Contents:
A new type of ransomware has been identified. Agenda is written in Go language (or Golang), a language more and more used by hackers because it’s stand-alone, integrating all the necessary libraries for running.
The malware strain using the double extortion technique is targeting healthcare and education companies in Indonesia, Saudi Arabia, South Africa, and Thailand.
How Does Agenda Work
It appears that the threat actor behind Agenda, named Qilin, can offer his collaborators tailored versions of this ransomware.
For each victim the hacker can decide on:
- the ransom notes
- the encryption extension
- the list of processes and services to terminate before commencing the encryption process.
“Agenda can reboot systems in safe mode, attempts to stop many server-specific processes and services, and has multiple modes to run,” according to Trend Micro researchers, the ones who discovered Agenda.
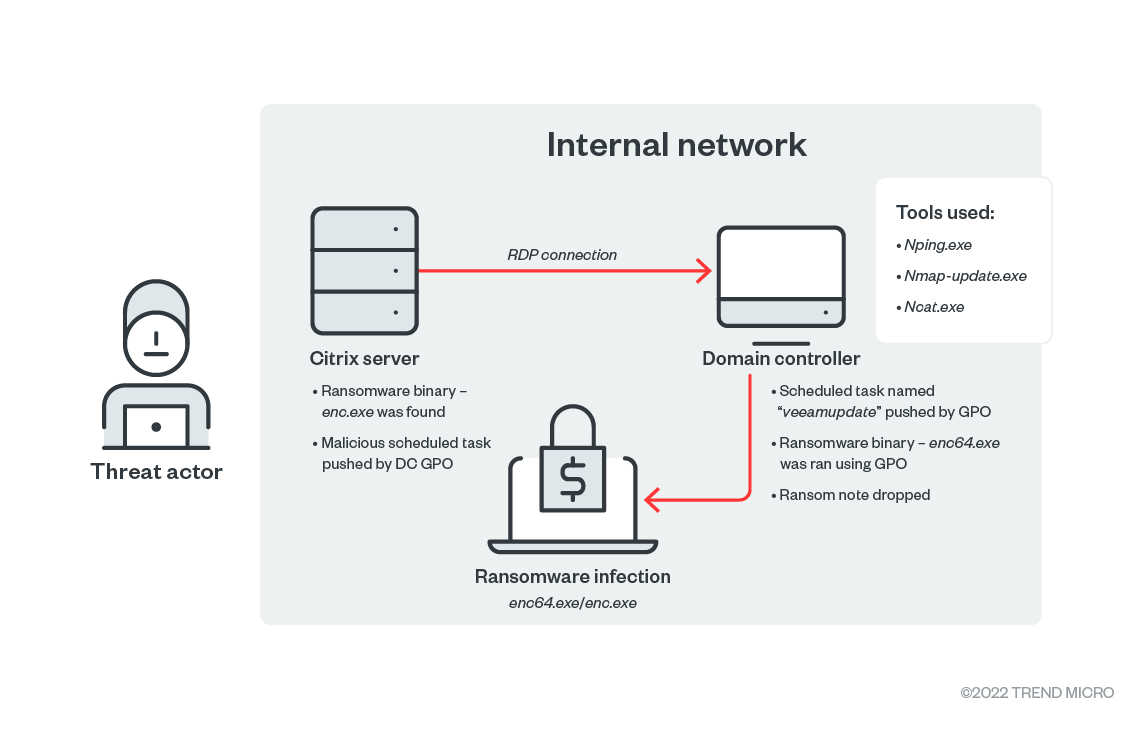
The ransomware also benefits from the machine’s safe mode feature to start its file encryption without being noticed. Before this, Agenda changes the default user’s password and allows the automatic login. All those above are detection evasion techniques that make it even harder to trace.
Upon successful encryption, Agenda renames the files with the configured extension, drops the ransom note in each encrypted directory, and reboots the machine in normal mode. The ransomware amount requested varies from company to company, ranging anywhere from $50,000 to $800,000.
The malware has the capability to infect an entire network and its shared drives in a short period of time. As an example, after attacking a Citrix server, Agenda used it as a starting place to spread the infection in less than two days.
Agenda vs. Other Ransomware
Researchers observed source code similarities between Agenda and other ransomware families like Black Basta, Black Matter, and REvil (aka Sodinokibi).
Black Basta also uses the double extortion technique encrypting files on the targeted network and asking for a ransom to decrypt them, while pressuring to make public the stolen data if the victim chooses not to pay. This malware made 75 attacks only last week.
As the ransomware world continues to evolve, becoming more and more complex, Agenda is following BlackCat, Hive, and Luna in using Go programming language.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









