Contents:
A new wave of ransomware attacks is targeting ESXi hypervisors. VMware ESXi is a hypervisor developed by VMware that is enterprise-class and type-1. It is used to install and maintain virtual machines.
A patch for CVE-2021-21974 has been available since February 23, 2021, the Computer Emergency Response Team (CERT) of France said in an advisory on Friday.
At the time, VMware described the vulnerability as an OpenSLP heap-overflow vulnerability that could allow arbitrary code to be executed.
According to the virtualization services provider, “A malicious actor within the same network segment as ESXi who has access to port 427 may be able to trigger the heap-overflow issue in OpenSLP service and execute remote code.”
According to French cloud services provider OVHcloud, the intrusions have been detected globally, focusing on Europe. The intrusions are thought to be linked to a new Rust-based ransomware strain called Nevada that emerged in December 2022.
Ransomware families that have embraced Rust in recent months include BlackCat, Hive, Luna, RansomExx, and Agenda.
The actors are inviting Russian- and English-speaking affiliates to collaborate with a large number of Initial Access Brokers (IABs) in the dark web.
In addition to buying compromised access, the Nevada Ransomware group has a dedicated team for post-exploitation and intrusion into target networks.
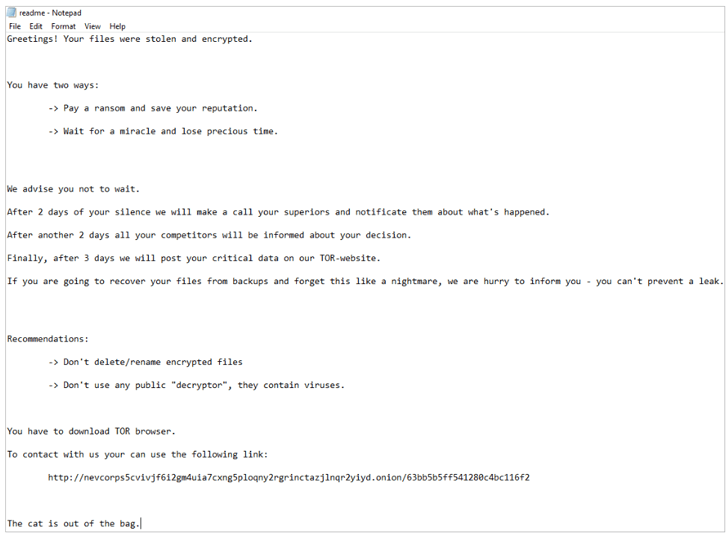
However, the ransom notes seen in the attacks do not resemble Nevada ransomware, and the strain is known as ESXiArgs.
To mitigate potential threats and restrict access to OpenSLP to trusted IP addresses, users should upgrade to the latest version of ESXi.
The Latest Update
Over the weekend, OVHcloud confirmed that the ransomware attacks used OpenSLP as a compromise vector. However, at this point, it cannot guarantee that it involved the abuse of CVE-2021-21974. In addition, the company reiterated that Nevada ransomware was not linked to the intrusions.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
How Can Heimdal Help?
Keep your servers protected by all means with the Ransomware Encryption Protection module by Heimdal®, which provides its customers with an exceptional integrated cybersecurity suite and is 100% signature-free and universally compatible with any antivirus solution, ensuring superior detection and remediation of all types of ransomware.
On another note, if you wish to learn more about ransomware prevention and mitigation, feel free to check out our in-depth articles, where we guide you in the fight against ransomware every step of the way.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








