal will scan the website and tell you if it’s malicious or not
VirusTotal is a free service that analyzes a URL link or file with dozens of antivirus programs, looking for malware or malicious links.
Whenever you are unsure if a site is safe or not, you can simply pop it into VirusTotal’s URL scan, and see if anything suspicious come up.
It’s very easy to use, and best of all, free.
4. Web of Trust is a community-based filter that helps you detect a malicious website
Web of Trust by myWOT is a browser extension that brings together millions of users who rate the trustworthiness of a site. This gives you a crowdsourced database of which sites are safe to visit, and which aren’t.
Once you visit a site with a poor reputation, WoT will notify you so you can be on your guard.
IMPORTANT NOTE: Before you download the extension, however, it’s fair to warn you that myWOT was embroiled in a scandal some months back for not properly anonymizing user data, which caused it to be taken down for Chrome and Firefox.
Since then, the extension has been republished on both stores so we can assume they’ve straightened up their act.
5. Use an ad blocker
If you are concerned about malvertising and other malicious ads, you could consider installing an ad blocker. This will prevent almost all types of ads from appearing on pages you visit, including malicious ones.
Here’s a link that compares ad blockers, in case you would like an in-depth review of them.
6. Keep all of your software updated
Malicious websites with exploit kits embedded into them will hunt down vulnerabilities in your software, which then function as gates for more types of malware infections.
Keeping your software updated at all times can be a serious hassle that involves too many update pop-ups. For this reason, we suggest you use Thor FREE, a security tool that automatically updates your software without bothering you about it.
7. A traffic filtering solution can protect you from malware infected websites
Traffic filtering programs will scan both incoming and outgoing traffic to/from your PC. For incoming traffic (HTTP, HTTPS, DNS), it looks for known and unknown types of malware that seek to infiltrate the computer and blocks them once they are discovered.
For outgoing traffic, the filter will seek information packets your computer sends to known malicious websites, or other sites that act suspiciously, and then cuts the communication between your computer and the site’s server.
A good fit for this would be Heimdal™ Threat Prevention, a next-generation antimalware tool that stops malware from landing on your PC in the first place.
8. Beware of shortened links
Malicious hackers user URL shorteners such as bitly or TinyURL, to disguise links to malicious websites by masking them. In other cases, URL shorteners will obfuscate the original link, so that antivirus or other security solutions have trouble detecting the malware hidden on the page.
Fortunately, there are dedicated tools that can check these shortened links to make sure you won’t end up somewhere you wish you hadn’t.
Here’s a short list of URL checkers to help you out:
- http://www.checkshorturl.com/
- http://www.getlinkinfo.com/
- http://untiny.com/
- http://www.linkexpander.com/
The cost of an infection from a compromised site
The malware that can spread from compromised and infected pages has a real, monetary impact on both companies and regular users.
Malvertising on these malicious websites is cheap. With just $0.36, a cybercriminal can infect around 1000 users with malware of any kind.
Ransomware, which at the moment is a favorite among cybercriminals, is so effective that more than 50% of infected businesses end up paying between $10,000 to $40,000 to recover their encrypted files. For consumers, the recovery price can vary from $200 to $10,000. To make matters worse, 1 out of 4 paying users don’t recover their data.
We spend most of our time on the internet browsing, and this exposes us to malware infections you didn’t even think were possible.
Have you ever suffered infection by visiting a suspicious or malicious page? If yes, how did it end up for you?











 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security