Contents:
In operation since 2020, the Makop ransomware gang is classified as a tier-B ransomware gang. The threat actor has successfully targeted companies in Europe and Italy with its hybrid arsenal of custom-developed and off-the-shelf software tools despite its low classification.
The Makop ransomware operators started their criminal business back in 2020, leveraging a new variant of the notorious Phobos ransomware. Even though the gang did not engage in double extortion during the last years, it maintained a solid presence in the criminal underground. The majority of the intrusion is handled by hands-on keyboard criminals, even during encryption.
Detailed Findings
According to cyber security researcher Luca Mella, Makop ransomware gang has been found to be using a set of custom-developed tools in their campaigns. Among them is a tool called ARestore that was built in 2020 and partially obfuscated.
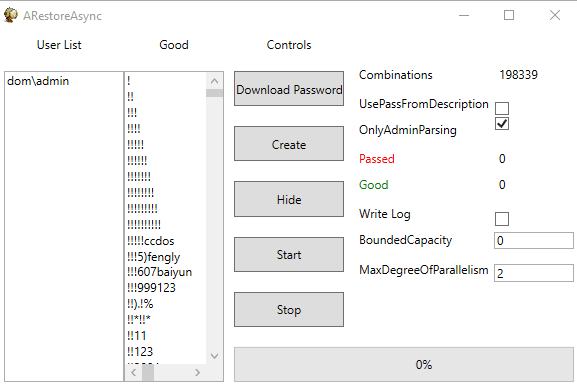
This tool generates comb lists of local Windows usernames and potential passwords and tests them locally. The APT use it after the initial access phase of their attack chain.
Additionaly, the operators leverage other custom .NET assemblies, PuffedUp for example, to achieve further stages of the kill chain.
This particular tool is designed to ensure persistence after the initial access. It relies on a textual configuration file placed in the same folder, containing one or more 42-character strings that will be placed into the user clipboard.
Furthermore, the ransomware gang is also using off-the-shelf open-source and freeware tools to conduct lateral movement and system discovery.
Along with the abuse of Microsoft SysInternal tools such as PsExec and other well-known open-source tools such as Putty and Mimikatz, Makop has abused even more peculiar software.
- The attackers recently used Advanced Port Scanner and the Windows Everything tool.
- Another unique tool used by the group includes a system administration tool called YDArk. It is an open-source tool available on GitHub.
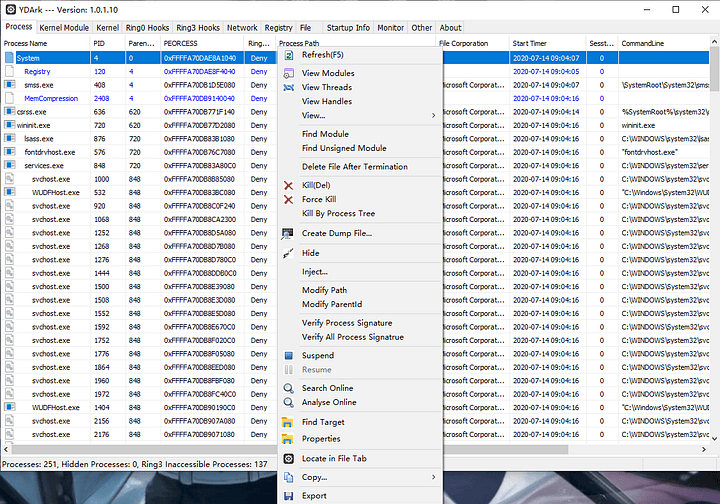
The Makop ransomware gang has an arsenal of both custom-developed and off-the-shelf software tools at its disposal. The use of these tools is a clear indicator of the evolving techniques cybercriminals use to conduct digital extortions. In order to defend themselves against Makop ransomware attacks, organizations need to conduct regular security audits and keep their software up to date.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










