Contents:
This year, many ransomware-as-a-service groups, including Agenda and Qilin, have developed versions of their ransomware in Rust. Like its Golang counterpart, the Rust variant of Agenda has targeted essential industries.
In the past month, Trend Micro has observed that the Agenda ransomware has posted information about many businesses on its leaked website.
In addition to claiming that they had hacked into these companies’ servers, threat actors threatened to leak their files.
Businesses listed on the leak site of the ransomware organization are primarily from the manufacturing and IT sectors, and their combined annual revenue exceeds US$550 million.
Targeting Major Sectors with Agenda Ransomware Using Rust
We found a sample of Agenda ransomware written in Rust language and detected as Ransom.Win32.AGENDA.THIAFBB. Notably, the same ransomware, originally written in Go language, was known for targeting healthcare and education sectors in countries like Thailand and Indonesia.
Previous versions were targeted ransomware attacks which aimed at the healthcare and education sectors in Indonesia, Saudi Arabia, South Africa, and Thailand.
As a new strategy to evade detection and speed up encryption, the Rust variant employs intermittent encryption.
The ransomware will drop its ransom letter onto each encrypted directory, and the password required to run it will also be used to access the ransomware group’s support chat website.
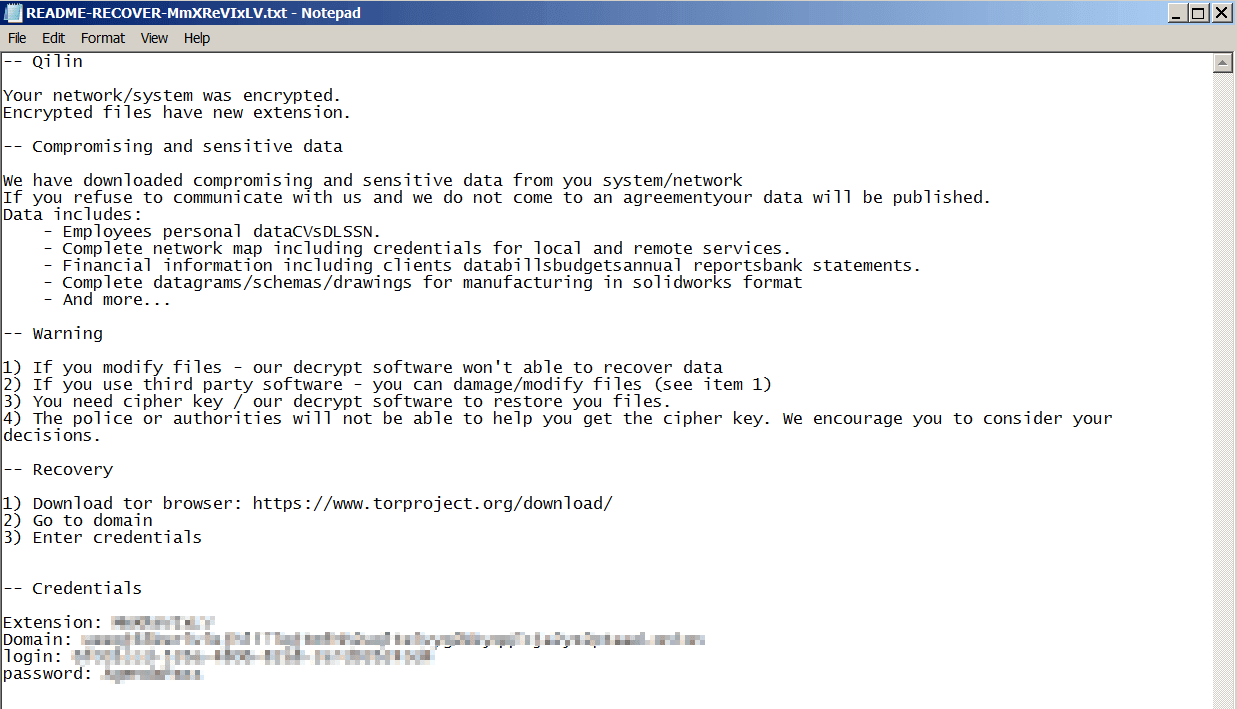
Agenda in Rust accepts only three arguments, compared to ten in Golang.
In addition to having a hard-coded configuration, the Rust variant also adds the -n, -p, fast, skip, and step flags. These flags are used for intermittent encryption.
As a result, the ransomware can encrypt the victim’s files more quickly using a partial encryption technique based on the values of the flags. Experts say this helps them encrypt faster and avoid detections requiring read/write file operations.
Furthermore, Agenda ransomware is also known for deploying customized ransomware for each victim. Its Rust variants have an allocation for adding accounts in their configuration to be used primarily for privilege escalation.
As ransomware continues to be used by threat actors, organizations and businesses must take a multilayered approach to data security.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










